帮联队里别的师傅看的比赛,做了点简单题
Misc
ez-picture
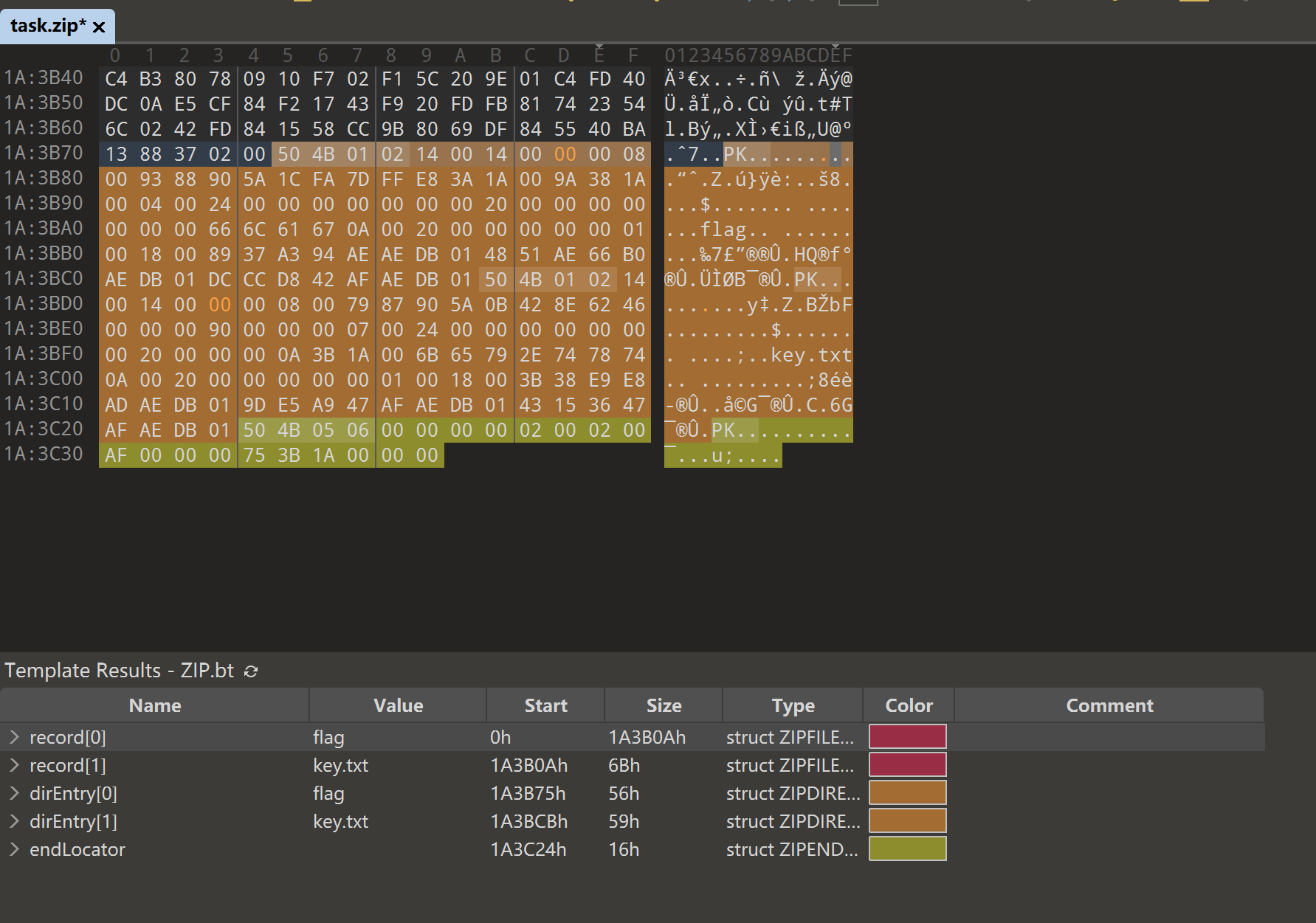
伪加密改回去解开压缩包
image-20250713190109710
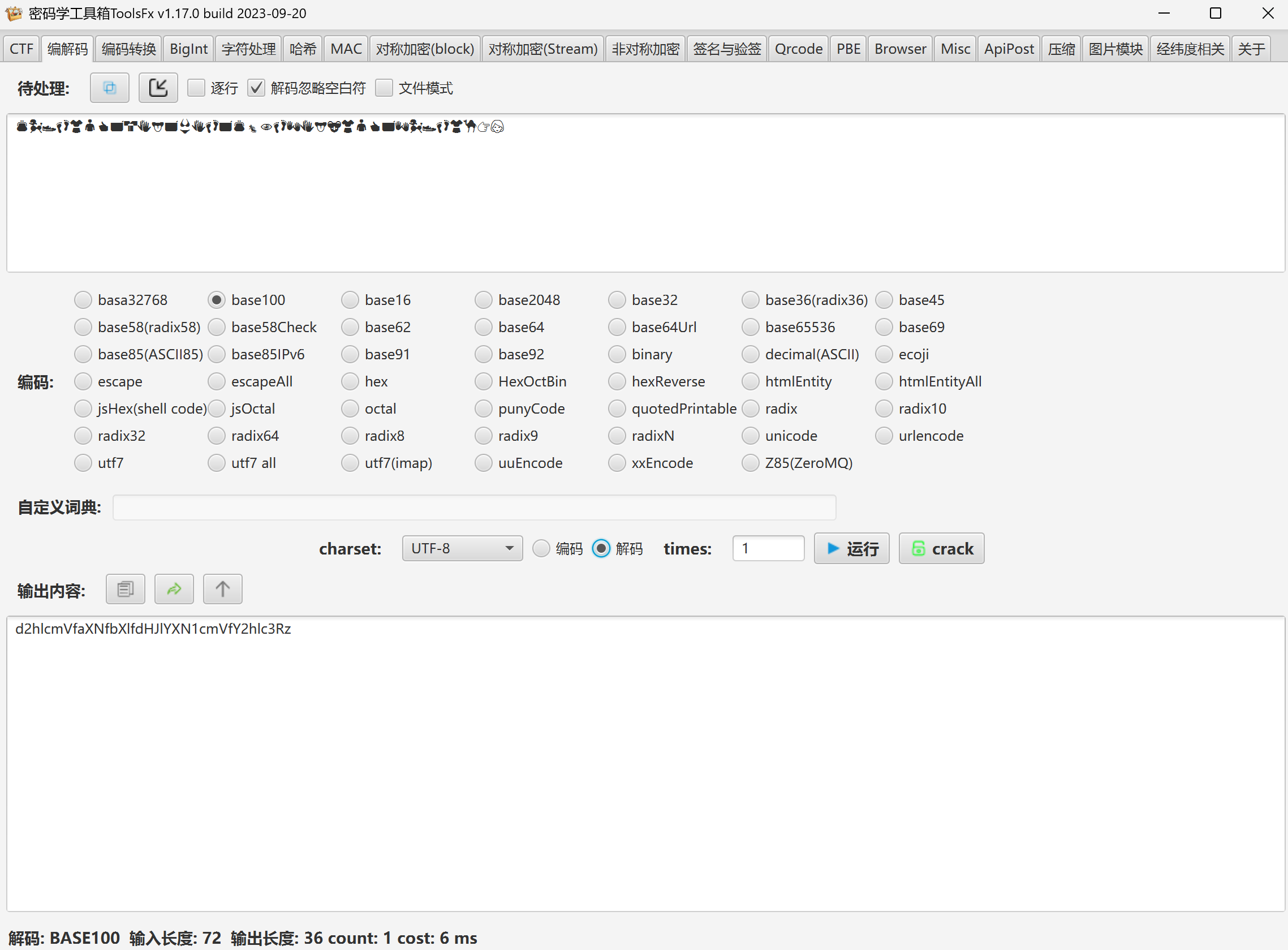
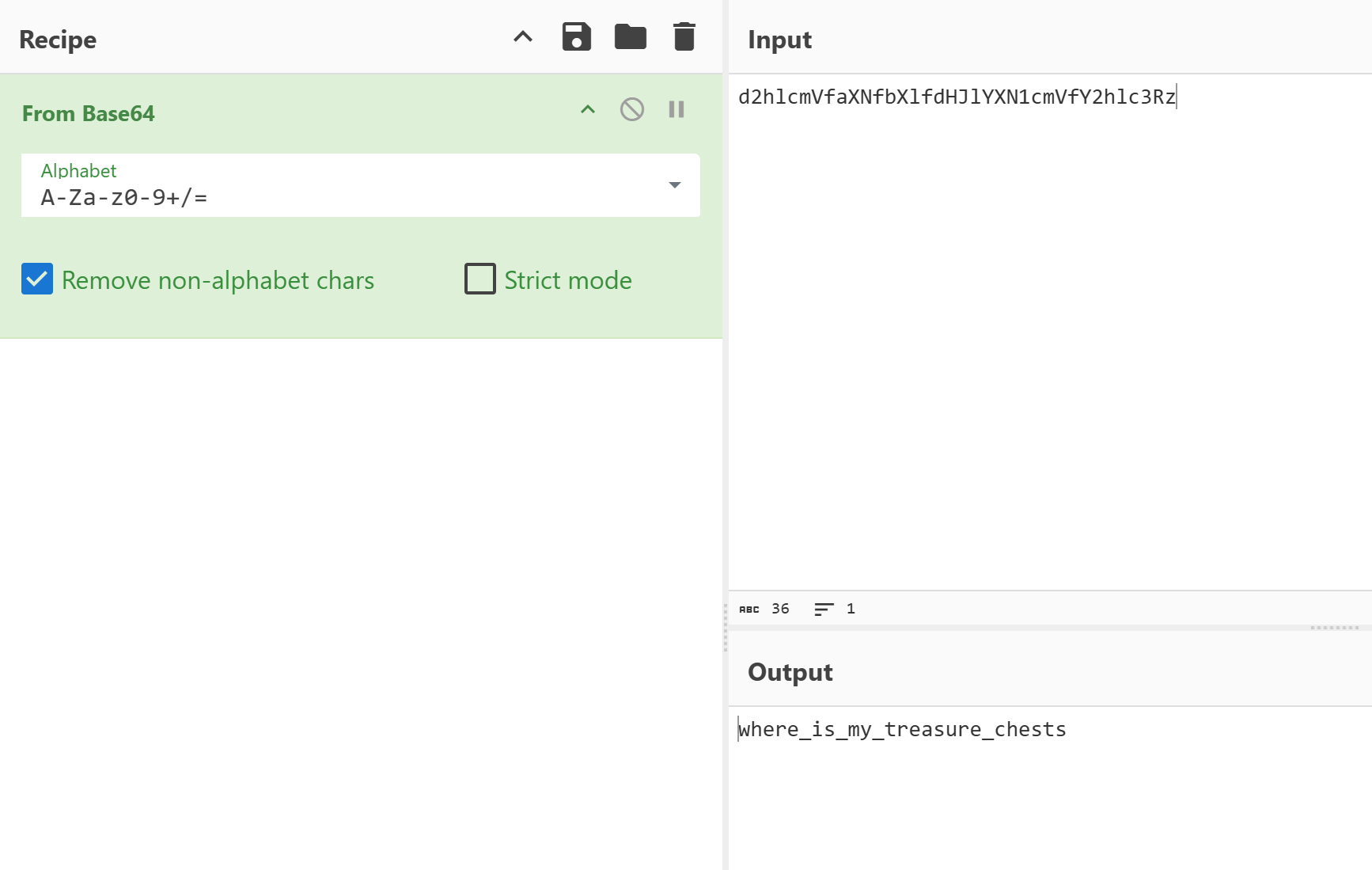
对于key.txt:base100 -> base64
image-20250713190221446
image-20250713190251979
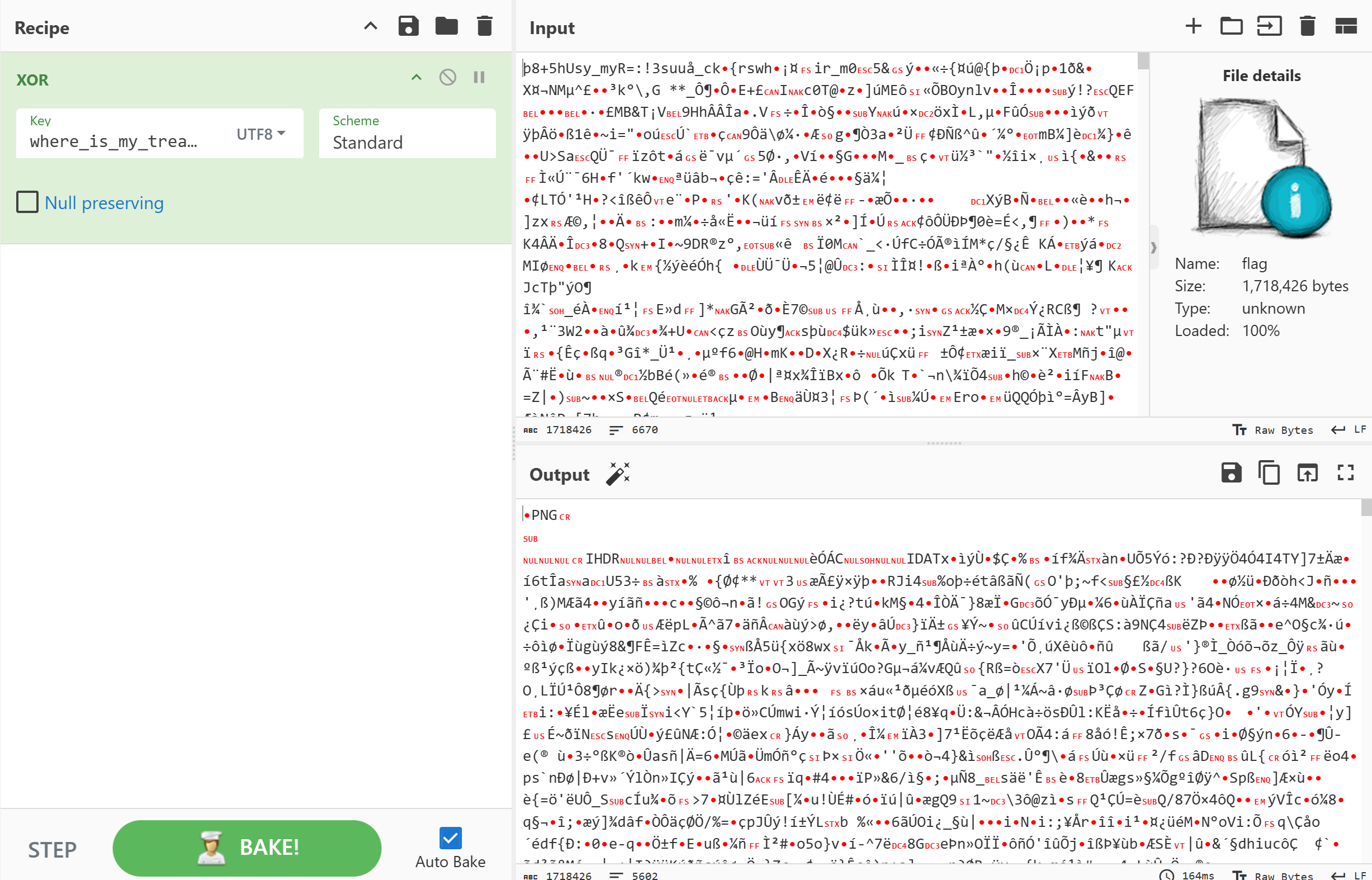
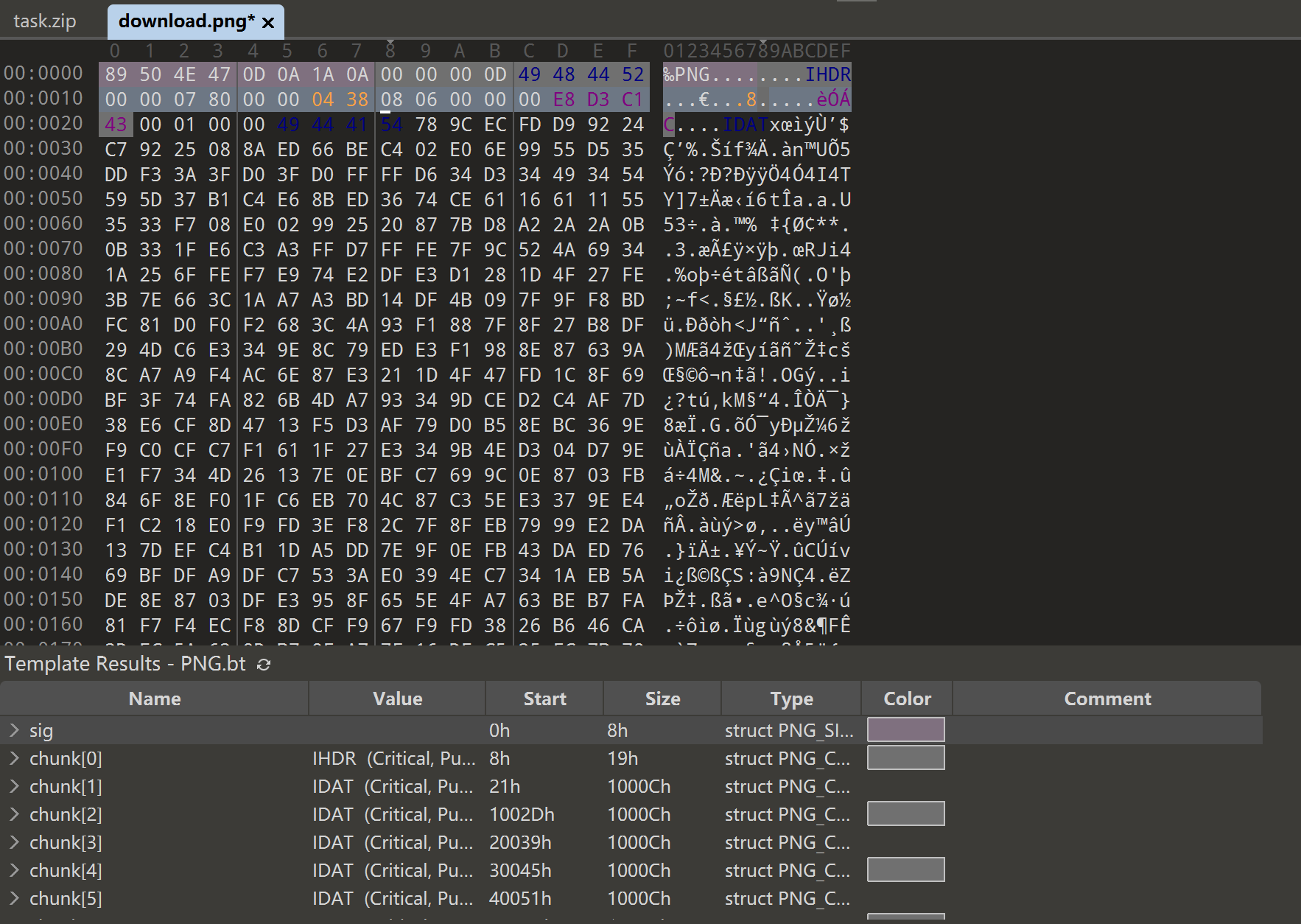
用key对flag文件异或,得到一个png
image-20250713190344888
爆破png的宽高,修改为正确的值即可看到flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 import binasciiimport structcrcbp = open ("download.png" , "rb" ).read() crc32frombp = int (crcbp[29 :33 ].hex (),16 ) print (crc32frombp) for i in range (10000 ): for j in range (10000 ): data = crcbp[12 :16 ] + \ struct.pack('>i' , i)+struct.pack('>i' , j)+crcbp[24 :29 ] crc32 = binascii.crc32(data) & 0xffffffff if (crc32 == crc32frombp): print (i, j) print ('hex:' , hex (i), hex (j)) exit(0 )
image-20250713190548509
download
Crypto
ez-learning
题目
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 from Crypto.Util.number import getPrime, bytes_to_long, long_to_bytes, GCDimport gmpy2 from secret import flagdef extended_gcd (a, b ): if a == 0 : return b, 0 , 1 d, x1, y1 = extended_gcd(b % a, a) x = y1 - (b // a) * x1 y = x1 return d, x, y def main (): print ("RSA learning 挑戰 " ) print ("=" * 40 ) m1_val = bytes_to_long(flag_part1_str.encode('utf-8' )) m2_val = bytes_to_long(flag_part2_str.encode('utf-8' )) m3_val = bytes_to_long(flag_part3_str.encode('utf-8' )) m4_val = bytes_to_long(flag_part4_str.encode('utf-8' )) print ("--- 第一部分 ---" ) p1_bits = 256 q1_bits = 256 p1 = getPrime(p1_bits) q1 = getPrime(q1_bits) while p1 == q1: q1 = getPrime(q1_bits) n1 = p1 * q1 phi1 = (p1 - 1 ) * (q1 - 1 ) e1 = 65537 c1 = pow (m1_val, e1, n1) print (f"n1 = {n1} " ) print (f"e1 = {e1} " ) print (f"c1 = {c1} " ) print (f"p1_given = {p1} " ) print ("-" * 40 ) print ("--- 第二部分 ---" ) p2_bits = 256 p2 = getPrime(p2_bits) q2 = gmpy2.next_prime(p2) n2 = p2 * q2 phi2 = (p2 - 1 ) * (q2 - 1 ) e2 = 65537 c2 = pow (m2_val, e2, n2) print (f"n2 = {n2} " ) print (f"e2 = {e2} " ) print (f"c2 = {c2} " ) print ("-" * 40 ) print ("--- 第三部分 ---" ) e3 = 3 m3_bits = m3_val.bit_length() p3_q3_bits = 128 if m3_bits * e3 >= p3_q3_bits * 2 - 10 : p3_q3_bits = (m3_bits * e3 // 2 ) + 20 p3 = getPrime(p3_q3_bits) while (p3 - 1 ) % e3 == 0 : p3 = getPrime(p3_q3_bits) q3 = getPrime(p3_q3_bits) while (q3 - 1 ) % e3 == 0 or p3 == q3: q3 = getPrime(p3_q3_bits) n3 = p3 * q3 phi3 = (p3 - 1 ) * (q3 - 1 ) c3 = pow (m3_val, e3, n3) print (f"n3 = {n3} " ) print (f"e3 = {e3} " ) print (f"c3 = {c3} " ) print ("-" * 40 ) print ("--- 第四部分 ---" ) p4_bits = 256 q4_bits = 256 p4 = getPrime(p4_bits) q4 = getPrime(q4_bits) while p4 == q4: q4 = getPrime(q4_bits) n4 = p4 * q4 phi4 = (p4 - 1 ) * (q4 - 1 ) e4a = 65537 e4b = 65539 c4a = pow (m4_val, e4a, n4) c4b = pow (m4_val, e4b, n4) print (f"n4 = {n4} " ) print (f"e4a = {e4a} " ) print (f"c4a = {c4a} " ) print (f"e4b = {e4b} " ) print (f"c4b = {c4b} " ) print ("=" * 40 ) print ("生成完畢。" ) if __name__ == "__main__" : main() ''' --- 第一部分 --- n1 = 6812896682529270617889699041268397231216344502100994418898483090399363050725238802825519610890413646309466494321918636827383749031784541498873387892731639 e1 = 65537 c1 = 4427729071087402462891221302870960264377546560852404414763265602889920597278631371895561554533422266459579128710764143355754615245149034250540901716118396 p1_given = 83018022170775357156881992679804004613671250493281300137495505566721083549673 ---------------------------------------- --- 第二部分 --- n2 = 8618941019390135762450560251440447449812344988348002904674567734387521342905027779518989812368861070593805164745239666403382823700616097172234834567736147 e2 = 65537 c2 = 5090157394401735030895991956180326655655690673641213577889910602055845449426923727333236685488219458241927620516575355892867356153466992699239192192910803 ---------------------------------------- --- 第三部分 --- n3 = 44935859354785283479720490973543160302824014776763758544522532443340696020267 e3 = 3 c3 = 345422409558921105091064923418692102360936093114398968000 ---------------------------------------- --- 第四部分 --- n4 = 8050202063335318202668477773676061807230884209991655693527143039730083343444420055444708024772406517257344636757261685775610919720030730312364281795306843 e4a = 65537 c4a = 5944697746898769084130690069563137465626689325180948580645355816012208942196895961186706314322689146225405184339425445878469418993890870252122256787094490 e4b = 65539 c4b = 590873621149745423995166880880817186889129377479311590030588253033344142558245476231076545393071246375504750217939956792516706707037717951120503693278372 ======================================== '''
第一部分有了p直接算就行
第二部分p和q十分接近,所以可以通过开根去nextprime挨个试
第三部分低指数幂攻击
第四部分共模攻击
exp:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 from Crypto.Util.number import *import gmpy2n1 = 6812896682529270617889699041268397231216344502100994418898483090399363050725238802825519610890413646309466494321918636827383749031784541498873387892731639 e1 = 65537 c1 = 4427729071087402462891221302870960264377546560852404414763265602889920597278631371895561554533422266459579128710764143355754615245149034250540901716118396 p1 = 83018022170775357156881992679804004613671250493281300137495505566721083549673 q1=n1//p1 phi1=(p1-1 )*(q1-1 ) d1=gmpy2.invert(65537 ,phi1) m1=long_to_bytes(pow (c1,d1,n1)) n2 = 8618941019390135762450560251440447449812344988348002904674567734387521342905027779518989812368861070593805164745239666403382823700616097172234834567736147 e2 = 65537 c2 = 5090157394401735030895991956180326655655690673641213577889910602055845449426923727333236685488219458241927620516575355892867356153466992699239192192910803 tmp2=gmpy2.iroot(n2,2 )[0 ] while n2%tmp2 !=0 : tmp2=gmpy2.next_prime(tmp2) p2=n2//tmp2 q2=tmp2 phi2=(p2-1 )*(q2-1 ) d2=gmpy2.invert(65537 ,phi2) m2=long_to_bytes(pow (c2,d2,n2)) n3 = 44935859354785283479720490973543160302824014776763758544522532443340696020267 e3 = 3 c3 = 345422409558921105091064923418692102360936093114398968000 k=0 while True : mm=c3+n3*k m3,flag=gmpy2.iroot(mm,e3) if True ==flag: break k+=1 m3=long_to_bytes(m3) n4 = 8050202063335318202668477773676061807230884209991655693527143039730083343444420055444708024772406517257344636757261685775610919720030730312364281795306843 e4a = 65537 c4a = 5944697746898769084130690069563137465626689325180948580645355816012208942196895961186706314322689146225405184339425445878469418993890870252122256787094490 e4b = 65539 c4b = 590873621149745423995166880880817186889129377479311590030588253033344142558245476231076545393071246375504750217939956792516706707037717951120503693278372 _gcd,s1,s2=gmpy2.gcdext(e4a,e4b) m4=long_to_bytes(pow (c4a,s1,n4)*pow (c4b,s2,n4)%n4) print (m1+m2+m3+m4)
OSINT
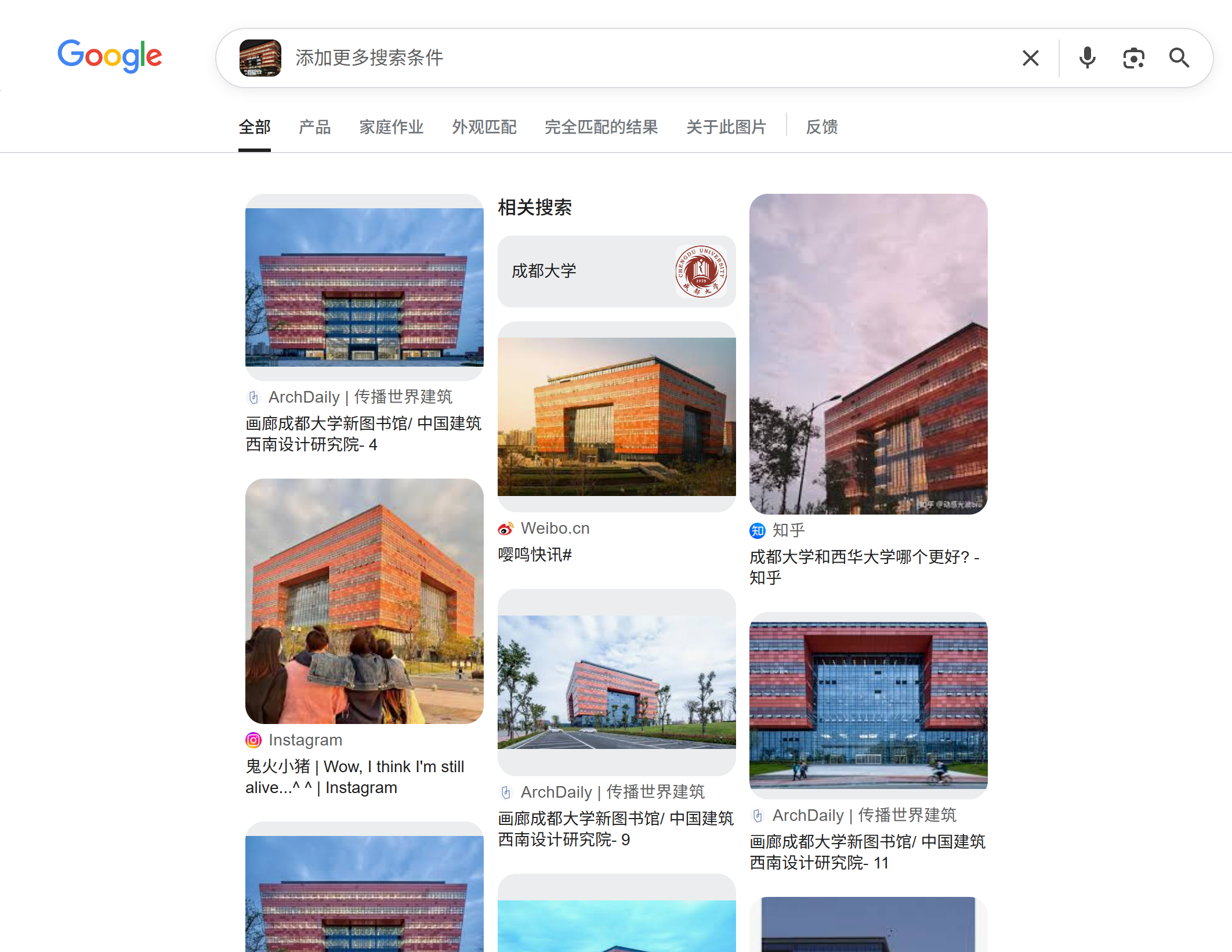
ez-college
一搜就是成都大学
image-20250713191236972
Forensics
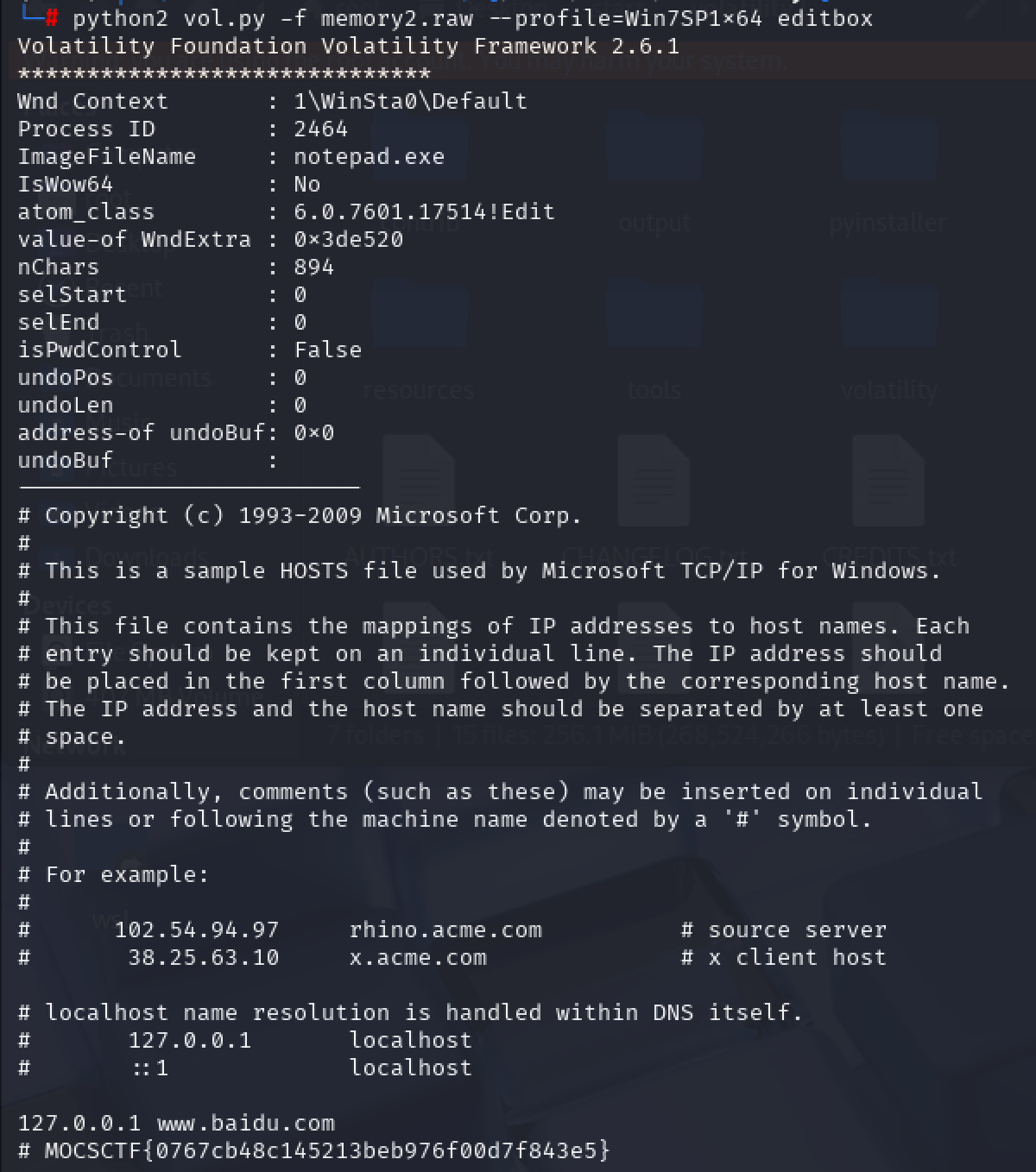
easymem
在查看记事本的时候就发现了flag(
image-20250713191440783
easysword
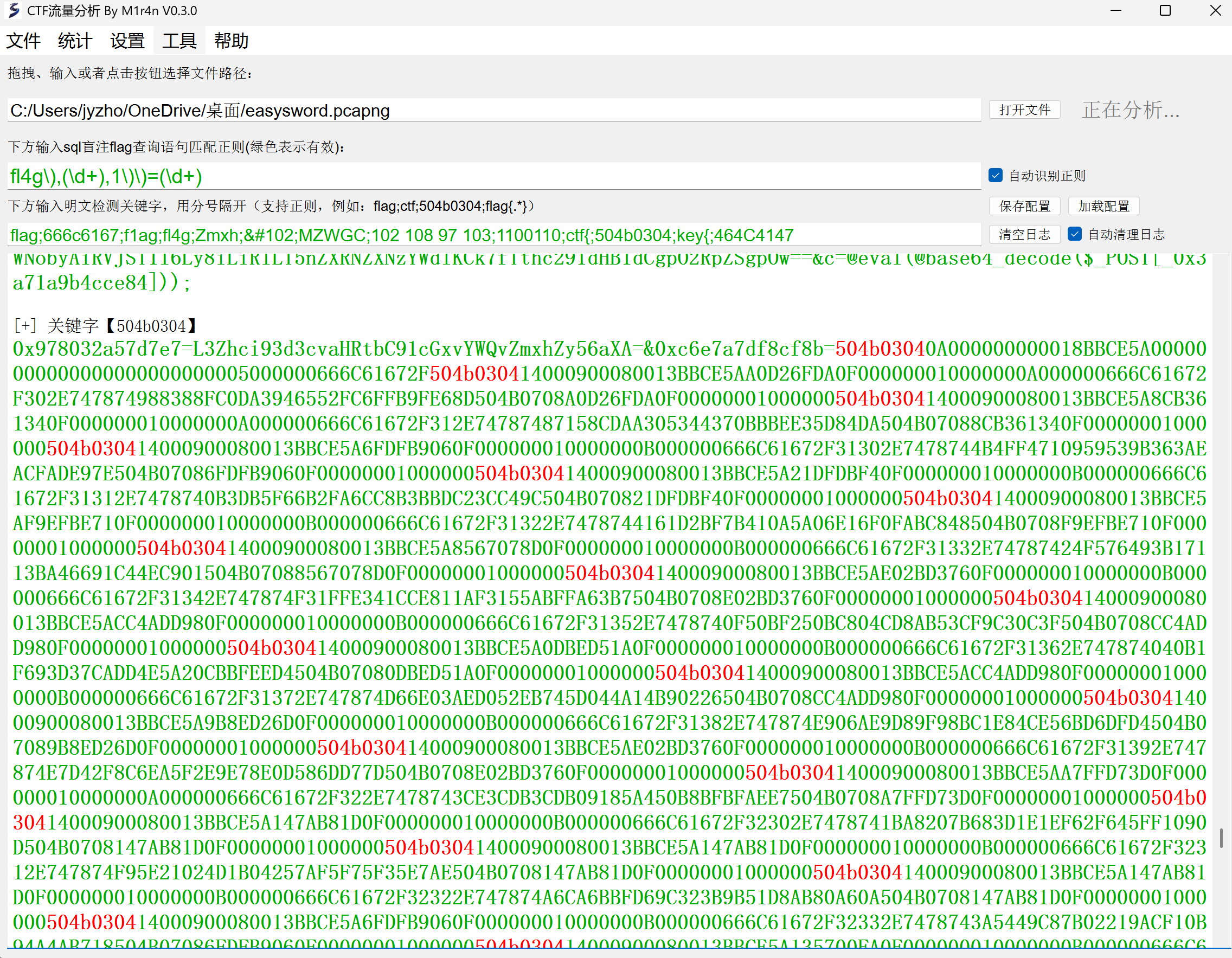
看题目名字就盲猜某webshell工具流量,直接丢给Net-A梭一下看,找到有个压缩包
image-20250713191704829
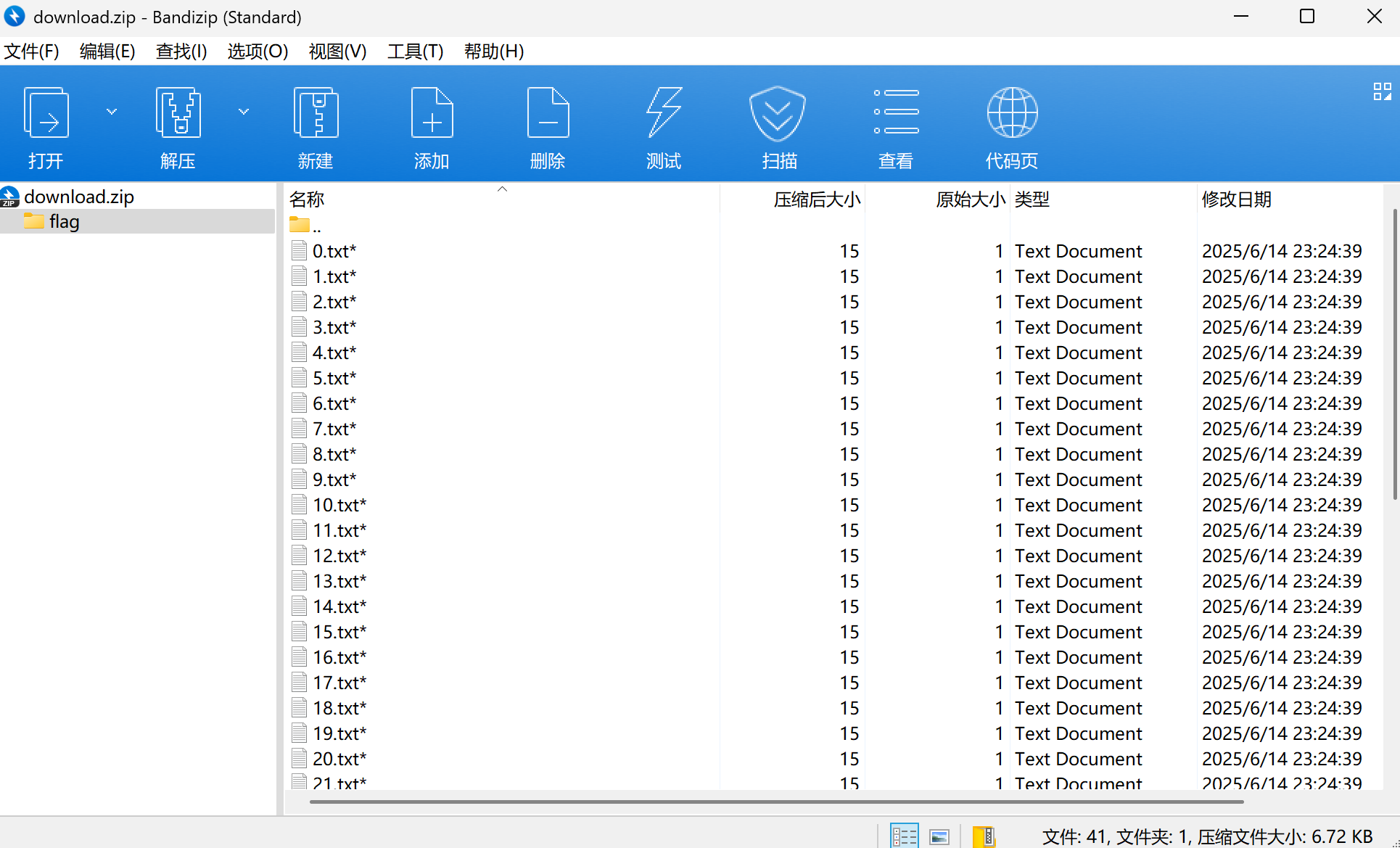
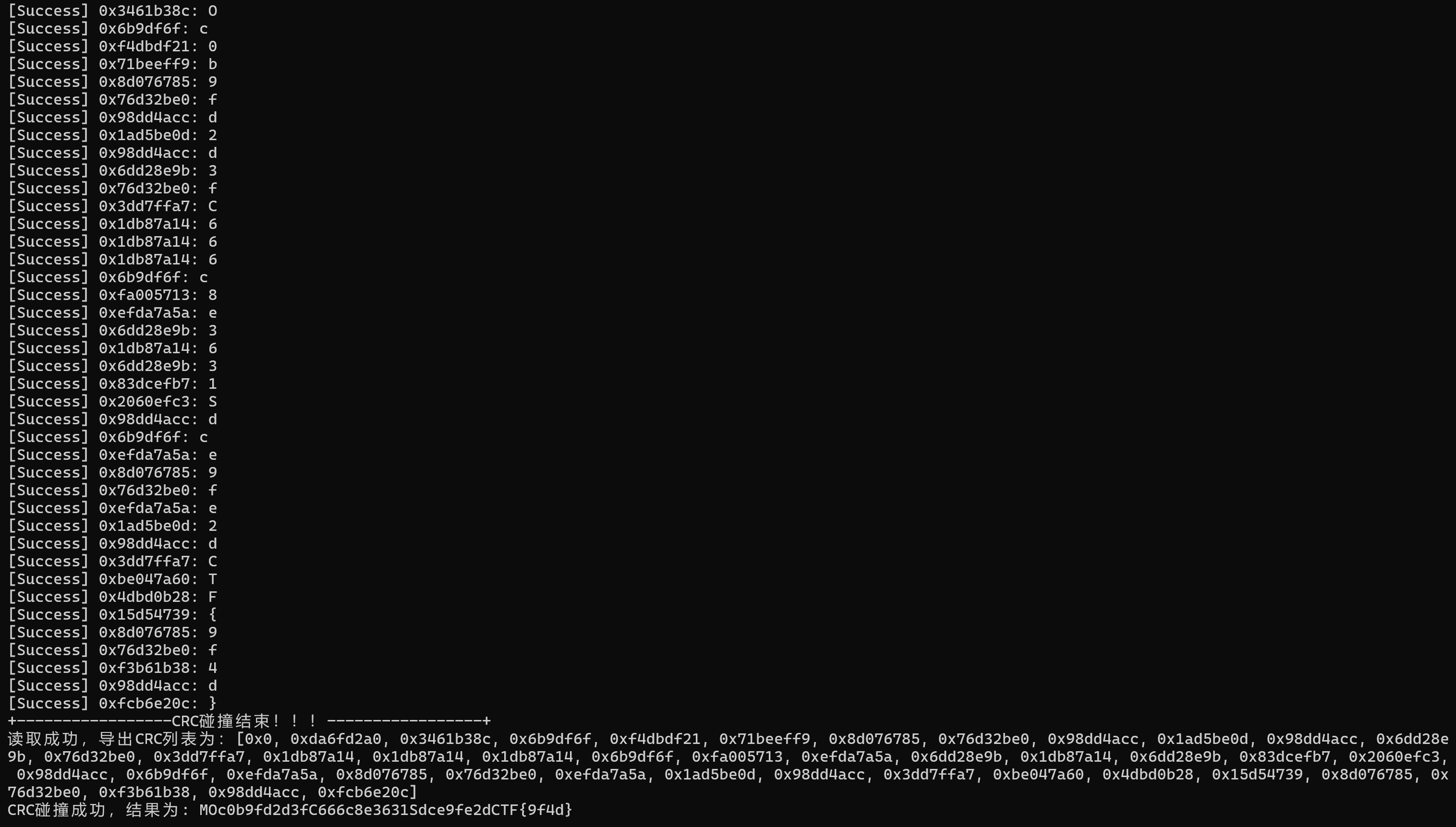
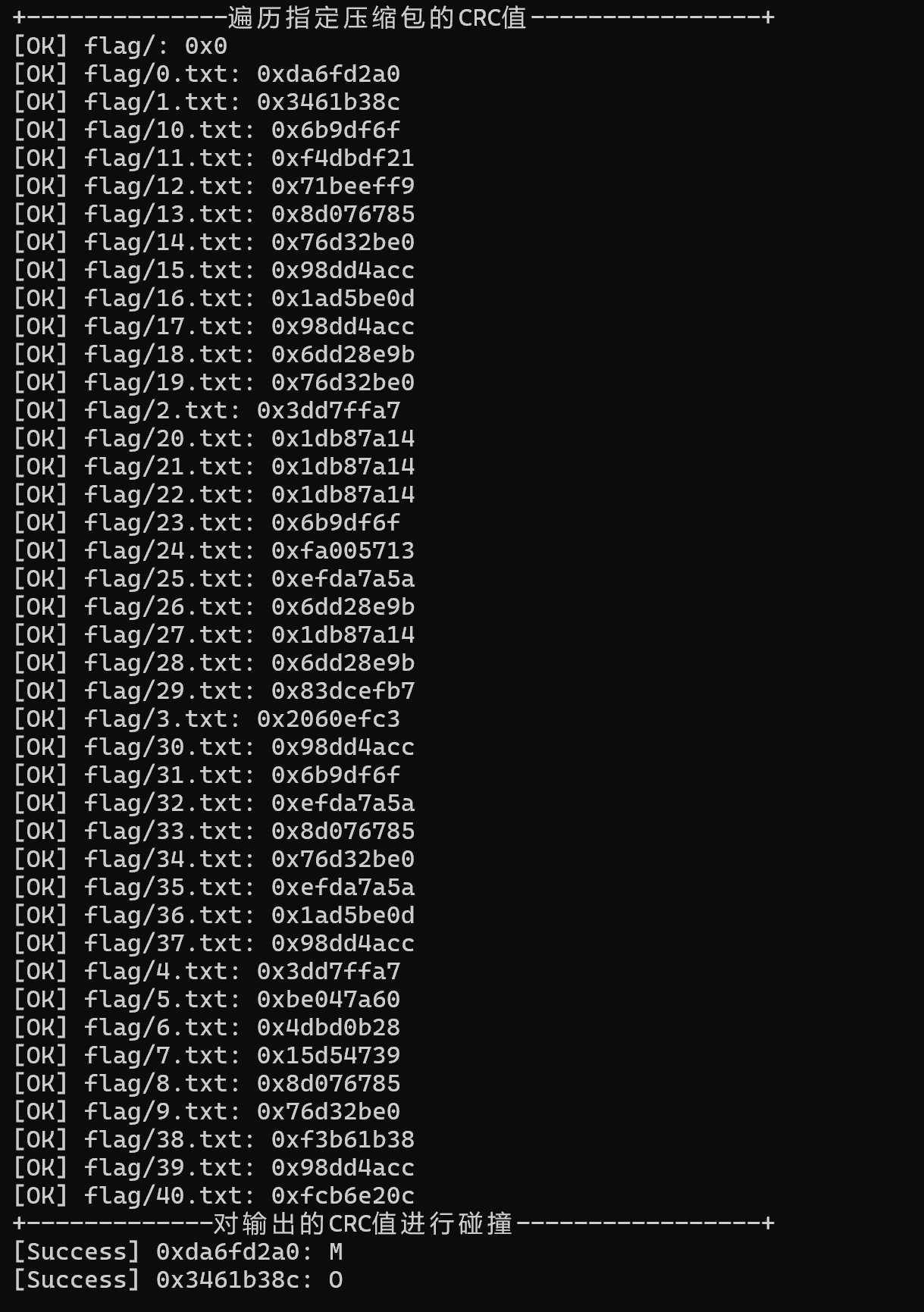
里面的文件都特别小,所以爆破CRC
image-20250713191811263
image-20250713191903694
注意他是按这个顺序排的,得记得换回来(
image-20250713191938726
MOCSCTF{9fc0b9fd2d3f666c8e3631dce9fe2d4d}