强网拟态2024 初赛Misc Writeup+复现
Writeup部分
Crypto
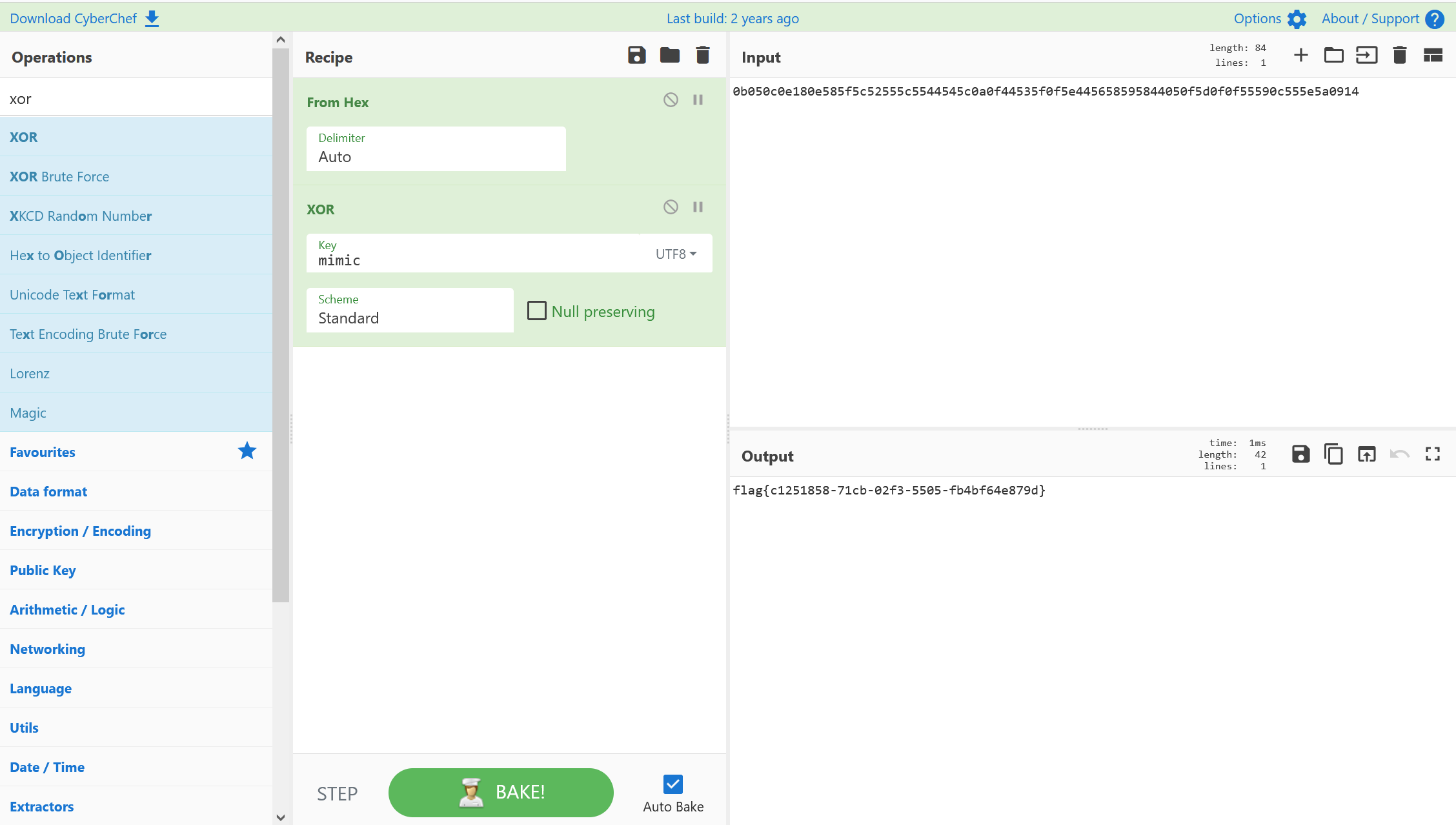
Xor
签到题
Misc
ezflag
追踪一下tcp流,一眼看到pk,得知是传了一个压缩包,提取出来
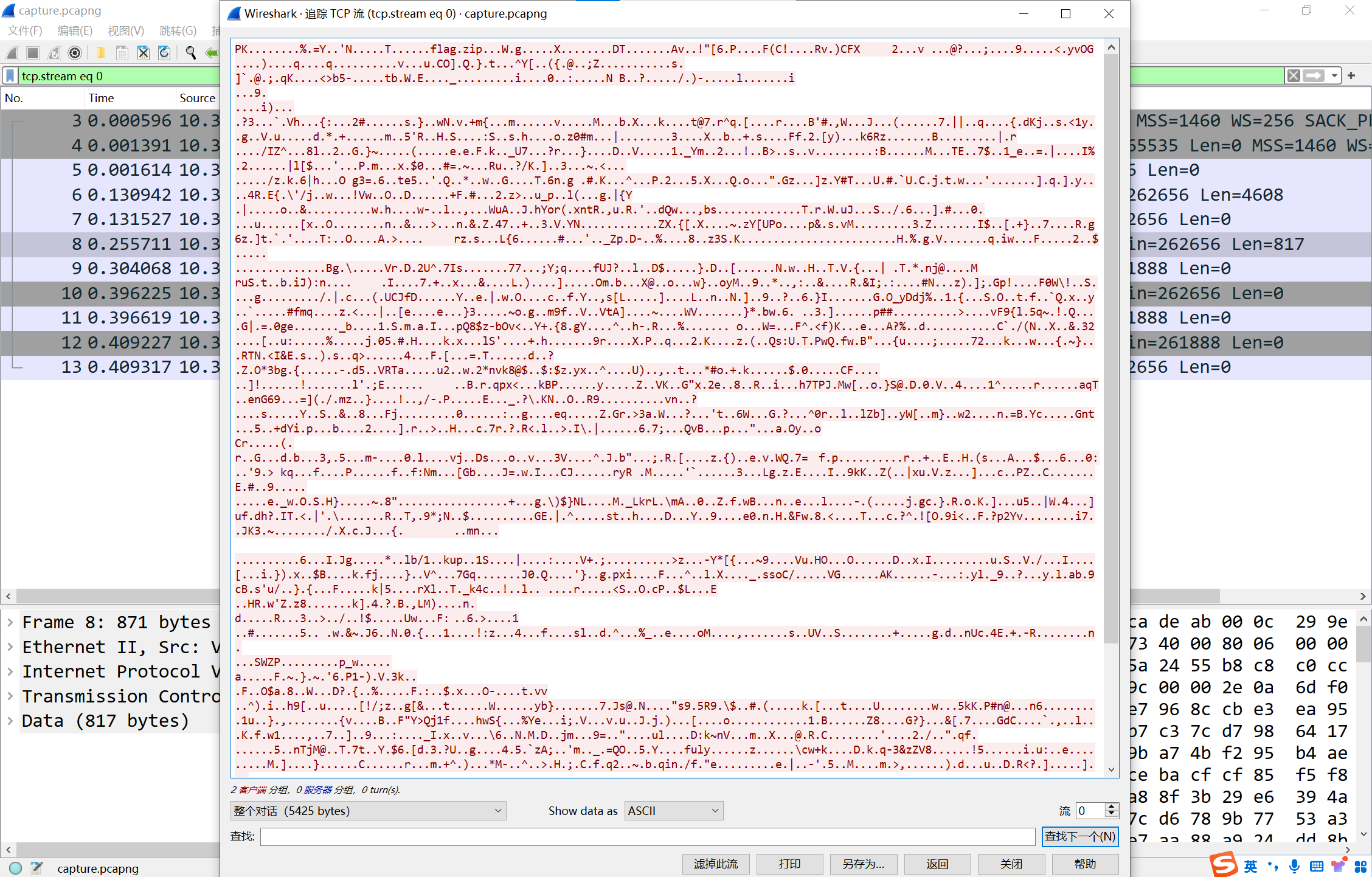
解压出来的flag.zip没法解压,丢进010看一下,发现这其实是个png
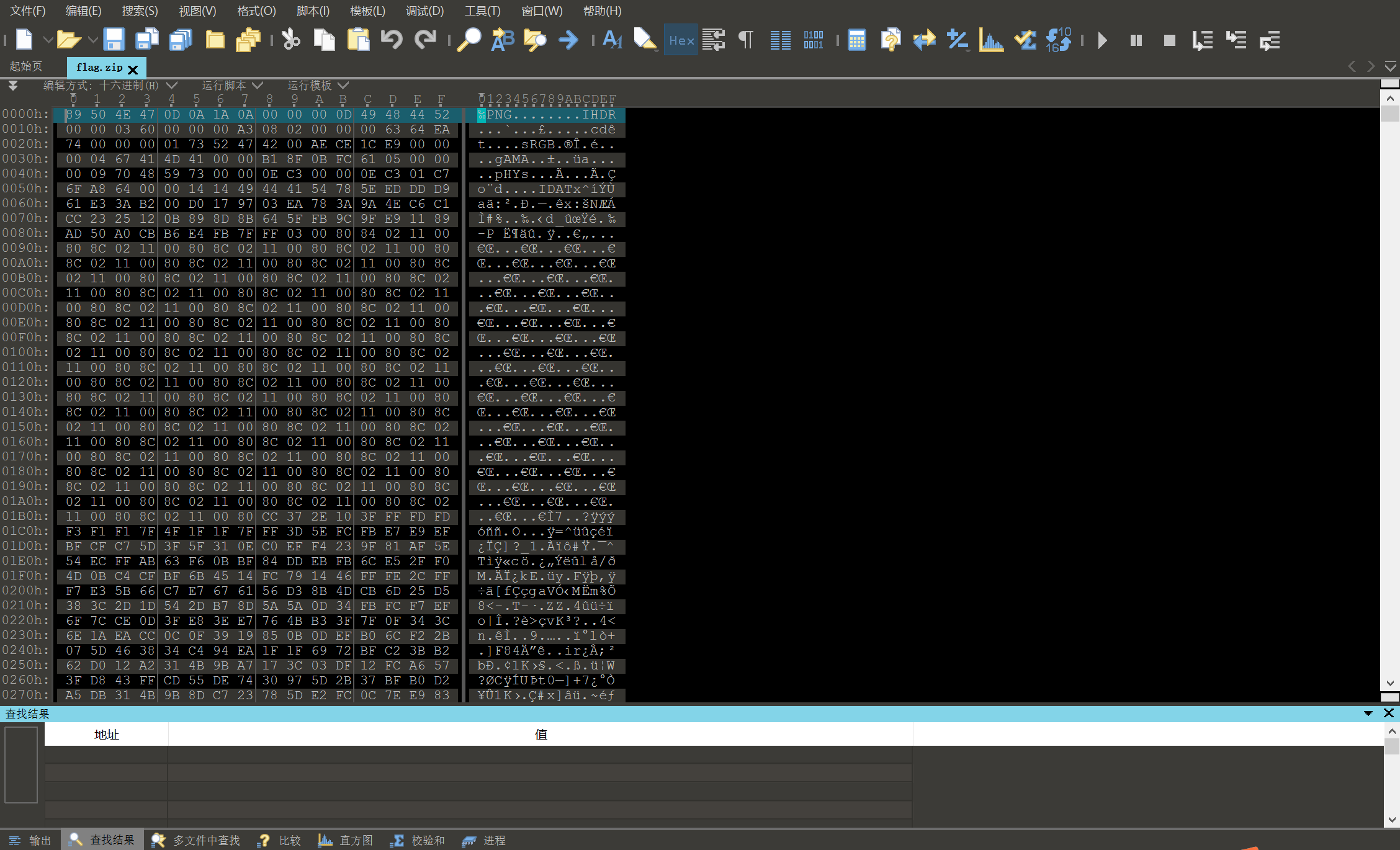
改后缀名为.png即可看到flag
Pvz
提示说压缩包密码是pvz图中消耗阳光数的md5值,懒得去算,直接爆破
1 | import hashlib |
正确的答案是738
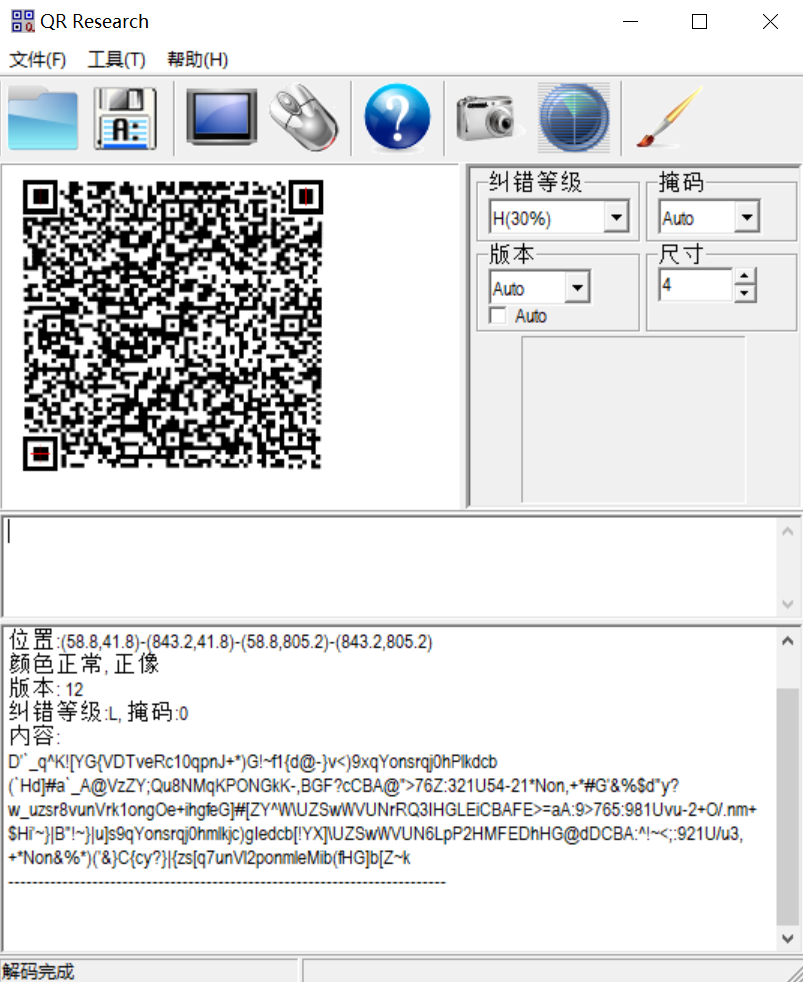
解压出来一个被旋转、裁剪过的二维码

用gimp等等软件处理一下,恢复二维码原来的状态

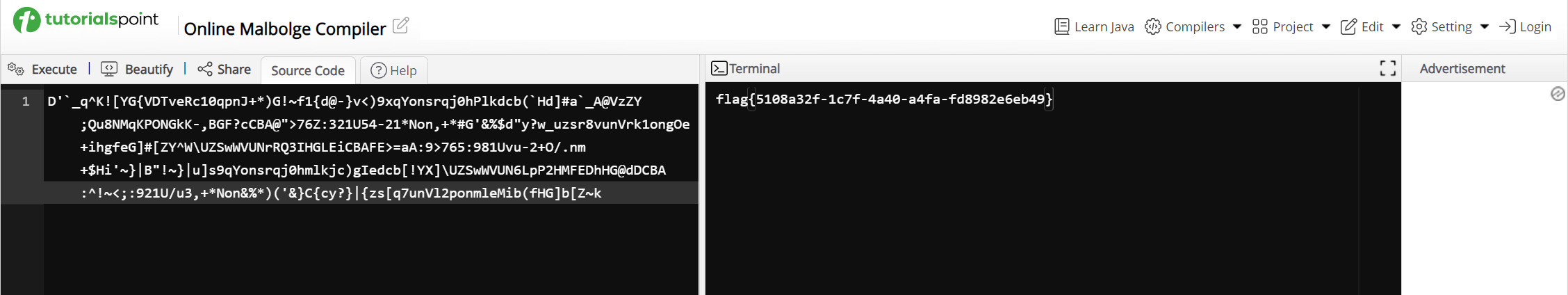
扫出来一串奇怪的东西,结合文件名可以知道这是一种叫做malbolge的抽象语言
复现部分
剩下的感觉都是一些脑洞题,想不到,真的想不到。。。
Misc
Find way to read video
题目说tessa3098把一个邮件模板放在了一个公共平台上。经过寻找,我们可以在gitcode上找到要找的东西。
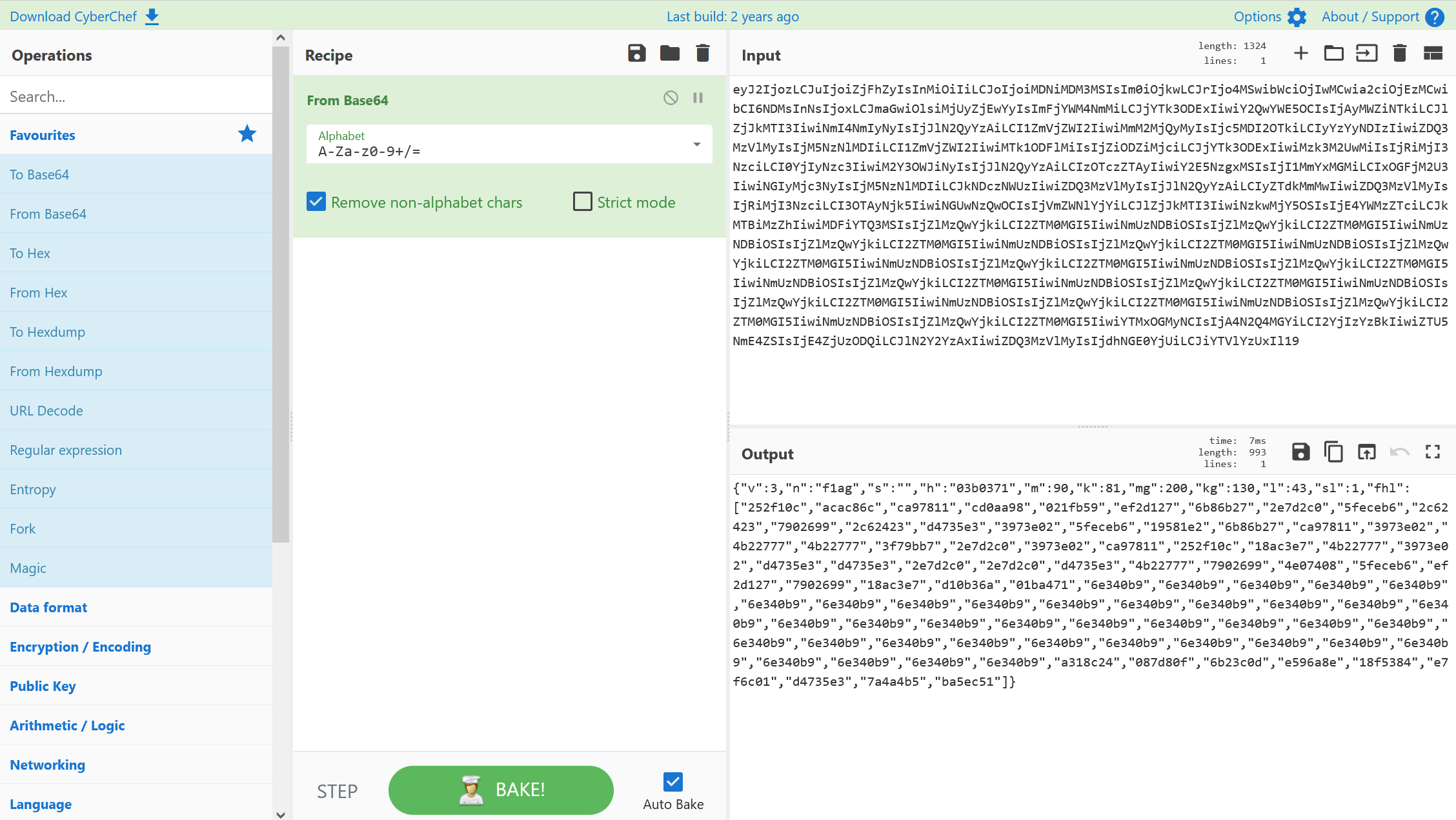
这是一个垃圾邮件隐写,解码可以得到一个BV号和一串看起来是session cookie的东西,可以直接base64解码

通过BV号在B站上可以搜到九十集视频,全部爬下来

当时是卡在这了,注意到了视频上移动的小白点,但不知道要干什么
预期解没看懂,但是有一种方法看懂了。base解码得到的那一堆十六进制数,经过尝试可以发现是不同字符的哈希值头几位,写脚本还原一下。
1 | import hashlib |
Streaming
追踪一下udp流,可以看到是在传一个h264视频
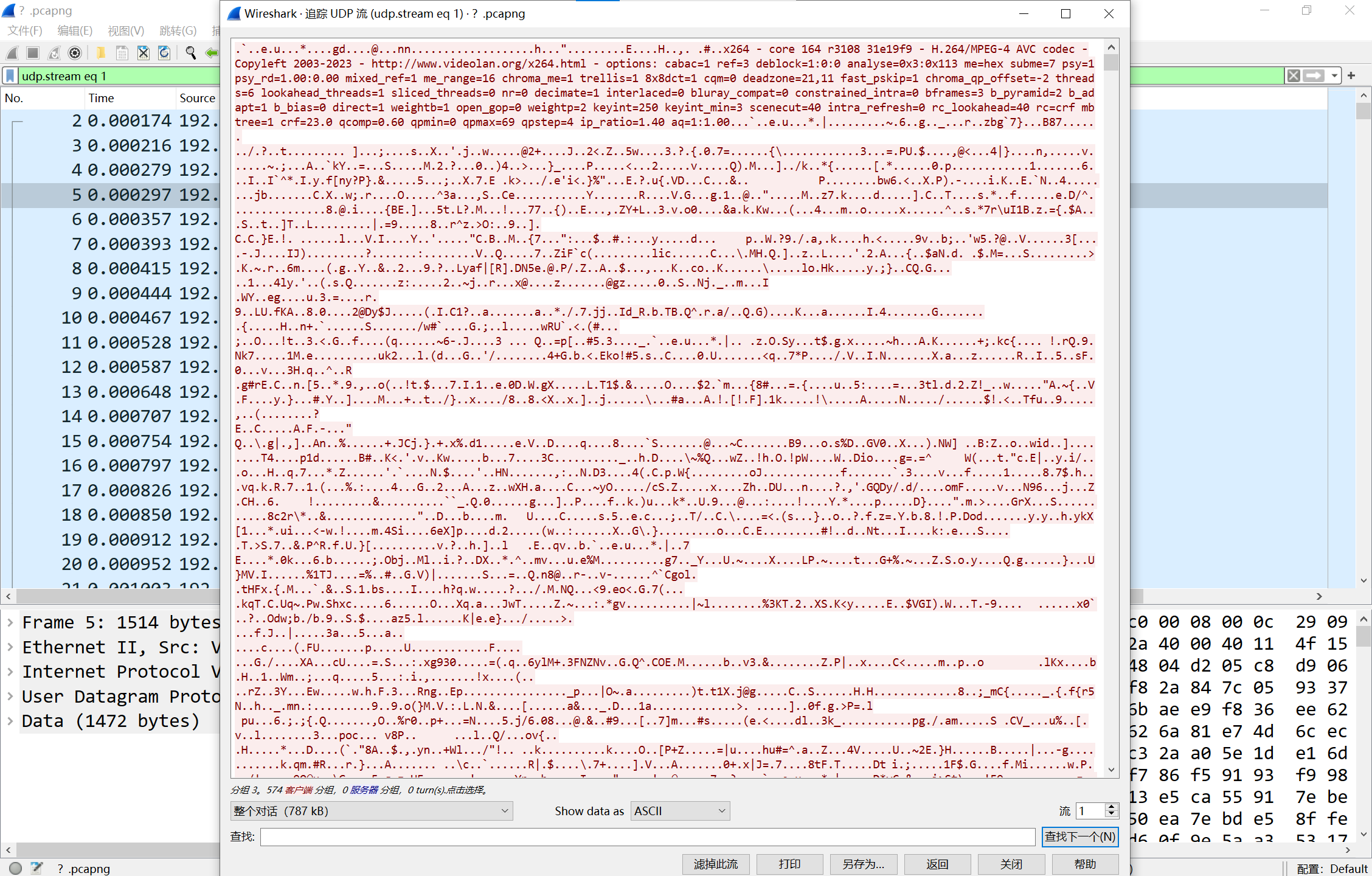
右键decode as改为rtp
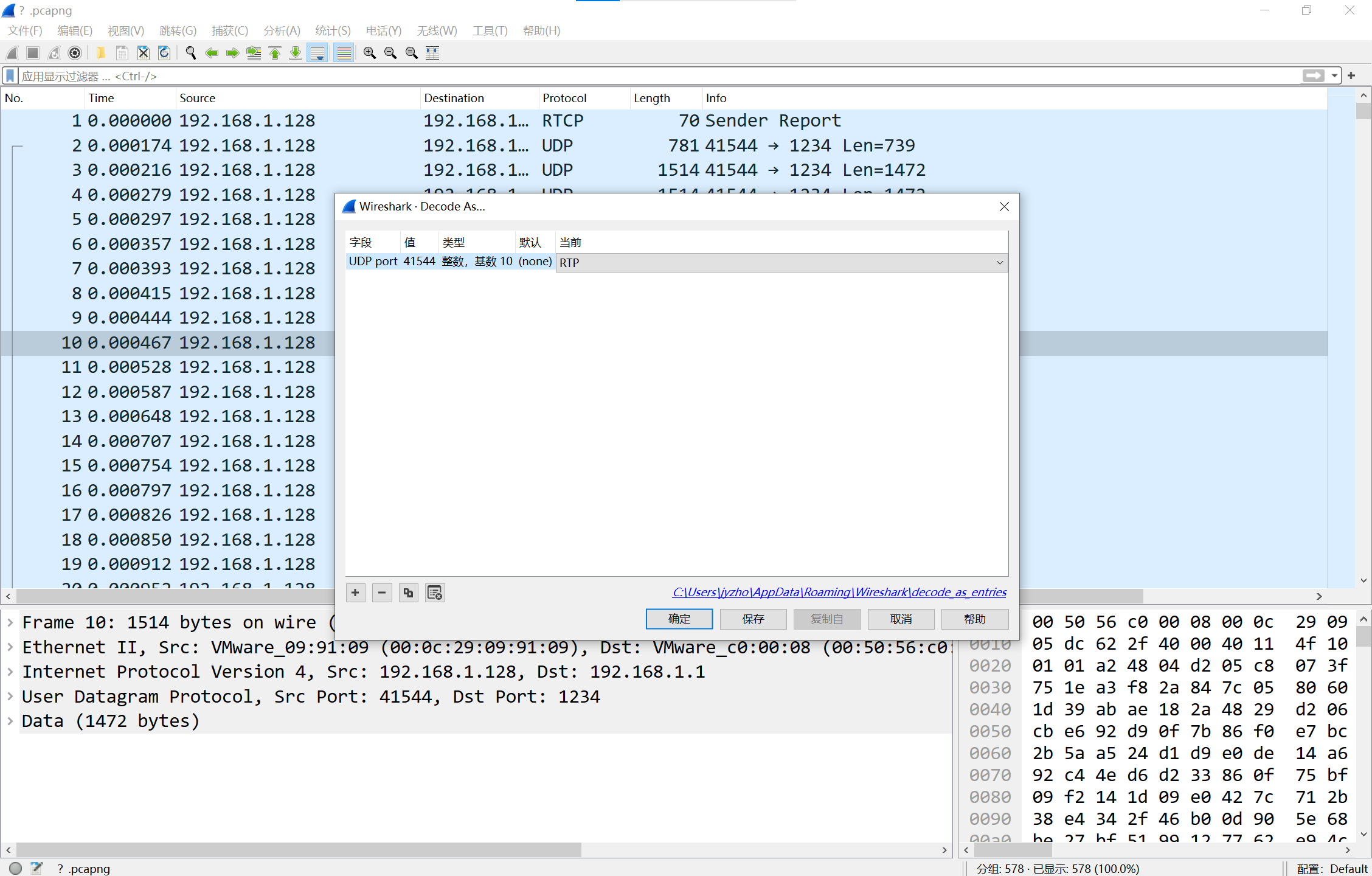
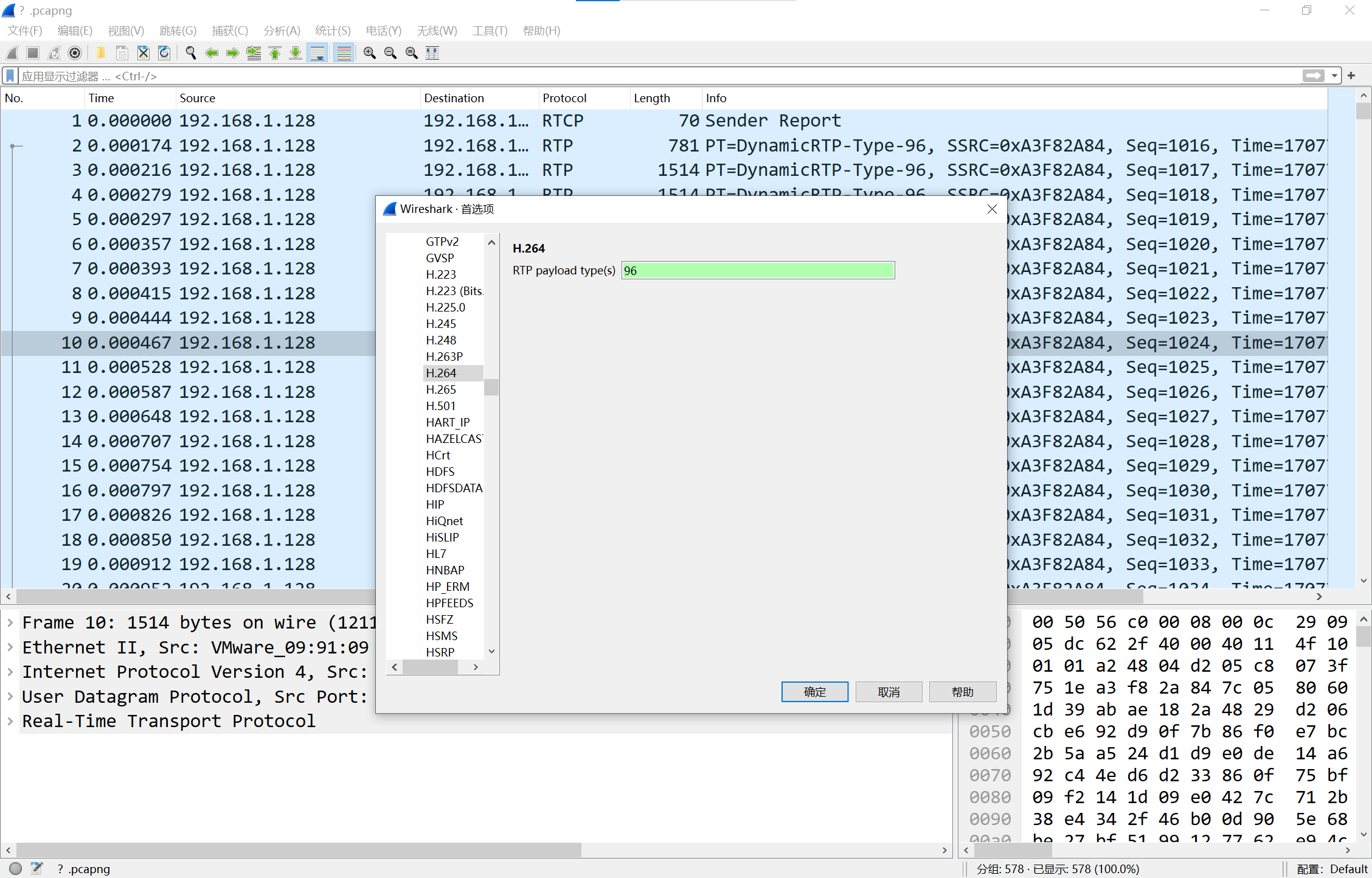
可以看到DynamicRTP-Type-96,打开编辑-首选项,找到H.264,填入96
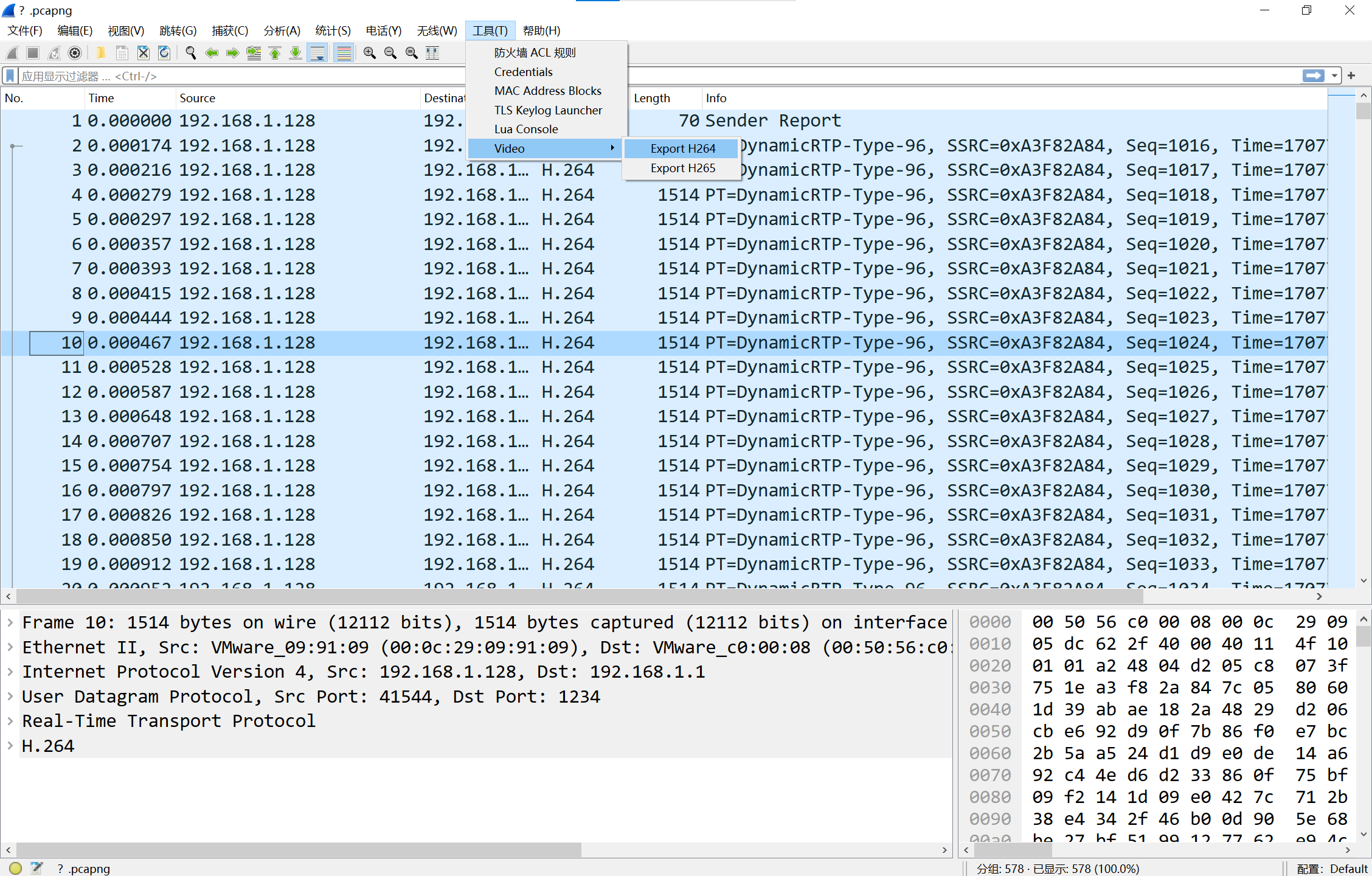
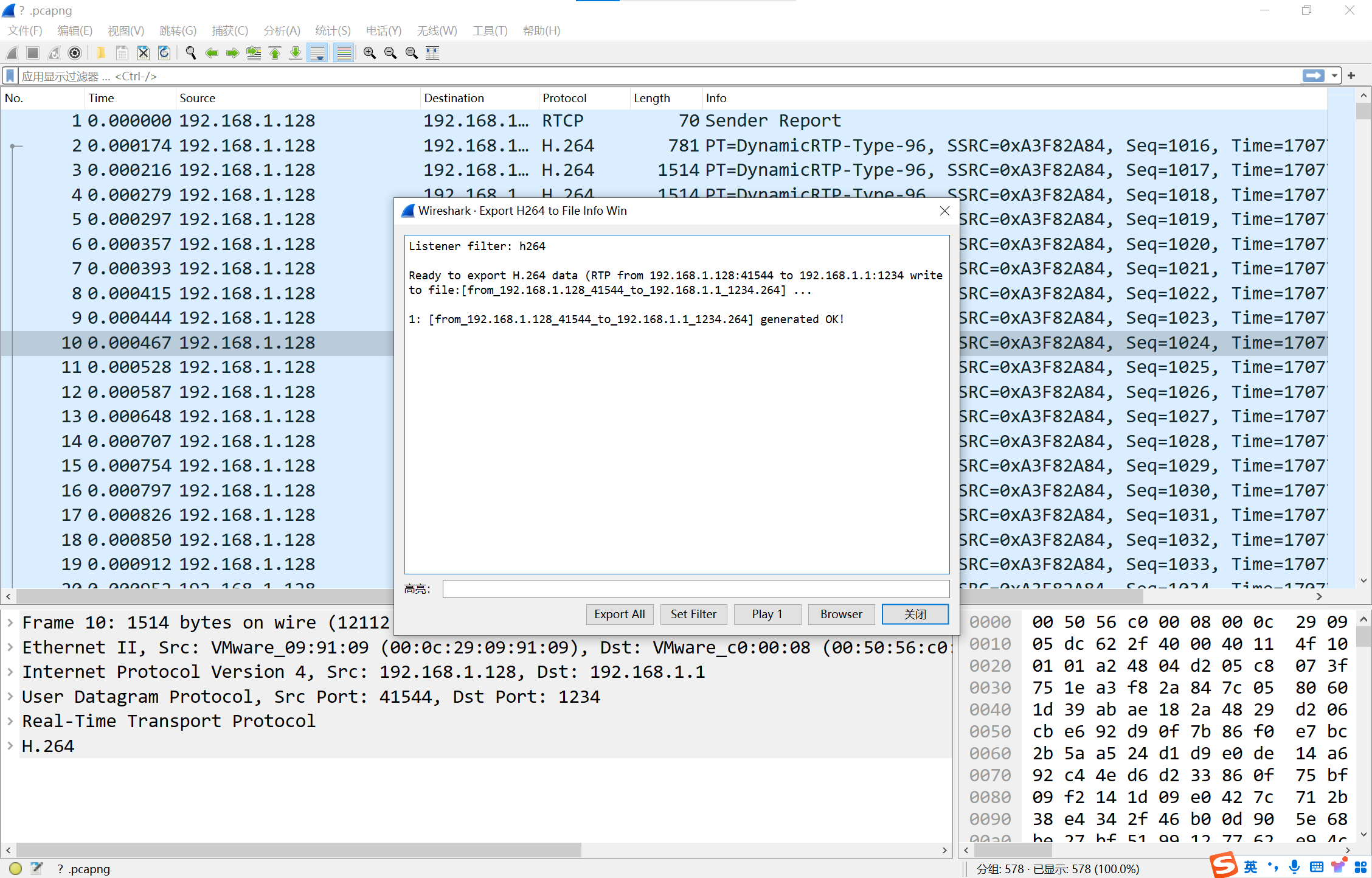
下载lua插件,提取H264视频
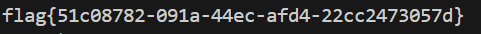
用milkplayer播放一下,可以看到第一段flag以及一个hint
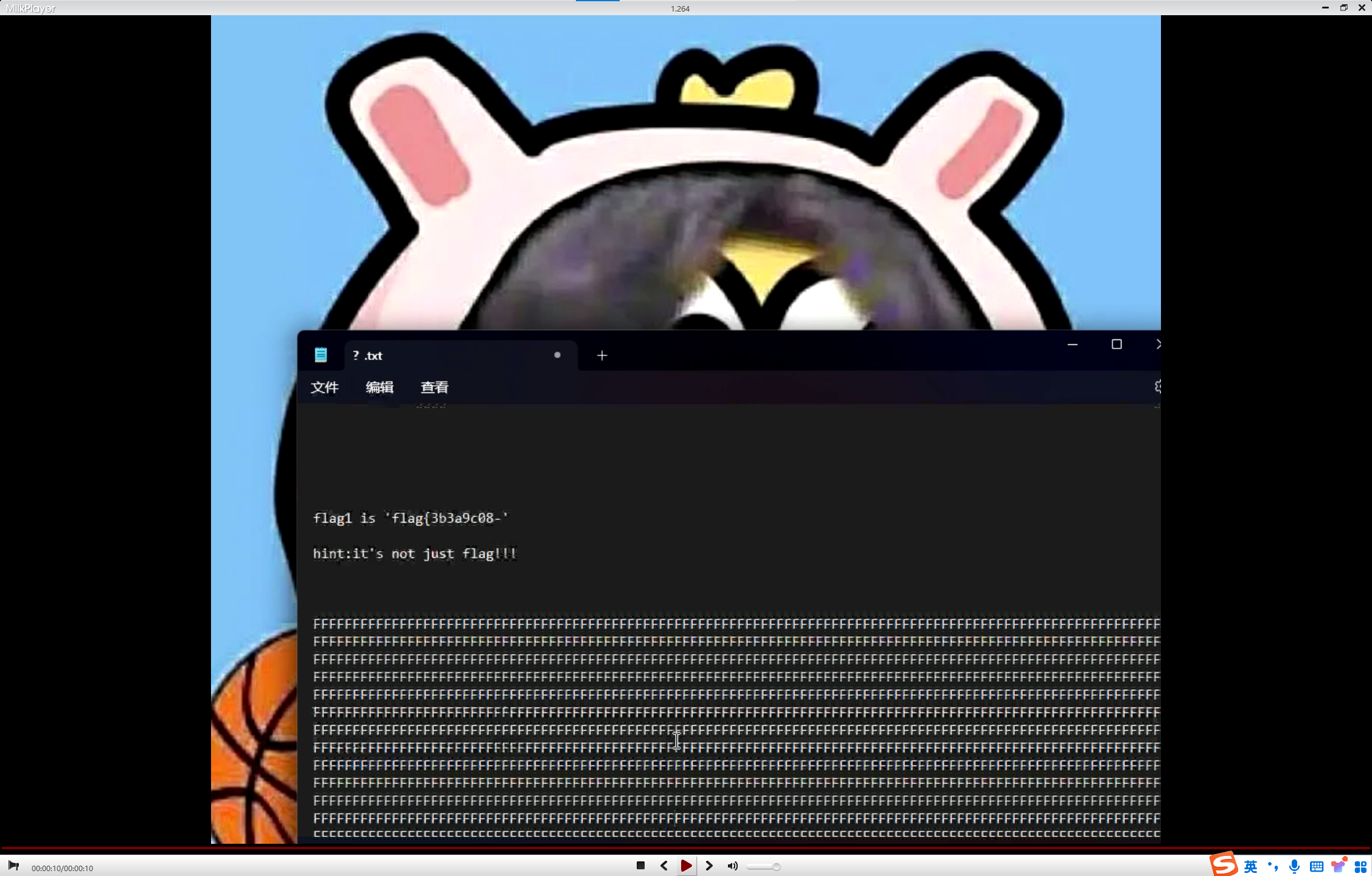
当时是卡在了这,知道肯定是要用这个flag1做某种key去解密另一个文件,但是试了半天都不对。。。又是一个脑洞
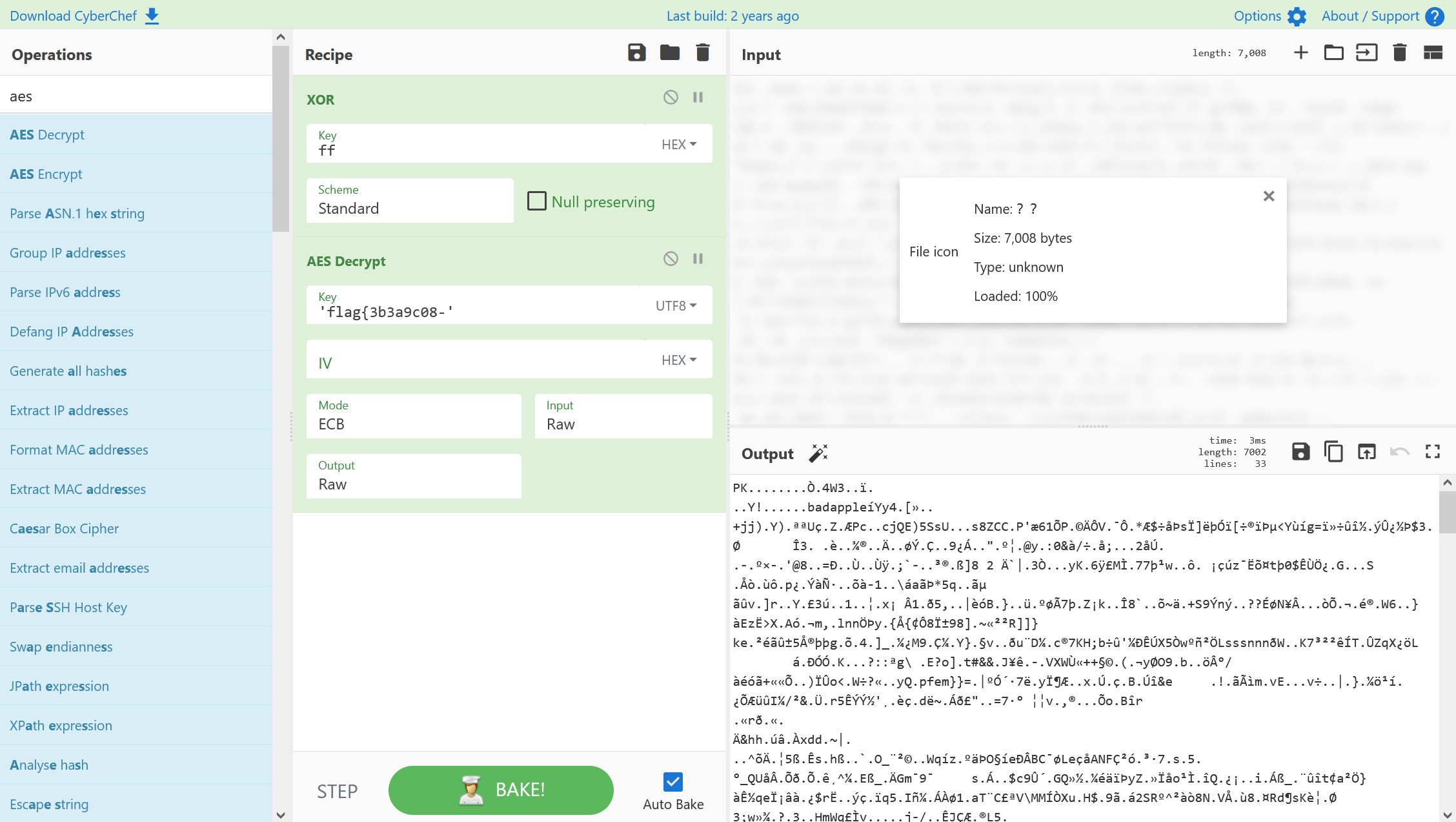
实际上这里是要先进行异或ff,然后再进行AES解密。(不知道怎么想到的。。。)
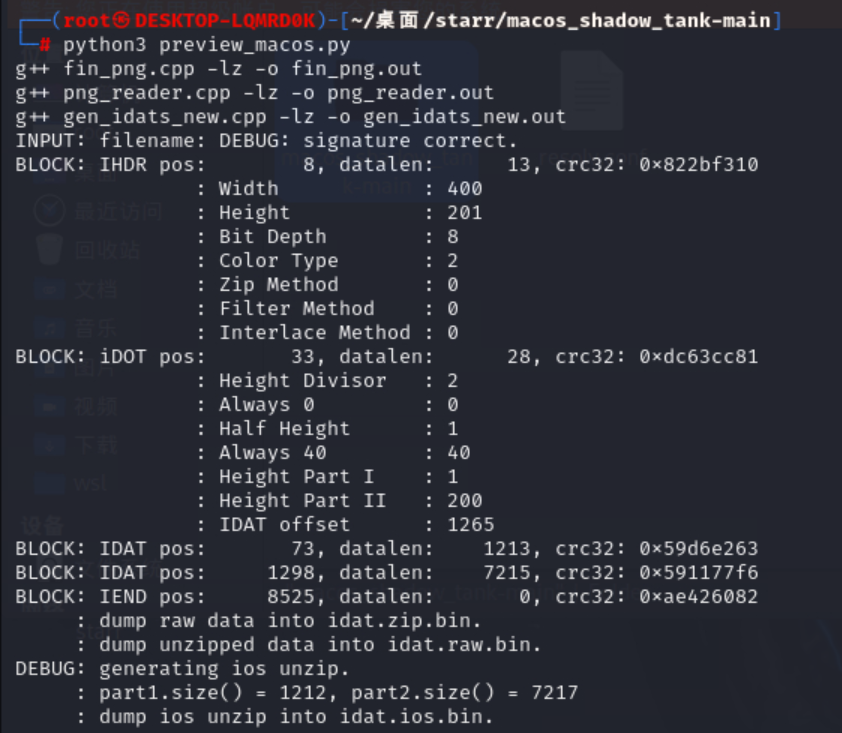
解压出来两个没有后缀的文件,其中一个用trid识别出来是png,用这个项目在linux下提取一下得到第二段flag

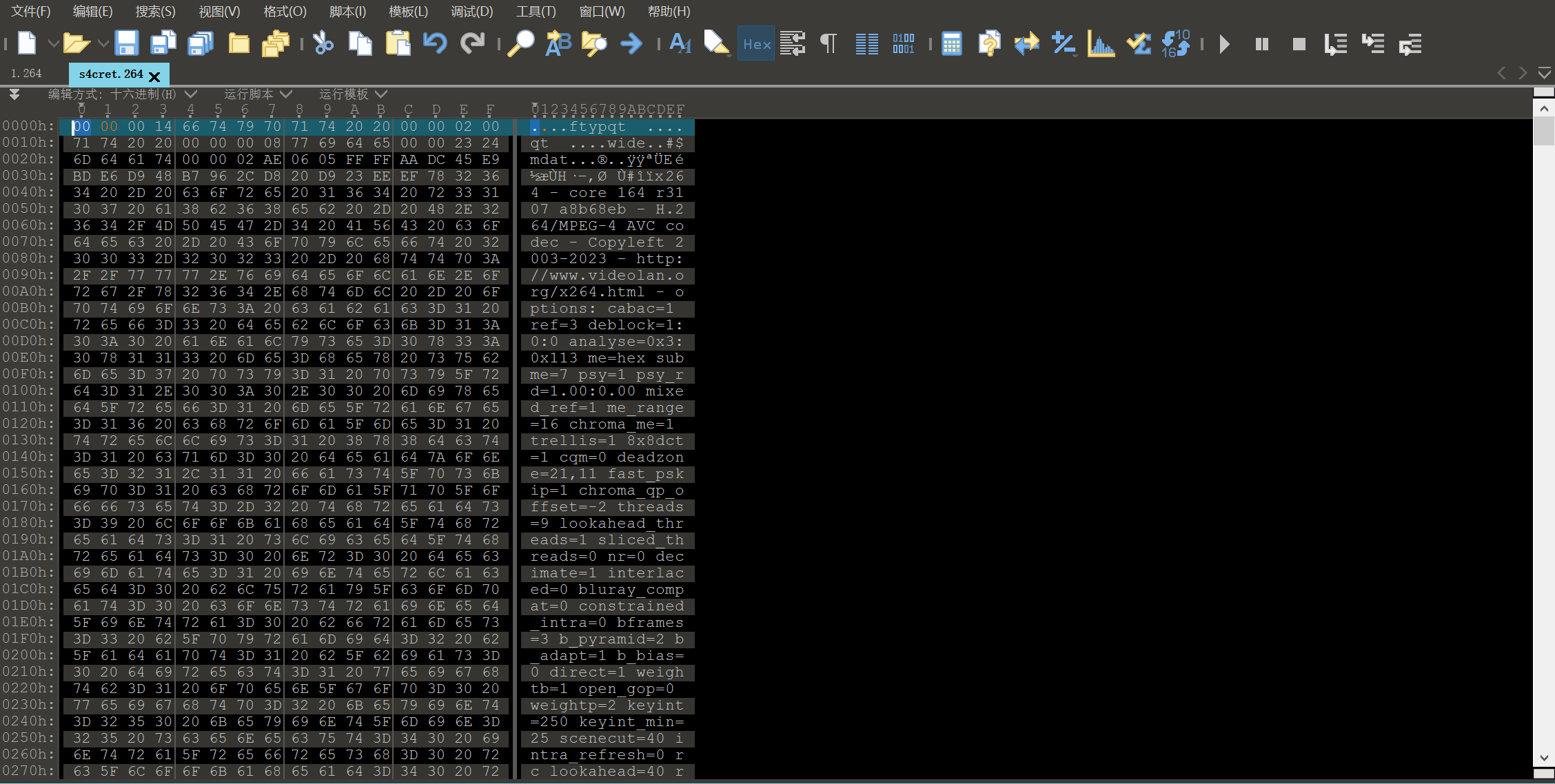
另一个文件用010打开发现又是H264视频,照着之前的264文件在前面补3个00
播放后发现是黑白帧的交替,转换成01二进制串
1 | import cv2 |
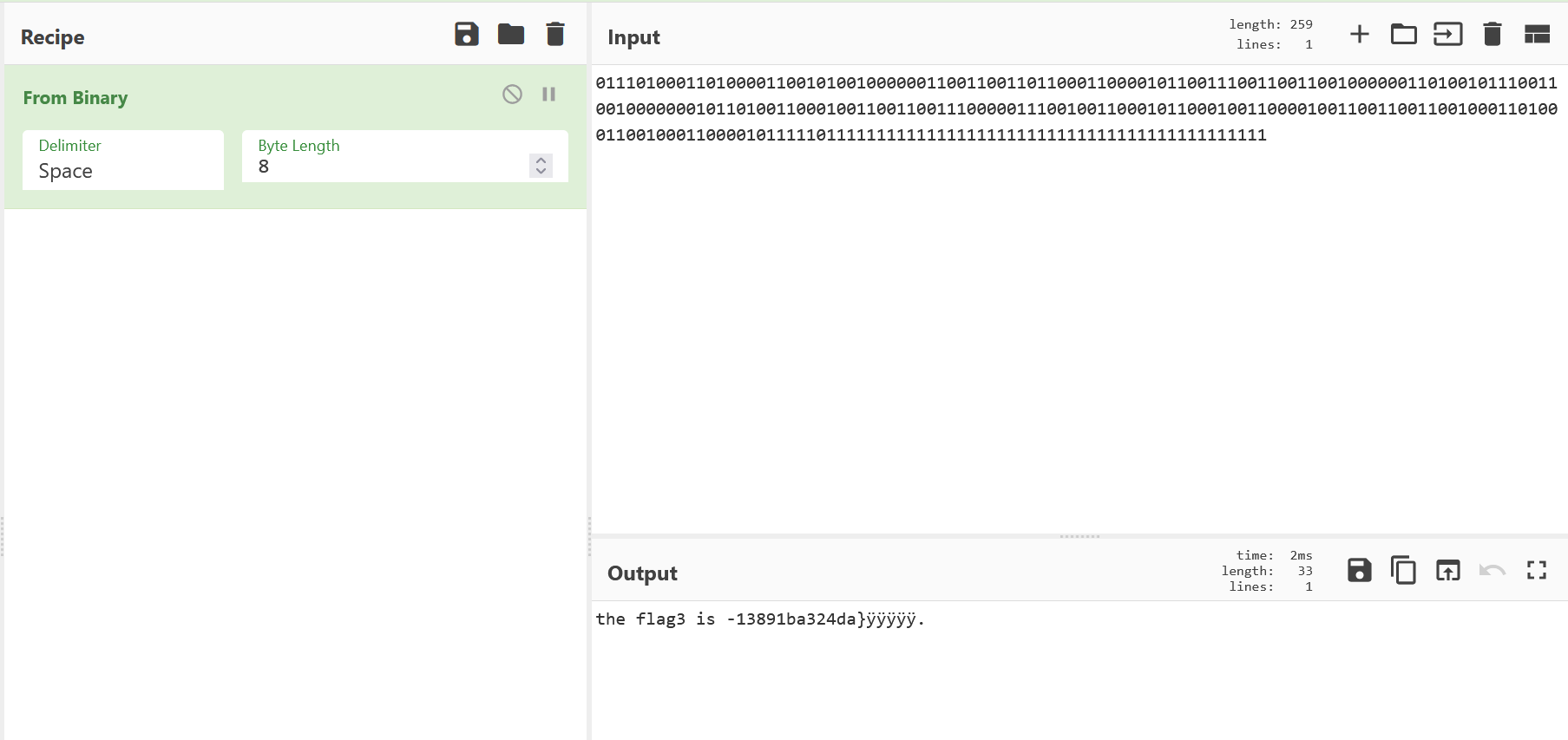
flag{3b3a9c08-88c4-4d65-b59e-13891ba324da}