西湖论剑2025 Misc Writeup+复现
Writeup
糟糕的磁盘
取证大师一下子导入五个镜像即可,可以看到key和secret
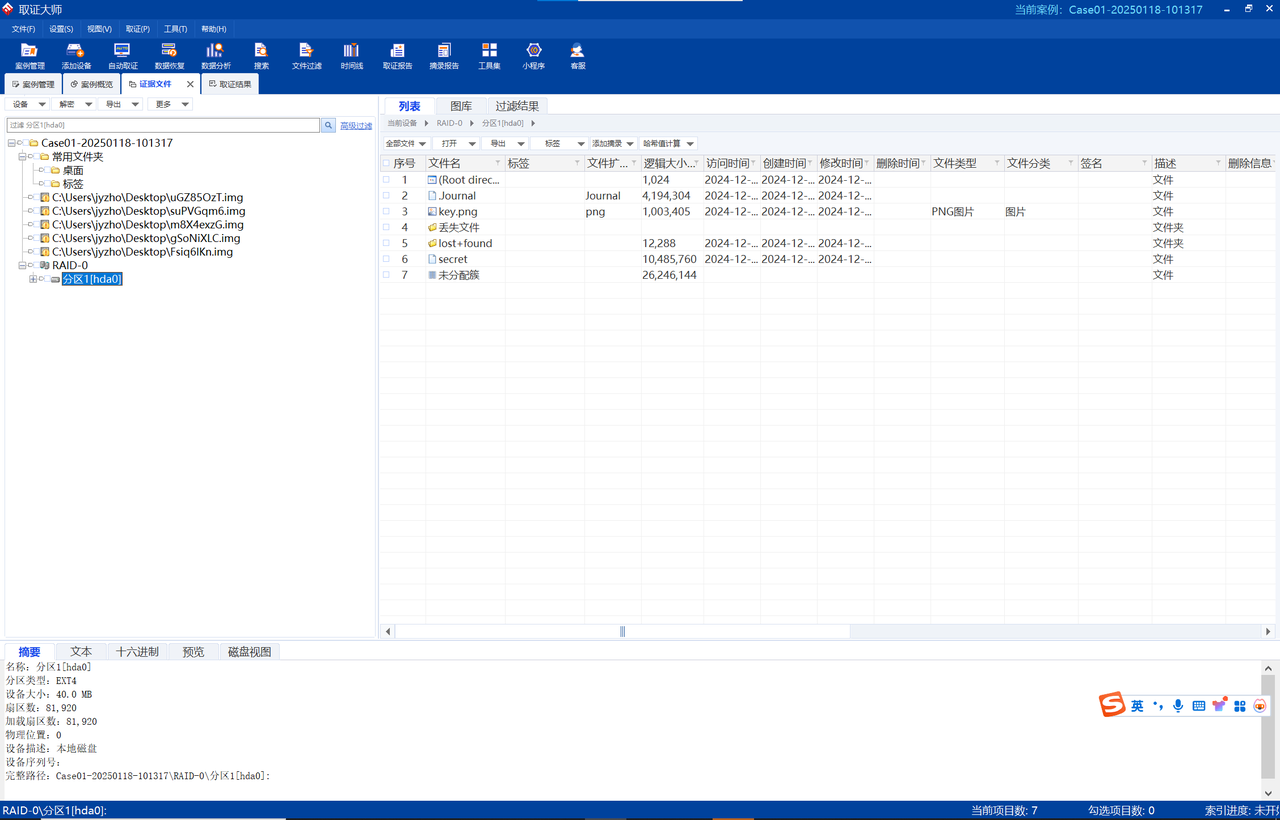
veracrypt挂载一下,key.png当做密钥文件

复现
CSCS
挺逆天的题目,当时比赛的时候是零解。本来前阵子我为了出题专门研究过CS流量,结果这个题中没直接给私钥,也不是已知私钥,也没给镜像什么的,当时就直接给我干懵了。谁知道他这里是要用密码学自己去分解得到私钥。。。不过手撕pem什么的操作我倒是也会。。。好吧还是我菜了:(
可以看到给出了http beacon
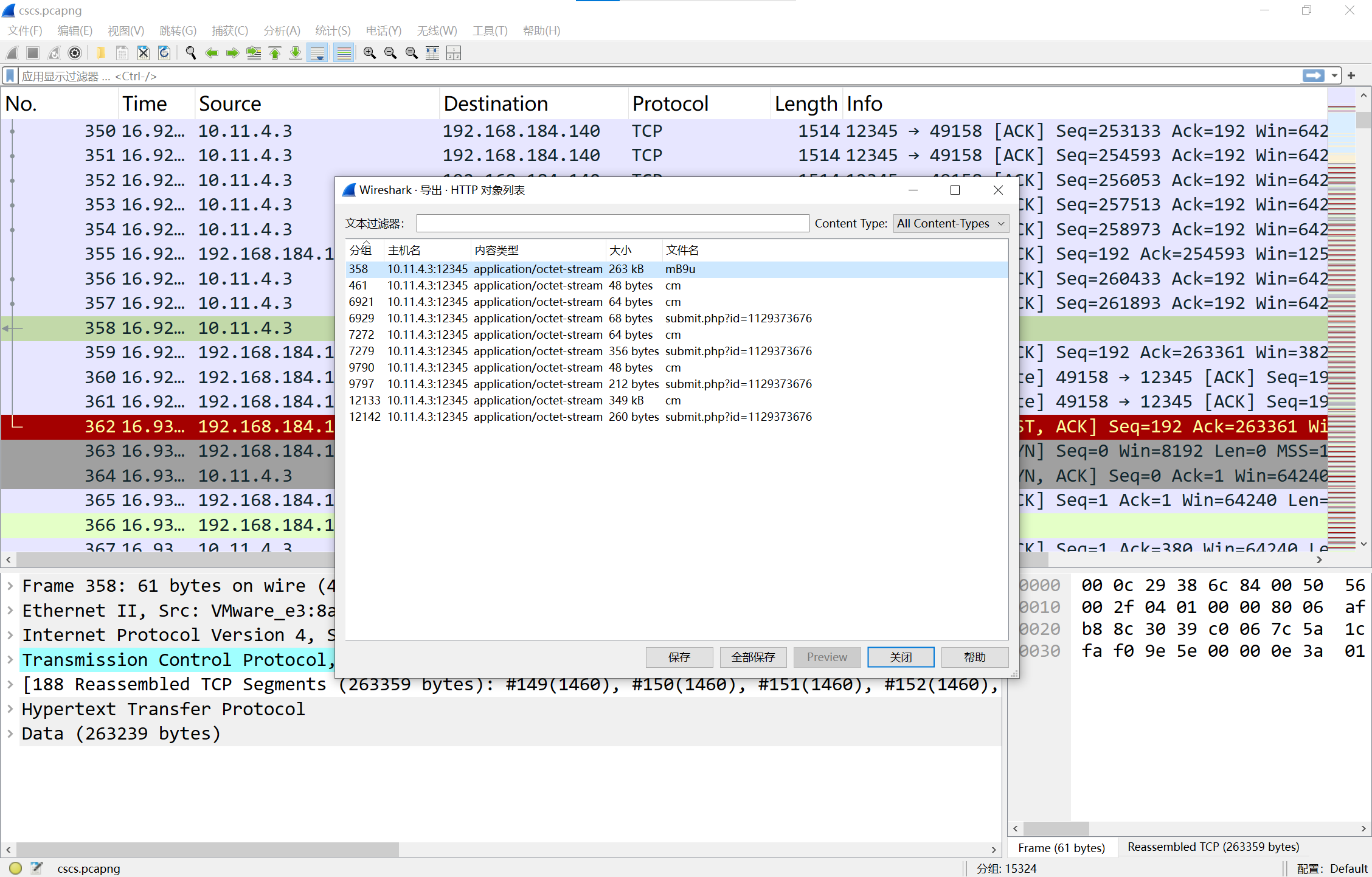
用1768.py可以拿到公钥
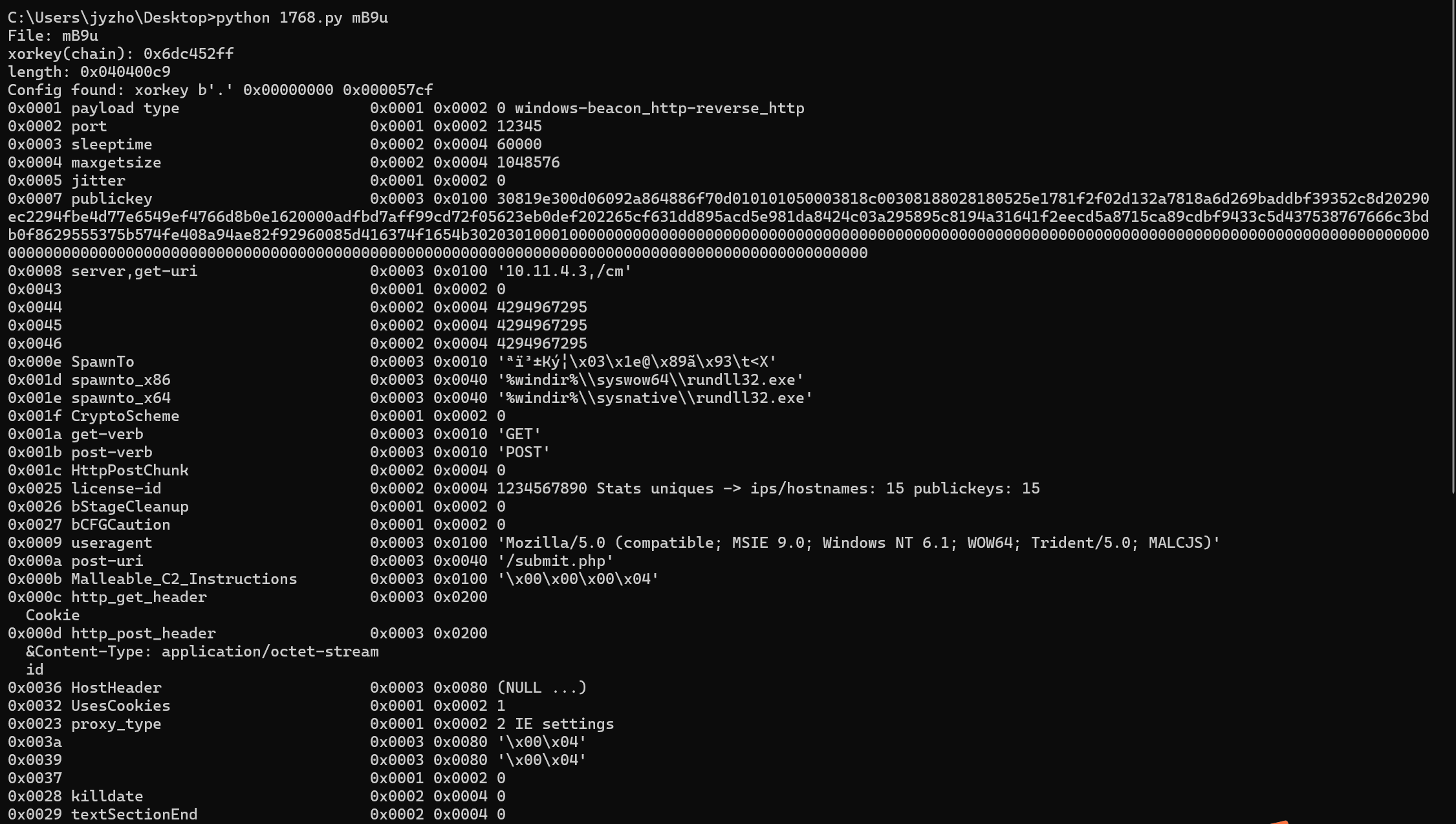
当时就是停在这了,根本没想到这个公钥可以分解。。。
把这串十六进制数做成pem格式,拿到n
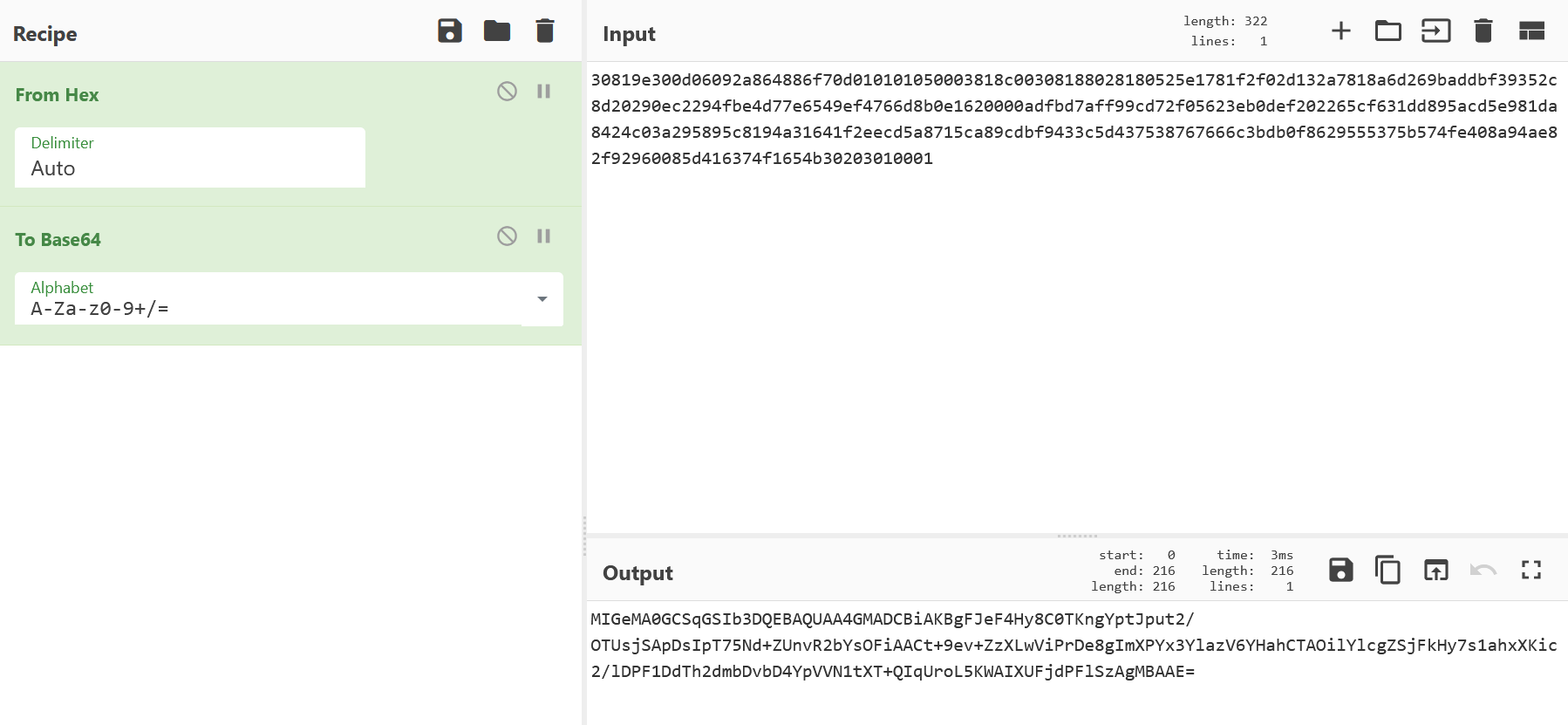
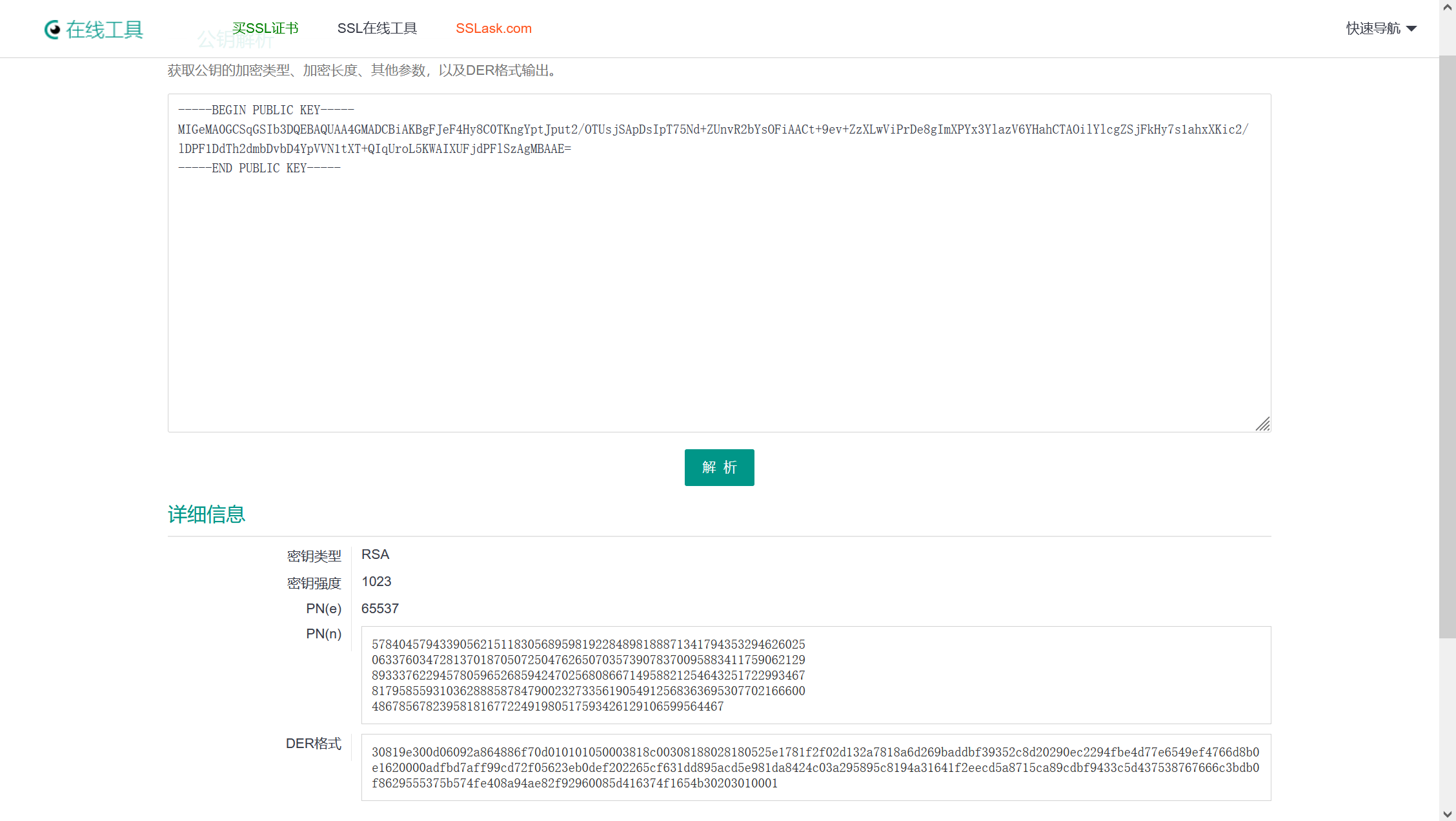
这n可以直接用yafu分解。。。
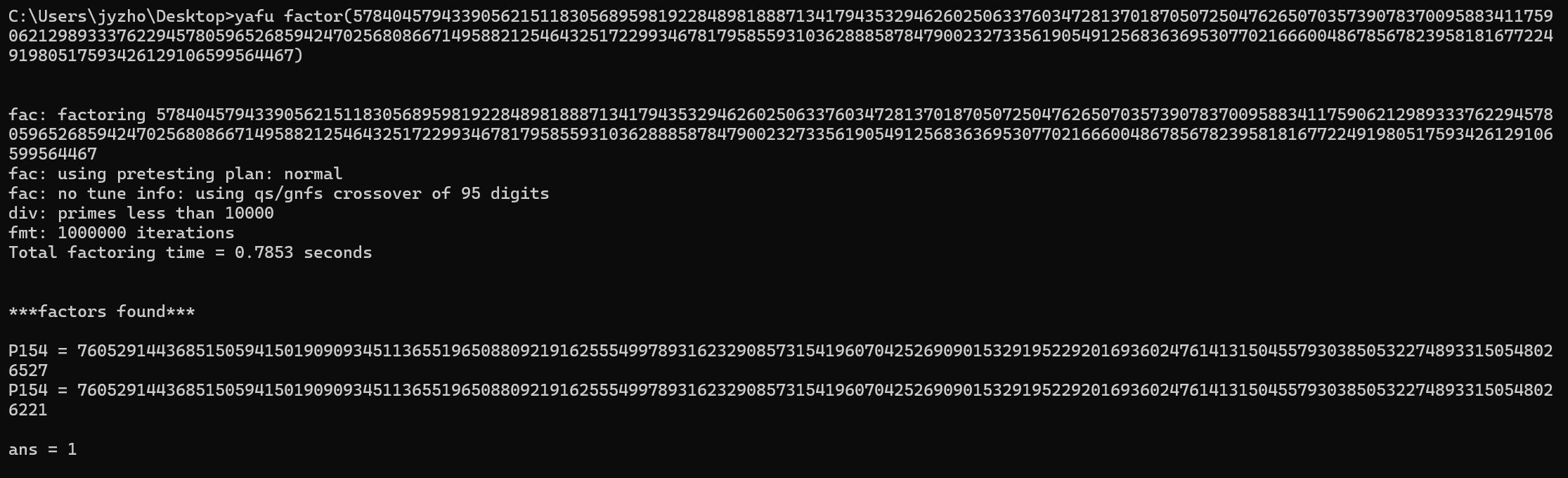
然后做成pem格式的私钥文件
1 | from cryptography.hazmat.primitives.asymmetric import rsa |
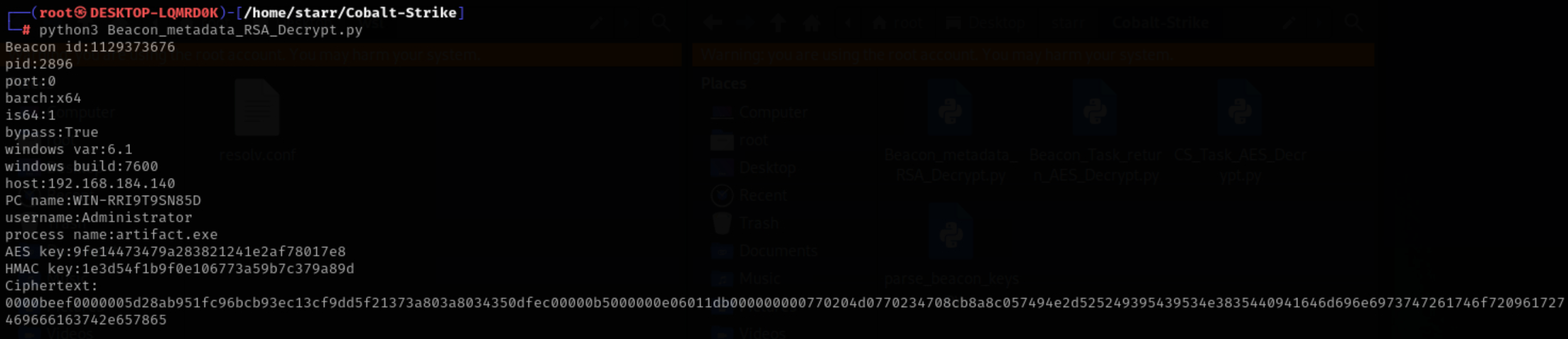
接下来就是经典的解密cs流量
先找到cookie,拿到AES key和HMAC key
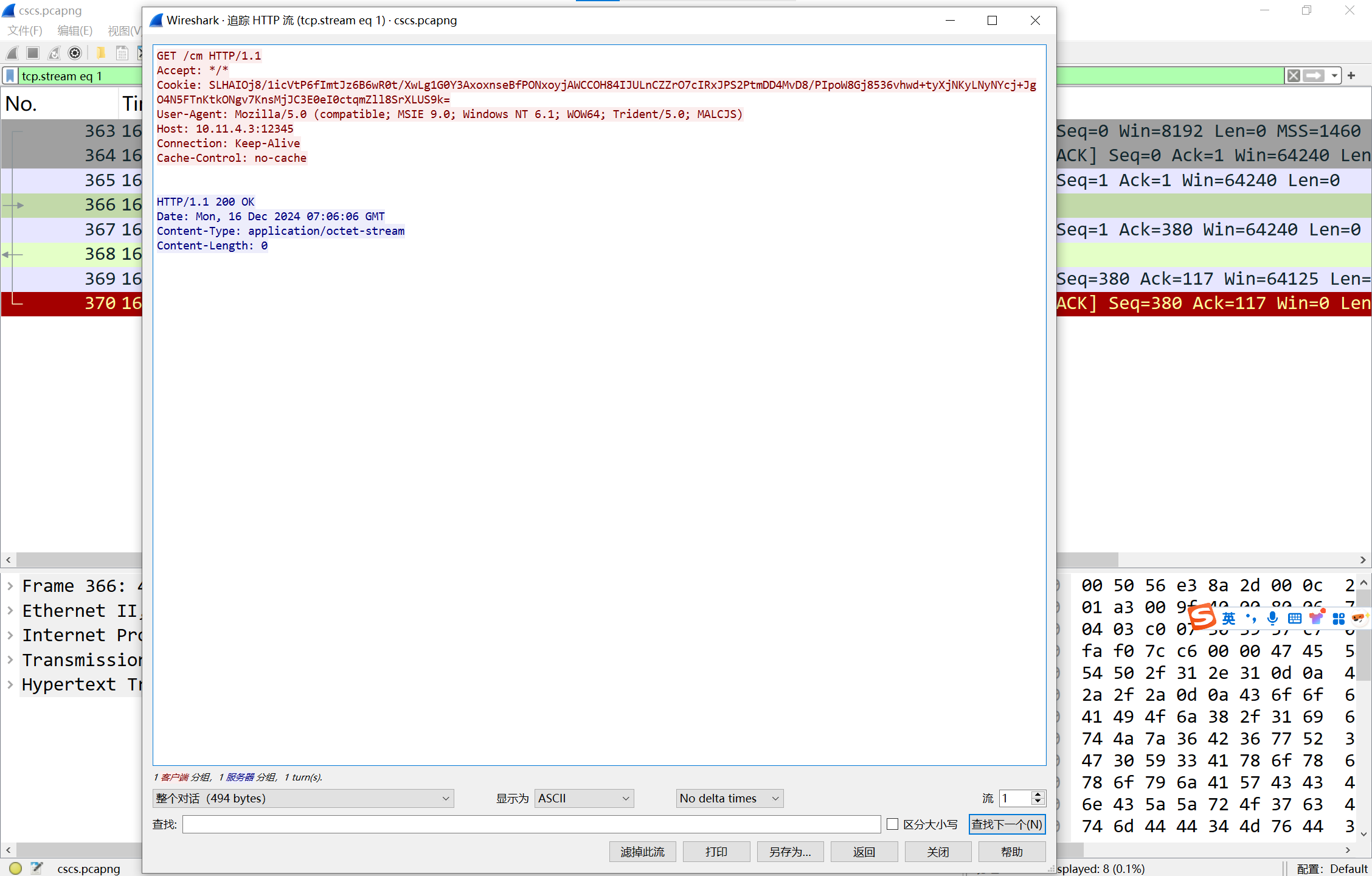
1 | import base64 |
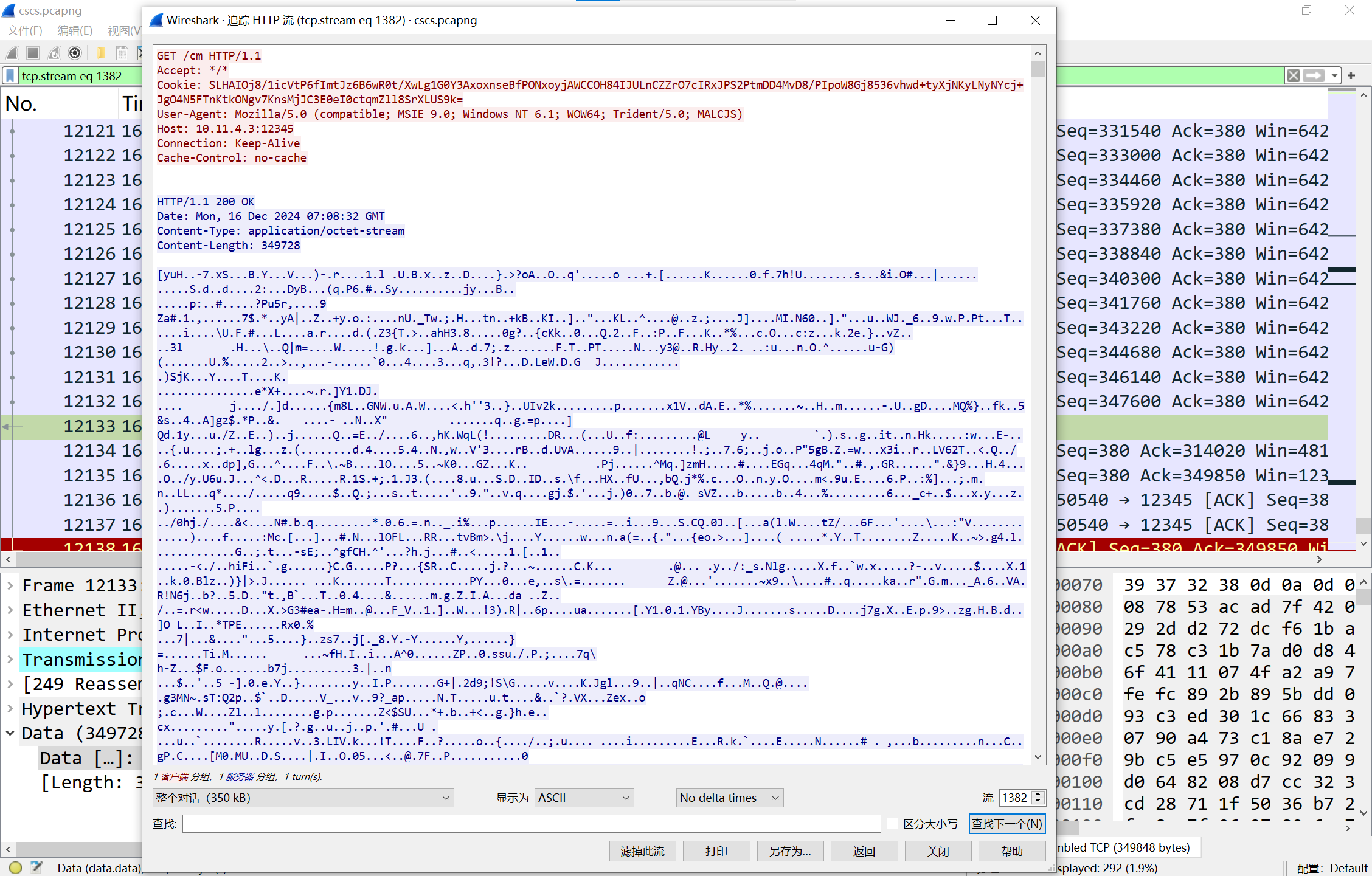
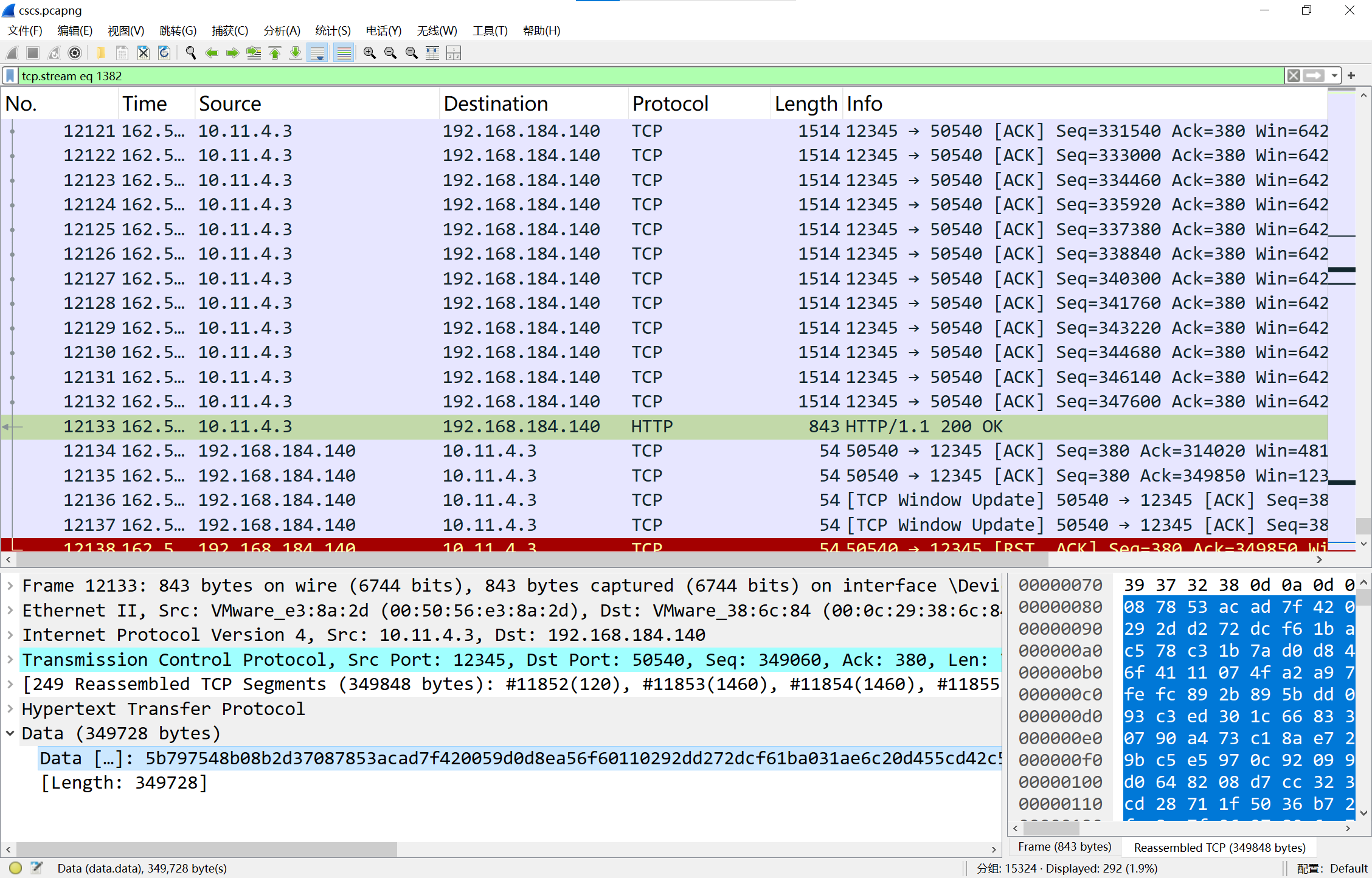
在流1382处传了一个流量包,提取出来
1 | import hmac |
打开流量包,发现里面全都是27015端口在通讯,查询可知这是游戏cs1.6的流量包
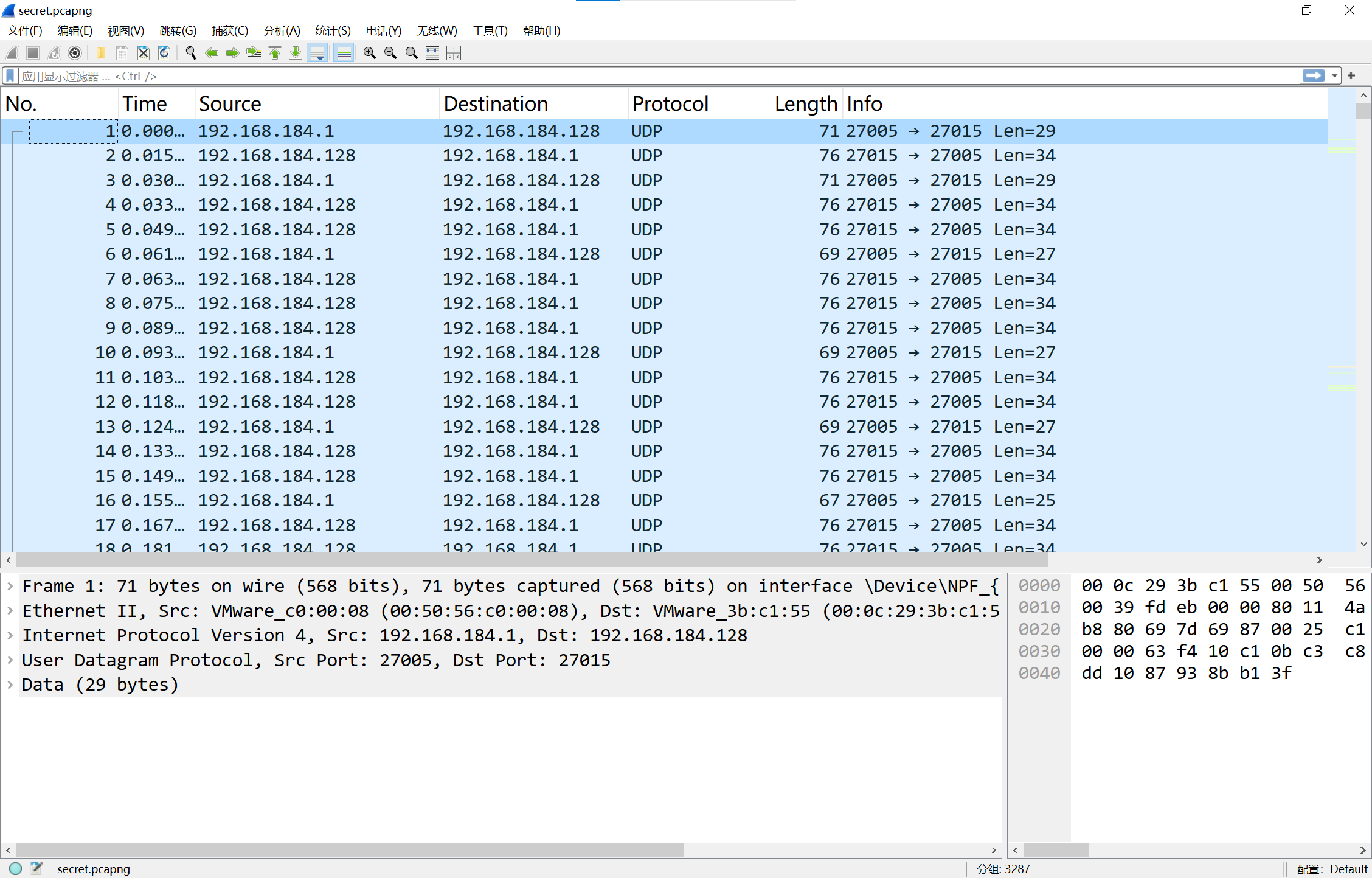
接下来根据这篇文章来解密
将下面这个cpp文件编译成so文件
1 | extern "C" |
1 | g++ -fPIC -shared -o dll.so 1.cpp |
然后用下面的程序加载编译出的dll.so解密流量
1 | # -*- coding: UTF-8 -*- |
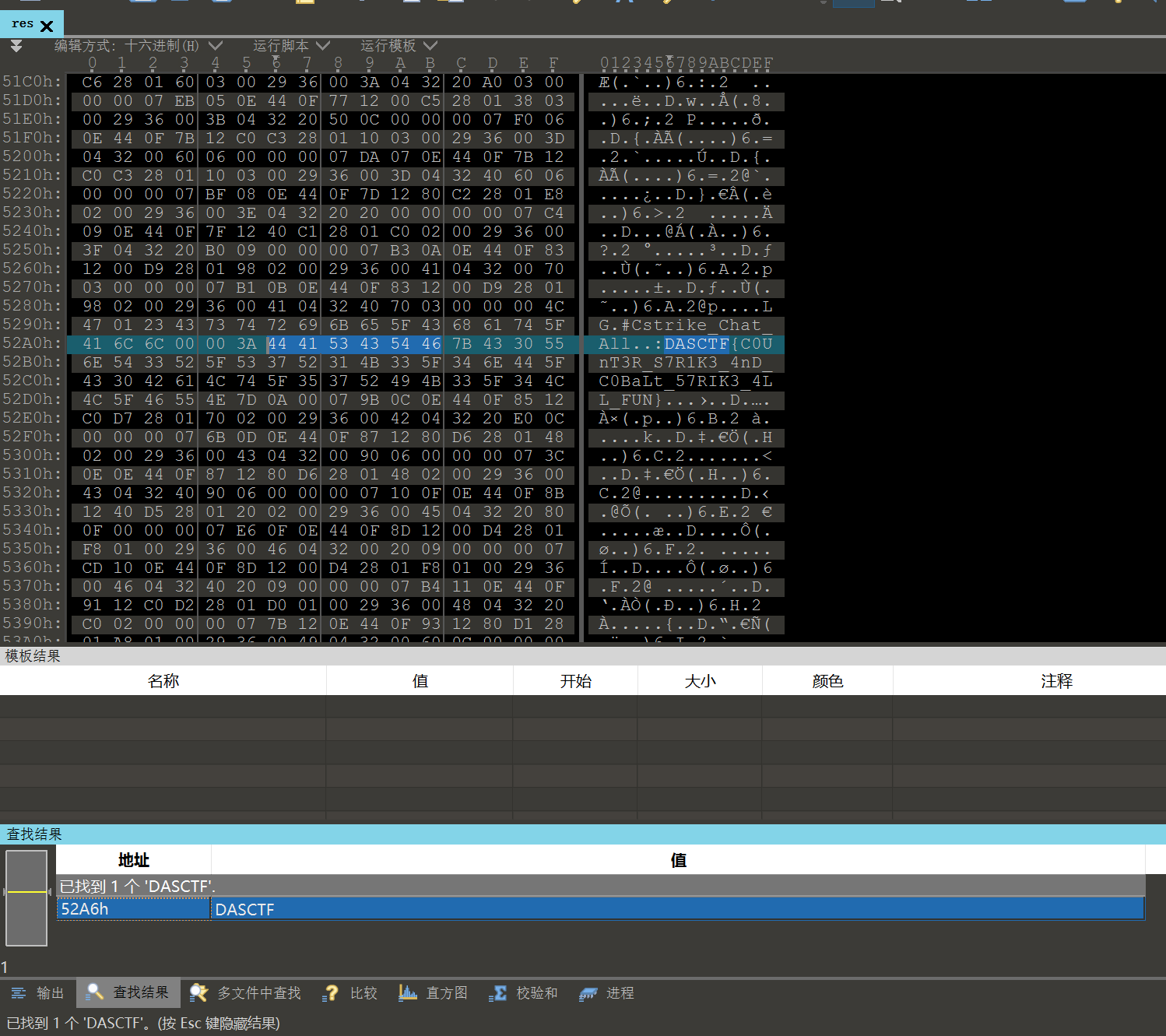
在得到的res文件中搜索不难找到flag
All articles in this blog are licensed under CC BY-NC-SA 4.0 unless stating additionally.
Comment