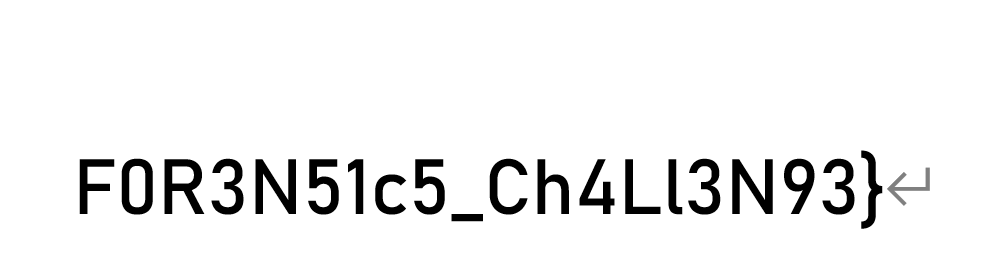这次跟校队的几位同届的大师傅一起打的,师傅们都很强,又是被师傅们带着冲的一集。可惜我们缺个pwn手,这次的pwn从解题人数来看应该不难,但是我们一题都没做。。。
Writeup部分
复现部分
不懂的还是太多了,好好复现一下吧。
Misc
Just_F0r3n51Cs
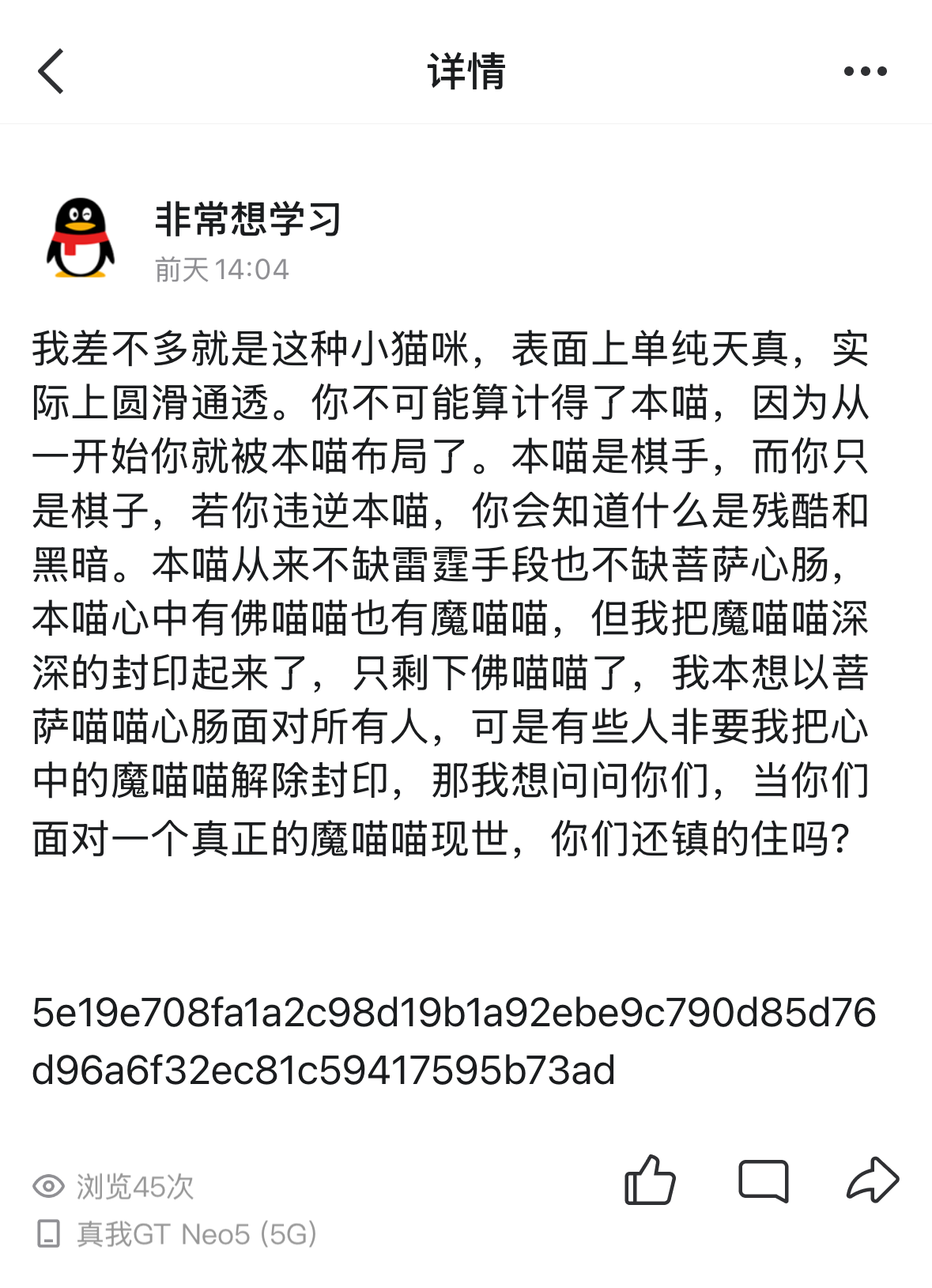
这题当时是找到了第三第四个flag,第一个flag找到了密钥但是没找到密文。
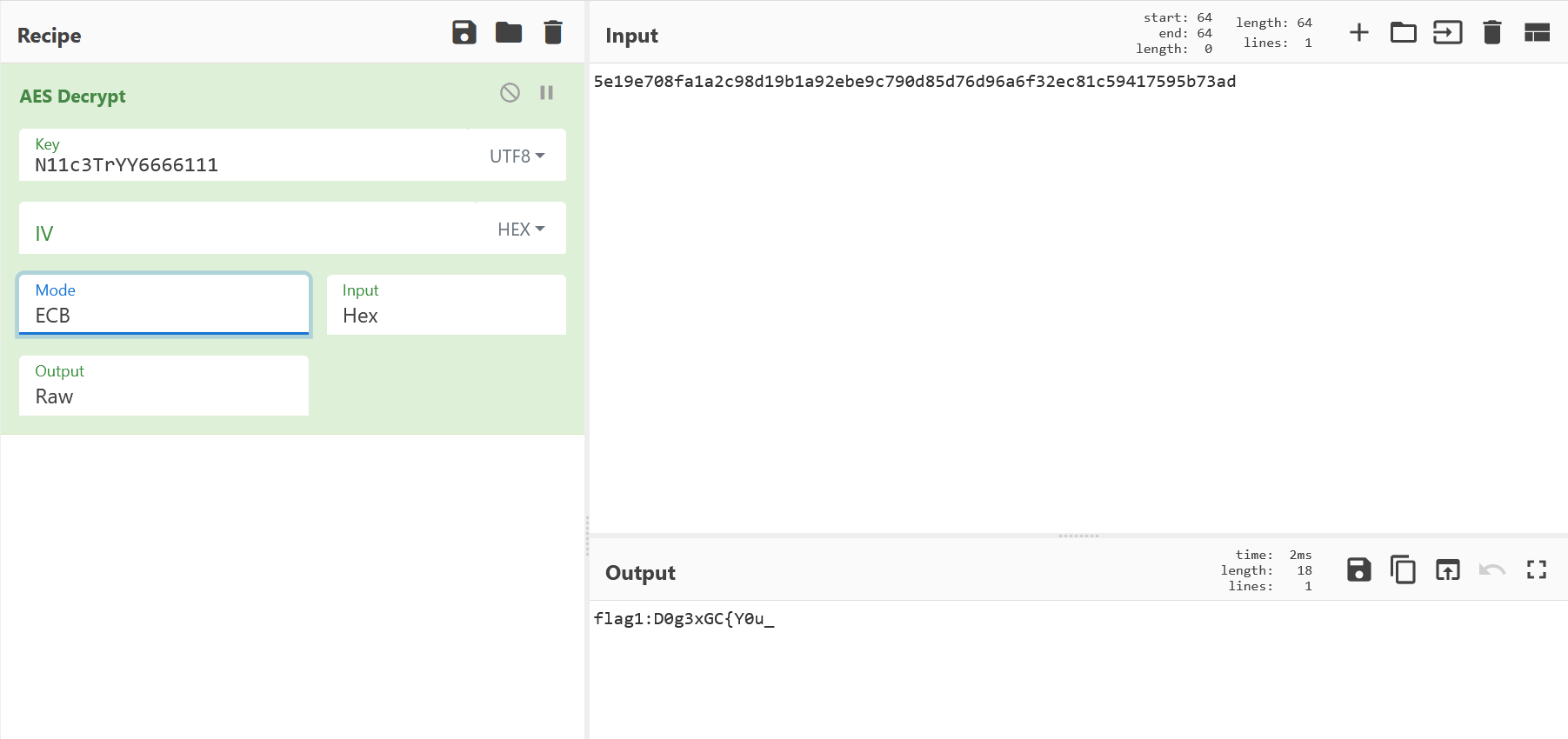
flag1
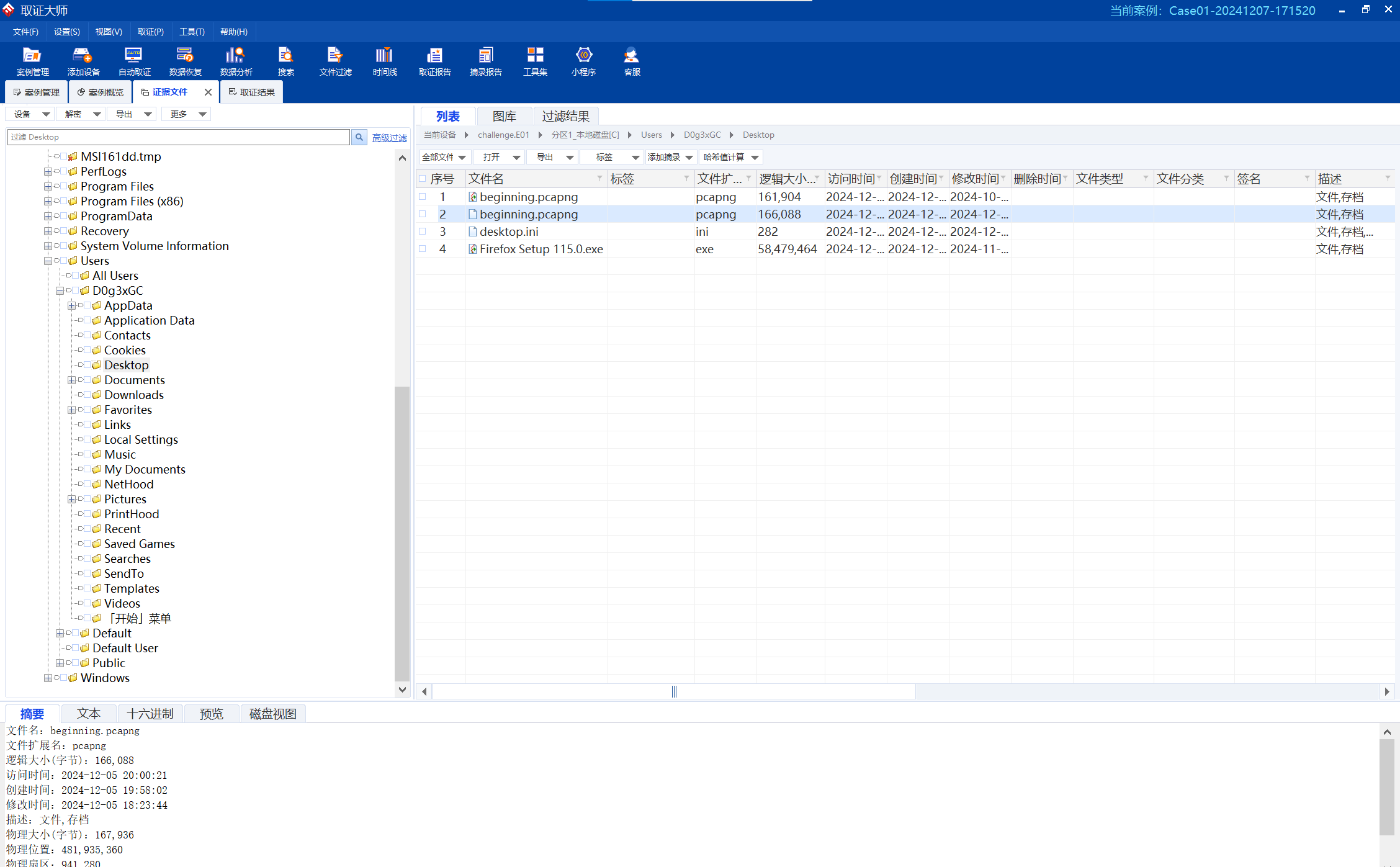
在桌面上可以找到beginning.pcapng
image-20241207185904257
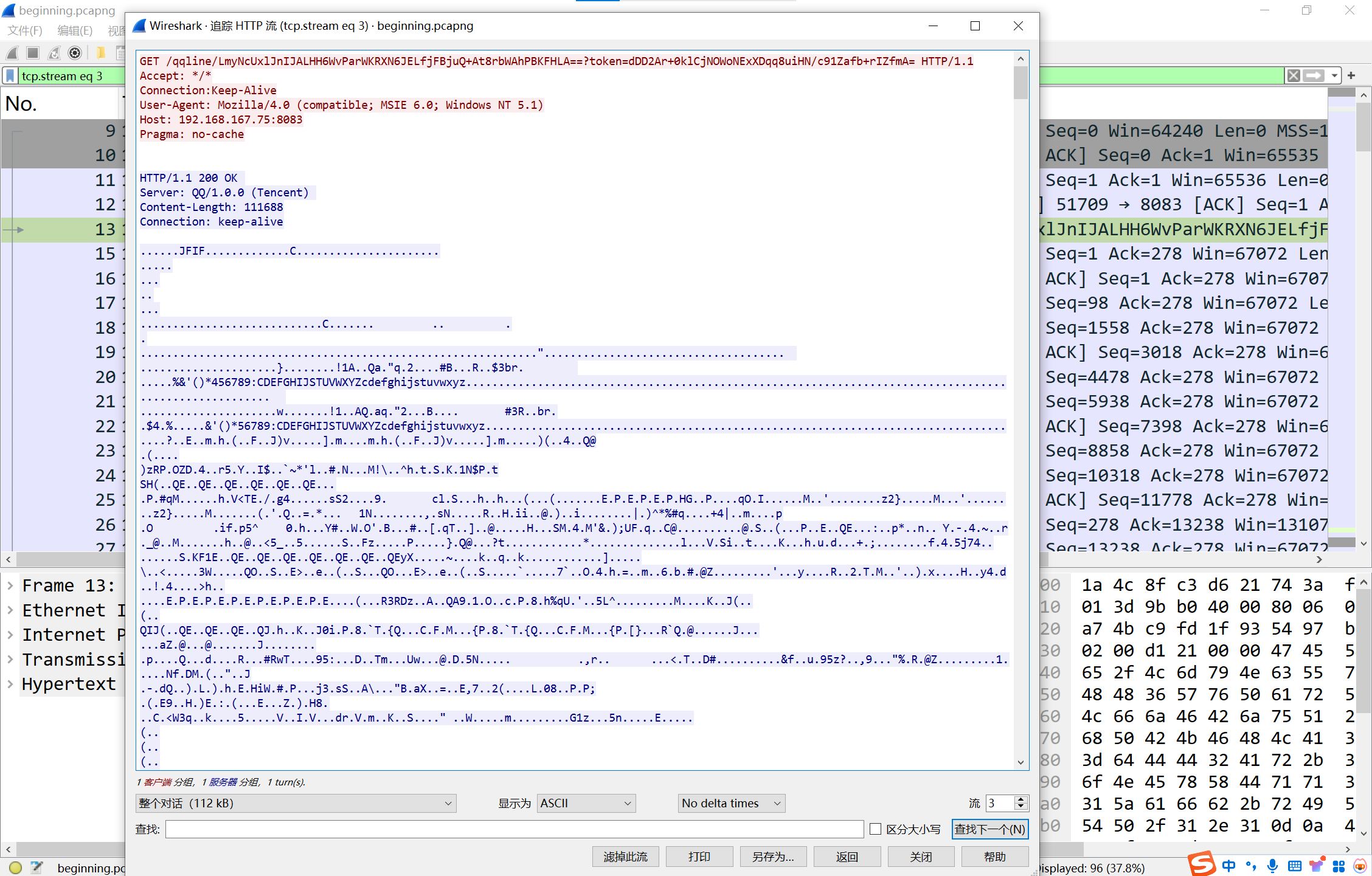
追踪一下http流可以看到传输了一张jpg图片,保存下来
image-20241207190018698
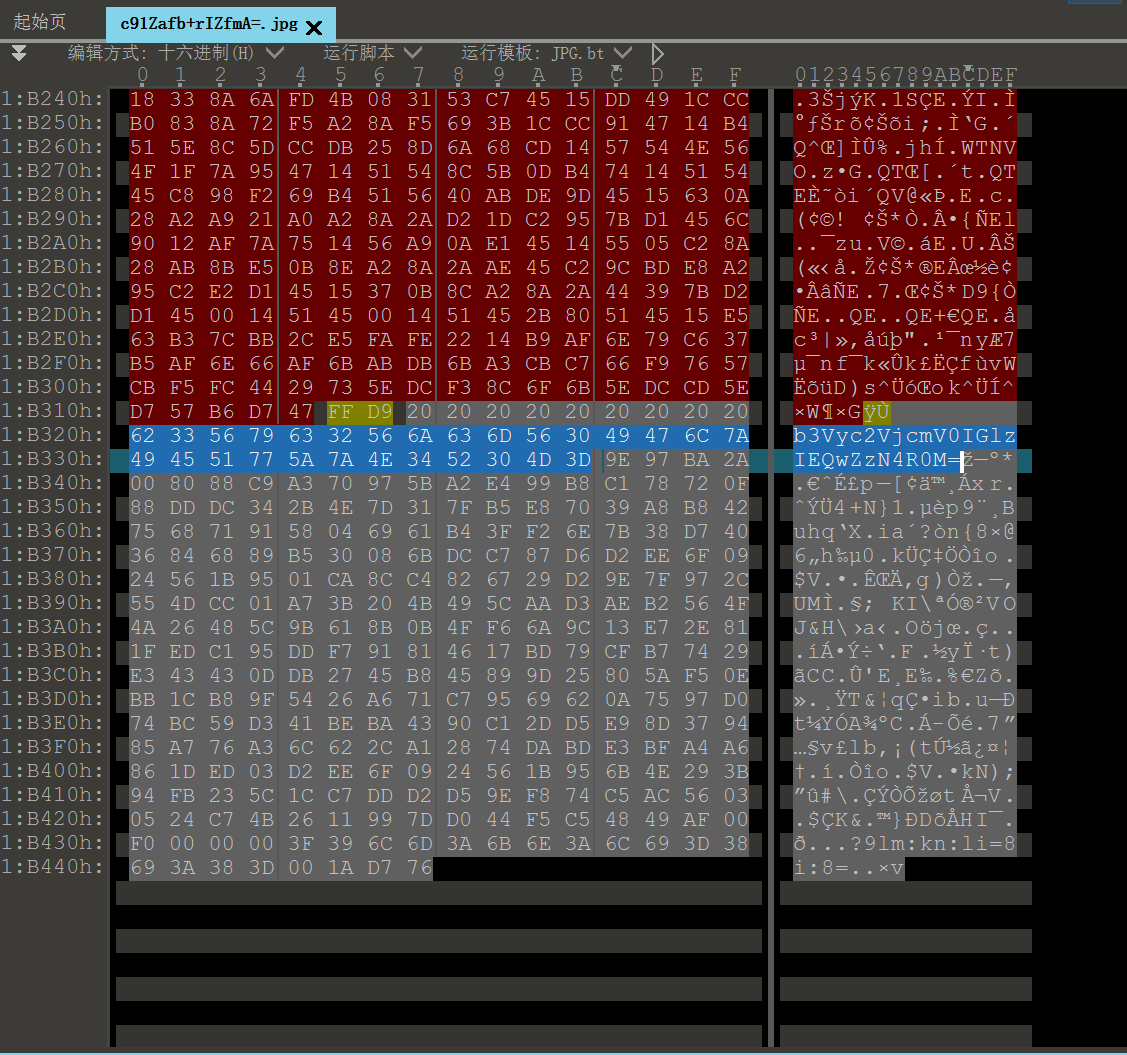
图片结尾有一串base64
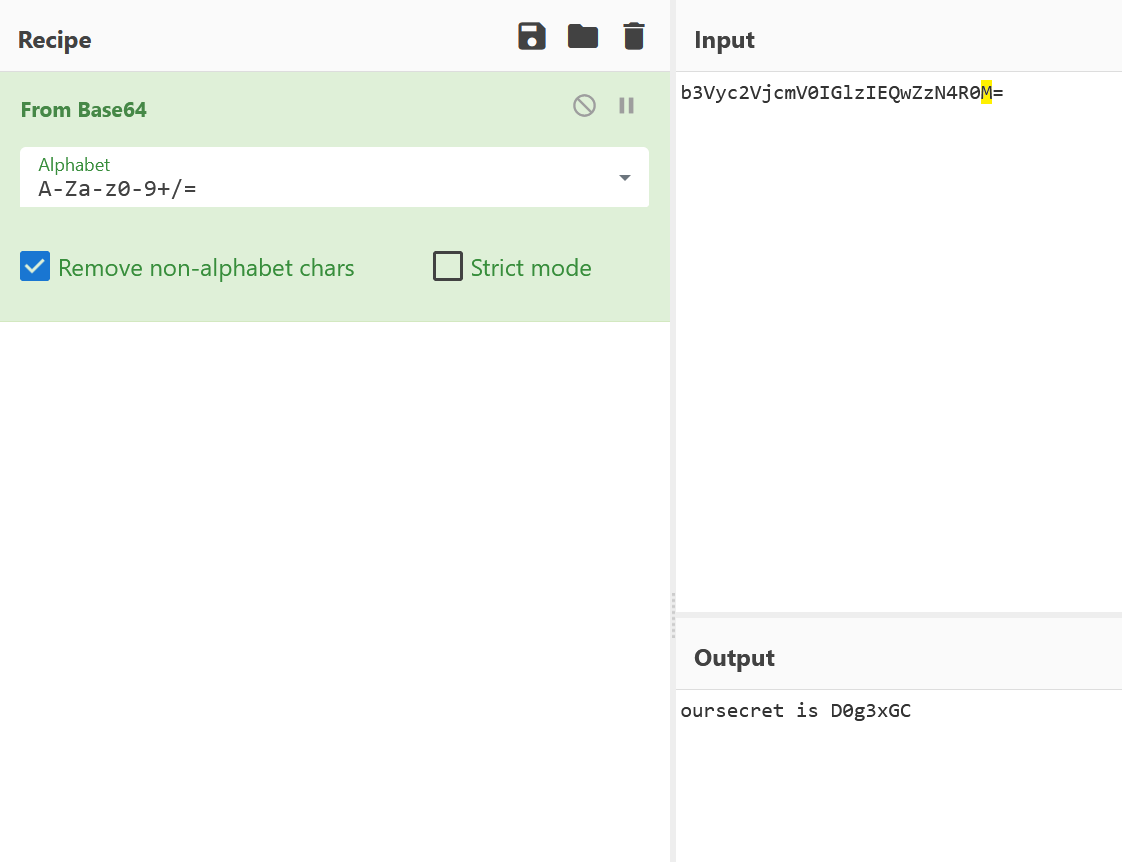
image-20241207190302519
解出来提示oursecret,用oursecret提取得到hidden.txt
image-20241207190353388
image-20241207190505330
内容如下
1 2 3 ECB's key is N11c3TrYY6666111 记得给我秋秋空间点赞
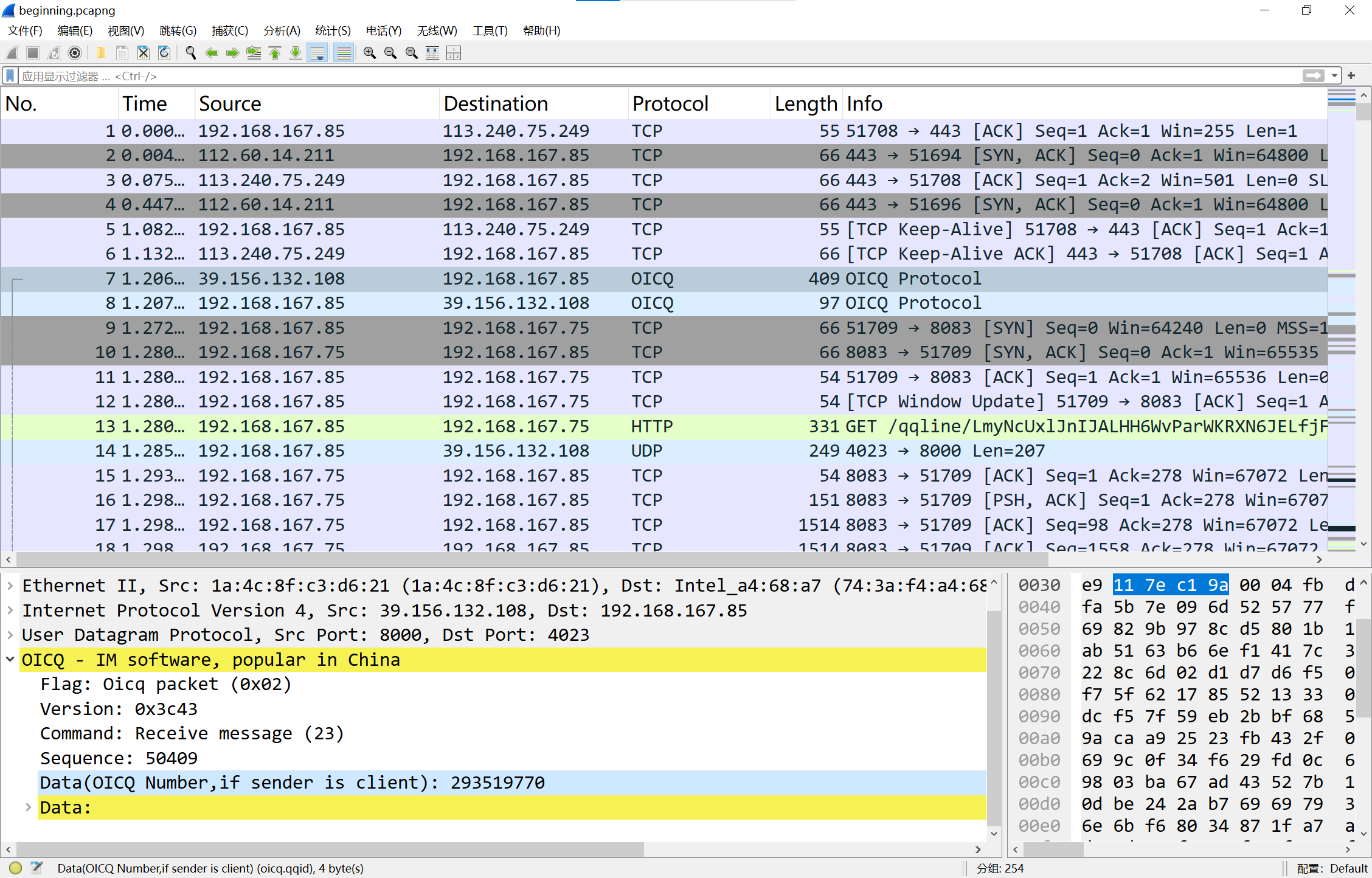
查看流量包中的oicq流,可以看到一个QQ号
image-20241207190631379
看一下其空间,找到密文
image-20241207190927635
flag2
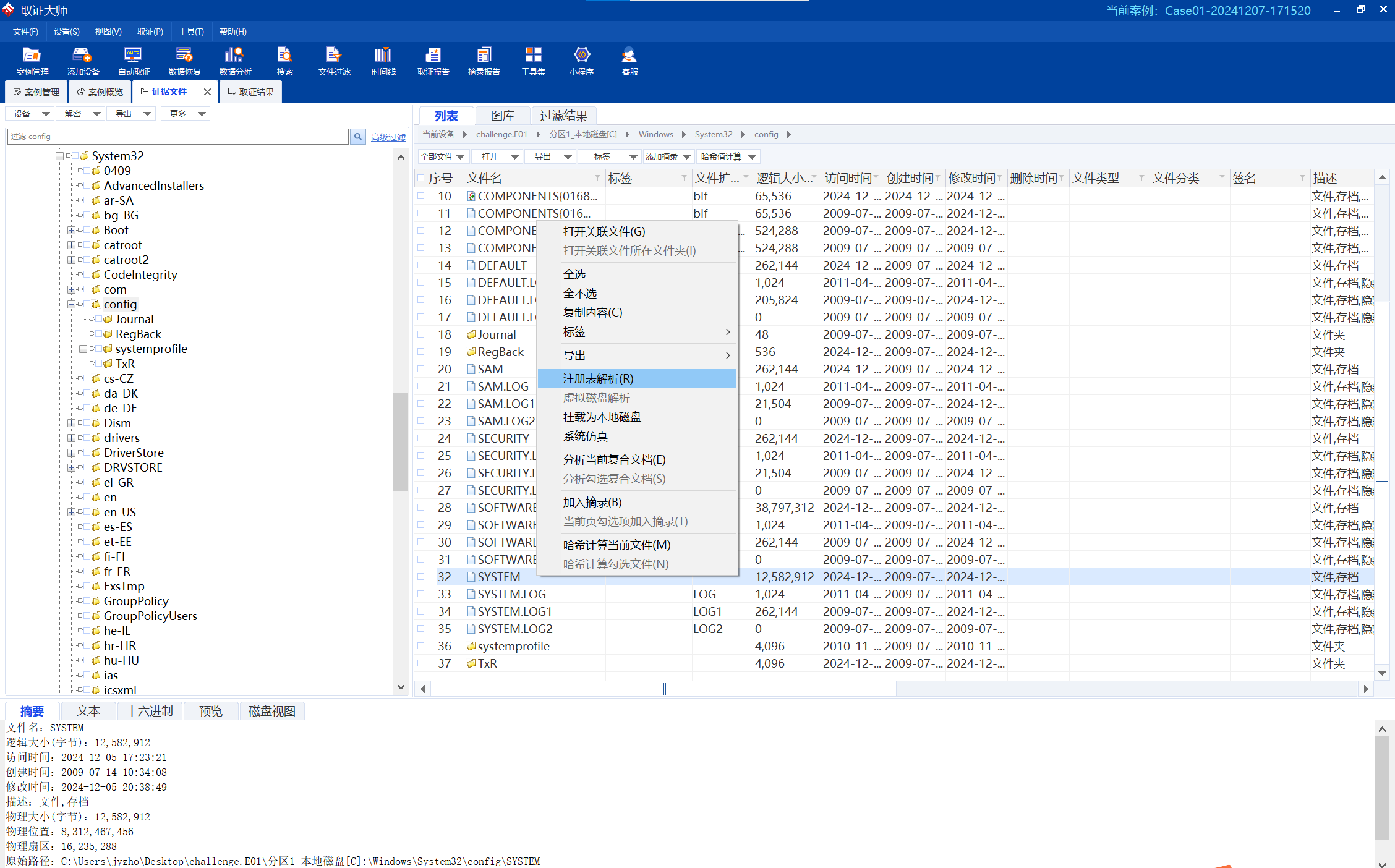
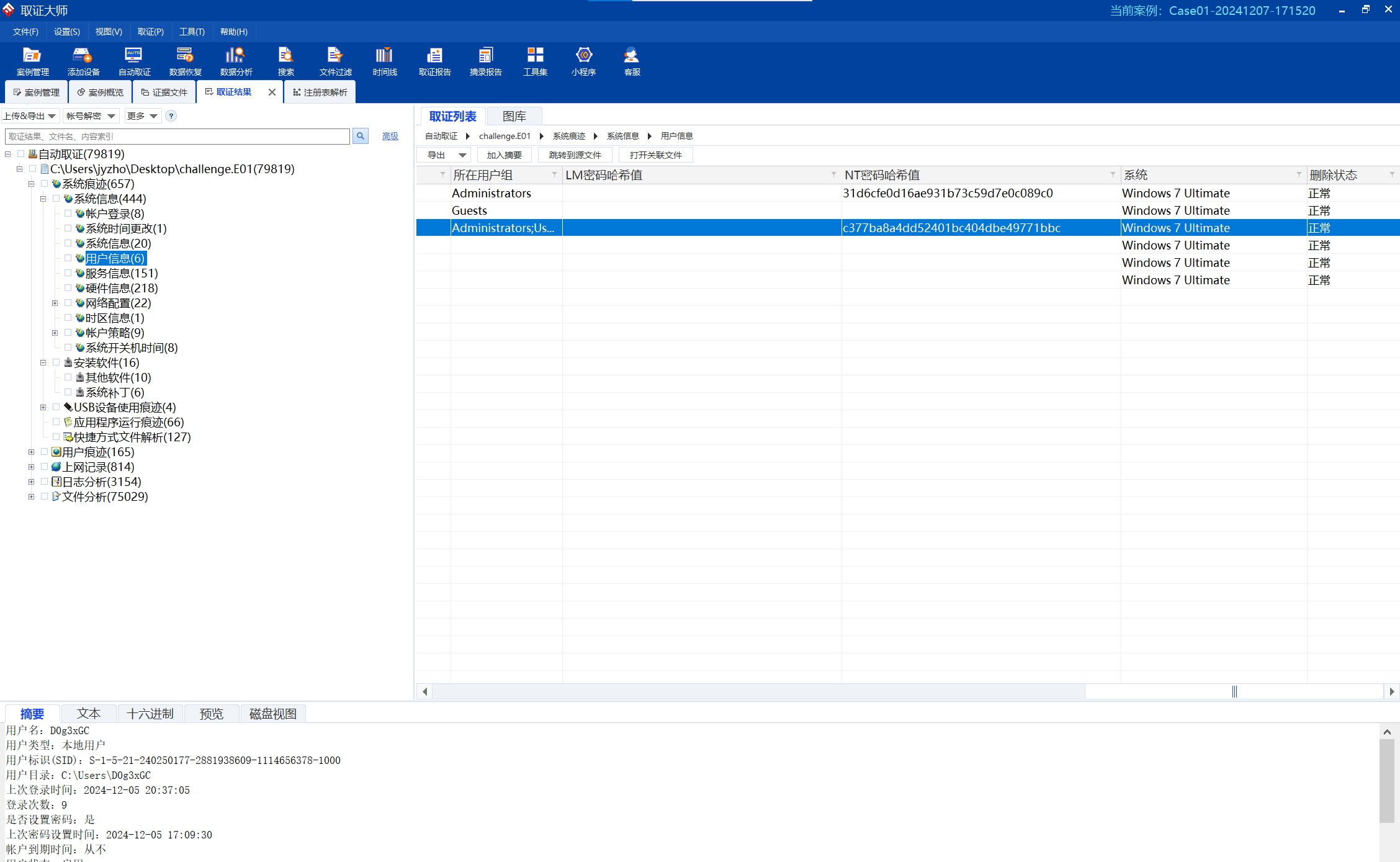
找到SYSTEM,右键解析注册表
image-20241207191051755
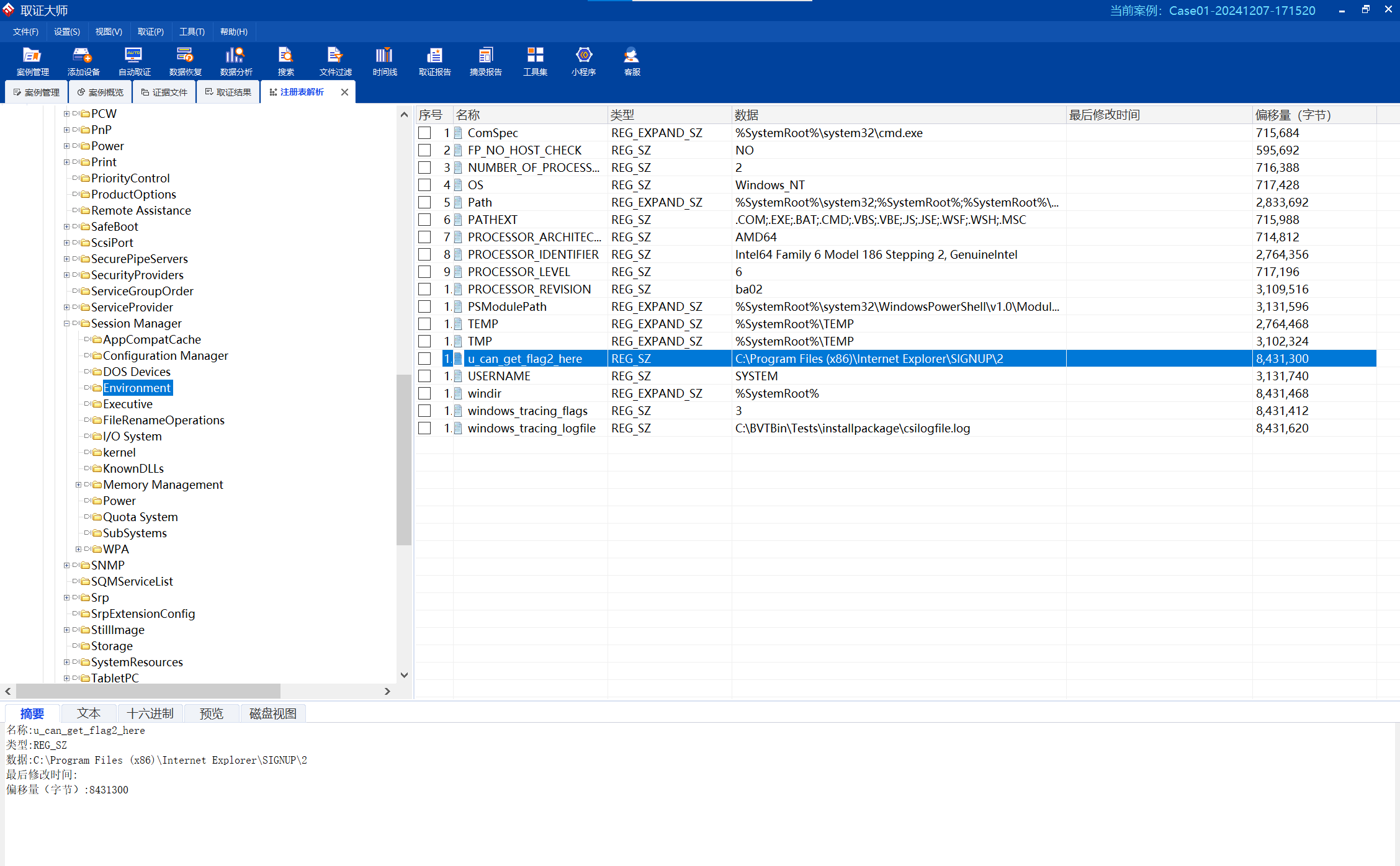
查看环境变量,找到第二个flag存放的路径,前往将其导出
image-20241207191309431
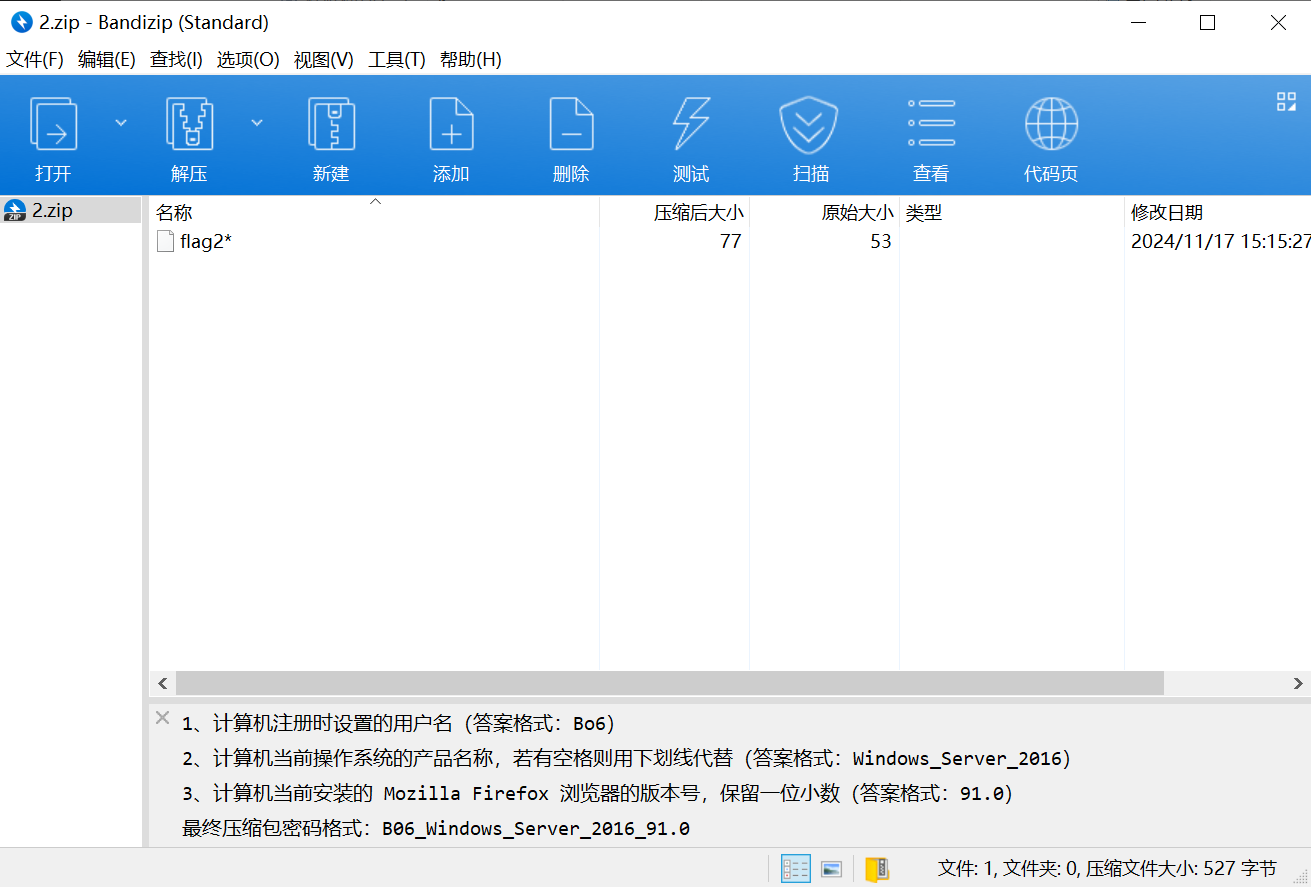
文件名字叫2,但是从特征不难发现这是个压缩包,有注释。
image-20241207191511072
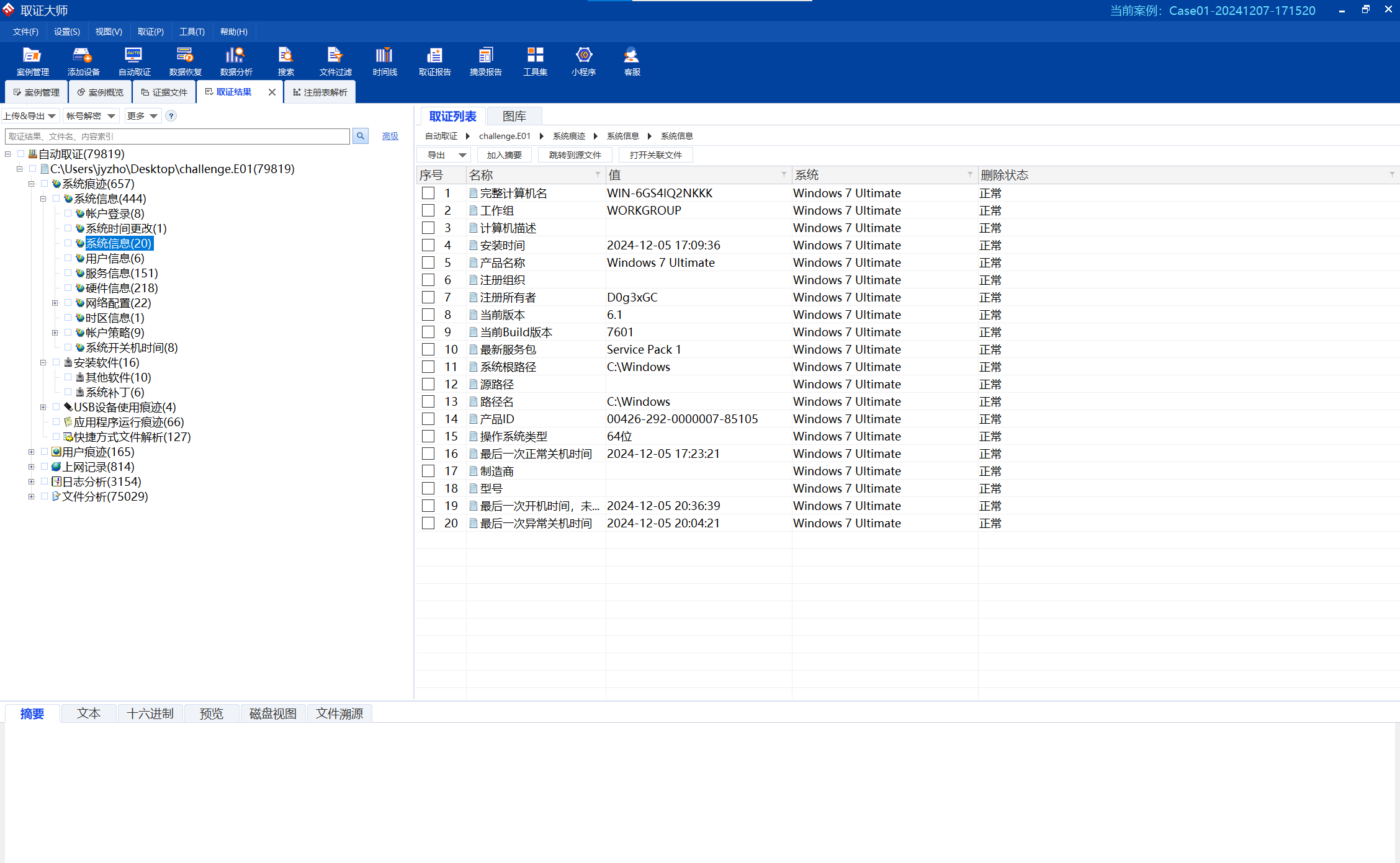
根据要求找到相关信息,得到密码D0g3xGC_Windows_7_Ultimate_115.0
image-20241207192038615
image-20241207192104491
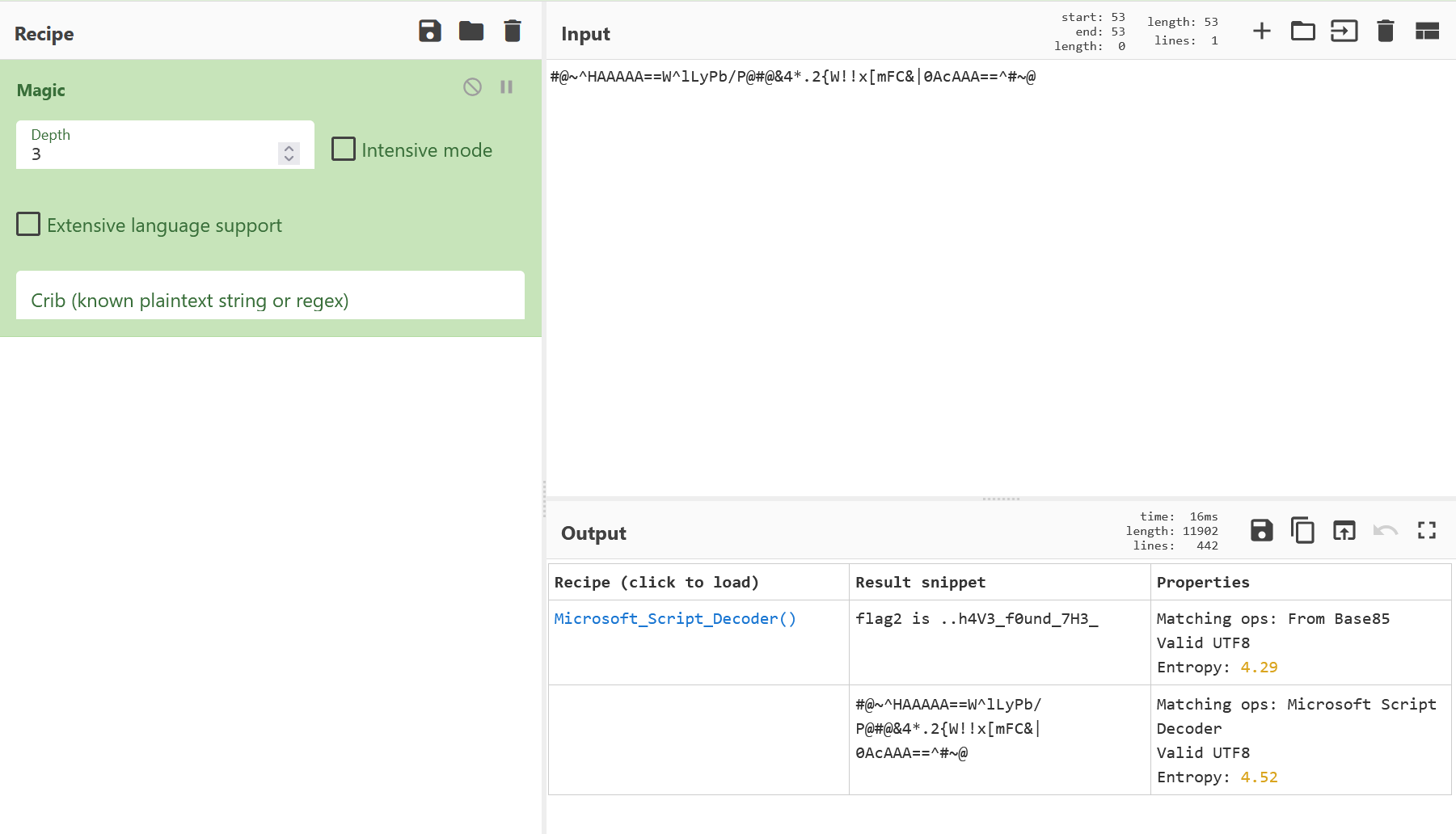
base85
image-20241207192304255
flag3
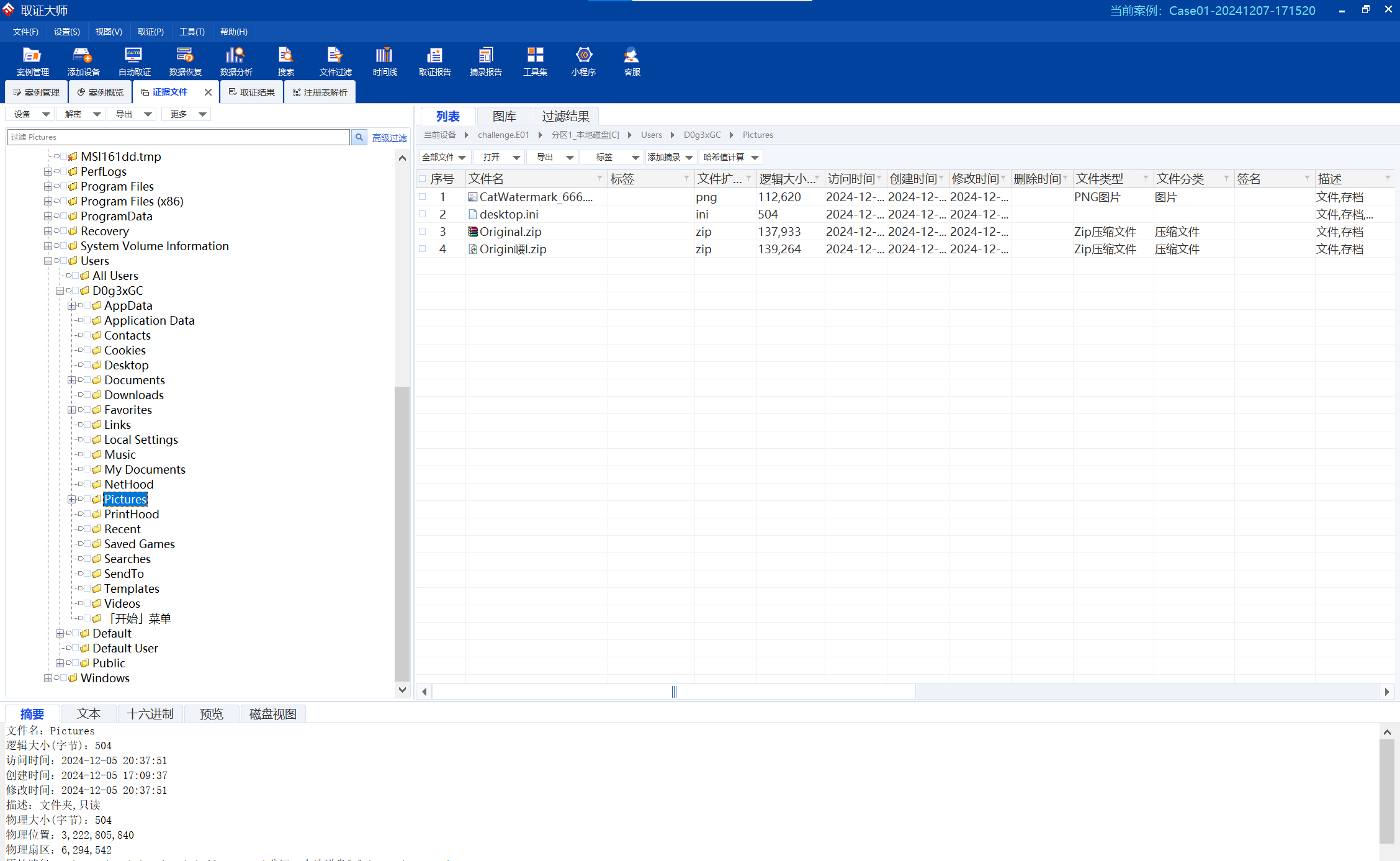
不难找到original.zip,到处都是它的痕迹。同时在图片文件夹下可以找到一张特殊的图片。
image-20241207192522212
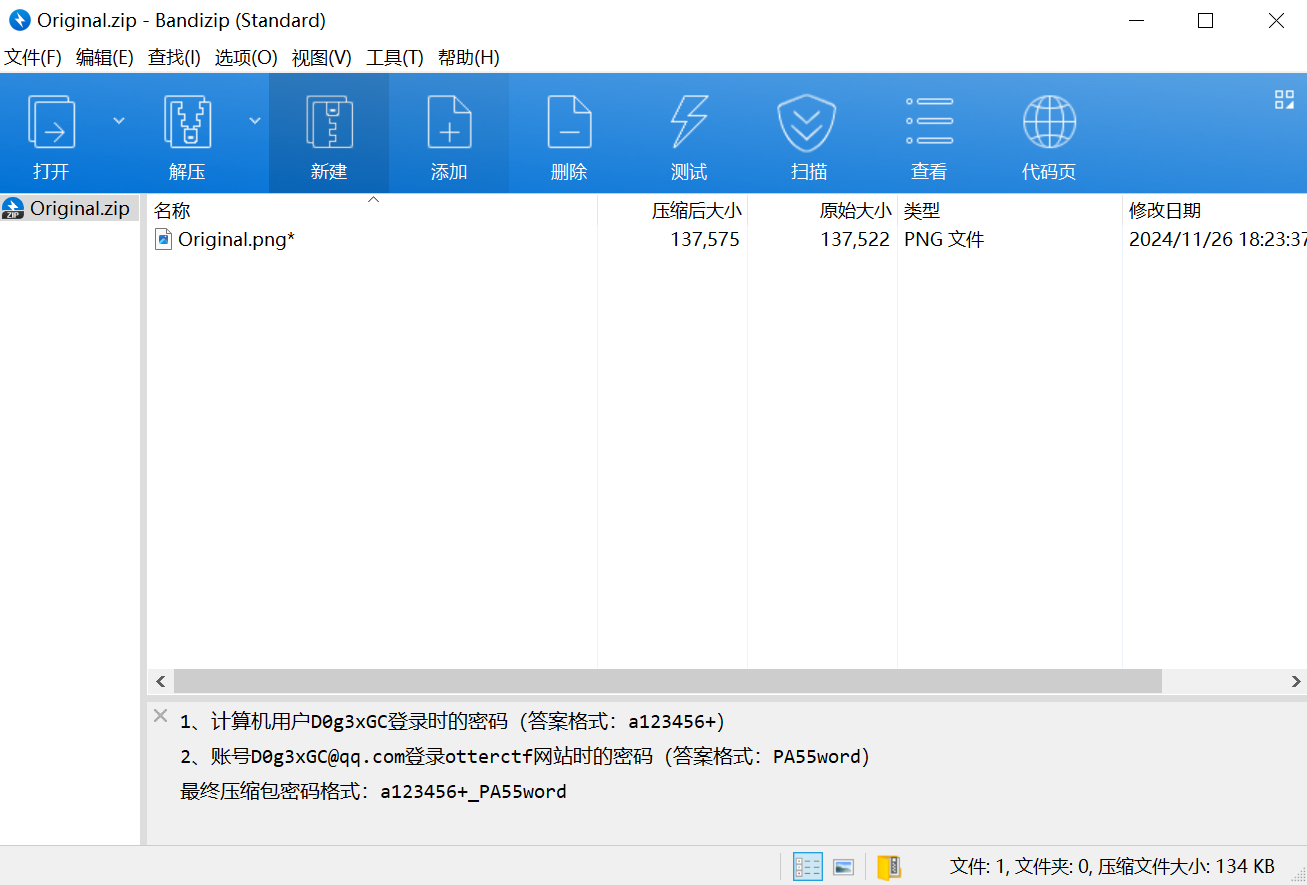
压缩包有注释
image-20241207192609657
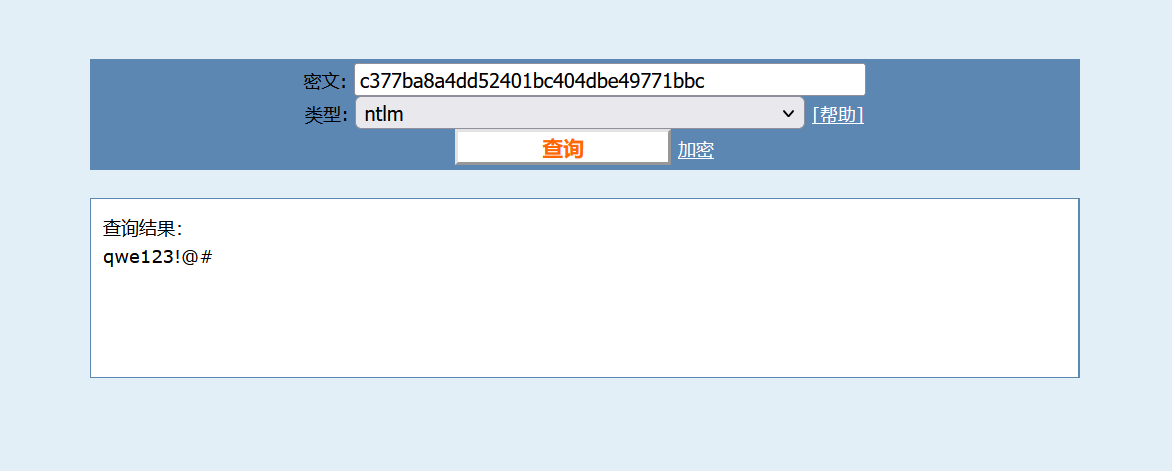
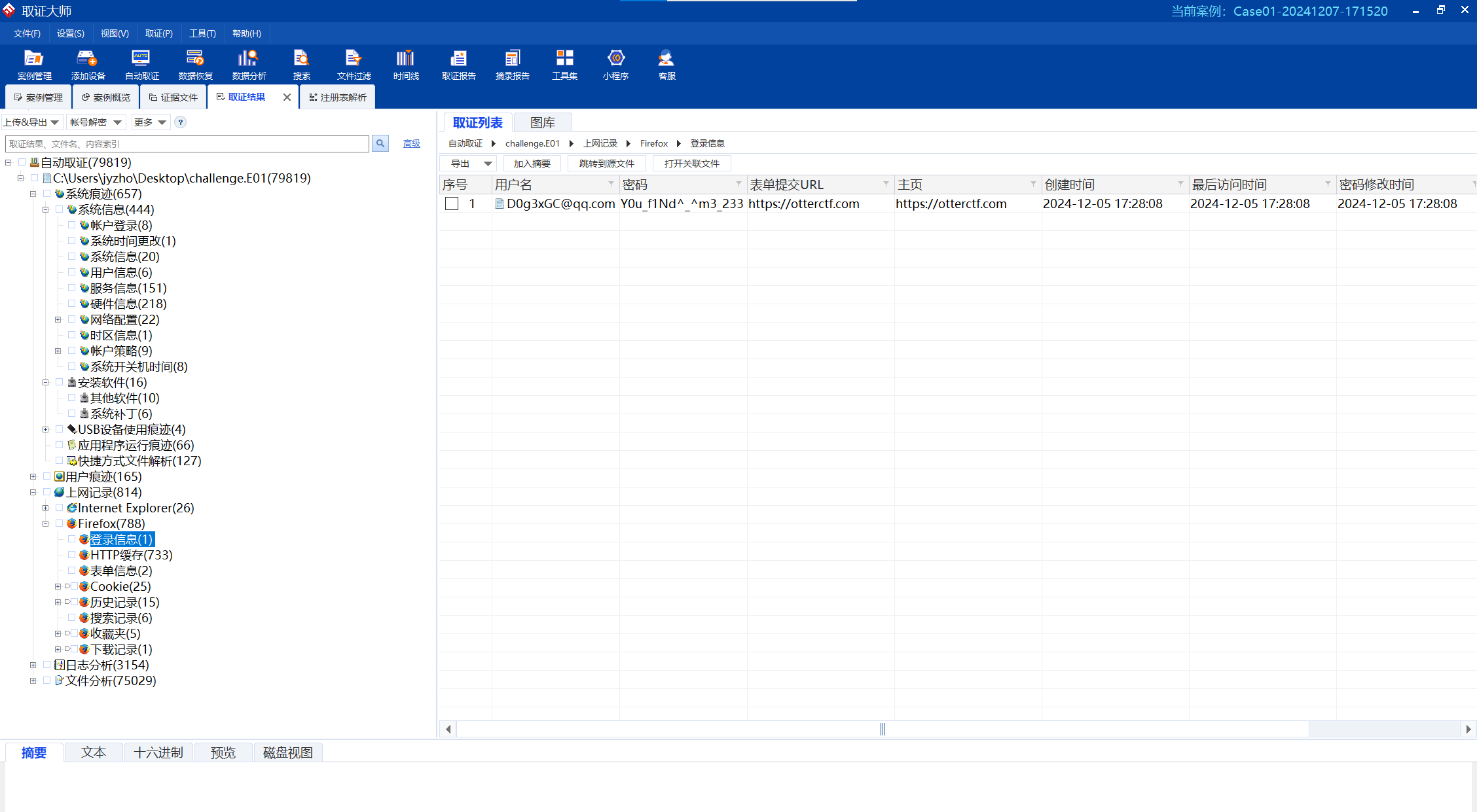
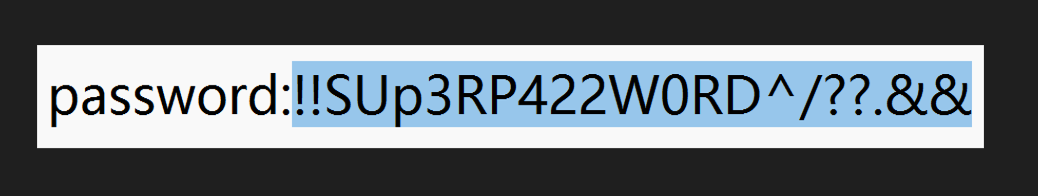
根据要求找到相关信息,得到密码qwe123!@#_Y0u_f1Nd_ m3_233
image-20241207192723500
image-20241207192801229
image-20241207192901376
根据水印图片的名字CatWaterMark_666.png可知,用github上的这个工具 提取盲水印,参数为666
1 python decode.py Original.png CatWaterMark_666.png output.png 6 6 6
image-20241207193442527
flag4
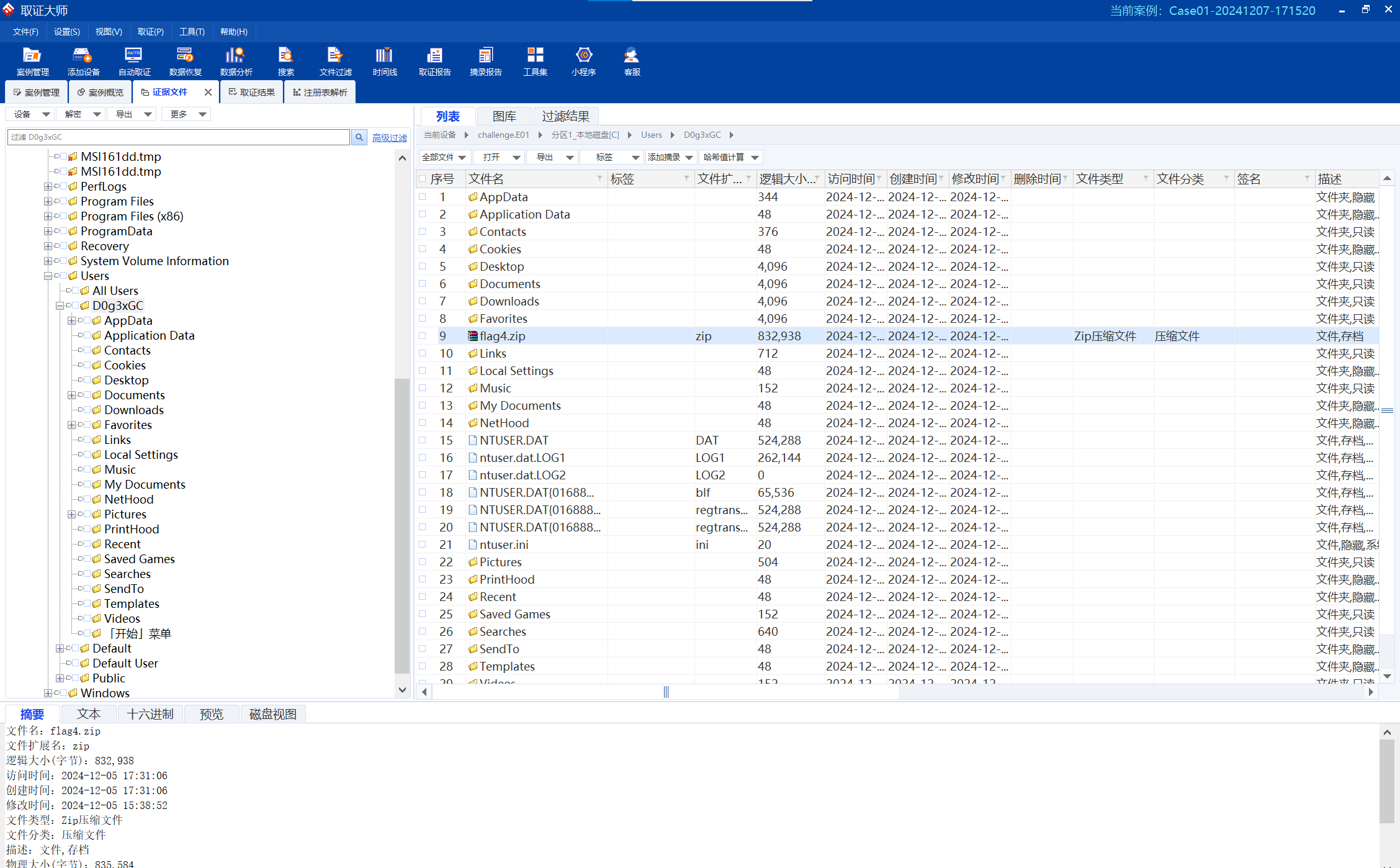
不难找到flag4.zip,到处都是它的痕迹。
image-20241207193653243
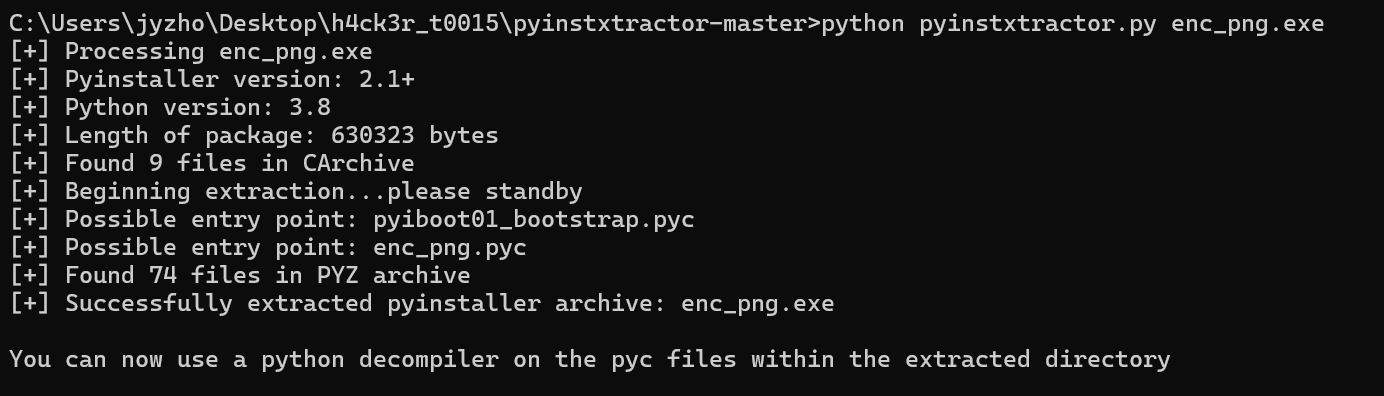
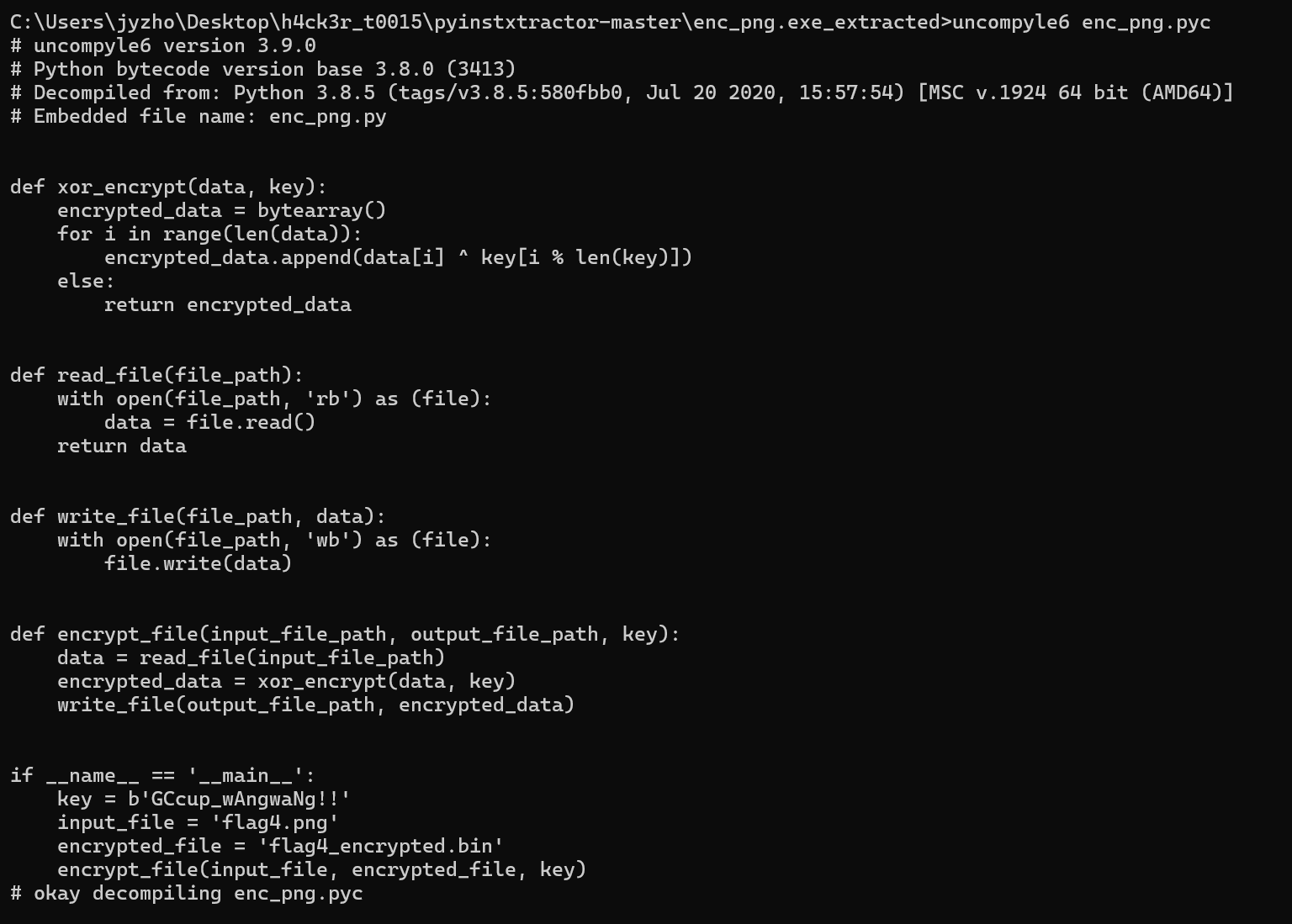
flag4.zip里面有个python打包的exe和一个加密的bin文件,python逆向一下
image-20241207194149584
image-20241207194230130
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 def xor_encrypt (data, key ): encrypted_data = bytearray () for i in range (len (data)): encrypted_data.append(data[i] ^ key[i % len (key)]) else : return encrypted_data def read_file (file_path ): with open (file_path, "rb" ) as file: data = file.read() return data def write_file (file_path, data ): with open (file_path, "wb" ) as file: file.write(data) def encrypt_file (input_file_path, output_file_path, key ): data = read_file(input_file_path) encrypted_data = xor_encrypt(data, key) write_file(output_file_path, encrypted_data) if __name__ == "__main__" : key = b'GCcup_wAngwaNg!!' input_file = "flag4.png" encrypted_file = "flag4_encrypted.bin" encrypt_file(input_file, encrypted_file, key)
什么都不用改就能解密:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 def xor_decrypt (data, key ): encrypted_data = bytearray () for i in range (len (data)): encrypted_data.append(data[i] ^ key[i % len (key)]) else : return encrypted_data def read_file (file_path ): with open (file_path, "rb" ) as file: data = file.read() return data def write_file (file_path, data ): with open (file_path, "wb" ) as file: file.write(data) def decrypt_file (input_file_path, output_file_path, key ): data = read_file(input_file_path) decrypted_data = xor_decrypt(data, key) write_file(output_file_path, decrypted_data) if __name__ == "__main__" : key = b'GCcup_wAngwaNg!!' input_file = "flag4_encrypted.bin" decrypted_file = "flag4.png" decrypt_file(input_file, decrypted_file, key)
flag4.png:
img
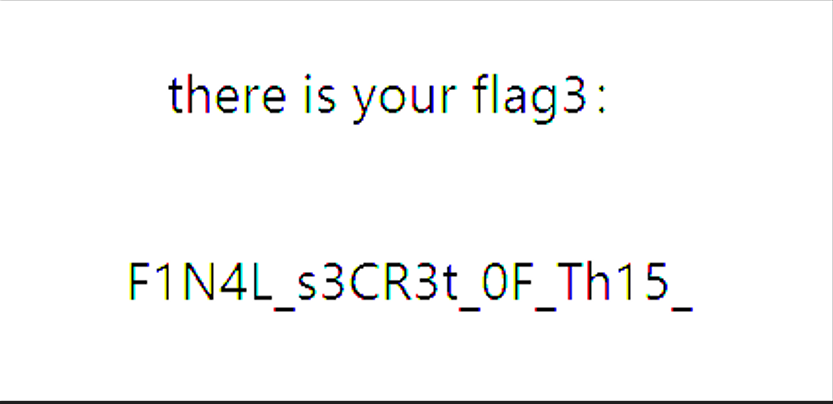
合起来
1 D0g3xGC{Y0u_h4V3_f0und_7H3_F1N4L_s3CR3t_0F_Th15_F0R3N51c5_Ch4Ll3N93}
eZ_Steg0
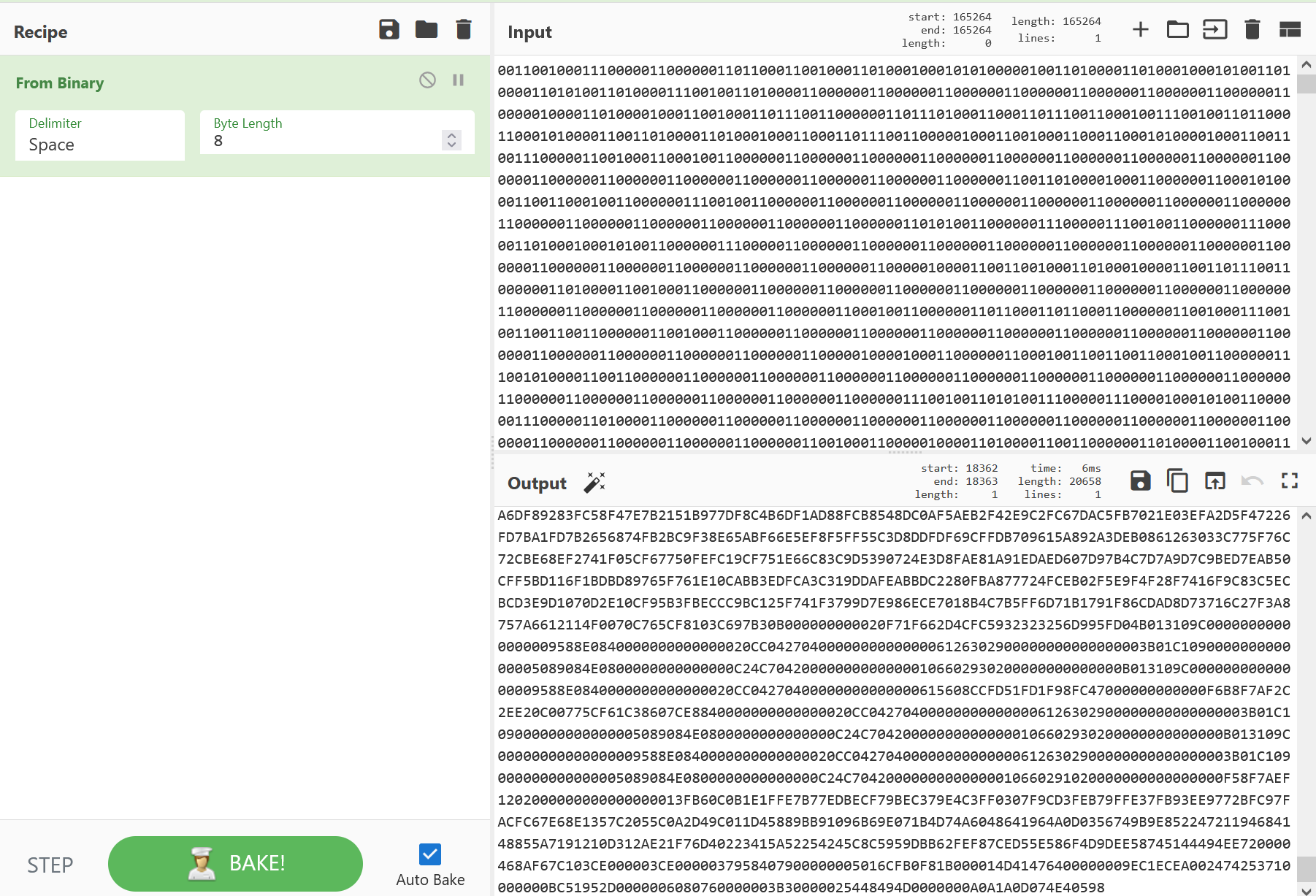
图片名叫01.png,写个python脚本遍历每个像素,黑色记为0,白色记为1,输出二进制字符串
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 from PIL import Imagedef image_to_binary_string (image_path, threshold=127 ): with Image.open (image_path) as img: img = img.convert('L' ) binary_string = "" for y in range (img.height): for x in range (img.width): pixel_value = img.getpixel((x, y)) if pixel_value < threshold: binary_string += "0" else : binary_string += "1" return binary_string.strip() image_path = '01.png' result_string = image_to_binary_string(image_path) print (result_string)
cyberchef转换一下,删去一些0以后发现结尾有倒着的png头
image-20241209184653844
处理一下保存为png
image-20241209184747610
image-20241209185016483
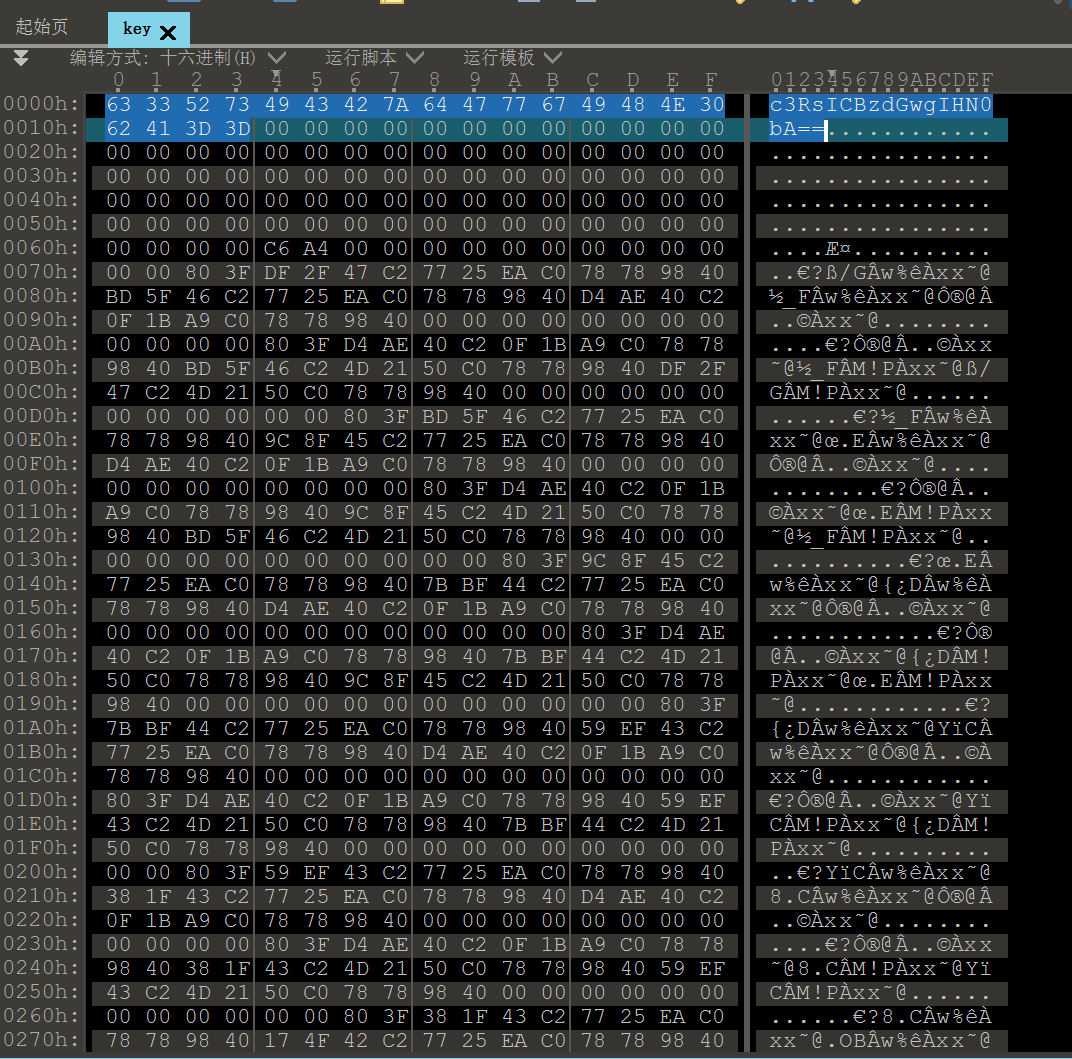
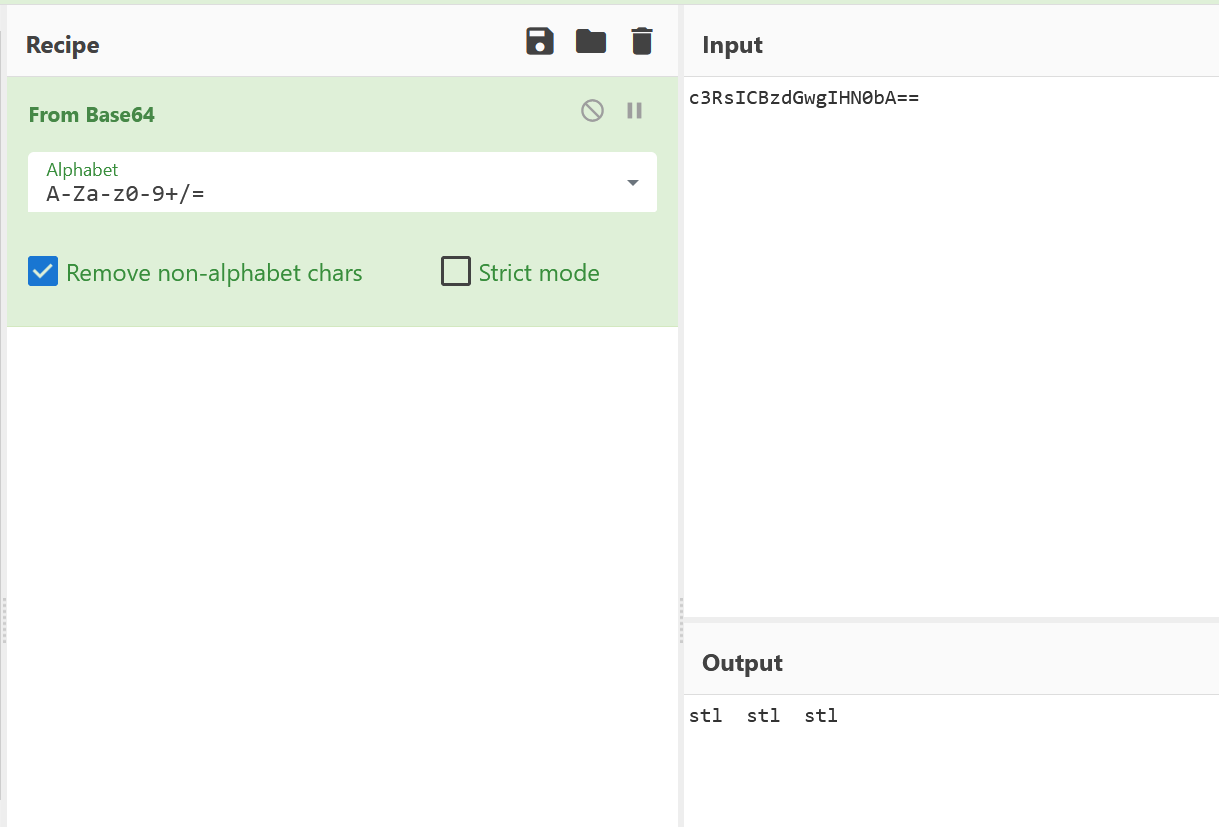
这就是key.zip的密码。解压得到的key开头有段base64
image-20241209185254500
image-20241209185317446
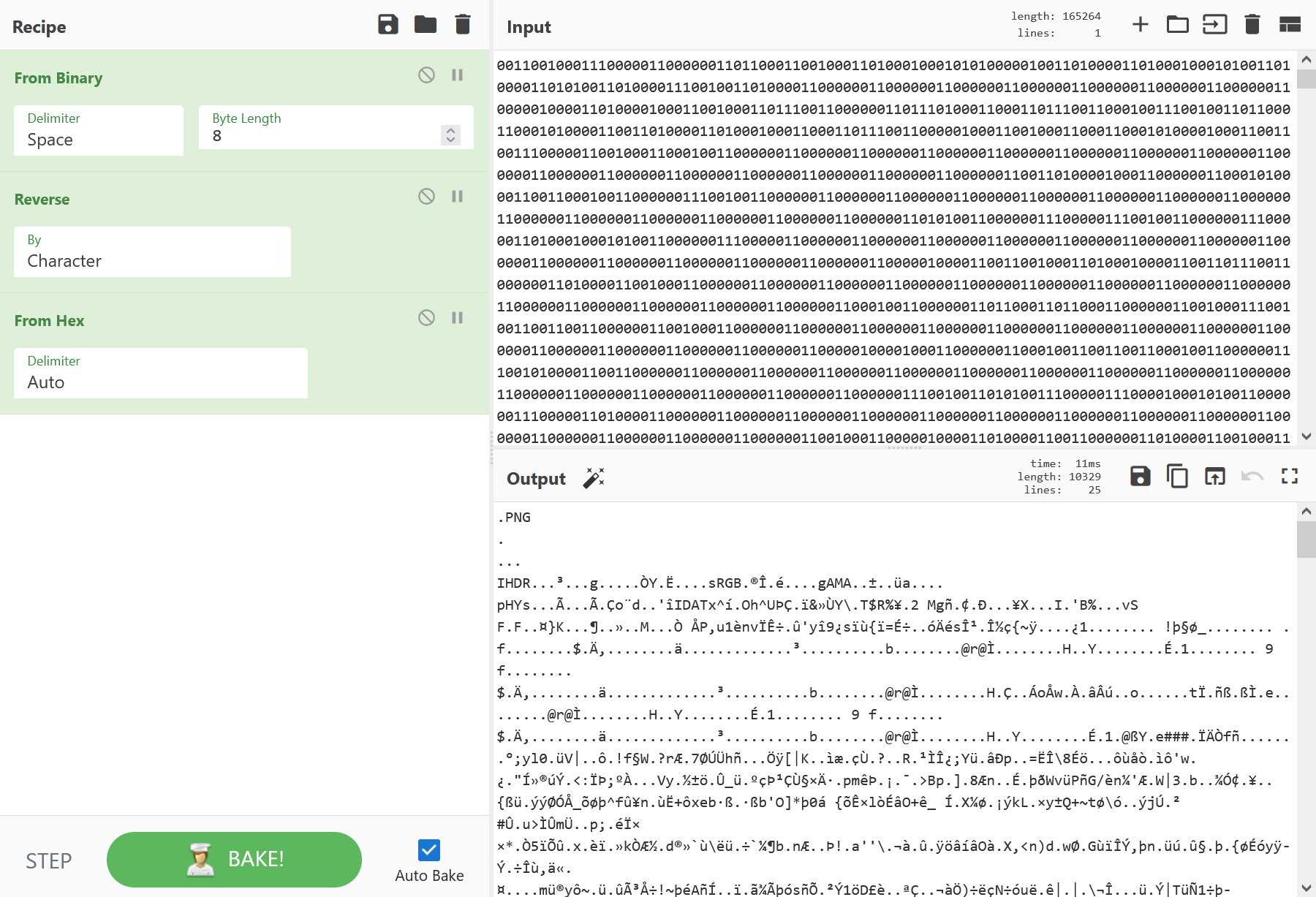
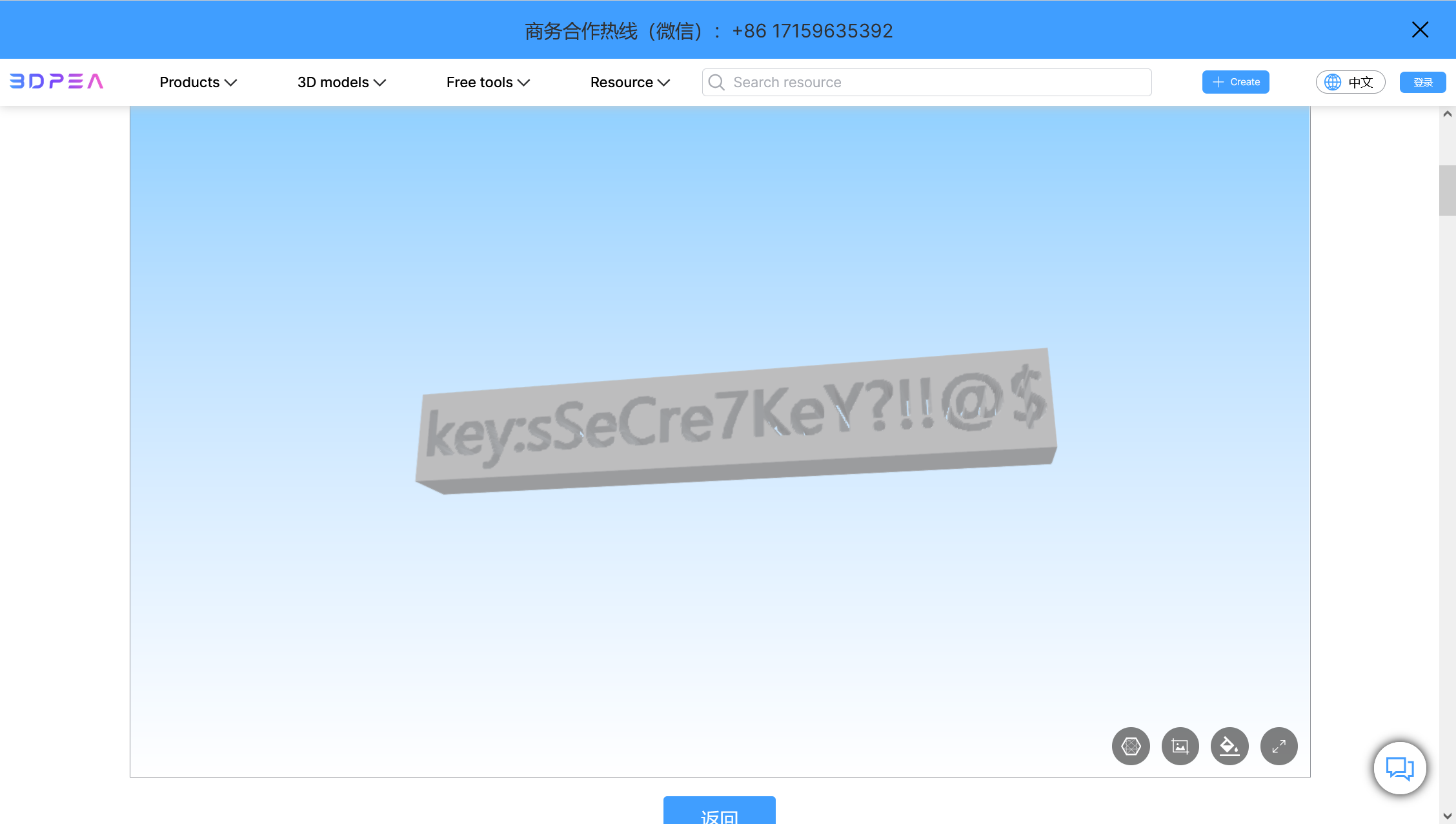
提示了这是一个stl文件,删去开头的base64,修改后缀名为.stl,用这个网站 查看,即可看到key
image-20241209185656525
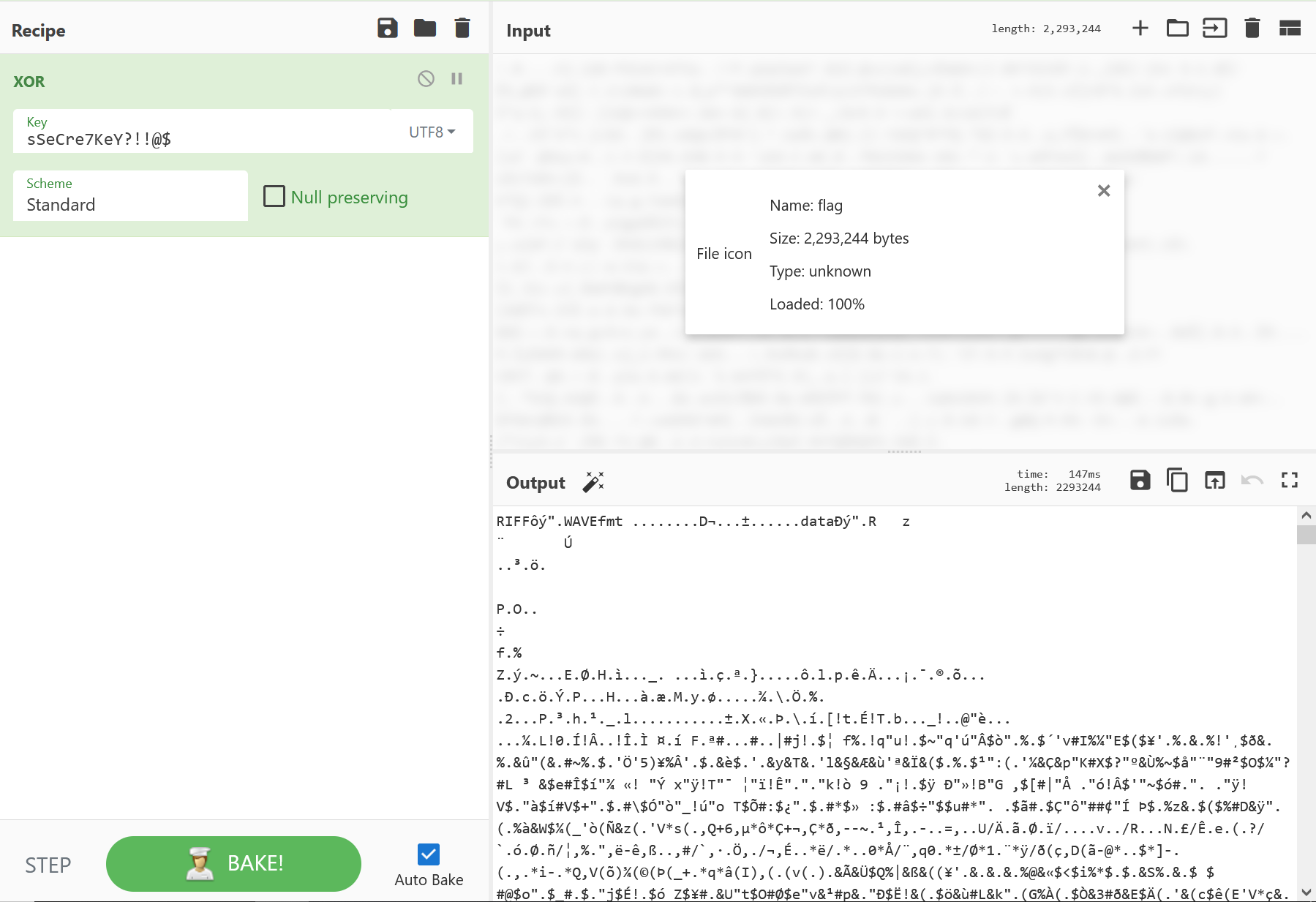
用这个key去对不知道是什么东西的flag文件异或一下,可以得到一个wav文件
image-20241209185954584
提取音频lsb隐写 ,得到flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 import wavesong = wave.open ("download.wav" , mode='rb' ) frame_bytes = bytearray (list (song.readframes(song.getnframes()))) extracted = [frame_bytes[i] & 1 for i in range (len (frame_bytes))] string = "" .join(chr (int ("" .join(map (str ,extracted[i:i+8 ])),2 )) for i in range (0 ,len (extracted),8 )) decoded = string.split("###" )[0 ] print ("Sucessfully decoded: " +decoded)song.close()
1 D0g3xGC{U_4rE_4_WhI2_4t_Ste9An09r4pHY}