VNCTF2025 Writeup
其他的没看,就看了misc的取证看了一天没做出来,看了wp发现思路是对的,but yes,又是差那么一点点。。。
Writeup部分
Misc
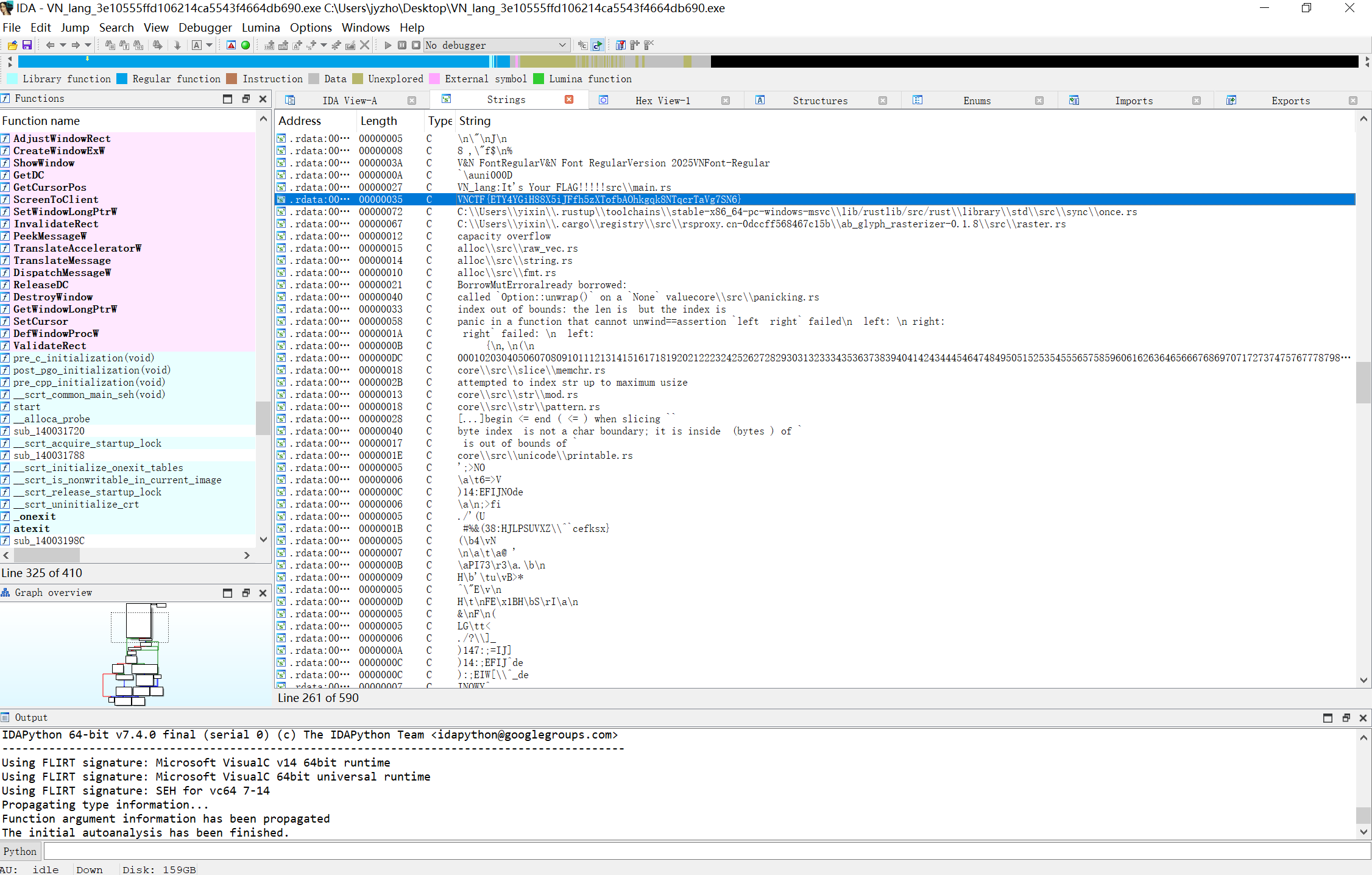
VN_Lang
丢进IDA就能看到flag
Crypto
easymath
题目
1 | from Crypto.Util.number import * |
exp
1 | from libnum import n2s |
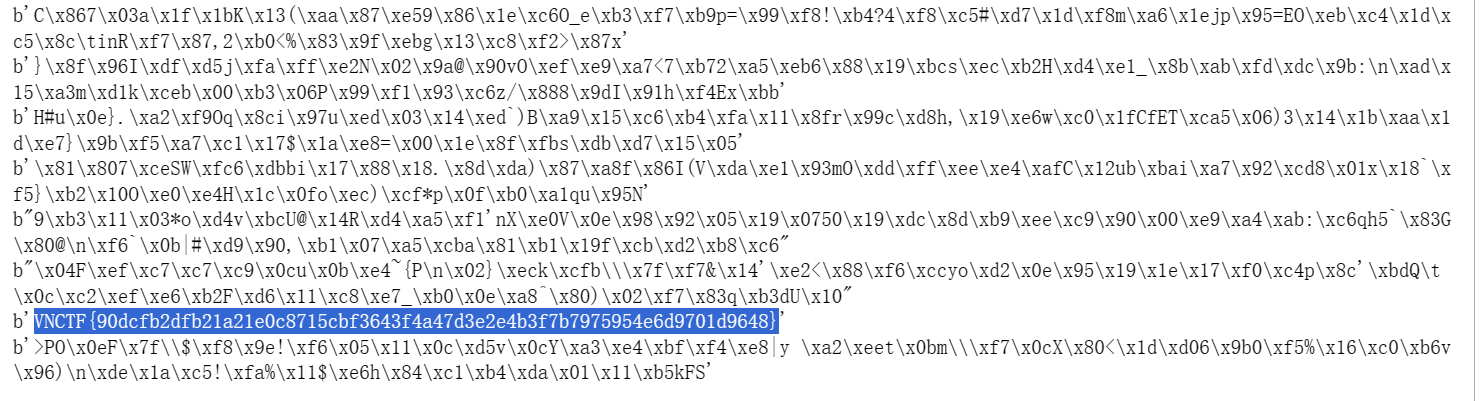
ss0Hurt!
题目
1 | from Crypto.Util.number import * |
丢给ai一把梭了
1 | from Crypto.Util.number import inverse, long_to_bytes |
复现部分
echo_flowers
imToken这个软件没有漏洞,因此是无法得知私钥的。在软件中可以看到账号是通过助记词导入的,因此猜测恢复助记词方法与输入法有关。
在android-7.1- r5/data/data/com.sohu.inputmethod.sogouoem/files/dict中找到词库
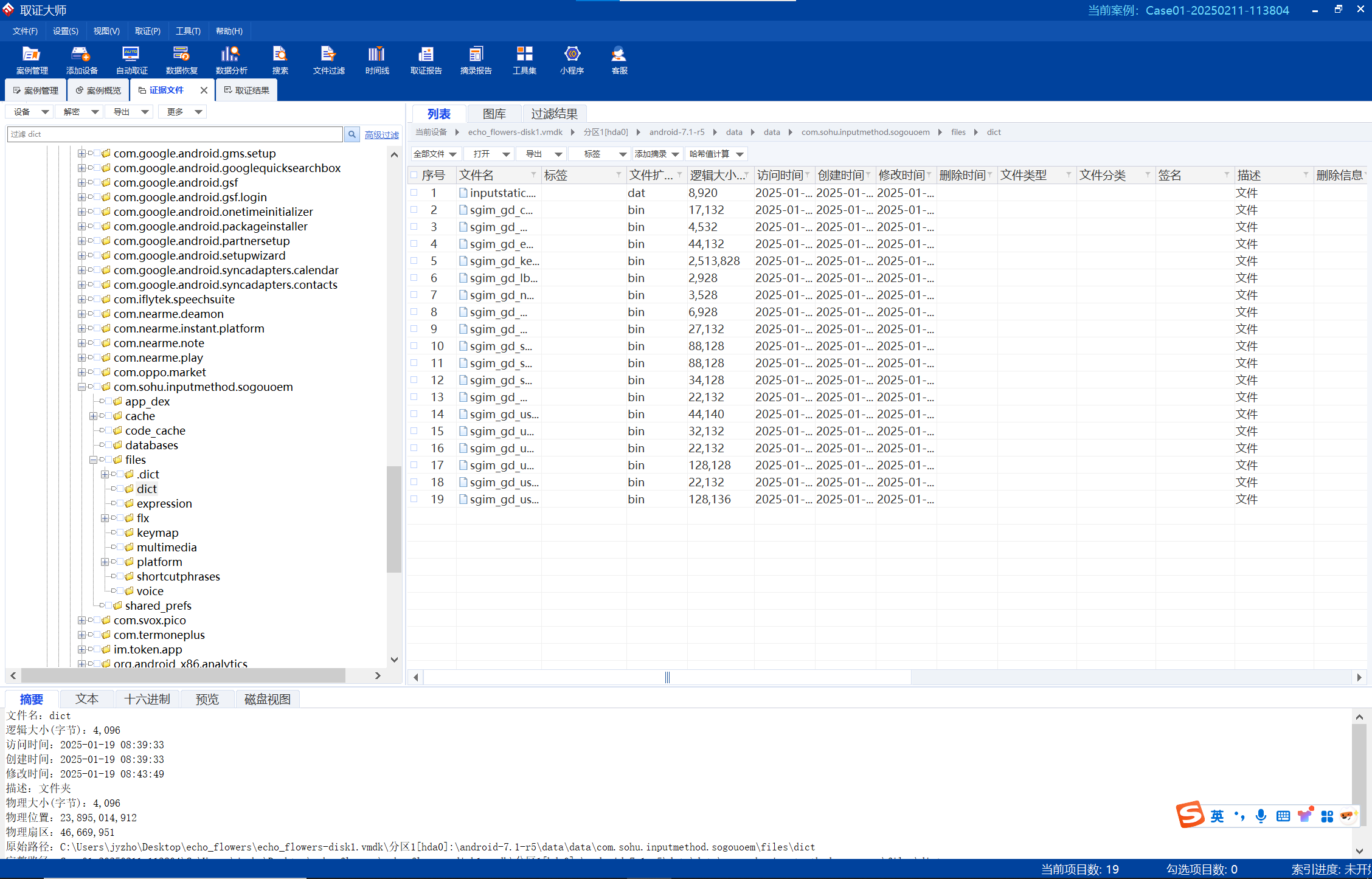
词库中字符是以utf-16编码存储的,用strings解一下得到助记词
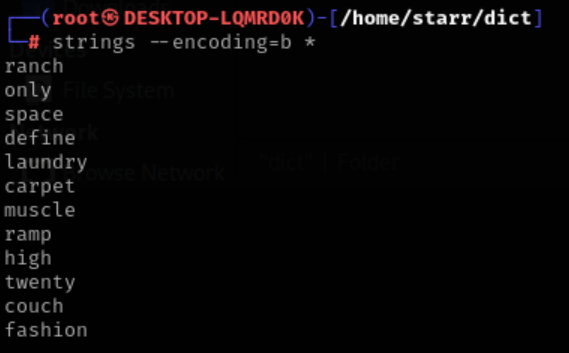
正常进imToken导入一遍助记词即可创建钱包设置密码查看私钥
VNCTF{6433c196bb66b0d8ce3aa072d794822fd87edfbc3a30e2f2335a3fb437eb3cda}
All articles in this blog are licensed under CC BY-NC-SA 4.0 unless stating additionally.
Comment