能源安全大赛2025 复现
这次是跟联队最顶尖的佬们组的队,对我来说完全高端局。师傅们很厉害,给队伍干到了第四名Orz,但是我又爆零了。。。
赛后看了其他队伍的wp,misc的黑白相间这题我没做出来真的纯纯千古罪人了OrzOrzOrz
多说无益,开始复现(能看懂的题都复现一下好了)
Misc
黑白相间
发现在图片的末尾还有一张倒着的图片,提取出来
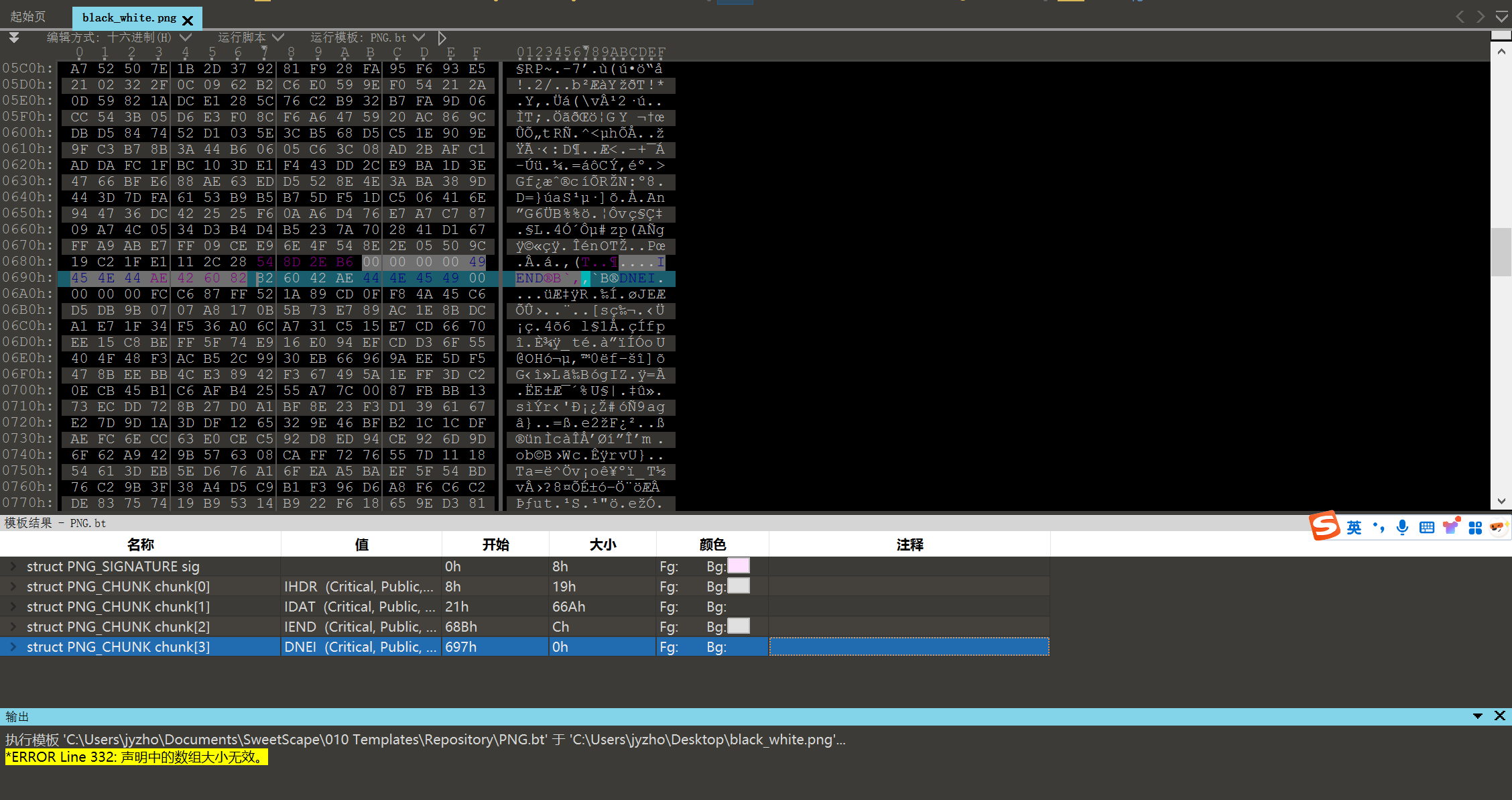
分别读取1.png和2.png,读到黑色像素记为1,白色像素记为0,将两张图片逐个像素异或得到一个二进制字符串,from bin以后发现是个zip文件
1 | from PIL import Image |
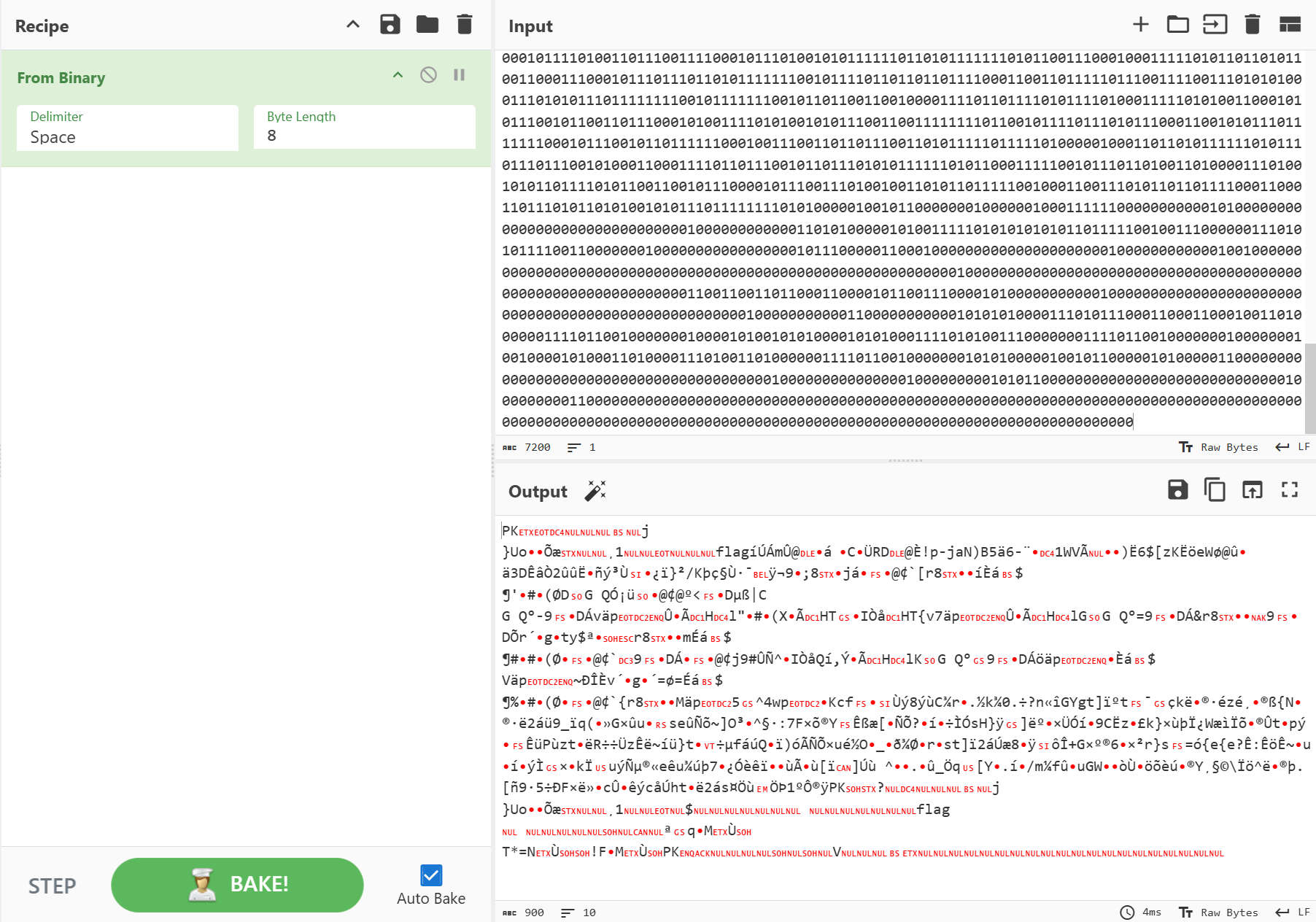
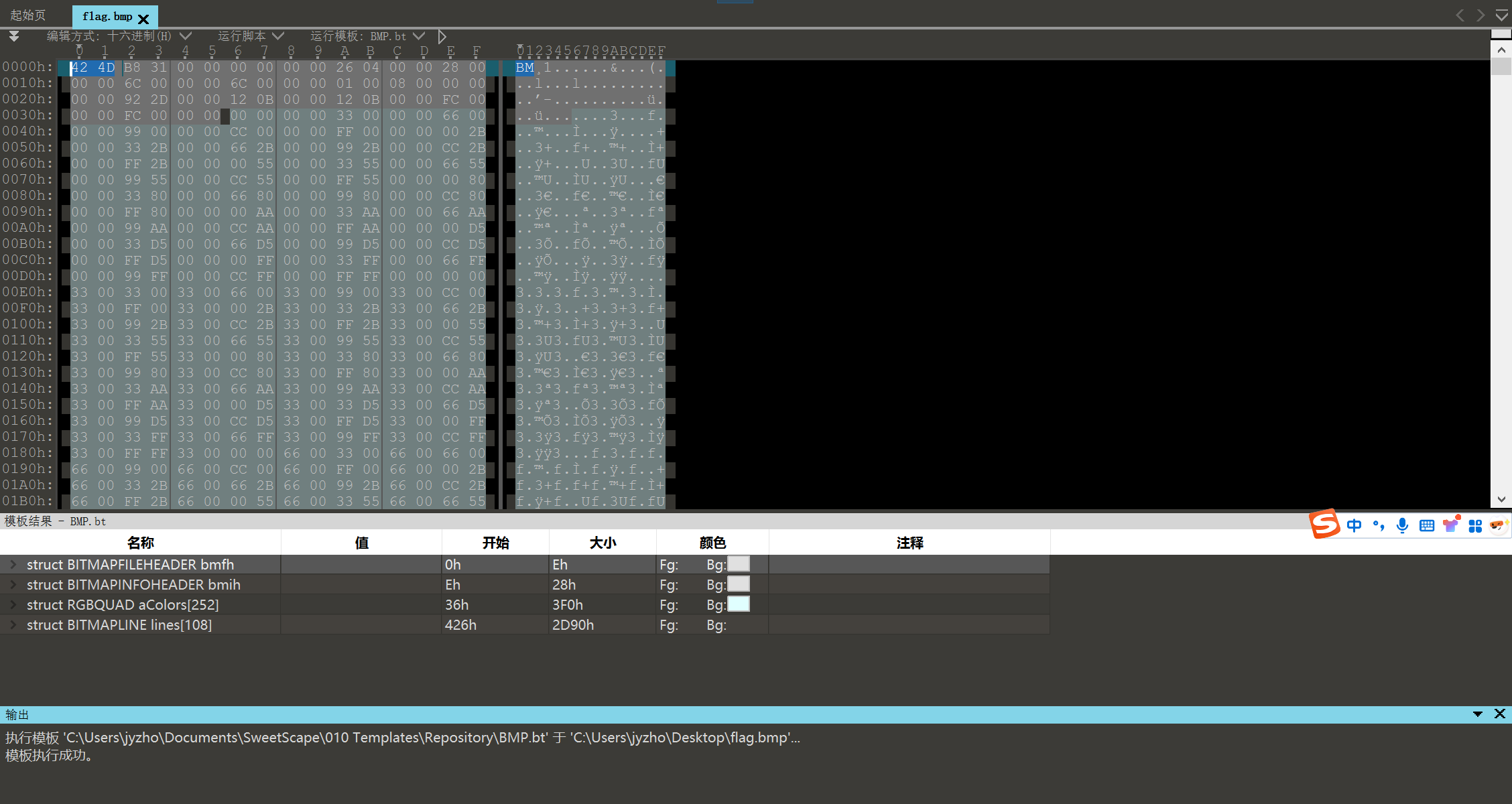
但是卡在这了,解压出来的flag看了半天不知道是什么东西,结果是个去掉了头的bmp文件。。。
作为一个misc手,对bmp文件的十六进制格式还如此生疏,在此做出深刻检讨。
flag是一个去掉了头的bmp文件,在开头补上424d即可
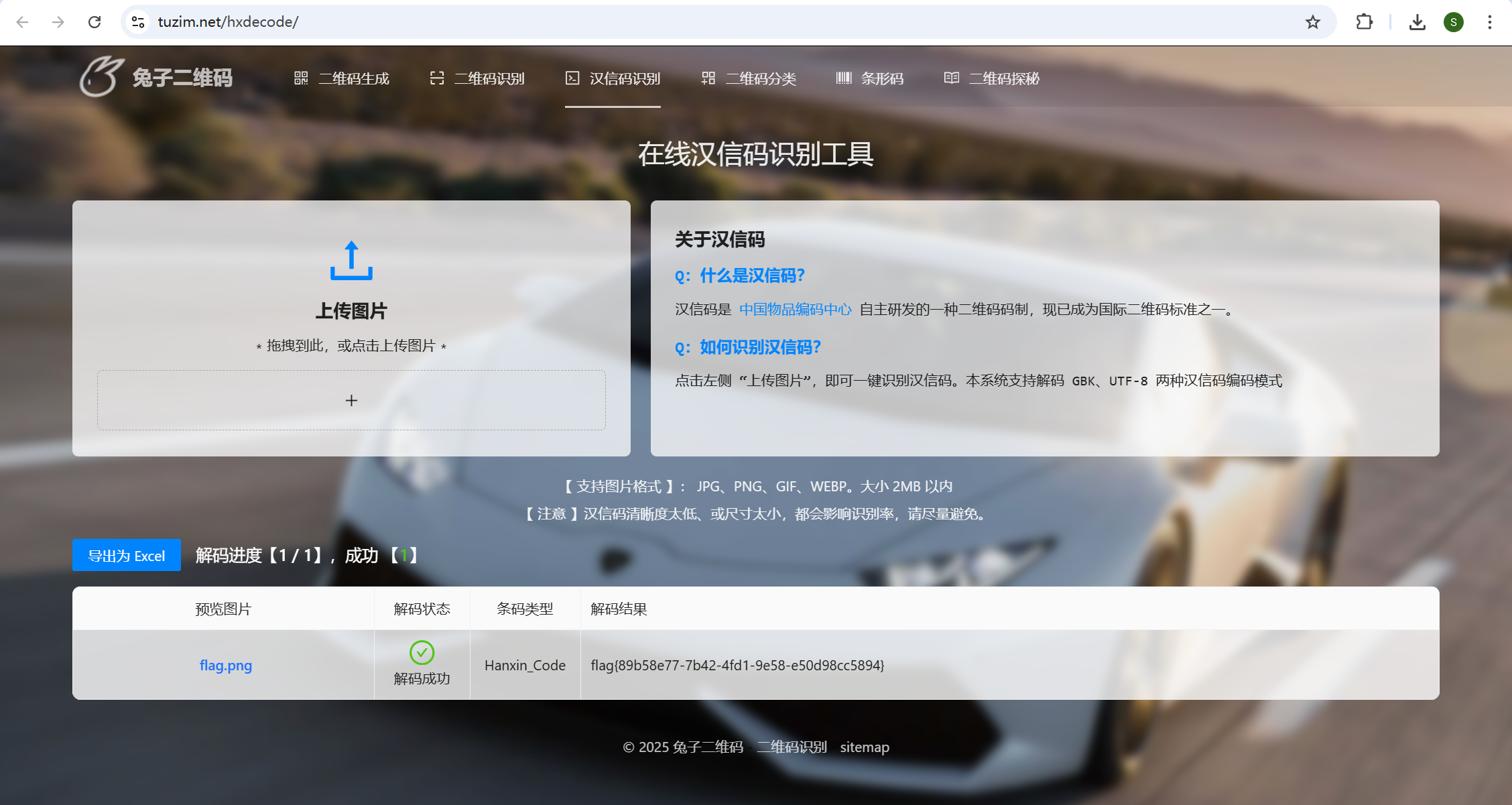
是一个汉信码,但是可以看出左下角的定位点被旋转过了,转回去

knn
大体思路就是从检测数据的csv表格中读取A车和B车的数据,根据题目名称可知用knn算法训练模型,然后对待检测数据表格中的每一行数据进行识别判断出是A车还是B车,A车记为1,B车记为0,from bin得到flag
不清楚n_neighbors是多少,写个脚本爆破一下找找合乎格式的flag即可
1 | import pandas as pd |
最终flag:
flag{e0f095bd-16e6-4bf5-a1c5-3dce1d693aa5}
数据安全
数据脱敏
题目要求
1 | 为了抵抗黑客攻击导致数据拖库等问题,需要将敏感数据识别并脱敏存储成⼀个表。给定脱敏算法逻辑,要求选⼿⽣成脱敏后的数据表数据(所有数据均为随机⽣成,与现实世界⽆任何联系)。为了防⽌⼀些隐私数据泄漏,现需要对该数据表进⾏脱敏操作,请按照指定要求对各字段进⾏脱敏处理,并按照先行后列拼接字符串(不包含标题行),对此字符串进行md5计算,得到答案。 |
比赛时以为是格式上有什么问题,怎么调都不对。没想到这里这个编号无需脱敏的意思是,编号也不用加到最终的字符串中。。。
1 | import pandas as pd |
Crypto
NumberTheory
题目
1 | from Crypto.Util.number import * |
由题 \[ hint+233*k=233*k*p \] 变换得 \[ hint=233*k*(p-1) \] 设a \[ a^{hint}\equiv a^{233*k*(p-1)}(mod\ p) \]
由费马小定理得 \[ a^{hint}\equiv1(mod\ p) \] 因此 \[ p=gcd(a^{hint}-1,n) \] exp
1 | from Crypto.Util.number import * |
能源行业
usb
又来见识新的妙妙工具了
经典usb流量,knm.py把所有hid data提取出来
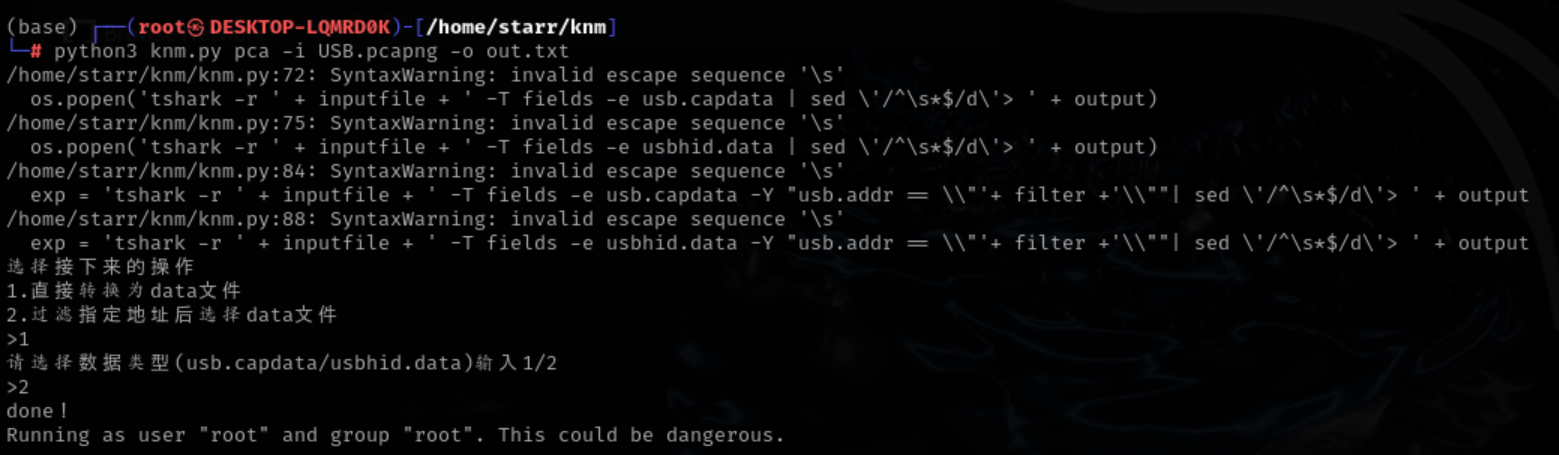
然后处理数据
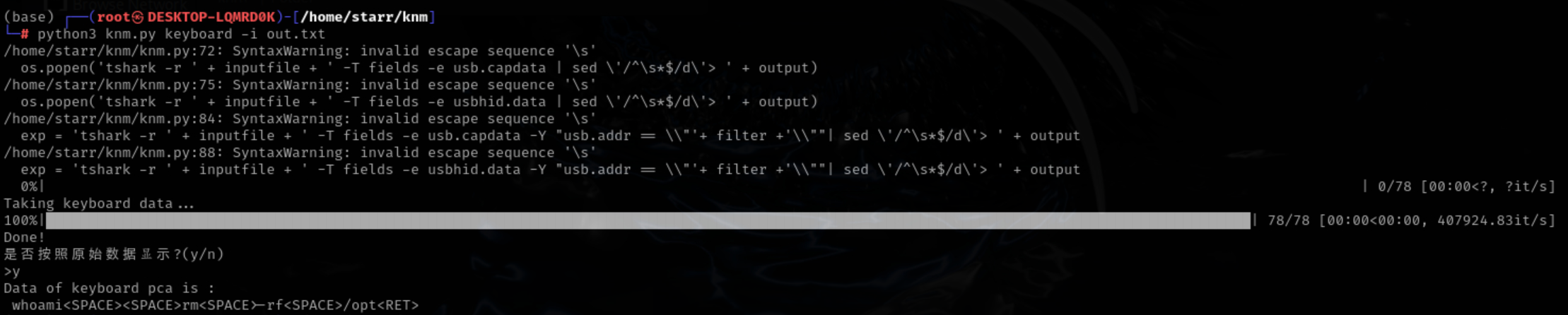
或者用祖传脚本对应按键解码hid data。解出来的东西不大精准,但大概也能看出来。
1 | KEYCODE_MAP = { |
whoami && rm -rf /opt